A variant of the Power Worm ransomware is infecting computers, encrypting their data files, and throwing away the encryption key, all because of an error in the malware’s programming.
The Power Worm malware is a PowerShell-based ransomware, which uses the Windows PowerShell to initiate and execute its malicious activity.
The Windows PowerShell is a framework developed by Microsoft to allow developers to automate tasks and operations on Windows PCs.
Trend Micro researchers were the ones that discovered the Power Worm ransomware back in March 2014, when they detected an active campaign targeting Word and Excel files.
The hacker made an error in the encryption routine’s code
This particular variant of the Power Worm ransomware targets a broader scope of data file types, but this is not the particular “feature” that makes it stand out amongst other ransomware families.
The “feature” is actually a badly implemented encryption routine, caused in the hacker’s attempt at simplifying the decryption process and cutting down operational costs.
As Nathan Scott, a malware researcher explained to Bleeping Computer, the ransomware’s author used the AES encryption engine, but wanted to do away with the random and unique encryption keys generated for each user, and use a static AES key instead, the same for each victim.
This would have allowed him to simplify the website where users download the decryption keys, by not having to query a database of private decryption keys, and then serve a custom-generated decryption tool based on a local ID generated for each infected user.
Users cannot recover the files encrypted by this ransomware
The problem is that a programming error (improperly padded AES key) led to the ransomware generating random decryption keys instead of static keys. Because the author had not prepared special routines inside the malware’s code to deal and store random keys, the ransomware was encrypting files, and then throwing away the decryption key.
The only way users can recover their files is if they restore them from a backup.
You can recognize if you have been infected by this ransomware by the ransom message it shows, copied from the CryptoWall ransomware. For all users, the user ID is always “qDgx5Bs8H” because the author knew users would have the same encryption key. There’s a screenshot of the ransom message below, courtesy of Bleeping Computer.
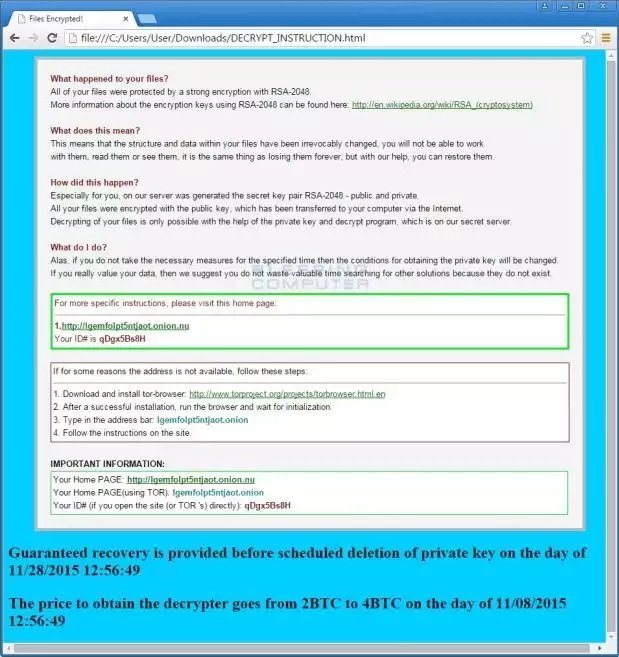
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











