BABYSPLOIT INTRO:- Babysploit is a pentesting tool kit used in initial phase of pentesting. BabySploit mostly covers each and every scan. This tool is a bundle of all the small tools. This tool is used for people who are new in hacking and want to learn initial phases of pentesting, as per ethical hacking expert from International Institute of Cyber Security.
INSTALLING BABYSPLOIT:-
IF YOU ARE NOT USING KALI LINUX FOLLOW BELOW STEPS TO INSTALL BABYSPLOIT:-
- If you are running any other linux distros. You need to clone tool from github.
- For cloning type:- git clone git://github.com/M4cs/BabySploit ~/BabySploit
- After cloning open the babysploit folder and run below commands for creating an virtual environment for the babysploit.
- For upgrading
type sudo apt-get update
then
type sudo apt-get upgrade
- After upgrading the linux you have to install python libraries:-
For installing python type sudo python3 install.py
- Create the babysploit environment in linux.
For creating environment type virtualenv babysploit
then type source babysploit/bin/activate
- After creating the environment:-
type pip3 install -r requirements.txt
then type python start.py
IF YOU ARE USING KALI LINUX FOLLOW BELOW STEPS TO INSTALL BABYSPLOIT:-
- If you are running on kali linux, you have to upgrade the kali linux in order to run babysploit.
- For upgrading kali linux
type sudo apt-get update
then
type sudo apt-get upgrade
- After upgrade type:- git clone git://github.com/M4cs/BabySploit ~/BabySploit then follow below steps.
- Then type ls.
- Install the required libraries for the babysploit
For that type: pip3 -r requirement.txt
root@kali:~/BabySploit# ls babysploit images install.py LICENSE.md pdfs README.md requirements.txt sites start.py root@kali:~/BabySploit# pip3 install -r requirements.txt Requirement already satisfied: netifaces==0.10.7 in /usr/local/lib/python3.6/dist-packages (from -r requirements.txt (line 1)) Requirement already satisfied: urllib3==1.24 in /usr/lib/python3/dist-packages (from -r requirements.txt (line 2)) Requirement already satisfied: humanfriendly==4.17 in /usr/local/lib/python3.6/dist-packages (from -r requirements.txt (line 3)) Requirement already satisfied: terminaltables==3.1.0 in /usr/local/lib/python3.6/dist-packages (from -r requirements.txt (line 4)) Requirement already satisfied: pyfiglet==0.7.6 in /usr/local/lib/python3.6/dist-packages (from -r requirements.txt (line 5)) Requirement already satisfied: requests==2.20.1 in /usr/local/lib/python3.6/dist-packages (from -r requirements.txt (line 6)) Requirement already satisfied: PyPDF3==1.0.1 in /usr/local/lib/python3.6/dist-packages (from -r requirements.txt (line 7)) Requirement already satisfied: raccoon-scanner==0.8.5 in /usr/local/lib/python3.6/dist-packages (from -r requirements.txt (line 8)) Requirement already satisfied: chardet<3.1.0,>=3.0.2 in /usr/lib/python3/dist-packages (from requests==2.20.1->-r requirements.txt (line 6)) Requirement already satisfied: certifi>=2017.4.17 in /usr/lib/python3/dist-packages (from requests==2.20.1->-r requirements.txt (line 6)) Requirement already satisfied: idna<2.8,>=2.5 in /usr/lib/python3/dist-packages (from requests==2.20.1->-r requirements.txt (line 6)) Requirement already satisfied: tqdm in /usr/local/lib/python3.6/dist-packages (from PyPDF3==1.0.1->-r requirements.txt (line 7)) Requirement already satisfied: click in /usr/lib/python3/dist-packages (from raccoon-scanner==0.8.5->-r requirements.txt (line 8)) Requirement already satisfied: lxml in /usr/lib/python3/dist-packages (from raccoon-scanner==0.8.5->-r requirements.txt (line 8)) Requirement already satisfied: beautifulsoup4 in /usr/lib/python3/dist-packages (from raccoon-scanner==0.8.5->-r requirements.txt (line 8)) Requirement already satisfied: xmltodict in /usr/local/lib/python3.6/dist-packages (from raccoon-scanner==0.8.5->-r requirements.txt (line 8)) Requirement already satisfied: fake-useragent in /usr/local/lib/python3.6/dist-packages (from raccoon-scanner==0.8.5->-r requirements.txt (line 8)) Requirement already satisfied: dnspython in /usr/lib/python3/dist-packages (from raccoon-scanner==0.8.5->-r requirements.txt (line 8))
We have already have the installed dependencies that is why we are getting “Requirement already satisfied”
- Then type python3 start.py
root@kali:~/BabySploit# python3 start.py
.-""-. _
/ _ \ _ /|)
.'---""-.| /|) /|/
.' `. /|/ /|/
__/_ \ . /|/ /|/
.' `-. .8-. \\-/|/ /|/
J .--. Y .o./ .o8\ |/\ `/_.-.
| ( \ 98P 888| /\ / ( ` |
| `-._/ | `"|/\ / \|\ F
`. . "-'|\ / \/\ J
|---' _/\ / \// ` |
J /// / / F
_\ .'`-._ ./// / /\\.'
/ `. / .-' `<-'/// / _/\ \\
F.--.\|| `.`/ /.-' )|\ \`.
\__.-/)' `.-' ')/\\ /
.-' .'/ \ ') `-'
( .'.' '`. .'
\'.' ' `. .-'
/ ' `.__.-'/|
J : `._/ |
| : |
J ;-"""-. F
\ / \ /
`.J L _.'
F |--' |
J | |__
L | `.
| |-. \|
| \ )_.'
F -.\ )-'
\ )_)
`""""""""
[i] Default Gateway: 192.168.1.1 [i]
BabySploit!
Developed by @maxbridgland
https://github.com/M4cs/BabySploit
[i] Loaded Configuration... [i]
BabySploit is a framework aimed at helping aspiring
penetration testers learn how to use the most common and
useful tools in the field. Below is a table displaying
what commands are available and what they do.
lqqqqqqqqqqqqqqqqwqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqk
x Command x Description x
tqqqqqqqqqqqqqqqqnqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqu
x help or ? x Display this menu x
x info x Display current configuration options x
x search x Search exploitdb for exploits and get link x
x tools x Display available tools x
x set <key name> x Set configuration key x
x reset x Reset configuration to default x
x update x Check for updates and update thes framework x
x tutorial x Run the tutorial wizard x
x exit x Exit framework x
mqqqqqqqqqqqqqqqqvqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqj
[babysploit]>
CLI OUTPUT OF BABYSPLOIT:
- Typing help or ? will display the same menu appearing above in red font.
- For checking the current configuration option type info in linux terminal.
[babysploit]> info lhost: 0.0.0.0 lport: 8080 rhost: google.com rport: 80 platform: Linux 4.15.0-kali2-686-pae usernamelist: lists/users passwordlist: lists/pass/rockyou.txt urlpath: /connect
- Then type tools to view list of tools included in babysploit.
BABYSPLOIT INBUILT TOOLS:-
[babysploit]> tools ______ __ /_ __/___ ____ / /____ / / / __ \/ __ \/ / ___/ / / / /_/ / /_/ / (__ ) /_/ \____/\____/_/____/ Simply enter the name of the tool you want to use to use it. lInformation Gatheringqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqk x x x x Tool x Description x tqqqqqqqqqqqqqqnqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqu x nmap x nmap port scanner tool x x iplookup x ip info tool x x dnslookup x dns lookup tool x x censyslookup x censys api lookup | req api creds x x raccoon x use raccoon scanner tool | command: raccoon --help x x cfbypass x cloudflare bypasser x mqqqqqqqqqqqqqqvqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqj lExploitationqqwqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqk x x x x Tool x Description x tqqqqqqqqqqqqqqnqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqu x searchsploit x search available exploits (use search command) x x reverseshell x reverse shell tool for creating payloads x x ftpvulnscan x check for ftp buffer overflow x x wpseku x wordpress vulnerability scanner x mqqqqqqqqqqqqqqvqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqj lPhishingqqwqqqqqqqqqqqqqqqqqqqqk x x Description x x Tool x x tqqqqqqqqqqnqqqqqqqqqqqqqqqqqqqqu x blackeye x BlackEye Phish Kit x mqqqqqqqqqqvqqqqqqqqqqqqqqqqqqqqj lCryptography/Steganographyk x x x x Tool x Description x tqqqqqqqqqnqqqqqqqqqqqqqqqu x pdfmeta x pdf meta data x mqqqqqqqqqvqqqqqqqqqqqqqqqj lBruteforcingqqqwqqqqqqqqqqqqqqqqqqqqqqk x x x x Tool x Description x tqqqqqqqqqqqqqqqnqqqqqqqqqqqqqqqqqqqqqqu x ftpbruteforce x ftp brute force tool x mqqqqqqqqqqqqqqqvqqqqqqqqqqqqqqqqqqqqqqj
There are many tools which can be used in information gathering.
NOW WE WILL FIRST TAKE IPLOOKUP TOOL:-
Iplookup is used to know the ip of the target.
- Type iplookup
- Then type testphp.vulnweb.com
[babysploit]> iplookup [?] Enter IP or Domain To Lookup: testphp.vulnweb.com [!] Sending Request... [!] Request Successful Displaying Response: Location: Frankfurt am Main, Hesse Germany 60313 IP: 176.28.50.165 ISP: Host Europe GmbH Scan Complete. SneakyBoy..
- After scanning the target, Iplookup has found target IP address and the location of the target. And its ISP.
- The above output can be used in initial phase of information gathering
NOW WE WILL TAKE DNSLOOKUP TOOL:-
Dnslookup is used to know the records of the target.
- Type dnslookup
- Then type hackthissite.org
[babysploit]> dnslookup [?] Please Enter The Domain You'd Like To Lookup: hackthissite.org Checking For A Records ---------------------- First A Record: 137.74.187.100 | TTL: 1603 Second A Record: 137.74.187.102 | TTL 1603 Checking For MX Records ------------------------- First MX Record: 30 aspmx5.googlemail.com | TTL: 3600 Second MX Record: 10 aspmx.l.google.com | TTL: 3600 Checking For AAAA Records ------------------------- First AAAA Record: 2001:41d0:8:ccd8:137:74:187:100 | TTL: 3600 Second AAAA Record: 2001:41d0:8:ccd8:137:74:187:102 | TTL: 3600 Checking For TXT Records ------------------------- [!] Failed To Find TXT Records [!] DNS Lookup Complete!
- After scanning the target dnslookup has found some of the records which can be used in other hacking activities.
NOW WE WILL TAKE RACCOON TOOL:-
Raccoon is a tool used in information gathering. Raccoon is mostly used to show the DNS records, port scanner and URL fuzzer.
- For using raccoon type raccoon –help.
[babysploit]> raccoon --help Usage: raccoon [OPTIONS] TARGET Options: --version Show the version and exit. -d, --dns-records TEXT Comma separated DNS records to query. Defaults to: A,MX,NS,CNAME,SOA,TXT --tor-routing Route HTTP traffic through Tor (uses port 9050). Slows total runtime significantly --proxy-list TEXT Path to proxy list file that would be used for routing HTTP traffic. A proxy from the list will be chosen at random for each request. Slows total runtime -c, --cookies TEXT Comma separated cookies to add to the requests. Should be in the form of key:value Example: PHPSESSID:12345,isMobile:false --proxy TEXT Proxy address to route HTTP traffic through. Slows total runtime -w, --wordlist TEXT Path to wordlist that would be used for URL fuzzing -T, --threads INTEGER Number of threads to use for URL Fuzzing/Subdomain enumeration. Default: 25 --ignored-response-codes TEXT Comma separated list of HTTP status code to ignore for fuzzing. Defaults to: 302,400,401,402,403,404,503,504 --subdomain-list TEXT Path to subdomain list file that would be used for enumeration -sc, --scripts Run Nmap scan with -sC flag -sv, --services Run Nmap scan with -sV flag -f, --full-scan Run Nmap scan with both -sV and -sC -p, --port TEXT Use this port range for Nmap scan instead of the default --vulners-nmap-scan Perform an NmapVulners scan. Runs instead of the regular Nmap scan and is longer. --vulners-path TEXT Path to the custom nmap_vulners.nse script.If not used, Raccoon uses the built-in script it ships with. -fr, --follow-redirects Follow redirects when fuzzing. Default: False (will not follow redirects) --tls-port INTEGER Use this port for TLS queries. Default: 443 --skip-health-check Do not test for target host availability --no-url-fuzzing Do not fuzz URLs --no-sub-enum Do not bruteforce subdomains --skip-nmap-scan Do not perform an Nmap scan -q, --quiet Do not output to stdout -o, --outdir TEXT Directory destination for scan output --help Show this message and exit.
For Checking the version of the raccoon.
- Type raccoon –version
[babysploit]> raccoon --version raccoon, version 0.8.5
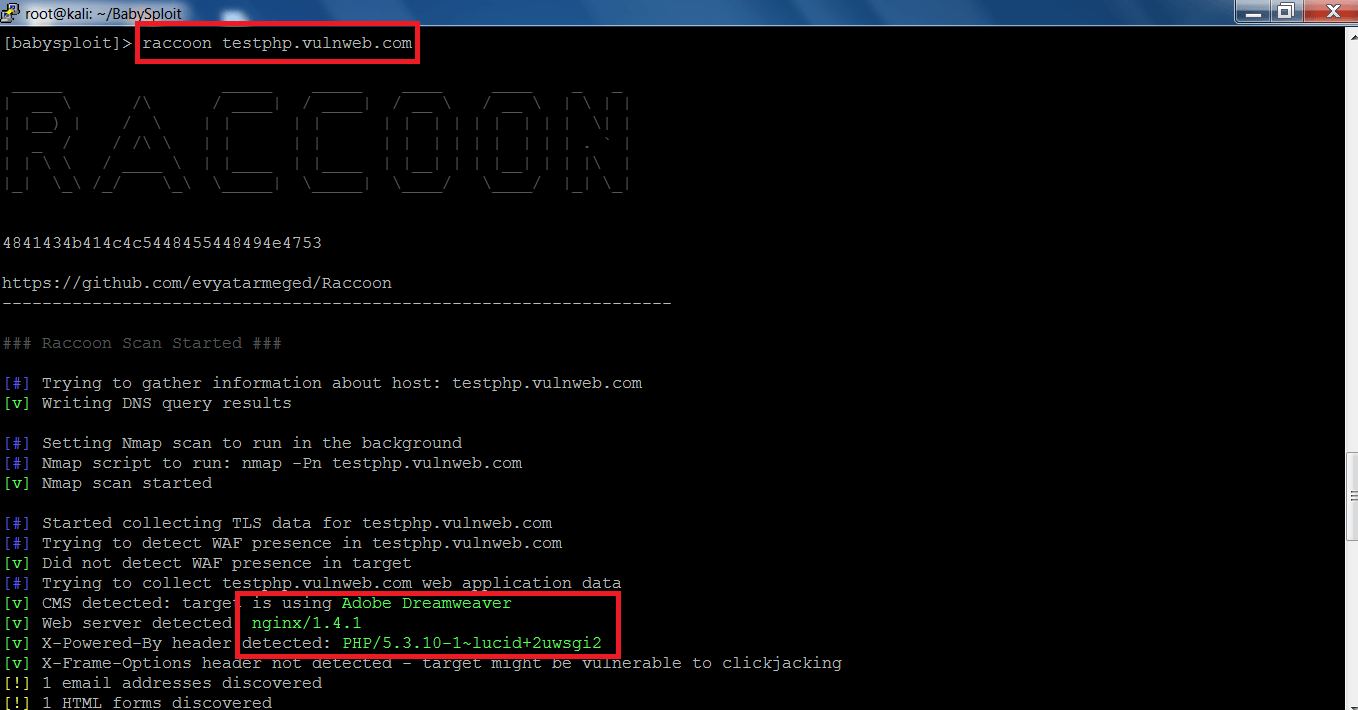
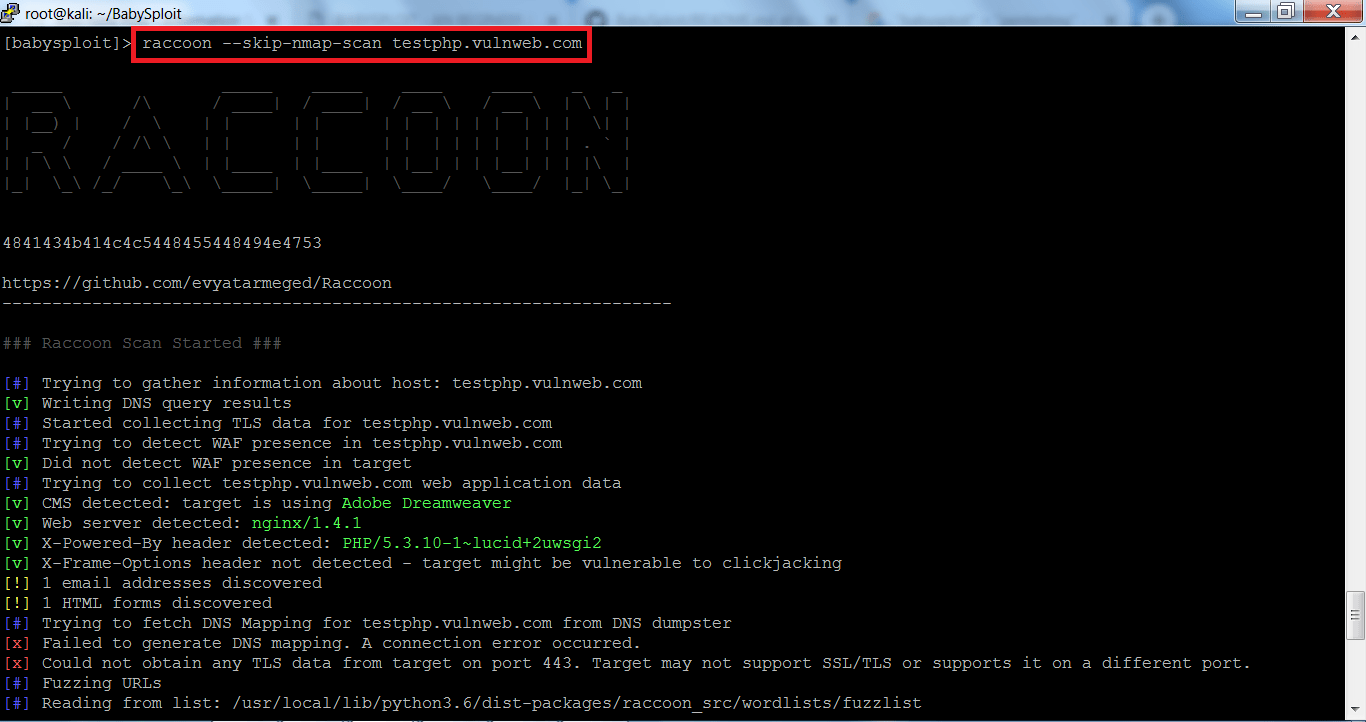
Raccoon Default Scan:-
- For using raccoon type raccoon <Target URL>
- For example – type raccoon testphp.vulnweb.com
===================SNIP======================
======================SNIP==================
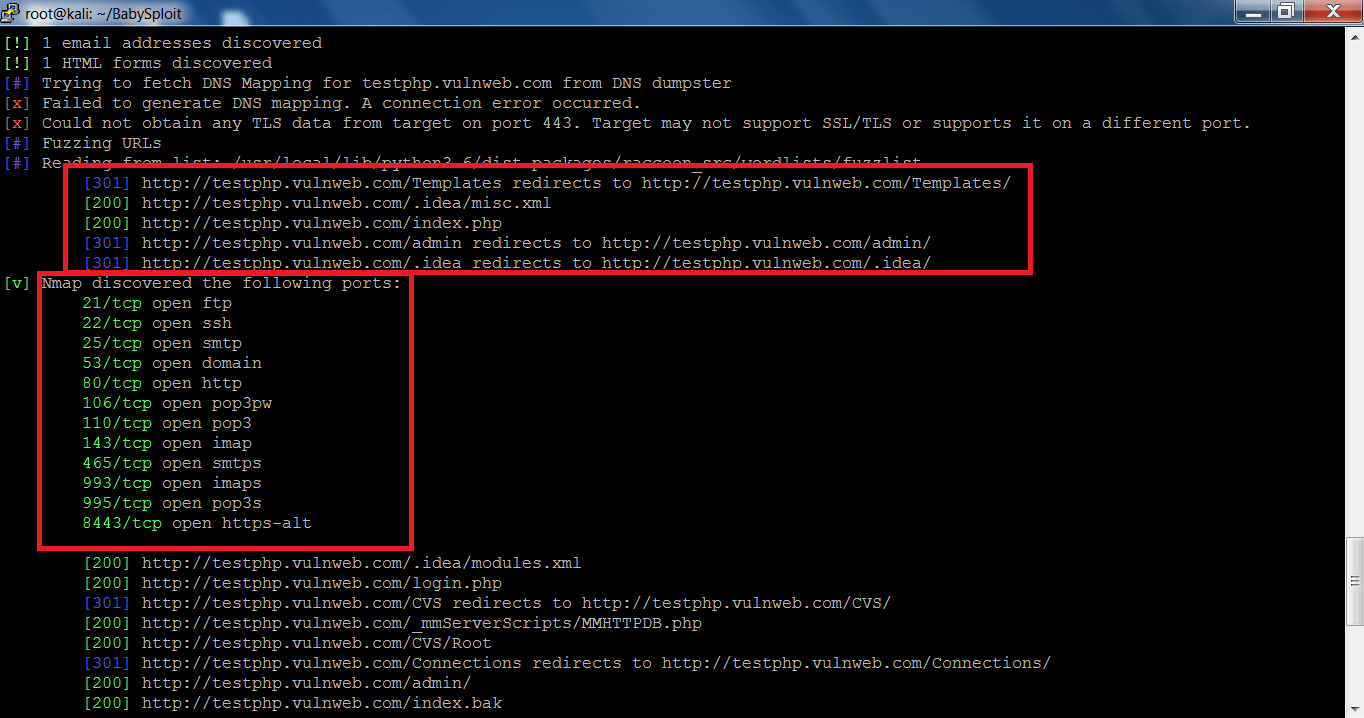
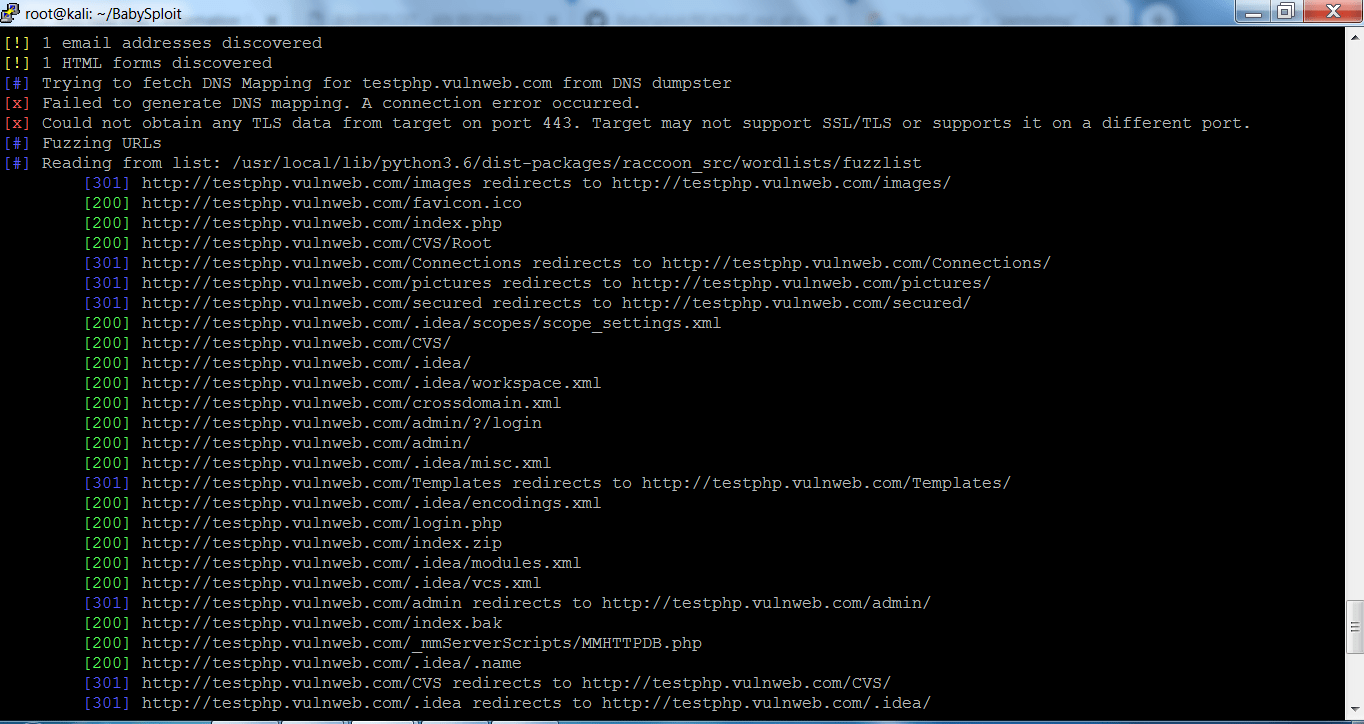
- In the above screen shots, the raccoon has found some the DNS queries, web application URL’s and the language on which the target web application has been used in development.
- The above information can be used in other hacking activities. Getting an admin URL can make the brute force attack on the target website.
Raccoon Full Scan:-
- Type racconn –full-scan testphp.vulnweb.com
=====================SNIP=====================
===================SNIP====================
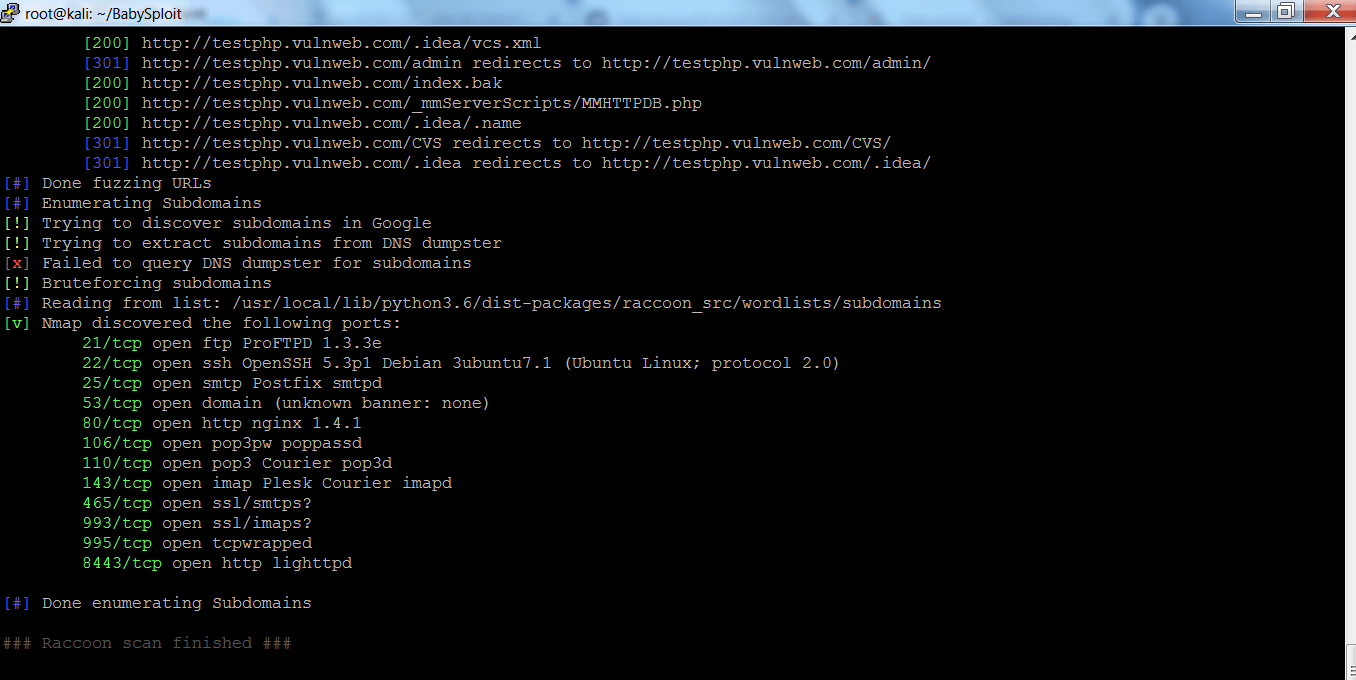
- After executing the above query, using “–full-scan” command will try to gather as much information as raccoon can. The above information could be used by remote attackers in other hacking activities.
- Raccoon has found all the open ports of the target which makes an attacker to easily attack on the website.
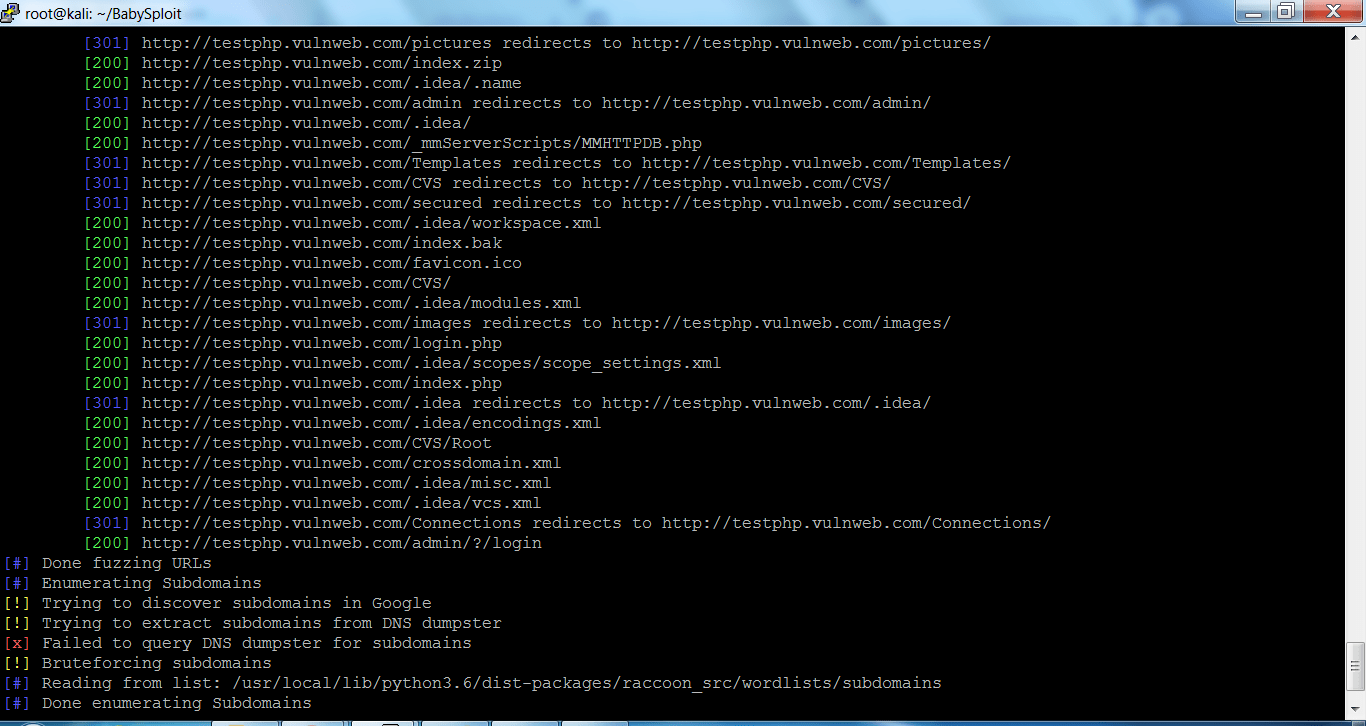
RACCOON SKIP NMAP SCAN:-
- Type raccoon –skip-nmap-scan
====================SNIP=====================
- Using the “–skip-nmap-scan” will not use nmap queries to scan the target. Raccoon will only use the URL fuzzer to grab all the target URL’s.
- All grabbed URL’s by URL fuzzer can be used in creating the phishing pages to take credentials of the target’s clients.
NOW WE WIL TALK ABOUT SEARCHSPLOIT TOOL:-
Searchsploit will give you type of exploits that can be used in exploiting the operating systems, explain ethical hacking experts. Searchsploit consists of big list as listed below.
- Type searchsploit
- Then select the platform (Windows, Mac, Linux).
- In the below example Windows exploits has been selected.
[babysploit]> searchsploit _____ __ / ___/___ ____ ___________/ /_ \__ \/ _ \/ __ `/ ___/ ___/ __ \ ___/ / __/ /_/ / / / /__/ / / / /____/\___/\__,_/_/ \___/_/ /_/ Platform [Windows, Linux, MacOS, PHP, All]: Windows Search: exploit Running Search.. ============================================== Result ============================================== ---------------------------------------------------------------------------------------------------- Title: (Gabriel's FTP Server) Open & Compact FTP Server 1.2 - 'PORT' Remote Denial of Service Platform: windows Path: /usr/share/exploitdb/exploits/windows/dos/12698.py Author: Ma3sTr0-Dz ---------------------------------------------------------------------------------------------------- Title: (Gabriel's FTP Server) Open & Compact FTP Server 1.2 - Authentication Bypass / Directory Traversal SAM Retrieval Platform: windows Path: /usr/share/exploitdb/exploits/windows/remote/27401.py Author: Wireghoul ---------------------------------------------------------------------------------------------------- Title: (Gabriel's FTP Server) Open & Compact FTP Server 1.2 - Full System Access Platform: windows Path: /usr/share/exploitdb/exploits/windows/remote/13932.py Author: Serge Gorbunov ---------------------------------------------------------------------------------------------------- Title: (Gabriel's FTP Server) Open & Compact FTP Server 1.2 - Universal Denial of Service Platform: windows Path: /usr/share/exploitdb/exploits/windows/dos/12741.py Author: Dr_IDE ---------------------------------------------------------------------------------------------------- Title: (Gabriel's FTP Server) Open & Compact FTPd 1.2 - Buffer Overflow (Metasploit) Platform: windows Path: /usr/share/exploitdb/exploits/windows/remote/11742.rb Author: blake ---------------------------------------------------------------------------------------------------- Title: (Gabriel's FTP Server) Open & Compact FTPd 1.2 - Crash (PoC) Platform: windows Path: /usr/share/exploitdb/exploits/windows/dos/11391.py Author: loneferret
----------------------------------------------------------------------------------------------------
--------------------------SNIP OUTPUT-------------------------------------------------------
FIND WORDPRESS VULNERABILITIES:-
For finding the vulnerabilities
- Type wpseku
- By default wpseku select the target google.com. So for changing the target type N
- Then enter your desired target <URL>
- Type haqeacademy.com
[babysploit]> wpseku
== Current Configuration: ==
Target: google.com
[?] Is this configuration correct? [?]
[y\n] n
[?] Enter Target: [?]
> haqueacademy.edu.pk
[?] What type of scan would you like to perform: [?]
[bruteforce login | generic scan | wp plugin] generic scan
[!] Confirm Settings [!]
Target: haqueacademy.edu.pk
Scan Type: Generic
Press ENTER To Confirm
----------------------------------------
_ _ _ ___ ___ ___| |_ _ _
| | | | . |_ -| -_| '_| | |
|_____| _|___|___|_,_|___|
|_| v0.4.0
WPSeku - WordPress Security Scanner
by Momo Outaadi (m4ll0k)
----------------------------------------
[ + ] Target: https://haqueacademy.edu.pk
[ + ] Starting: 07:19:44
[ + ] Server: Apache
[ i ] Checking Full Path Disclosure...
[ + ] Full Path Disclosure: /home/content/21/11179421/html/wp-includes/rss-functions.php
[ i ] Checking wp-config backup file...
[ + ] wp-config.php available at: https://haqueacademy.edu.pk/wp-config.php
[ i ] Checking common files...
[ + ] robots.txt file was found at: https://haqueacademy.edu.pk/robots.txt
[ + ] sitemap.xml file was found at: https://haqueacademy.edu.pk/sitemap.xml
[ + ] readme.html file was found at: https://haqueacademy.edu.pk/readme.html
[ i ] Checking directory listing...
[ i ] Checking wp-loging protection...
[ i ] Checking robots paths...
[ + ] Robots was found at: https://haqueacademy.edu.pk/robots.txt
----------------------------------------
User-agent: *
Disallow: /worldsecuritynews/
Allow: /worldsecuritynews/admin-ajax.php
----------------------------------------
[ i ] Checking WordPress version...
[ + ] Running WordPress version: 4.9.8
| Not found vulnerabilities
[ i ] Passive enumeration themes...
[ + ] Name: haqueacademy
[ i ] Checking themes changelog...
[ i ] Checking themes full path disclosure...
[ i ] Checking themes license...
[ i ] Checking themes readme...
[ i ] Checking themes directory listing...
[ i ] Checking theme vulnerabilities...
| Not found vulnerabilities
[ i ] Passive enumeration plugins...
[ + ] Name: custom-facebook-feed-pro
[ i ] Checking plugins changelog...
[ i ] Checking plugins full path disclosure...
[ i ] Checking plugins license...
[ i ] Checking plugins readme...
[ i ] Checking plugins directory listing...
[ i ] Checking plugin vulnerabilities...
b'{"error":"Not found"}'
| Not found vulnerabilities
[ i ] Enumerating users...
-------------------------
| ID | Username | Login |
-------------------------
| 0 | admin | admin |
| 1 | admin | None |
| 2 | | admin |
-------------------------
CREATE PHISHING PAGES USING BLACKEYE TOOL:-
Normal user can easily create phishing pages using this tool. Blackeye.
- For creating phishing page, type blackeye
- Then select any of the listed social media platforms type <social media platform number>
- In below example we have chosen facebook by typing 2
[babysploit]> blackeye Availble Templates [1] Instagram [2] Facebook [3] Snapchat [4] Twitter [5] GitHub [6] Google [7] Spotify [8] Netflix [9] PayPal [10] Origin [11] Steam [12] Yahoo! [13] LinkedIn [14] Protonmail [15] WordPress [16] Microsoft [17] IGFollowers [18] eBay [19] Pinterest [20] CryptoCurrency [21] Verizon [22] DropBox [23] Adobe ID [24] Shopify [25] FB Messenger [26] GitLab [27] Twitch [28] MySpace [29] Badoo [30] VK [31] Yandex [32] devianART [33] Custom Please Choose A Number To Host Template: [?]> 2 Loading facebook Enter A Custom Subdomain [?]> www.testing.com Starting Server at www.testing.com.serveo.net... Logs Can Be Found In sites/facebook/ip.txt and sites/facebook/usernames.txt PHP 7.2.3-1 Development Server started at Sat Nov 24 07:42:12 2018 Listening on https://127.0.0.1:80 Document root is /root/BabySploit/sites/facebook Press Ctrl-C to quit. The authenticity of host 'serveo.net (159.89.214.31)' can't be established. RSA key fingerprint is SHA256:07jcXlJ4SkBnyTmaVnmTpXuBiRx2+Q2adxbttO9gt0M. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'serveo.net,159.89.214.31' (RSA) to the list of known hosts. Hi there Press g to start a GUI session and ctrl-c to quit. Warning: no TLS certificate available for www.testing.com.serveo.net. You won't be able to use HTTPS, only HTTP. Forwarding HTTP traffic from https://www.testing.com.serveo.net HTTP request from 120.59.146.150 to https://www.testing.com.serveo.net/ HTTP request from 120.59.146.150 to https://www.testing.com.serveo.net/robots.txt [Sat Nov 24 07:42:52 2018] 127.0.0.1:51672 [302]: / [Sat Nov 24 07:42:52 2018] 127.0.0.1:51674 [404]: /robots.txt - No such file or directory HTTP request from 120.59.146.150 to https://www.testing.com.serveo.net/login.html [Sat Nov 24 07:42:53 2018] 127.0.0.1:51676 [200]: /login.html HTTP request from 120.59.146.150 to https://www.testing.com.serveo.net/ [Sat Nov 24 07:43:30 2018] 127.0.0.1:51678 [302]: / HTTP request from 120.59.146.150 to https://www.testing.com.serveo.net/login.html [Sat Nov 24 07:43:31 2018] 127.0.0.1:51680 [200]: /login.html HTTP request from 120.59.146.150 to https://www.testing.com.serveo.net/osd.xml [Sat Nov 24 07:43:49 2018] 127.0.0.1:51682 [404]: /osd.xml - No such file or directory HTTP request from 120.59.146.150 to https://www.testing.com.serveo.net/login.html [Sat Nov 24 07:44:20 2018] 127.0.0.1:51684 [200]: /login.html HTTP request from 120.59.146.150 to https://www.testing.com.serveo.net/osd.xml [Sat Nov 24 07:44:34 2018] 127.0.0.1:51686 [404]: /osd.xml - No such file or directory
- After creating the subdomain, a fake phishing page has been created. The Most common attacks are done using phishing pages as per the research done by ethical hacking group of International Institute of Cyber Security.
- In the above screen shot, a phishing has been created. These phishing are the most common attacks.
- Most of the users get these phishing pages via their mails/mobile chatting applications, according to ethical hacking courses.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.