Twitter is most popular social network platform nowdays. In Twitter users post their messages and interact with anyone which are known as tweets. Normally if you want to take information of any twitter user you will definitely check his twitter handler. But there are many options to analyse all the details of twitter account easily with the help of tool called tinfoleak. Tinfoleak is an complete open source tool used in analyzing Twitter handlers, mention ethical hacking teachers.
According to ethical hacking researcher of international institute of cyber security says that tinfoleak can be used while investigating any person.
Tinfoleak is written by Vicente Aguilera Diaz. The tool comes for windows and for linux platform. For showing you we have tested in Windows. In Linux platform steps are same and UI also.
- For downloading the tool go to : https://github.com/vaguileradiaz/tinfoleak/tree/master/Windows-EXE
- After downloading the tool unzip the tool. You can use any zip softwares for unzipping the tool.
- After unzipping open tinfoleak folder. For using the tinfoleak firstly you have to edit the tinfoleak.py.
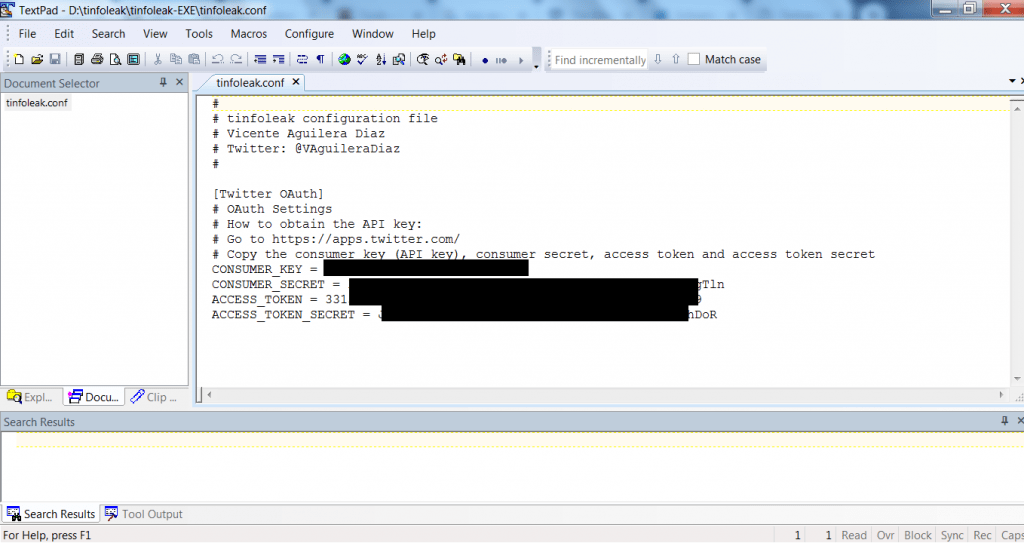
- Enter the access tokens and api key, consumer tokens and api key. Be careful while editing the conf file.
- Use wordpad or textpad to enter the tokens and api keys. Don’t use notepad while entering the access tokens as distort the file format.
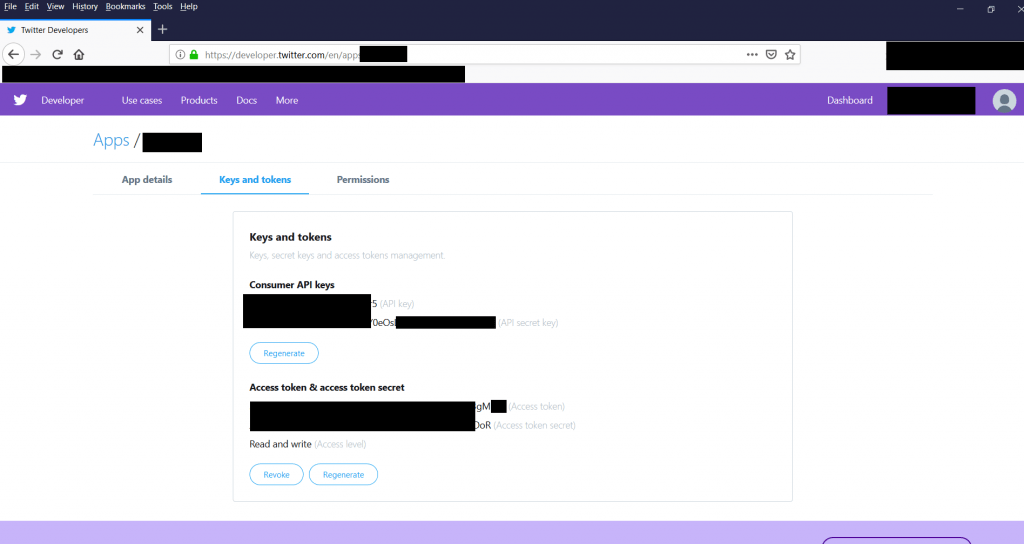
- To get the access tokens, you have to create an developer account in twitter. After creating an account in twiiter. Sign in : https://developer.twitter.com/
- You can get the access tokens from : https://developer.twitter.com/en/docs/basics/authentication/guides/access-tokens
- After entering the consumer tokens and api keys, access tokens and api keys. Save the file and open tinfoleak.exe as shown below.
- Tinfoleak do offer many features to analyse your target. So you can easily create an further scenario for penetrating the target.
- Tinfoleak saves information in html file. For accessing html file go to Output_Records folder inside tinfoleak folder D:\tinfoleak-EXE\Output_Reports. There tinfoleak will save analyse data in html form.
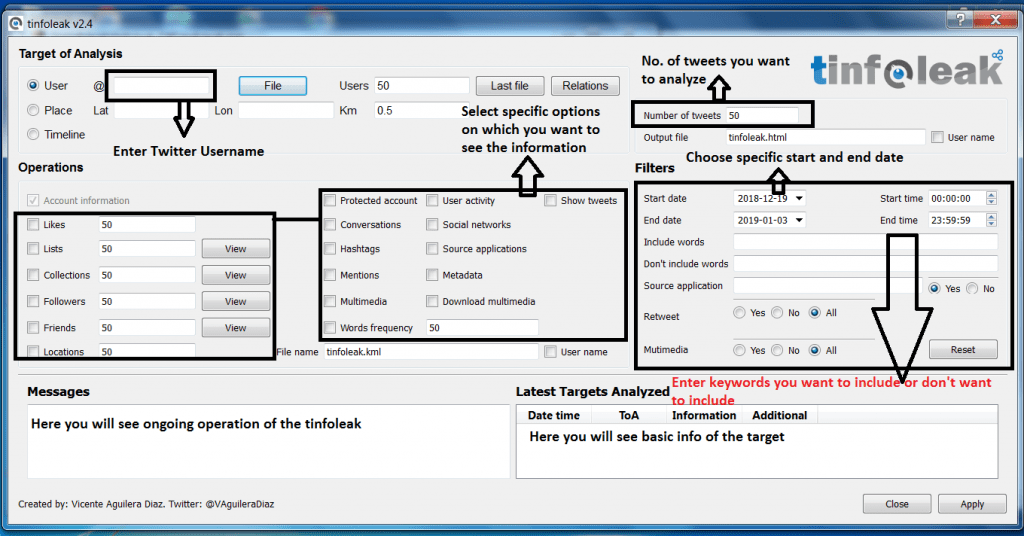
- Enter name carefully, as tinfoleak is case sensitive. Enter only twitter username.
- Tinfoleak gives many options to analyze twitter account of anyone. It shows options like collection, followers, friends, locations, hashtags, metadata and many other information which can be used in other hacking activities.
- Now enter the twitter username of any person you want to search. Type any twitter username. For ex we have analysed Webimprints.
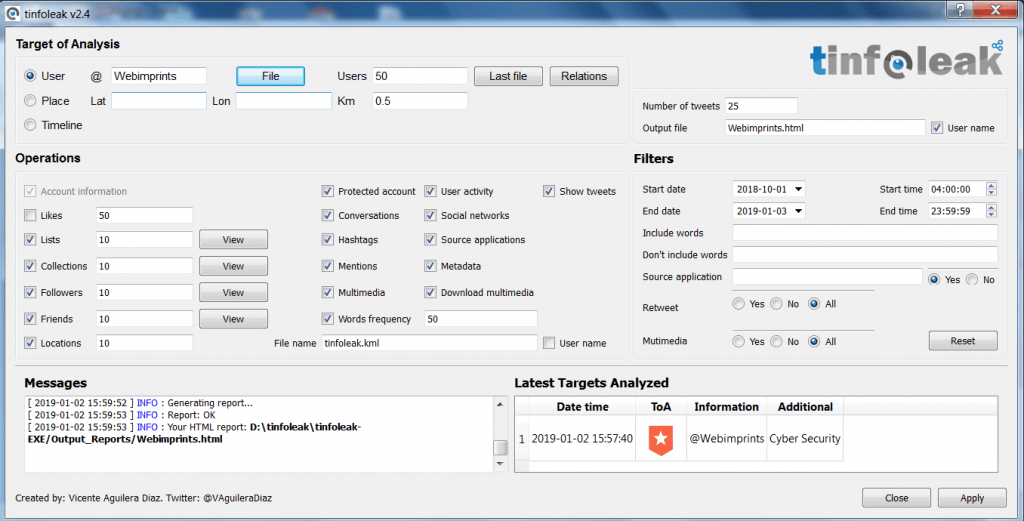
- After entering the username click on apply. As you click on apply, tinfoleak will start scanning the target twitter account. After scanning has complete tinfoleak will save the scanned data in html file.
- Open html file in output_reports folder.

- After opening the HTML file. Tinfoleak shows the basic details of webimprints. It shows the account creation date. It shows the twitter ID, location. It shows the URL of webimprints.
- The above information can be used in initial phase of pentesting.
- Scrolling down the webpage shows more information about webimprints.
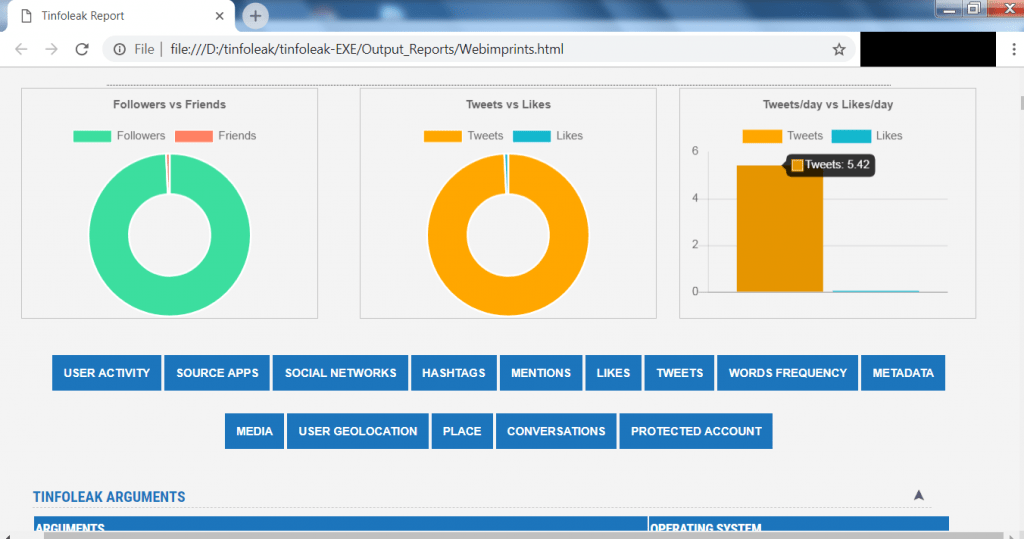
- The above screen shot shows the bar graph of webimprints. It shows the followers vs friends, tweets vs likes and tweets, likes per day.
- Scrolling down shows timeline activity and shared URLs.
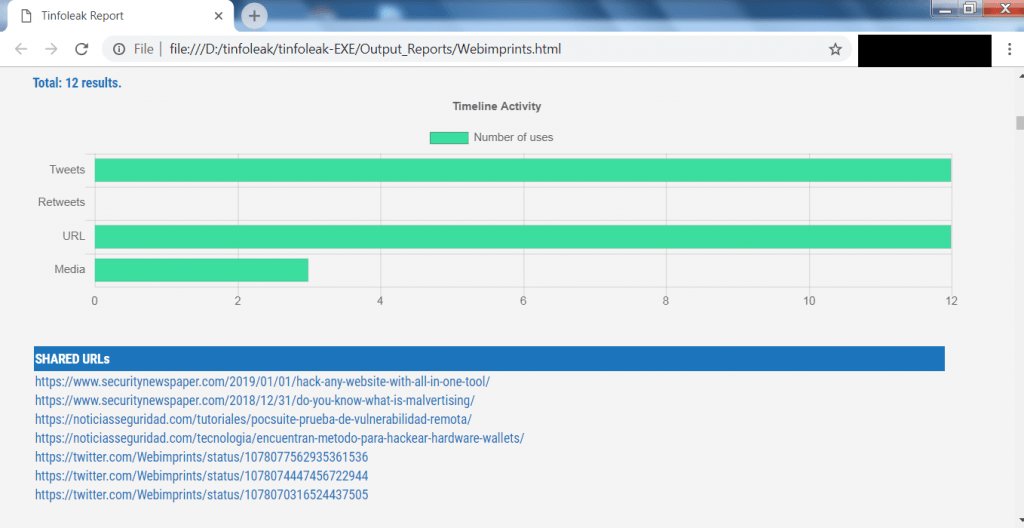
- The above screen shot shows the timeline activity in graph form and shared URLs list. The above URLs can be used in analyzing the target or can be used in other hacking activities.
- Tinfoleak do grab lot of information about webimprints. Further scrolling shows the no. of tweets.
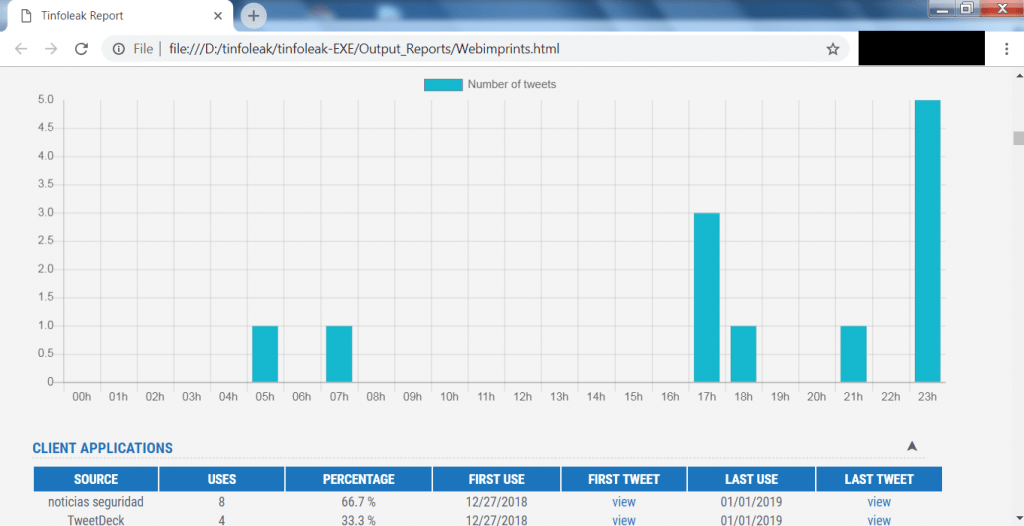
- The above screen shot shows the no. of tweets when webimprints has tweeted. This information can make attacker to know the login time of webimprints.
- The above graph can be used to prepare for session hijacking attacks or can be used in other hacking activities.
- Tinfoleak do gives hashing details of webimprints.
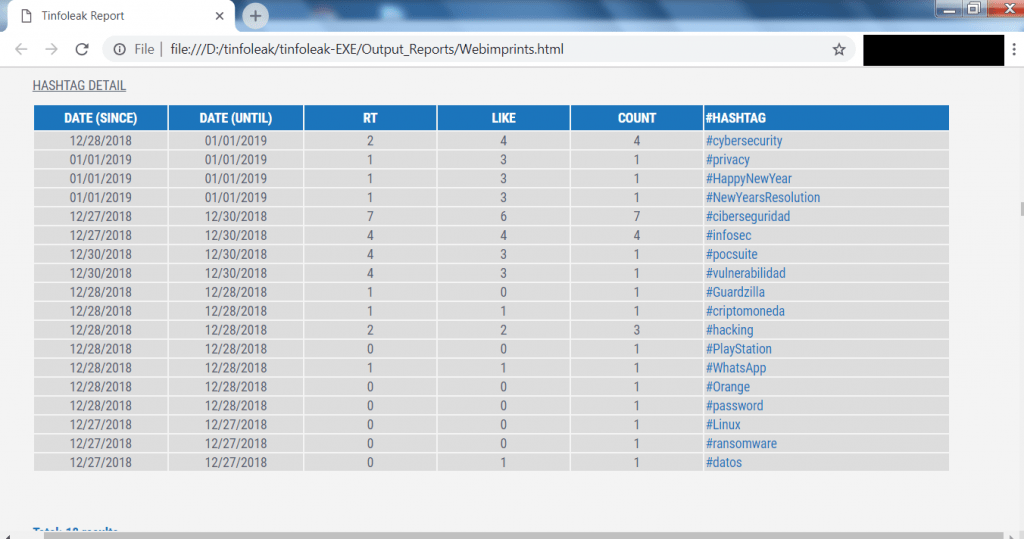
- The above screenshot shows the hash tags which have been used by webimprints while posting on twitter feed. The above hash tags are most related to cyber security tools.
- Further scrolling down shows the words used by webimprints, which can be further used for creating wordlists.
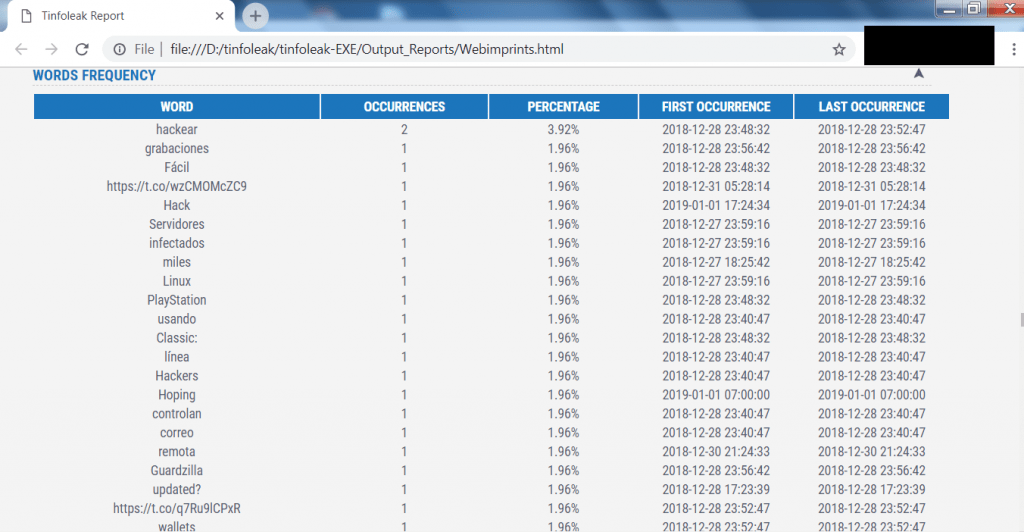
- The above screen shot shows the words that are used mostly by webimprints. The above list can help an attacker to prepare an dictionary attack or can be used in other hacking activities, say ethical hacking specialists.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











