There are many tools available which can find exploits. These tools are more often works on automated way. As they show results in very short period of time. Nowdays most security researchers/ pentesters rely on these tools, ethical hacking teachers assure. Today we will show you a tool which find exploits in automated search.
According to ethical hacking researcher of International Institute of Cyber Security, pompem is very useful tool which are capable of finding exploits. The tool comes handy in initial phase of pentesting.
Pompem is a tool design to search for exploits & vulnerability in automated way. Pompem uses some popular databases to search for exploits. It uses databases like National Vulnerability Database, WPScan Vulnerability Database, PacketStorm security, CXSecurity, ZeroDay, Vulners. These are the standard repositories where all the vulnerabilities are present, as per an ethical hacking investigation.
- The tool has been tested on Kali Linux 2018.4
- For cloning tool : https://github.com/rfunix/Pompem.git
root@kali:/home/iicybersecurity# git clone https://github.com/rfunix/Pompem.git
Cloning into 'Pompem'…
remote: Enumerating objects: 749, done.
remote: Total 749 (delta 0), reused 0 (delta 0), pack-reused 749
Receiving objects: 100% (749/749), 377.13 KiB | 353.00 KiB/s, done.
Resolving deltas: 100% (421/421), done.
- Type cd Pompem
- Type chmod u+x pompem.py
root@kali:/home/iicybersecurity/Pompem# chmod u+x pompem.py
- Type pip install -r requirements.txt
root@kali:/home/iicybersecurity/Pompem# pip install -r requirements.txt
DEPRECATION: Python 2.7 will reach the end of its life on January 1st, 2020. Please upgrade your Python as Python 2.7 won't be maintained after that date. A future version of pip will drop support for Python 2.7.
Collecting requests==2.9.1 (from -r requirements.txt (line 1))
Downloading https://files.pythonhosted.org/packages/b8/f7/3bb4d18c234a8ce7044d5ee2e1082b7d72bf6c550afb8d51ae266dea56f1/requests-2.9.1-py2.py3-none-any.whl (501kB)
100% |████████████████████████████████| 501kB 668kB/s
dropbox 9.3.0 has requirement requests>=2.16.2, but you'll have requests 2.9.1 which is incompatible.
Installing collected packages: requests
Found existing installation: requests 2.18.4
Uninstalling requests-2.18.4:
Successfully uninstalled requests-2.18.4
Successfully installed requests-2.9.1
- Type python pompem.py
- Now e will run pompem
root@kali:/home/iicybersecurity/Pompem# python pompem.py
__________
\______ \____ _____ ______ ____ _____
| ___/ _ \ / \____ \_/ __ \ / \
| | ( <_> ) Y Y \ |_> > ___/| Y Y \
|____| \____/|__|_| / __/ \___ >__|_| /
\/|__| \/ \/
Rafael Francischini (Programmer and Ethical Hacker) - @rfunix
Bruno Fraga (Security Researcher) - @brunofraga_net
Usage: pompem.py [-s/--search <keyword,keyword,keyword,...>]
[--txt Write txt file ]
[--html Write html file ]
Get basic options and Help, use: -h\--help
- Type python pompem.py -s wordpress
- -s is used for search keyword. wordpress is the keyword to search.
root@kali:/home/iicybersecurity/Pompem# python pompem.py -s wordpress
+Results wordpress
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+Date Description Url
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-15 | WordPress Booking Calendar 8.4.3 SQL Injection | https://packetstormsecurity.com/files/151692/WordPress-Booking-Calendar-8.4.3-SQL-Injection.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-14 | WordPress WP-JS-External-Link-Info 2.2.0 Open Redi | https://packetstormsecurity.com/files/151679/WordPress-WP-JS-External-Link-Info-2.2.0-Open-Redirection.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-14 | WordPress Jssor-Slider 3.1.24 Cross Site Request F | https://packetstormsecurity.com/files/151678/WordPress-Jssor-Slider-3.1.24-Cross-Site-Request-Forgery-File-Upload.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-12 | Joomla WordPress Blog 4.8.0 SQL Injection | https://packetstormsecurity.com/files/151626/Joomla-WordPress-Blog-4.8.0-SQL-Injection.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-06 | WordPress YOP Poll 6.0.2 Cross Site Scripting | https://packetstormsecurity.com/files/151559/WordPress-YOP-Poll-6.0.2-Cross-Site-Scripting.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-06 | WordPress WP Live Chat 8.0.18 Cross Site Scripting | https://packetstormsecurity.com/files/151557/WordPress-WP-Live-Chat-8.0.18-Cross-Site-Scripting.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-06 | WordPress wpGoogleMaps 7.10.41 Cross Site Scriptin | https://packetstormsecurity.com/files/151556/WordPress-wpGoogleMaps-7.10.41-Cross-Site-Scripting.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-06 | WordPress Social Networks Auto-Poster 4.2.7 Cross | https://packetstormsecurity.com/files/151554/WordPress-Social-Networks-Auto-Poster-4.2.7-Cross-Site-Scripting.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-06 | WordPress KingComposer 2.7.6 Cross Site Scripting | https://packetstormsecurity.com/files/151552/WordPress-KingComposer-2.7.6-Cross-Site-Scripting.html
- After executing the above query, pompem has used above list databases to find exploits & vulnerabilities in target running wordpress.
- When we open the first URL which is found by pompem in wordpress. It shows :
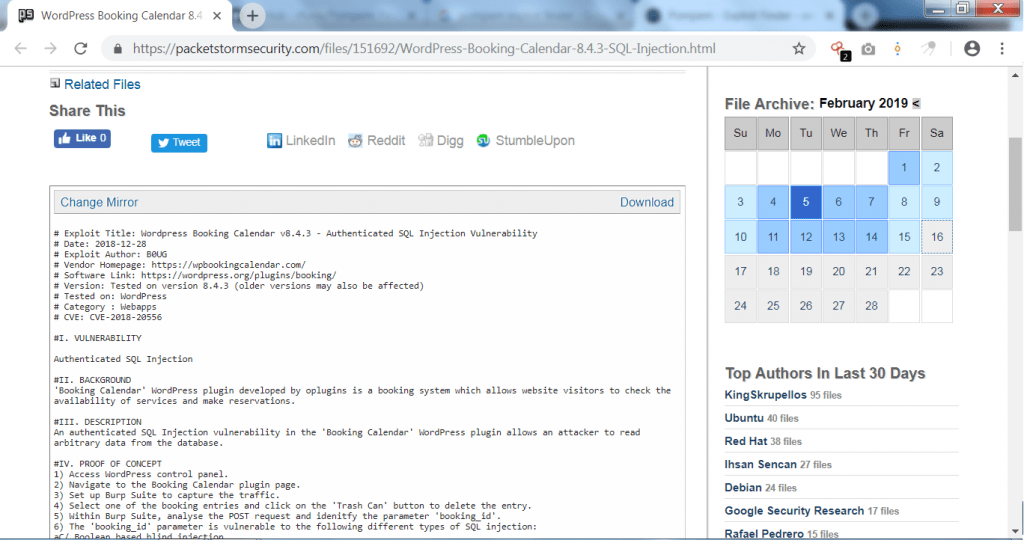
- As you can see the above listed link shows that vulnerability is in the wordpress plugin. This vulnerability can cause sql injection. If the target is using wordpress booking calendar in wordpress site. The attack can be done.
- As mentioned above pompem uses different security databases where all the vulnerabilities are listed which can be done easily.
- These vulnerabilities can be extended to further hacking activities.
- Type python pompem.py -s windows
- -s is the search keyword. windows is the keyword to search for.
root@kali:/home/iicybersecurity/Pompem# python pompem.py -s windows
+Results windows
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+Date Description Url
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-02 | SolarWinds Serv-U FTP 15.1.6 Privilege Escalation | https://packetstormsecurity.com/files/151473/SolarWinds-Serv-U-FTP-15.1.6-Privilege-Escalation.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-01-30 | Microsoft Windows/x86 msiexec.exe Download And Exe | https://packetstormsecurity.com/files/151404/Microsoft-Windows-x86-msiexec.exe-Download-And-Execute-Shellcode.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-01-27 | R 3.4.4 Local Buffer Overflow | https://packetstormsecurity.com/files/151344/R-3.4.4-Local-Buffer-Overflow.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-01-22 | Microsoft Windows VCF Arbitrary Code Execution | https://packetstormsecurity.com/files/151267/Microsoft-Windows-VCF-Arbitrary-Code-Execution.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-01-17 | Windows Debugging 101 | https://packetstormsecurity.com/files/151215/Windows-Debugging-101.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-01-16 | Microsoft Windows .contact Arbitrary Code Executio | https://packetstormsecurity.com/files/151194/Microsoft-Windows-.contact-Arbitrary-Code-Execution.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
- After executing the above query, pompem has find many vulnerabilities regarding windows operating system. As told above pompem uses security databases to find exploits.
- The above vulnerabilities can be used in other hacking activities.
- When we open first URL. It shows :
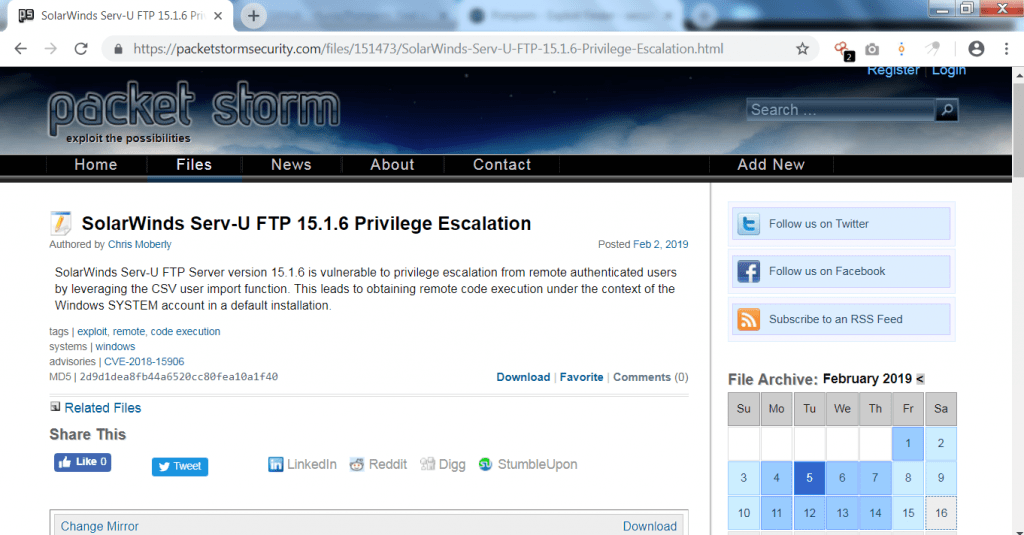
- The above vulnerability shows privilege escalation attack could be done on windows operating system.
- Type python pompem.py -s android –html
- -s is used to search for keyword. Here android is keyword to search for.
- –html is used to save file in html.
root@kali:/home/iicybersecurity/Pompem# python pompem.py -s android --html
+Results android
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+Date Description Url
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-12 | Android Binder VMA Use-After-Free | https://packetstormsecurity.com/files/151637/Android-Binder-VMA-Use-After-Free.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2019-02-12 | Android Binder fdget() Optimization Use-After-Free | https://packetstormsecurity.com/files/151636/Android-Binder-fdget-Optimization-Use-After-Free.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2018-11-20 | Ricoh myPrint Hardcoded Credentials / Information | https://packetstormsecurity.com/files/150399/Ricoh-myPrint-Hardcoded-Credentials-Information-Disclosure.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2018-11-16 | Everus.org 1.0.9 Second Factor Redirection | https://packetstormsecurity.com/files/150382/Everus.org-1.0.9-Second-Factor-Redirection.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2018-11-13 | Android RSSI Broadcast Information Disclosure | https://packetstormsecurity.com/files/150285/Android-RSSI-Broadcast-Information-Disclosure.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
- After executing the above query pompem has find vulnerabilities which can be used to exploit android users.
- Sometimes if the html file is not opened. Go to Pompem directory and open out.html. Opening its html file.
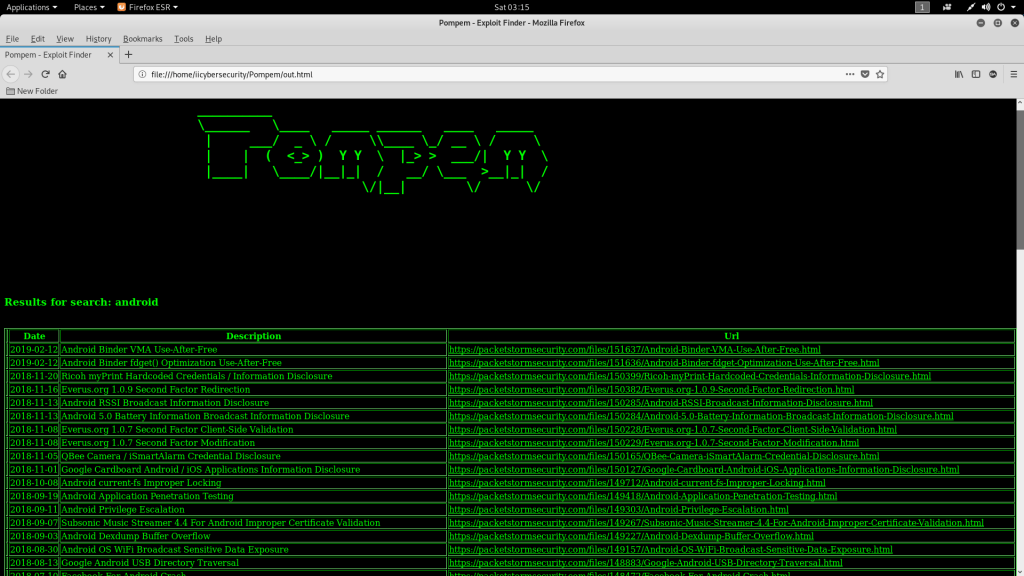
- Opening one of the scanned URL from output :
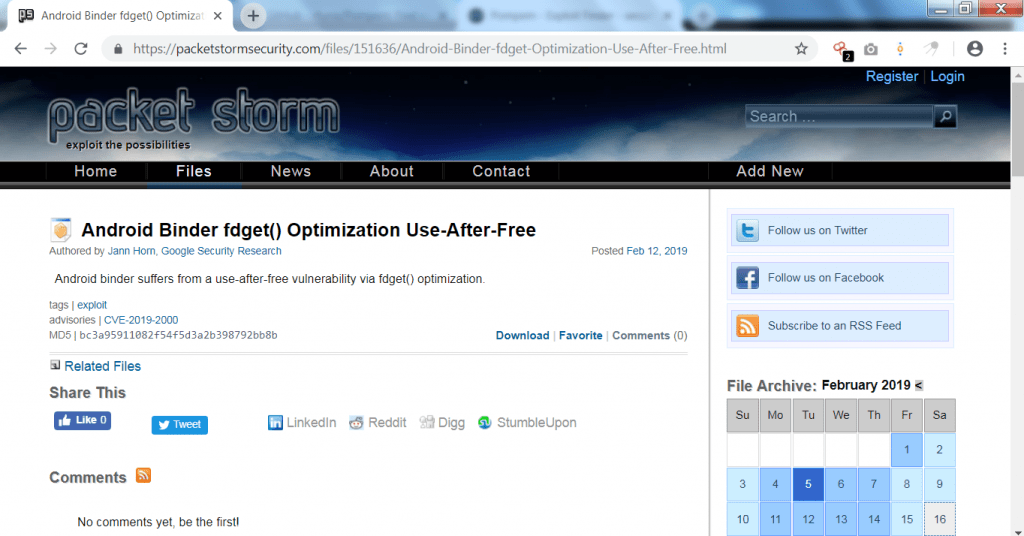
- The above shows the android binder vulnerability which can cause many other possibility of hacking attacks.
- You can also get an txt file. For that type python pompem.py -s android –txt
- -s is used to search for keyword. android is the keyword to search for.
- –txt is used to save file in txt form.
root@kali:/home/iicybersecurity/Pompem# python pompem.py -s android --txt
- For opening the txt file go to pompem directory. open out.txt
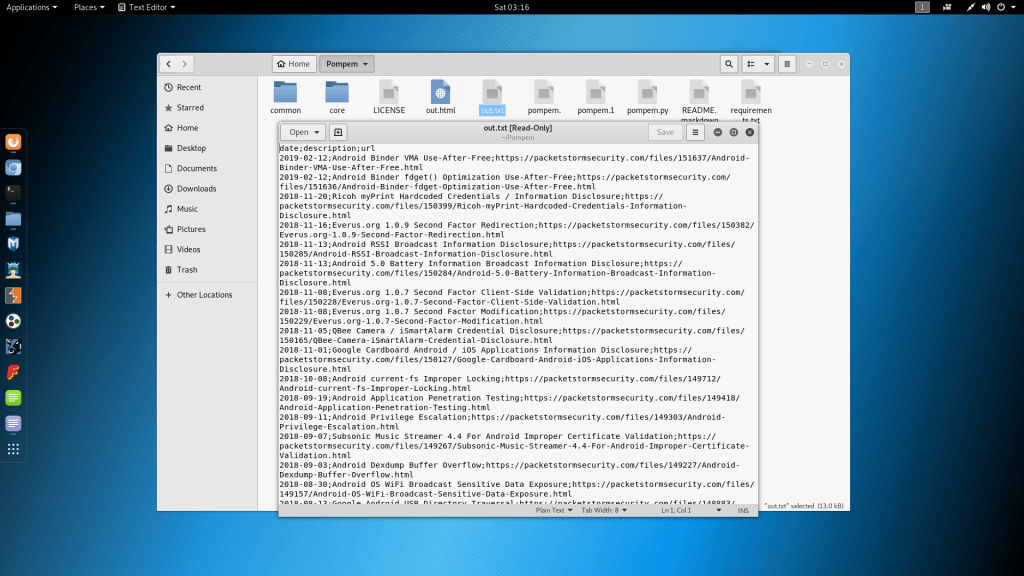
- The above is the list of URL which can be used in other hacking activities.
- Searching on diiferent keywords type python pompem.py -s fortinet
- -s is used to search for keyword. fortinet is the firewall to search for. Fortinet is network firewall used in networks.
root@kali:/home/iicybersecurity/Pompem# python pompem.py -s fortinet
+Results fortinet
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+Date Description Url
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2018-08-05 | Fortinet FortiClient 5.2.3 Local Privilege Escalat | https://packetstormsecurity.com/files/148811/Fortinet-FortiClient-5.2.3-Local-Privilege-Escalation.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2018-01-03 | Fortinet Installer Client 5.6 DLL Hijacking | https://packetstormsecurity.com/files/145625/Fortinet-Installer-Client-5.6-DLL-Hijacking.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2018-01-02 | Fortinet FortiClient Windows Privilege Escalation | https://packetstormsecurity.com/files/145611/Fortinet-FortiClient-Windows-Privilege-Escalation.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2017-12-13 | Fortinet FortiClient VPN Credential Disclosure | https://packetstormsecurity.com/files/145397/Fortinet-FortiClient-VPN-Credential-Disclosure.html
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
- The above query shows some serious vulnerabilities regarding firewall. Opening one of output links :
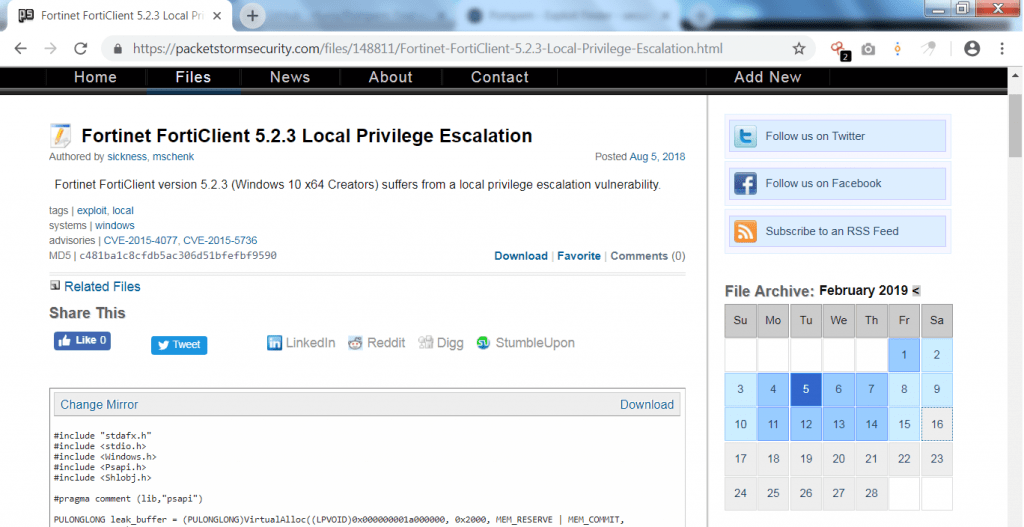
- Opening the links shows vulnerability of local privilege escalation. There are many vulnerabilities which can be used in further hacking activities.
- This tool can be used after Reconnaissance phase. For list of Reconnaissance tools & techniques please refer link over it.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











