As per ethical hacking investigators, Tor is the very much popular for being anonymous over the internet. Tor allows to user to protect user privacy. TOR name origin from The Onion Router. Tor protects the privacy of the user as it does not save any log files. Most of the Government agencies or enforcement law keep an surveillance over the internet like the most popular search engine google. But in tor everything is anonymous. This project was developed in 2002. As Tor consists of huge proxies uses tor relays and nodes to stay anonymous over the internet. Tor creates an tunnel where it bounces an user from different relays, explain ethical hacking experts.
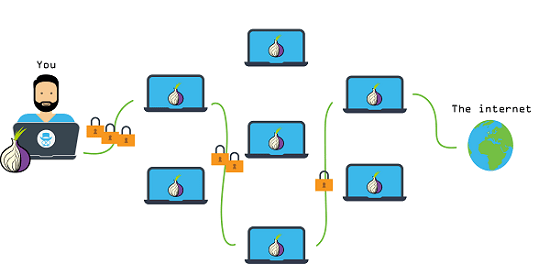
- Hosting tor service is very easy and you can also host your own website on TOR.
According to ethical hacking researcher of International Institute of Cyber Security, creating an custom tor link is not so difficult. This method mostly used by spammers who try to sell irrelevant content on the deep web.
For showing you we are using Kali linux.
Hosting a Web Server in Tor :-
- Before hosting the service on the tor it is recommended to test the Tor default hosting service. For Testing the default service we are using apache server. You can use any web server.
- For starting the server type sudo service apache2 start
root@kali:/home/iicybersecurity# sudo service apache2 restart
- Then for checking if the server has started type ps -ef | grep apache2
root@kali:/var/lib/tor/hidden_service# ps -ef | grep apache2
root 1514 1 0 Dec25 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1515 1514 0 Dec25 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1516 1514 0 Dec25 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1517 1514 0 Dec25 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1518 1514 0 Dec25 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1519 1514 0 Dec25 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1520 1514 0 Dec25 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1589 1514 0 00:09 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1591 1514 0 00:09 ? 00:00:00 /usr/sbin/apache2 -k start
root 1719 1565 0 01:13 pts/3 00:00:00 grep apache2
- After executing the above command . Go to tor configuration page and edit the torrc.
- Type cd /etc/tor
- Then type ls
- Type nano torrc
- Then press ctrl+w and type location-hidden
- In that section remove # from HiddenService as shown below.
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
#HiddenServiceDir /var/lib/tor/other_hidden_service/
#HiddenServicePort 80 127.0.0.1:80
#HiddenServicePort 22 127.0.0.1:22
root@kali:~# cd /etc/tor
root@kali:/etc/tor#
root@kali:/etc/tor# ls
torrc torrc.save torsocks.conf
root@kali:/etc/tor# nano torrc
Configuration file for a typical Tor user
Last updated 9 October 2013 for Tor 0.2.5.2-alpha.
(may or may not work for much older or much newer versions of Tor.)
#
Lines that begin with "## " try to explain what's going on. Lines
that begin with just "#" are disabled commands: you can enable them
by removing the "#" symbol.
#
See 'man tor', or https://www.torproject.org/docs/tor-manual.html,
for more options you can use in this file.
#
Tor will look for this file in various places based on your platform:
https://www.torproject.org/docs/faq#torrc
Tor opens a socks proxy on port 9050 by default -- even if you don't
configure one below. Set "SocksPort 0" if you plan to run Tor only
as a relay, and not make any local application connections yourself.
SocksPort 9050 # Default: Bind to localhost:9050 for local connections.
SocksPort 192.168.0.1:9100 # Bind to this address:port too.
Entry policies to allow/deny SOCKS requests based on IP address.
First entry that matches wins. If no SocksPolicy is set, we accept
all (and only) requests that reach a SocksPort. Untrusted users who
can access your SocksPort may be able to learn about the connections
you make.
SocksPolicy accept 192.168.0.0/16
SocksPolicy reject *
Logs go to stdout at level "notice" unless redirected by something
else, like one of the below lines. You can have as many Log lines as
you want.
#
We advise using "notice" in most cases, since anything more verbose
may provide sensitive information to an attacker who obtains the logs.
#
Send all messages of level 'notice' or higher to /var/log/tor/notices.log
Log notice file /var/log/tor/notices.log
Send every possible message to /var/log/tor/debug.log
Log debug file /var/log/tor/debug.log
Use the system log instead of Tor's logfiles
Log notice syslog
To send all messages to stderr:
Log debug stderr
Uncomment this to start the process in the background… or use
--runasdaemon 1 on the command line. This is ignored on Windows;
see the FAQ entry if you want Tor to run as an NT service.
RunAsDaemon 1
The directory for keeping all the keys/etc. By default, we store
things in $HOME/.tor on Unix, and in Application Data\tor on Windows.
DataDirectory /var/lib/tor
The port on which Tor will listen for local connections from Tor
controller applications, as documented in control-spec.txt.
ControlPort 9051
If you enable the controlport, be sure to enable one of these
authentication methods, to prevent attackers from accessing it.
HashedControlPassword 16:872860B76453A77D60CA2BB8C1A7042072093276A3D701AD684053EC4C
CookieAuthentication 1
######### This section is just for location-hidden services
Once you have configured a hidden service, you can look at the
contents of the file "…/hidden_service/hostname" for the address
to tell people.
#
HiddenServicePort x y:z says to redirect requests on port x to the
address y:z.
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
#HiddenServiceDir /var/lib/tor/other_hidden_service/
#HiddenServicePort 80 127.0.0.1:80
#HiddenServicePort 22 127.0.0.1:22
########## This section is just for relays
#
See https://www.torproject.org/docs/tor-doc-relay for details.
Required: what port to advertise for incoming Tor connections.
ORPort 9001
If you want to listen on a port other than the one advertised in
ORPort (e.g. to advertise 443 but bind to 9090), you can do it as
follows. You'll need to do ipchains or other port forwarding
yourself to make this work.
ORPort 443 NoListen
ORPort 127.0.0.1:9090 NoAdvertise
The IP address or full DNS name for incoming connections to your
relay. Leave commented out and Tor will guess.
Address noname.example.com
If you have multiple network interfaces, you can specify one for
outgoing traffic to use.
OutboundBindAddress 10.0.0.5
A handle for your relay, so people don't have to refer to it by key.
Nickname ididnteditheconfig
Define these to limit how much relayed traffic you will allow. Your
own traffic is still unthrottled. Note that RelayBandwidthRate must
be at least 20 KB.
Note that units for these config options are bytes per second, not bits
per second, and that prefixes are binary prefixes, i.e. 2^10, 2^20, etc.
RelayBandwidthRate 100 KB # Throttle traffic to 100KB/s (800Kbps)
RelayBandwidthBurst 200 KB # But allow bursts up to 200KB/s (1600Kbps)
Use these to restrict the maximum traffic per day, week, or month.
Note that this threshold applies separately to sent and received bytes,
not to their sum: setting "4 GB" may allow up to 8 GB total before
hibernating.
#
Set a maximum of 4 gigabytes each way per period.
AccountingMax 4 GB
Each period starts daily at midnight (AccountingMax is per day)
AccountingStart day 00:00
Each period starts on the 3rd of the month at 15:00 (AccountingMax
is per month)
AccountingStart month 3 15:00
Administrative contact information for this relay or bridge. This line
can be used to contact you if your relay or bridge is misconfigured or
something else goes wrong. Note that we archive and publish all
descriptors containing these lines and that Google indexes them, so
spammers might also collect them. You may want to obscure the fact that
it's an email address and/or generate a new address for this purpose.
ContactInfo Random Person
You might also include your PGP or GPG fingerprint if you have one:
ContactInfo 0xFFFFFFFF Random Person
Uncomment this to mirror directory information for others. Please do
if you have enough bandwidth.
DirPort 9030 # what port to advertise for directory connections
If you want to listen on a port other than the one advertised in
DirPort (e.g. to advertise 80 but bind to 9091), you can do it as
follows. below too. You'll need to do ipchains or other port
forwarding yourself to make this work.
DirPort 80 NoListen
DirPort 127.0.0.1:9091 NoAdvertise
Uncomment to return an arbitrary blob of html on your DirPort. Now you
can explain what Tor is if anybody wonders why your IP address is
contacting them. See contrib/tor-exit-notice.html in Tor's source
distribution for a sample.
DirPortFrontPage /etc/tor/tor-exit-notice.html
Uncomment this if you run more than one Tor relay, and add the identity
key fingerprint of each Tor relay you control, even if they're on
different networks. You declare it here so Tor clients can avoid
using more than one of your relays in a single circuit. See
https://www.torproject.org/docs/faq#MultipleRelays
However, you should never include a bridge's fingerprint here, as it would
break its concealability and potentionally reveal its IP/TCP address.
MyFamily $keyid,$keyid,…
A comma-separated list of exit policies. They're considered first
to last, and the first match wins. If you want to replace
the default exit policy, end this with either a reject : or an
accept :. Otherwise, you're augmenting (prepending to) the
default exit policy. Leave commented to just use the default, which is
described in the man page or at
https://www.torproject.org/documentation.html
#
Look at https://www.torproject.org/faq-abuse.html#TypicalAbuses
for issues you might encounter if you use the default exit policy.
#
If certain IPs and ports are blocked externally, e.g. by your firewall,
you should update your exit policy to reflect this -- otherwise Tor
users will be told that those destinations are down.
#
For security, by default Tor rejects connections to private (local)
networks, including to your public IP address. See the man page entry
for ExitPolicyRejectPrivate if you want to allow "exit enclaving".
#
ExitPolicy accept *:6660-6667,reject *:* # allow irc ports but no more
ExitPolicy accept *:119 # accept nntp as well as default exit policy
ExitPolicy reject : # no exits allowed
Bridge relays (or "bridges") are Tor relays that aren't listed in the
main directory. Since there is no complete public list of them, even an
ISP that filters connections to all the known Tor relays probably
won't be able to block all the bridges. Also, websites won't treat you
differently because they won't know you're running Tor. If you can
be a real relay, please do; but if not, be a bridge!
BridgeRelay 1
By default, Tor will advertise your bridge to users through various
mechanisms like https://bridges.torproject.org/. If you want to run
a private bridge, for example because you'll give out your bridge
address manually to your friends, uncomment this line:
PublishServerDescriptor 0
- After completing the whole process open an new terminal and type tor
root@kali:/home/iicybersecurity# tor
Dec 26 00:02:50.045 [notice] Tor 0.3.4.9 (git-cf9f4bf3cf8b43bb) running on Linux with Libevent 2.1.8-stable, OpenSSL 1.1.1a, Zlib 1.2.11, Liblzma 5.2.2, and Libzstd 1.3.4.
Dec 26 00:02:50.047 [notice] Tor can't help you if you use it wrong! Learn how to be safe at https://www.torproject.org/download/download#warning
Dec 26 00:02:50.047 [warn] Tor was compiled with zstd 1.3.5, but is running with zstd 1.3.4. For safety, we'll avoid using advanced zstd functionality.
Dec 26 00:02:50.092 [notice] Read configuration file "/etc/tor/torrc".
Dec 26 00:02:50.197 [notice] Scheduler type KIST has been enabled.
Dec 26 00:02:50.197 [notice] Opening Socks listener on 127.0.0.1:9050
Dec 26 00:02:50.000 [notice] Parsing GEOIP IPv4 file /usr/share/tor/geoip.
Dec 26 00:02:51.000 [notice] Parsing GEOIP IPv6 file /usr/share/tor/geoip6.
Dec 26 00:02:51.000 [warn] You are running Tor as root. You don't need to, and you probably shouldn't.
Dec 26 00:02:51.000 [notice] Bootstrapped 0%: Starting
Dec 26 00:02:53.000 [notice] Starting with guard context "default"
Dec 26 00:02:53.000 [notice] Bootstrapped 80%: Connecting to the Tor network
Dec 26 00:02:53.000 [notice] Bootstrapped 85%: Finishing handshake with first hop
Dec 26 00:02:54.000 [notice] Bootstrapped 90%: Establishing a Tor circuit
Dec 26 00:02:55.000 [notice] Tor has successfully opened a circuit. Looks like client functionality is working.
Dec 26 00:02:55.000 [notice] Bootstrapped 100%: Done
- For check if tor is running or not type ps -ef | grep tor
root@kali:/home/iicybersecurity# ps -ef | grep tor
iicyber+ 1004 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-udisks2-volume-monitor
iicyber+ 1024 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-mtp-volume-monitor
iicyber+ 1032 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-gphoto2-volume-monitor
iicyber+ 1043 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-afc-volume-monitor
iicyber+ 1048 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-goa-volume-monitor
iicyber+ 1160 845 0 Dec25 ? 00:00:00 /usr/lib/tracker/tracker-store
iicyber+ 1233 845 0 Dec25 ? 00:00:01 /usr/lib/evolution/evolution-calendar-factory
iicyber+ 1273 1233 0 Dec25 ? 00:00:01 /usr/lib/evolution/evolution-calendar-factory-subprocess --factory all --bus-name org.gnome.evolution.dataserver.Subprocess.Backend.Calendarx1233x2 --own-path /org/gnome/evolution/dataserver/Subprocess/Backend/Calendar/1233/2
iicyber+ 1282 845 0 Dec25 ? 00:00:00 /usr/lib/evolution/evolution-addressbook-factory
iicyber+ 1295 1282 0 Dec25 ? 00:00:00 /usr/lib/evolution/evolution-addressbook-factory-subprocess --factory all --bus-name org.gnome.evolution.dataserver.Subprocess.Backend.AddressBookx1282x2 --own-path /org/gnome/evolution/dataserver/Subprocess/Backend/AddressBook/1282/2
root 1549 1545 10 00:02 pts/2 00:00:02 tor
root 1570 1565 0 00:03 pts/3 00:00:00 grep tor
- Then go to another location of tor for opening onion link. For that type cd /var/lib/tor/hidden_service
- Then type ls
- Type cat hostname
root@kali:/etc/tor# cd /var/lib/tor/hidden_service
root@kali:/var/lib/tor/hidden_service# ls
hostname private_key
root@kali:/var/lib/tor/hidden_service# cat hostname
bzak2gopn2llmsnv.onion
- Copy the URL of onion and open that URL in tor browser as shown below.
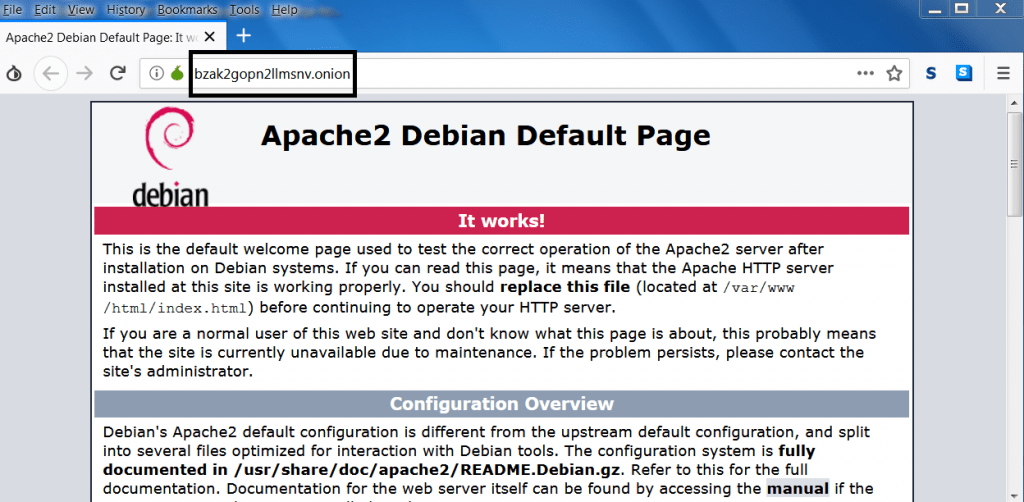
- As you can see above, onion URL is working using apache server.
Create an Custom Onion URL :-
- You can also create an custom onion URLs with tool called eschalot.
- Eschalot is the tool used for generating the custom onion names. It uses brute force method to generate custom names.
- Eschalot can be used on any Linux distros. For showing we are using Kali Linux for generating the names.
- You can also enter desired name in characters but not all th
- Type git clone https://github.com/ReclaimYourPrivacy/eschalot.git
- Then type ls
- Type cd eschalot
- Type ls
- Type make for installing eschalot.
root@kali:/home/iicybersecurity/Downloads# git clone https://github.com/ReclaimYourPrivacy/eschalot.git
Cloning into 'eschalot'…
remote: Enumerating objects: 76, done.
remote: Total 76 (delta 0), reused 0 (delta 0), pack-reused 76
Unpacking objects: 100% (76/76), done.
root@kali:/home/iicybersecurity/Downloads# ls
eschalot
root@kali:/home/iicybersecurity/Downloads# cd eschalot/
root@kali:/home/iicybersecurity/Downloads/eschalot# ls
CHANGELOG eschalot.c LICENSE Makefile nouns.txt README top1000.txt top150adjectives.txt top400nouns.txt typecard.c worgen.c
root@kali:/home/iicybersecurity/Downloads/eschalot# make
cc -std=c99 -O2 -fPIC -finline-functions -Wall -W -Wunused -pedantic -Wpointer-arith -Wreturn-type -Wstrict-prototypes -Wmissing-prototypes -Wshadow -Wcast-qual -Wextra -o eschalot eschalot.c -lpthread -lssl -lcrypto
In function ‘setoptions’,
inlined from ‘main’ at eschalot.c:172:2:
eschalot.c:788:4: warning: ‘strncpy’ specified bound 17 equals destination size [-Wstringop-truncation]
strncpy(prefix, optarg, ONION_LENP1);
^~~~~~~~
cc -std=c99 -O2 -fPIC -finline-functions -Wall -W -Wunused -pedantic -Wpointer-arith -Wreturn-type -Wstrict-prototypes -Wmissing-prototypes -Wshadow -Wcast-qual -Wextra -o worgen worgen.c
- After installing the eschalot type ./eschalot -vct4 -p null
- ./escalot is the tool which will be used for creating the custom onion link.
- -vct is used for eschalot default wordlist.
- 4 is the number of cpu cores.
- null will work as prefix. You can enter any of the alphabets which is used for generating the onion link. You can type aaa or adc any alphabet.
- The above command will generate the onion link with RSA keys. The link will generate continuously. For stopping the generation of the onion links enter ctrl+c
- RSA keys is used for authentication during SSL session. This key is part of public key that is generally used in SSL certificates.
root@kali:/home/iicybersecurity/Downloads/eschalot# ./eschalot -vct4 -p null
Verbose, continuous, no digits, 4 threads, prefixes 4-4 characters long.
Thread #1 started.
Thread #2 started.
Thread #3 started.
Thread #4 started.
Running, collecting performance data…
Found a key for null (4) - nullbhldupqqrafc.onion
nullbhldupqqrafc.onion
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDSrpomuQTqtI4UCeyX+FBsq2+2UOCn/GrIg9eht7Yoh6glh0d/
u334RPTeBThuDQVAJITT0YnlTKfIhFOzHhMhg9xfpK5vNRK9/5tD0WaYZyO1qv0x
NN25NCQ2S/eCNkas1sDGIfw801no/tpB8+42cZQDNJFqjYdEobilUR2v0QIEAQAb
1QKBgGRjZ+B2CLlnt4IB+oUbLNQJ9L0bOyv9lwusmWt6wccfYVmq57YiJZP9cgi7
fj89FVn/g7QBARXe040y56D22dabItE+19Je63nlmbNmaVF5ZIJSybRrBsYioGlO
5eKLUHg+uBa3uaxKawlpeGxG/EVxHSJ7aFT6I/J3mjw+7m1NAkEA+5z7x4hGYsdP
z6ndtoRmyokMSFHhHPgm+qOc9ffWrUWh8RjaUwLtOgyjaGxOAlcg8ZPjYNDiBe1L
QuDC7lkoxwJBANZa7pQAH6YtfecllQWqAGwtYx2B/k7C9Ou3wVoTazCfG8Gvar4Q
79GAZrMnrtNSoN7FL3uV6WCBGcVSiS+ROqcCQCj80R7kxBDIXH7GND5EcVuwPyO5
V4mqSHmQfsznva/eX0oQ/Bqtq5QN8mCoxkxpIullLa2ucWmuFwgezRf9w8kCQQCF
+JO5G+ggRcVuCkbCzJhnm9sJUuG6Bn6iWATd5gl82j1iIpF3iSgqB9u8nTR76qUq
r4/A4DfK1z/gziUp0Ou/AkBhiq8CZxN38lYwZoEd9IKb80FJXVpY5rsh8gWDrgMx
aH1ZV5hKR7s+E1Nm2WW7weTqNwhjxDA9kD+4SOB0nQ2r
-----END RSA PRIVATE KEY-----
Found a key for null (4) - nullqvpp4spoef4i.onion
nullqvpp4spoef4i.onion
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQC0B0pNNJ+Q2xXqag/S8GPHoOcTZXdkngQtu5e/qZfB3r7eqWPn
2BAxRvQt+cy3LBxLjTRnjWa8PVOuzPE4oHeBWEpnOfH5Tfpdmc4KV3XxxS4C+pVI
3WXnR2Gjwis6z0DrkuvQgE7BsSTY195koC3r1bfi9u7YzOgtBC55wnE2kwIEAQS5
6QKBgAjSZ6GGmDh2Ss/aqBods3lwWr39mrYbErN1r6lpq8uAZ/bJN1Md7SZKph6m
o6+qfOuxC4ORX+zKU48u/+dntOl6Fu4VsybIE5ku30NvEkcrPsnDb0UAKNepMfmn
fK5AJ+0svD5YvWVT79BFfbUZglS/Hwo9vXAsob3hYwSNtEl5AkEA7/9EFpdN6N6V
gSDcvSi8VGCczArlniOCaZTY3ehmSP2xenWJ1zNM0cMfFLR1hZux2XCK/lugrKxy
erb8fLEjFQJBAMAIXROgz5RxsbAd21zIUsRjKRWk/8GU9MxrVR0RGX4bwmEno8NJ
WdHfCkpR/t6qOSfzRjrIP4ESbzk5xKuYfQcCQADIK/KjoguRMMy3JxX4v/ZwwvQc
7nkZ61zJMjU0Gsjn1PiVymq9nwM3TP1bScs1kppnqIxabhkrWxrPQXmEmNECQFF/
Tsb27slzvpUCm6wgw19fI7sGONlxwSqDnLsdbPav9JkLirTjlwvByKaJVNRd1Tvp
U/miFyKhBsckleBa3BcCQQDJ+hE9j3BtCjlnqGxVTxof/aOjPeAOD/Rrm9dG3CzD
eEVYW+ykqsHo894LMu+7ljHuNr4BT+fUvtEI7TpDndOw
-----END RSA PRIVATE KEY-----
Found a key for null (4) - nullauzvxlunyne5.onion
nullauzvxlunyne5.onion
-----BEGIN RSA PRIVATE KEY-----
MIICXgIBAAKBgQCrfAEBl2g6QRIPGzgAh0SqMALu+imguVaA/FgK1zpnnAEQfoiE
BNCuqc/fw4Q3yseDwZE2pLqWOn6iUDOkgUHpALOy5WcS/FkY1Ps9VzHaWJn8kc9q
uBpLP+hbot+3KucV0Q+JFqlgfVkUkFBwSpefuWQUtXl0YA0XSayqaGiGBwIEAQp9
gQKBgFAXUTMMUzJltvuTs3Iw1TMONnsaappLvnIoFRsrNspD1n42qBE/9o1qJ523
Fe0D7YQbx0xDE7uZMU5Ayy3jaqGvkoGwdaUNLjv1DGn+DyoYDEoE5bmprPzbnYgq
IAW83E6c59jfr6erBaz3WQtr9/KpgTufoZ/FpFzYV68yy1fpAkEA5C4TfvCdliXw
CBiG9rRfgNAkHGsRSmXQCHziI6LOcFV4Kn3y3T2Xq4bcsGyHBd127WvMFGheaQyq
vVrgq3oOswJBAMBkWi/DRCZB1Q7orWxGv5TRbwWI66Mmj+k5j9+q1mxnVUoTwper
5wGuhu/XGELMUlYFD5ZxjDFqg77FLtTxlV0CQQCJQc1xXDEIfGeoTxSeHI1fTQvI
ri9rlzMToHZCw9DnNAre1VUFE4Twyh4uiVsgsbFP4b09yGyBVv5stB5l8hwXAkBD
UcZxvD0GBdndxayfmMH0BvO1M/FyupIdXzjCaRGnvKEOEgBwxdiw/aH+DJFCIGkT
aCsSZSqgIaLLeFgHollZAkEAjLtHAviEMzcCUFo3Z+RyOHKRf7wY7bpojqIqhoTl
LupiINVe84dE9iMq7ICOezMA1bvyGaQvXFYCpBcTu1BRdQ==
-----END RSA PRIVATE KEY-----
- After executing the above command some of the onion links with RSA keys has been generated. This links can be used to host on TOR.
- The above RSA keys and onion links are only for testing purposes. Used them with cautions.
Adding An Onion Address to Tor Service :-
- Now for hosting generated link which earlier have been created using eschalot.
- Stop the running tor service. For that open terminal where tor is running and then press ctrl+c for stopping tor.
- For checking if the tor has stopped type ps -ef | grep tor
root@kali:/home/iicybersecurity# ps -ef | grep tor
iicyber+ 1004 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-udisks2-volume-monitor
iicyber+ 1024 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-mtp-volume-monitor
iicyber+ 1032 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-gphoto2-volume-monitor
iicyber+ 1043 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-afc-volume-monitor
iicyber+ 1048 845 0 Dec25 ? 00:00:00 /usr/lib/gvfs/gvfs-goa-volume-monitor
iicyber+ 1160 845 0 Dec25 ? 00:00:00 /usr/lib/tracker/tracker-store
iicyber+ 1233 845 0 Dec25 ? 00:00:01 /usr/lib/evolution/evolution-calendar-factory
iicyber+ 1273 1233 0 Dec25 ? 00:00:01 /usr/lib/evolution/evolution-calendar-factory-subprocess --factory all --bus-name org.gnome.evolution.dataserver.Subprocess.Backend.Calendarx1233x2 --own-path /org/gnome/evolution/dataserver/Subprocess/Backend/Calendar/1233/2
iicyber+ 1282 845 0 Dec25 ? 00:00:00 /usr/lib/evolution/evolution-addressbook-factory
iicyber+ 1295 1282 0 Dec25 ? 00:00:00 /usr/lib/evolution/evolution-addressbook-factory-subprocess --factory all --bus-name org.gnome.evolution.dataserver.Subprocess.Backend.AddressBookx1282x2 --own-path /org/gnome/evolution/dataserver/Subprocess/Backend/AddressBook/1282/2
- As you can see the tor service is not running. Now you have to copy the eschalot generated onion RSA keys into the tor hidden_service.
- For that type cd /var/lib/tor/hidden_service
- Then type ls
- Type rm hostname
root@kali:/home/iicybersecurity/Downloads/eschalot# cd /var/lib/tor/hidden_service/
root@kali:/var/lib/tor/hidden_service# ls
hostname private_key
root@kali:/var/lib/tor/hidden_service# rm hostname
root@kali:/var/lib/tor/hidden_service# ls
private_key
- Now you have to edit the private_key. Open private key and enter the RSA key which is generated eschalot into the private_key.
- Copy the entire RSA key from where you have downloaded the eschalot. Copy entire key from
—–BEGIN RSA PRIVATE KEY—– to
—–END RSA PRIVATE KEY—– as shown below. - Type nano private_key copy the key.
- Then open another terminal
- And type TOR to start tor in the Kali Linux.
root@kali:/var/lib/tor/hidden_service# nano private_key
GNU nano 2.9.8 private_key
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDSrpomuQTqtI4UCeyX+FBsq2+2UOCn/GrIg9eht7Yoh6glh0d/
u334RPTeBThuDQVAJITT0YnlTKfIhFOzHhMhg9xfpK5vNRK9/5tD0WaYZyO1qv0x
NN25NCQ2S/eCNkas1sDGIfw801no/tpB8+42cZQDNJFqjYdEobilUR2v0QIEAQAb
1QKBgGRjZ+B2CLlnt4IB+oUbLNQJ9L0bOyv9lwusmWt6wccfYVmq57YiJZP9cgi7
fj89FVn/g7QBARXe040y56D22dabItE+19Je63nlmbNmaVF5ZIJSybRrBsYioGlO
5eKLUHg+uBa3uaxKawlpeGxG/EVxHSJ7aFT6I/J3mjw+7m1NAkEA+5z7x4hGYsdP
z6ndtoRmyokMSFHhHPgm+qOc9ffWrUWh8RjaUwLtOgyjaGxOAlcg8ZPjYNDiBe1L
QuDC7lkoxwJBANZa7pQAH6YtfecllQWqAGwtYx2B/k7C9Ou3wVoTazCfG8Gvar4Q
79GAZrMnrtNSoN7FL3uV6WCBGcVSiS+ROqcCQCj80R7kxBDIXH7GND5EcVuwPyO5
V4mqSHmQfsznva/eX0oQ/Bqtq5QN8mCoxkxpIullLa2ucWmuFwgezRf9w8kCQQCF
+JO5G+ggRcVuCkbCzJhnm9sJUuG6Bn6iWATd5gl82j1iIpF3iSgqB9u8nTR76qUq
r4/A4DfK1z/gziUp0Ou/AkBhiq8CZxN38lYwZoEd9IKb80FJXVpY5rsh8gWDrgMx
aH1ZV5hKR7s+E1Nm2WW7weTqNwhjxDA9kD+4SOB0nQ2r
-----END RSA PRIVATE KEY-----
- After updating the private key, go to directory tor/hidden_services.
root@kali:/home/iicybersecurity/Downloads/eschalot# ls
CHANGELOG eschalot.c Makefile README top150adjectives.txt typecard.c worgen.c
eschalot LICENSE nouns.txt top1000.txt top400nouns.txt worgen
root@kali:/home/iicybersecurity/Downloads/eschalot# cd /var/lib/tor/hidden_service/
root@kali:/var/lib/tor/hidden_service# ls
hostname nullbhldupqqrafc.onion private_key
- As you can see tor has added the onion link to its service. Now open Tor browser and enter the onion link as shown below.
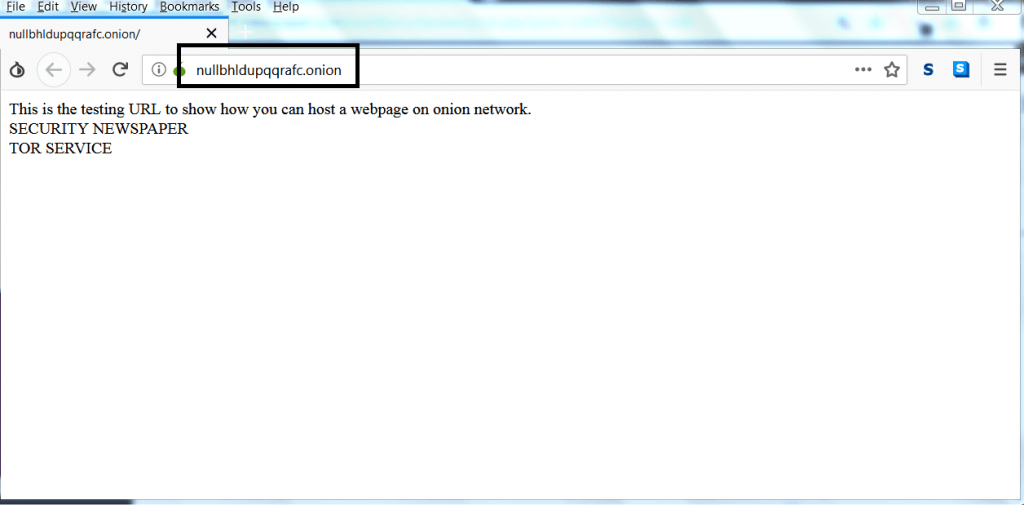
- The Tor service has added the onion link. You can also enter create your own onion link and host to TOR network.
Be cautious while hosting on TOR. If you host any illegal material. Law enforcement may catch that can put you in legal trouble, according to ethical hacking courses.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











