Core dumps or memory dumps are created when program is executed. A dump consists of modules or work flow that how program is working. In most of the cases dumps are used for files backups and directories, explain ethical hacking investigators. It contains an image processing memory of the applications. Sometimes when a process closes unexpected an core dump is created by operating system. That core dump saves all the information that how process was working. Today we are talking about tool called procdump,
Ethical hacking researcher of international institute of cyber security says procdump is useful in taking dump & analyzing any process running on Linux.
Procdump is a tool created by Microsoft developers from sysinternals suite. Now this tool has been integrated in Linux. This tool creates dumps of running processes in Linux. This tool was build using Microsoft libraries as this tool is redesign of Microsoft tool called Procdump which runs on cmd. Its an free utility created by microsoft which helps in Windows debugging but soon after they also created for Linux, as per ethical hacking courses. For testing we have used Ubuntu 16.04.
- For cloning tool type git clone https://github.com/Microsoft/ProcDump-for-Linux.git
root@ubuntu:/home/iicybersecurity/Downloads# git clone https://github.com/Microsoft/ProcDump-for-Linux.git
Cloning into 'ProcDump-for-Linux'…
remote: Enumerating objects: 303, done.
remote: Total 303 (delta 0), reused 0 (delta 0), pack-reused 303
Receiving objects: 100% (303/303), 272.61 KiB | 261.00 KiB/s, done.
Resolving deltas: 100% (170/170), done.
Checking connectivity… done.
- Then type cd ProcDump-for-Linux
- Then type sudo apt-get update and sudo apt-get install procdump
- Type sudo sh -c ‘echo “deb [arch=amd64] https://packages.microsoft.com/repos/microsoft-ubuntu-xenial-prod xenial main” > /etc/apt/sources.list.d/microsoft.list’
- The above command adds the public key of microsoft feed manager.
root@ubuntu:/home/iicybersecurity/Downloads/ProcDump-for-Linux#
sudo sh -c 'echo "deb [arch=amd64] https://packages.microsoft.com/repos/microsoft-ubuntu-xenial-prod xenial main" > /etc/apt/sources.list.d/microsoft.list'
The program 'curl' is currently not installed. You can install it by typing:
apt install curl
gpg: no valid OpenPGP data found.
- If it shows above error type sudo apt-get update and then type sudo apt-get install curl
root@ubuntu:/home/iicybersecurity/Downloads/ProcDump-for-Linux# apt-get install curl
Reading package lists… Done
Building dependency tree
Reading state information… Done
Some packages could not be installed. This may mean that you have
requested an impossible situation or if you are using the unstable
distribution that some required packages have not yet been created
or been moved out of Incoming.
The following information may help to resolve the situation:
The following packages have unmet dependencies:
curl : Depends: libcurl3-gnutls (= 7.47.0-1ubuntu2) but 7.47.0-1ubuntu2.8 is to be installed
E: Unable to correct problems, you have held broken packages.
- If it shows above curl error. Type sudo apt-get install libcurl3-gnutls=7.47.0-1ubuntu2
root@ubuntu:/home/iicybersecurity/Downloads/ProcDump-for-Linux# sudo apt-get install libcurl3-gnutls=7.47.0-1ubuntu2
Reading package lists… Done
Building dependency tree
Reading state information… Done
The following packages will be DOWNGRADED:
libcurl3-gnutls
0 upgraded, 0 newly installed, 1 downgraded, 0 to remove and 0 not upgraded.
Need to get 183 kB of archives.
After this operation, 2,048 B disk space will be freed.
Do you want to continue? [Y/n] Y
Get:1 https://us.archive.ubuntu.com/ubuntu xenial/main amd64 libcurl3-gnutls amd64 7.47.0-1ubuntu2 [183 kB]
Fetched 183 kB in 3s (60.2 kB/s)
dpkg: warning: downgrading libcurl3-gnutls:amd64 from 7.47.0-1ubuntu2.8 to 7.47.0-1ubuntu2
(Reading database … 184169 files and directories currently installed.)
Preparing to unpack …/libcurl3-gnutls_7.47.0-1ubuntu2_amd64.deb …
Unpacking libcurl3-gnutls:amd64 (7.47.0-1ubuntu2) over (7.47.0-1ubuntu2.8) …
Processing triggers for libc-bin (2.23-0ubuntu10) …
Setting up libcurl3-gnutls:amd64 (7.47.0-1ubuntu2) …
Processing triggers for libc-bin (2.23-0ubuntu10) …
- Then type sudo apt-get install curl
root@ubuntu:/home/iicybersecurity/Downloads/ProcDump-for-Linux# sudo apt-get install curl
Reading package lists… Done
Building dependency tree
Reading state information… Done
The following NEW packages will be installed:
curl
0 upgraded, 1 newly installed, 0 to remove and 0 not upgraded.
Need to get 138 kB of archives.
After this operation, 337 kB of additional disk space will be used.
Get:1 https://us.archive.ubuntu.com/ubuntu xenial/main amd64 curl amd64 7.47.0-1ubuntu2 [138 kB]
Fetched 138 kB in 2s (57.5 kB/s)
Selecting previously unselected package curl.
(Reading database … 184169 files and directories currently installed.)
Preparing to unpack …/curl_7.47.0-1ubuntu2_amd64.deb …
Unpacking curl (7.47.0-1ubuntu2) …
Processing triggers for man-db (2.7.5-1) …
Setting up curl (7.47.0-1ubuntu2) …
- Then type
sudo sh -c ‘echo “deb [arch=amd64] https://packages.microsoft.com/repos/microsoft-ubuntu-xenial-prod xenial main” > /etc/apt/sources.list.d/microsoft.list’ - Type procdump -h
root@ubuntu:/home/iicybersecurity/Downloads/ProcDump-for-Linux# procdump -h
ProcDump v1.0.1 - Sysinternals process dump utility
Copyright (C) 2017 Microsoft Corporation. All rights reserved. Licensed under the MIT license.
Mark Russinovich, Mario Hewardt, John Salem, Javid Habibi
Monitors a process and writes a dump file when the process exceeds the
specified criteria.
Usage: procdump [OPTIONS…] TARGET
OPTIONS
-h Prints this help screen
-C CPU threshold at which to create a dump of the process from 0 to 100 * nCPU
-c CPU threshold below which to create a dump of the process from 0 to 100 * nCPU
-M Memory commit threshold in MB at which to create a dump
-m Trigger when memory commit drops below specified MB value.
-n Number of dumps to write before exiting
-s Consecutive seconds before dump is written (default is 10)
-d Writes diagnostic logs to syslog
TARGET must be exactly one of these:
-p pid of the process
- Type sudo procdump -p 1409
- -p is used for entering process id.
- For getting processes id type ps -ef or ps for watching what process are running in Linux system.
root@ubuntu:/home/iicybersecurity/Downloads/ProcDump-for-Linux# sudo procdump -p 1409
ProcDump v1.0.1 - Sysinternals process dump utility
Copyright (C) 2017 Microsoft Corporation. All rights reserved. Licensed under the MIT license.
Mark Russinovich, Mario Hewardt, John Salem, Javid Habibi
Monitors a process and writes a dump file when the process exceeds the
specified criteria.
Process: Xorg (1409)
CPU Threshold: n/a
Commit Threshold: n/a
Threshold Seconds: 10
Number of Dumps: 1
Press Ctrl-C to end monitoring without terminating the process.
[00:26:04 - INFO]: Core dump 1 generated: Xorg_time_2019-01-25_21:09:07.1409
- After executing the above query procdump has created dump file. The dump file will be in same directory where procdump is installed.
- If you open files by typing cat Xorg_time_2019-01-25_21:09:07.1409 it will open as :-
VJ▒ڽV VJ▒ڽV▒ڽVl▒I▒ڽV▒L▒IڽV▒▒I&ڽVp9▒G`▒▒GVڽVfڽVvڽV▒ڽV▒ڽV▒▒▒Gp▒▒Gk▒G▒ڽVP▒H▒ڽVڽV@▒▒G0▒▒Gg▒IFڽVVڽVfڽV▒▒▒G`▒▒G▒G▒▒GVJ▒▒▒GPh▒G▒z▒G▒ڽVeVJڽV&ڽV▒H▒I ▒H0▒▒G▒l▒Io▒G▒ڽV;I▒ڽV▒ڽV▒ڽV▒ڽV▒vVJ▒ڽVڽVڽV&ڽV6ڽVFڽVVڽVfڽVp▒G▒hVJ▒ڽV@#VJ▒ڽV▒ڽV'VJ▒ڽV▒OJڽVڽV&ڽV6ڽV▒H▒j▒G0Q▒Gp▒▒G@▒G▒ڽV▒▒I▒V`I0▒G▒o▒G@▒H▒▒I▒▒GڽV▒I▒▒▒GFڽVVڽVfڽV@h▒I▒ڽV▒ڽV@o▒H▒VJ▒▒▒G▒bJ▒ڽV▒▒:IpVJH▒I▒▒:I6ڽVFڽVp▒▒GP▒▒G▒▒▒G▒ڽV`▒▒G▒▒▒G▒ڽVx▒G▒ڽV▒ڽV▒?HڽVڽV▒▒G6ڽVFڽVP▒▒GfڽVI▒I▒ڽV@ VJPVJ▒ڽV▒ڽV▒▒G▒ڽVPdVJp▒▒GڽVk▒G6ڽVFڽV0▒▒GfڽV▒T▒Ge▒G0p▒G▒ڽV ▒▒Gp▒:I▒ڽV▒▒:I`▒:I`iVJڽVP▒:I`56Ip▒▒G▒)H@▒▒G▒{▒G▒ڽV▒▒G▒ڽV▒ڽV▒ڽV▒▒G▒▒▒G@▒▒GڽVڽV&ڽV6ڽVFڽV ▒▒GfڽVvڽVp▒▒G▒ڽV▒Y`I▒ڽV▒▒▒G▒▒:I▒▒GP▒`H▒▒▒GЉ▒G&▒V6▒VF▒V▒▒If▒V@▒▒G▒▒▒G▒ϡI<H▒J▒▒V▒▒V▒▒V ▒▒G I▒I▒OH@▒`H [VJP▒▒IVڽVp▒▒GvڽV@▒▒I`g▒G▒ڽV▒ڽV▒▒▒Gp▒▒GVJ▒ڽV▒▒HڽV▒bVJ▒u▒G▒▒G▒jVJ▒▒GvڽV▒ڽV▒▒G▒ڽV0▒▒G▒▒▒G▒ڽV▒ڽV@▒I▒J▒IڽV@▒▒G h▒GFڽVVڽV▒▒GvڽV▒ڽ▒G ▒▒G▒▒▒G1VJ▒▒:I▒▒:I▒t▒GڽVڽV▒▒:I0gVJFڽVVڽVfڽV▒▒▒G▒▒▒G▒H▒ڽV▒[VJ▒:I`▒:I▒▒▒G▒▒▒G▒▒▒G ڽV |▒Gp▒▒G0▒▒IV ڽVf ڽVv ڽV@▒H▒ ڽV▒ ڽV▒▒:I▒ ڽV▒ ڽV▒ ڽV▒ ڽV▒]VJpp▒G&!ڽV6!ڽVF!ڽV▒vVJf!ڽV▒▒▒G▒!ڽV▒!ڽV▒!ڽV▒!ڽV▒!ڽV▒▒▒G▒~Jpj▒IЩ:I"ڽV&"ڽV6"ڽVF"ڽV▒▒:If"ڽV▒i▒G`▒▒G▒▒G@▒:I`▒:I▒"ڽV▒:I▒"ڽV▒3J#ڽV▒▒G AH6#ڽV@▒▒GV#ڽVf#ڽV0▒▒G▒#ڽVVJ0▒▒G]▒G▒#ڽV▒#ڽV▒▒:I{`I$ڽV▒▒▒G▒Y`I`▒▒GpϡIV$ڽVPwVJp▒G▒V`I▒$ڽV`▒▒G.Jp?Hp▒:Ip|▒G▒$ڽV@СI%ڽVpL▒I6%ڽV▒▒GpVJ0v▒G▒vVJ@▒:I▒%ڽV▒%ڽV▒%ڽV▒w▒G▒▒Gp▒Hpo▒G&ڽV0▒▒G&&ڽV6&ڽV0▒Jp▒Hf&ڽV▒I▒▒G▒&ڽV▒▒▒G@MJ▒V▒G@w▒H▒K`H'ڽV▒▒:I&'ڽV6'ڽVF'ڽV▒▒▒Gf'ڽV▒▒▒G▒'ڽV▒'ڽV▒'ڽV▒'ڽV▒'ڽV▒'ڽV▒'ڽV▒'ڽV(ڽV(ڽV▒▒H6(ڽVF(ڽV▒▒▒I0@▒G@▒H▒(ڽV▒(ڽV▒(ڽV▒(ڽV`]VJ▒(ڽV▒dH▒(ڽV▒~▒G▒▒▒G@▒H6)ڽVF)ڽVV)ڽVP▒H▒▒G▒)ڽV@▒▒G▒)ڽV`▒▒G▒)ڽV▒)ڽV▒)ڽV▒)ڽV*ڽV*ڽV&*ڽV /L▒▒▒GV*ڽVf*ڽV▒:I▒*ڽV▒}▒V6▒V▒▒V▒▒▒V0▒▒V@▒▒V▒▒V▒▒V▒▒▒V▒▒V▒▒▒V▒▒▒V`i▒V▒i▒V0r▒V@u▒V▒q▒V▒j▒V▒j▒V▒l▒VPm▒Vpv▒V▒v▒V▒v▒V@w▒V▒w▒V x▒V▒x▒V@z▒Vp▒▒V▒▒V`▒▒V▒3▒V`9▒V▒8▒V▒3▒V@9▒V▒8▒V9▒V:▒V▒9▒V▒▒V@▒▒VP▒▒V▒▒V0▒▒V▒▒▒V▒▒▒V▒▒▒V▒▒▒V▒▒V0▒▒VP▒▒V▒▒Vp▒V▒▒V@▒V▒▒V@▒V▒ ▒V0 ▒V▒!▒V`!▒Vp▒▒VЛ▒V▒V ▒▒VЫ▒V ▒▒V▒▒VП▒V▒߽V▒߽V▒▒▒V▒▒▒V▒▒▒V▒▒▒V▒▒V`▒▒V▒▒▒V0▒▒V▒▒▒V▒▒▒V▒▒▒V▒P▒VPQ▒V▒Q▒V▒S▒VPU▒V▒N▒VpN▒VPW▒V▒W▒V▒W▒VpW▒VH▒V▒H▒V`H▒V▒S▒V@H▒VS▒V`C▒V`S▒V▒C▒V▒C▒VD▒VG▒V▒W▒V▒W▒V▒Z▒V▒W▒V▒Z▒V▒[▒V\▒V▒\▒VP▒߽V ▒߽VX&▒V`&▒V▒߽V`▒߽V▒߽V▒n▒V▒o▒VPo▒V0p▒V▒4▒V▒@▒V0:▒V@$▒V▒;▒V<▒V▒:▒V▒?▒VpA▒V▒9▒V▒8▒V0B▒VD▒V▒D▒V%▒V▒>▒V▒=▒V▒1▒V▒<▒V▒<▒V▒:▒V@%▒V▒E▒V▒]▒V▒▒▒V▒▒▒V▒▒▒V▒▒▒V▒▒▒V0▒▒V▒▒▒V V▒V▒5ݽV▒▒ڽV▒,V▒,V`iݽV▒۽V0▒۽Vp▒۽V▒▒۽V▒▒۽V`- For opening file use Visual Studio. We are using Visual Studio 2012 for opening dump file. You can open dump file in Linux or Windows it self.
- For installing Visual Studio type sudo add-apt-repository ppa:ubuntu-desktop/ubuntu-make
- Type sudo apt-get update and type sudo apt-get install ubuntu-make
- Type umake web visual-studio-code
- Then type a to install visual studio
- After opening above file in visual studio it will look like :-
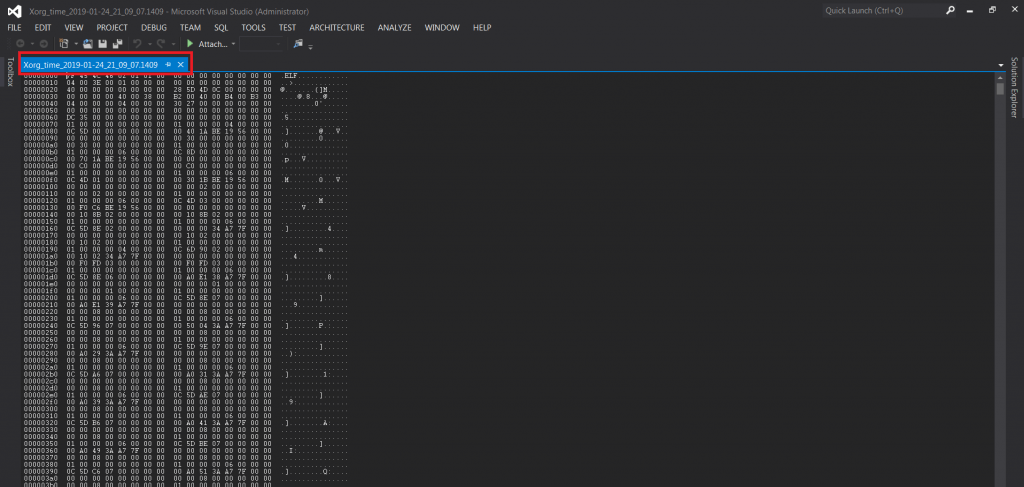
- The above is dump of process 1409 in Ubuntu. As you can see it has created dumps of the given process. It show codes of assembly language which can be decoded.
- The above information can be used in other hacking activities.
- Finding dumps in open server can give you the access to dump files. Those dump files can be used to grab passwords.
- As these dump files contains password in hash dump form which can reveal lot of information.
- Type sudo procdump -p 1409 -c 30 -n 3 -s 15
- -p is used to assign process id.
- -c is used to threshold CPU and create dump.
- -n is used to write no. of dumps.
- -s is used in consecutive seconds before dump is written.
root@ubuntu:/home/iicybersecurity/Downloads/ProcDump-for-Linux# sudo procdump -p 1409 -c 30 -n 3 -s 15
ProcDump v1.0.1 - Sysinternals process dump utility
Copyright (C) 2017 Microsoft Corporation. All rights reserved. Licensed under the MIT license.
Mark Russinovich, Mario Hewardt, John Salem, Javid Habibi
Monitors a process and writes a dump file when the process exceeds the
specified criteria.
Process: Xorg (1409)
CPU Threshold: <30
Commit Threshold: n/a
Threshold Seconds: 15
Number of Dumps: 3
Press Ctrl-C to end monitoring without terminating the process.
[21:47:38 - INFO]: CPU: 0%
[21:47:41 - INFO]: Core dump 1 generated: Xorg_cpu_2019-01-24_21:47:38.1409
[21:47:57 - INFO]: CPU: 0%
[21:48:03 - INFO]: Core dump 2 generated: Xorg_cpu_2019-01-24_21:47:57.1409
[21:48:19 - INFO]: CPU: 0%
[21:48:23 - INFO]: Core dump 3 generated: Xorg_cpu_2019-01-24_21:48:19.1409
- The above query has generated 3 dumps files. You can generate as many dumps you want.
- Now open all the dumps files in Visual Studio 2012.
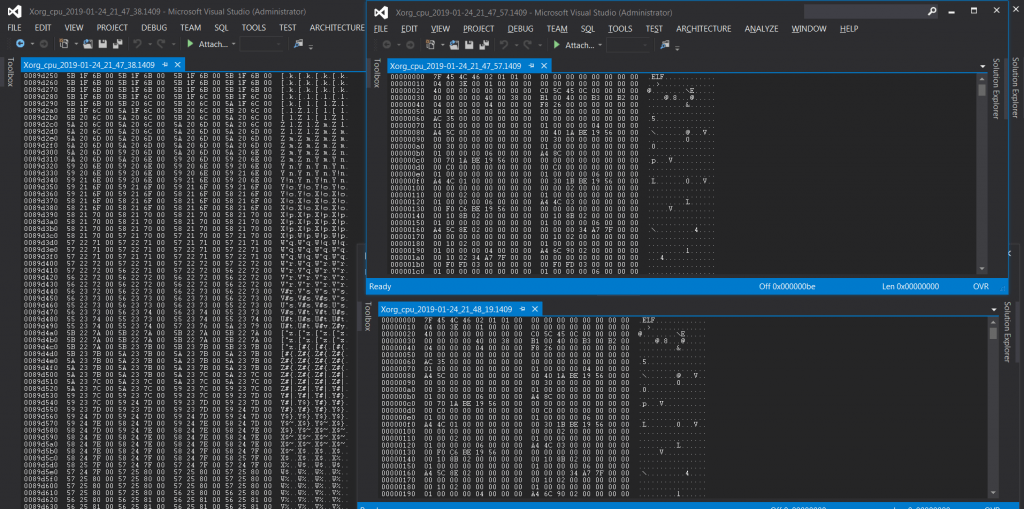
- The above is dump of process 1409 in Ubuntu. As you can see it has created dumps of the given process. It show codes of assembly language which can be decoded.
- The above information can be used in forensics of any malware running on the system, as stated by digital forensics expert of international institute of cyber security.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











