Internet is the hub of web applications. Many past developers has made numerous web applications to use internet more effectively. Internet has become more easy to use but complex to handle. Because it show case the lots of vulnerabilities. For gathering vulnerabilities we need an information gathering tool. That’s why we use information gathering or network reconnaissance tools. These tools gives basic information about the target. So that information can be used to build another scenario to exploit the target, explain ethical hacking investigators. Here comes Mercury tool which is used in information gathering of the target.
According to ethical hacking researcher of International Institute of Cyber Security says Mercury comes in bundle of other information gathering tools that’s why while testing a web application you don’t need to install separate tools.
Mercury is the tool to collect information about the target. It comprises of various small tools which are used to gather information. For showing you we have tested this tool on Kali Linux.
- Before installing this tool make sure you have selenium in your Kali Linux. For that type sudo apt-get update
- Type sudo apt-get install selenium
- Type git clone https://github.com/MetaChar/Mercury.git
- Then type ls
- Type cd Mercury
- Type pip install -r requirements.txt
pip install -r requirements.txt
Requirement already satisfied: colorama in /usr/lib/python2.7/dist-packages (from -r requirements.txt (line 1))
Collecting hashlib (from -r requirements.txt (line 2))
Using cached https://files.pythonhosted.org/packages/74/bb/9003d081345e9f0451884146e9ea2cff6e4cc4deac9ffd4a9ee98b318a49/hashlib-20081119.zip
Complete output from command python setup.py egg_info:
Traceback (most recent call last):
File "", line 1, in
File "/usr/lib/python2.7/dist-packages/setuptools/init.py", line 12, in
import setuptools.version
File "/usr/lib/python2.7/dist-packages/setuptools/version.py", line 1, in
import pkg_resources
File "/usr/lib/python2.7/dist-packages/pkg_resources/init.py", line 36, in
import email.parser
File "/usr/lib/python2.7/email/parser.py", line 12, in
from email.feedparser import FeedParser
File "/usr/lib/python2.7/email/feedparser.py", line 27, in
from email import message
File "/usr/lib/python2.7/email/message.py", line 16, in
import email.charset
File "/usr/lib/python2.7/email/charset.py", line 13, in
import email.base64mime
File "/usr/lib/python2.7/email/base64mime.py", line 40, in
from email.utils import fix_eols
File "/usr/lib/python2.7/email/utils.py", line 27, in
import random
File "/usr/lib/python2.7/random.py", line 49, in
import hashlib as _hashlib
File "hashlib.py", line 115, in
f()
TypeError: 'frozenset' object is not callable
----------------------------------------
Command "python setup.py egg_info" failed with error code 1 in /tmp/pip-build-hK3fYS/hashlib/
- The above command shows the error because some of the libraries are not inherited inside the code of the mercury.
- But still some of the main features of the mercury which are used in information gathering can be used.
- Type python Mercury.py
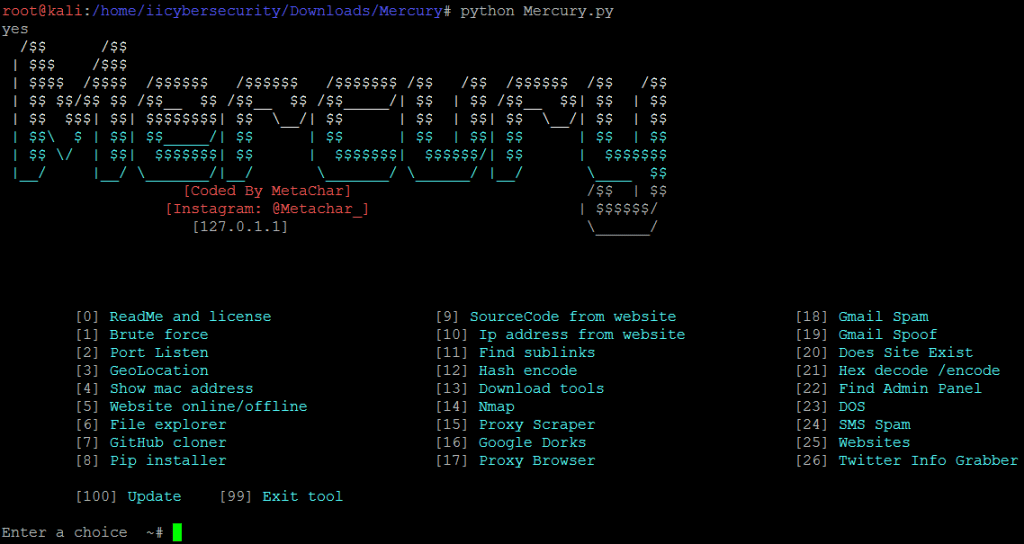
- The above are the list of tools used in information gathering.
Checking Website Online/Offline :-
- Type 5
- Then type https://hack.me
Enter a choice ~# 5
Enter a host name include https: https://www.hack.me
Attempt 1 at host: https://www.hack.me: online
Attempt 2 at host: https://www.hack.me: online
Attempt 3 at host: https://www.hack.me: online
Attempt 4 at host: https://www.hack.me: online
Attempt 5 at host: https://www.hack.me: online
- The above command shows that target website is online. Mercury tries to ping on the target to showcase that the target is online.
- The above is the basic method used in initial phase of information gathering.
Getting An IP address of the Target :-
- Type 10
- Type hack.me
Enter a choice ~# 10
Enter a website url hack.me
74.50.111.244
- The above command shows the IP address of the target.
Creating an Hash Value of the Word :-
- Type 12
- Then type testword or any word of your choice.
Enter a choice ~# 12
Please Enter a Word/String To Hash: testword
97d7f037cc3360e21991849c0dff4985
- The above command can be helpful to create an hash encode of target. The hash encode can be helpful to attack using other hacking activities.
Download Tools Using Mercury :-
- There are many tools in mercury which you can download and use them in information gathering. Some of the tools do include in Kali Linux and some are the basic tools that can be used.
- Type 13
Enter a choice ~# 13
- Then type any number of which you want to install the tool.
- Type 6
[0] Metasploit [9] Aircrack
[1] Mercury [10] Wifite
[2] Nmap [11] Hammer
[3] Lazy script [12] Xerxes
[4] fsociety [13] XSStrike
[5] Reaver [14] Wpscan
[6] InstaBrute [15] Cupp
[7] Cl0neMas3r [16] Hydra
[8] Sqlmap
[100] Install All [99] Exit submenu
Tools ~# 6
- Then the tool will be downloaded and can be used in other hacking activities.
Use Mercury For DOS Attack :-
- Type 23
- Type 192.168.1.105 target IP address.
Enter a choice ~# 23
Enter an ip address: 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
Bytes Sent to 192.168.1.105
- The above command is useful in DOS attack. DOS is the most popular attacks. This method can be used in other hacking activities.
Finding Admin Panel :-
- Type 22
- Then type www.hack.me
- Type https
Enter a choice ~# 22
Enter a site to scan just www: www.hack.me
Is the link https or https: https
https://www.hack.me/a
https://www.hack.me/dm
https://www.hack.me/in.
https://www.hack.me/php
https://www.hack.me/
https://www.hack.me/admin.
https://www.hack.me/html
https://www.hack.me/index.ph
https://www.hack.me/p
https://www.hack.me/login.php
https://www.hack.me/
- The above command tries to find the admin panel of target. This method can be used in other hacking activities.
- Mercury uses its own wordlist for creating an most common admin panel links.
Using NMAP in Mercury :-
- Type 14
- Type y if you have nmap install if not type n.
- Then type 192.168.1.105
Enter a choice ~# 14
Have you already installed nmap? y/n y
Enter an ip: 192.168.1.105
Starting Nmap 7.70 ( https://nmap.org ) at 2018-12-31 04:00 EST
NSE: Loaded 148 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 04:00
Completed NSE at 04:00, 0.00s elapsed
Initiating NSE at 04:00
Completed NSE at 04:00, 0.00s elapsed
Initiating ARP Ping Scan at 04:00
Scanning 192.168.1.105 [1 port]
Completed ARP Ping Scan at 04:00, 0.07s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 04:00
Completed Parallel DNS resolution of 1 host. at 04:00, 0.09s elapsed
Initiating SYN Stealth Scan at 04:00
Scanning dvwa (192.168.1.105) [1000 ports]
Discovered open port 80/tcp on 192.168.1.105
Discovered open port 443/tcp on 192.168.1.105
Discovered open port 3306/tcp on 192.168.1.105
Discovered open port 21/tcp on 192.168.1.105
Discovered open port 22/tcp on 192.168.1.105
Completed SYN Stealth Scan at 04:00, 0.16s elapsed (1000 total ports)
Initiating Service scan at 04:00
Scanning 5 services on dvwa (192.168.1.105)
Completed Service scan at 04:01, 12.10s elapsed (5 services on 1 host)
Initiating OS detection (try #1) against dvwa (192.168.1.105)
NSE: Script scanning 192.168.1.105.
Initiating NSE at 04:01
Completed NSE at 04:01, 1.58s elapsed
Initiating NSE at 04:01
Completed NSE at 04:01, 0.00s elapsed
Nmap scan report for dvwa (192.168.1.105)
Host is up (0.00100s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.2c
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|http-favicon: Unknown favicon MD5: 69C728902A3F1DF75CF9EAC73BD55556 | http-methods: | Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|/ |_http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | http-title: Damn Vulnerable Web App (DVWA) - Login |_Requested resource was login.php 443/tcp open ssl/http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1) | http-cookie-flags: | /: | PHPSESSID: | httponly flag not set
|http-favicon: Unknown favicon MD5: 69C728902A3F1DF75CF9EAC73BD55556 | http-methods: | Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|/ |_http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | http-title: Damn Vulnerable Web App (DVWA) - Login |_Requested resource was login.php | ssl-cert: Subject: commonName=localhost/organizationName=Apache Friends/stateOrProvinceName=Berlin/countryName=DE | Issuer: commonName=localhost/organizationName=Apache Friends/stateOrProvinceName=Berlin/countryName=DE | Public Key type: rsa | Public Key bits: 1024 | Signature Algorithm: md5WithRSAEncryption | Not valid before: 2004-10-01T09:10:30 | Not valid after: 2010-09-30T09:10:30 | MD5: b181 18f6 1a4d cb51 df5e 189c 40dd 3280 |_SHA-1: c4c9 a1dc 528d 41ac 1988 f65d b62f 9ca9 22fb e711 |_ssl-date: 2018-12-31T09:01:11+00:00; +4s from scanner time. | sslv2: | SSLv2 supported | ciphers: | SSL2_DES_64_CBC_WITH_MD5 | SSL2_RC4_128_WITH_MD5 | SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 | SSL2_DES_192_EDE3_CBC_WITH_MD5 | SSL2_IDEA_128_CBC_WITH_MD5 | SSL2_RC4_128_EXPORT40_WITH_MD5 | SSL2_RC2_128_CBC_WITH_MD5
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:58:9E:B1 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.17 - 2.6.36
Uptime guess: 0.049 days (since Mon Dec 31 02:50:06 2018)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=198 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 3s, deviation: 0s, median: 3s
TRACEROUTE
HOP RTT ADDRESS
1 1.00 ms dvwa (192.168.1.105)
NSE: Script Post-scanning.
Initiating NSE at 04:01
Completed NSE at 04:01, 0.00s elapsed
Initiating NSE at 04:01
Completed NSE at 04:01, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.90 seconds
Raw packets sent: 1020 (45.626KB) | Rcvd: 1016 (41.358KB)
- The above command uses nmap and shows open ports, MAC address, OS and information what nmap normally shows.
- The above information can be used in other hacking activities, say ethical hacking professors.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











