Credential abuse is something that happens only to CEOs or very rich people or employees of fortune 500 companies right? Nope. It’s everywhere, and your compromised passwords and usernames are enabling all kinds of cyber criminals to perform all kinds of account takeover (ATO) attacks. 24,649,096,027 account usernames and passwords have been leaked by cyber-threat actors, as of this year. That’s a big number―one that should shake the cyber security community at its core. But despite this number, which increases exponentially each year, and the deluge of reports highlighting the risk of insecure credentials, you still have a friend or an officemate or boss, who’s carefully typing 123456 into a password field right now.
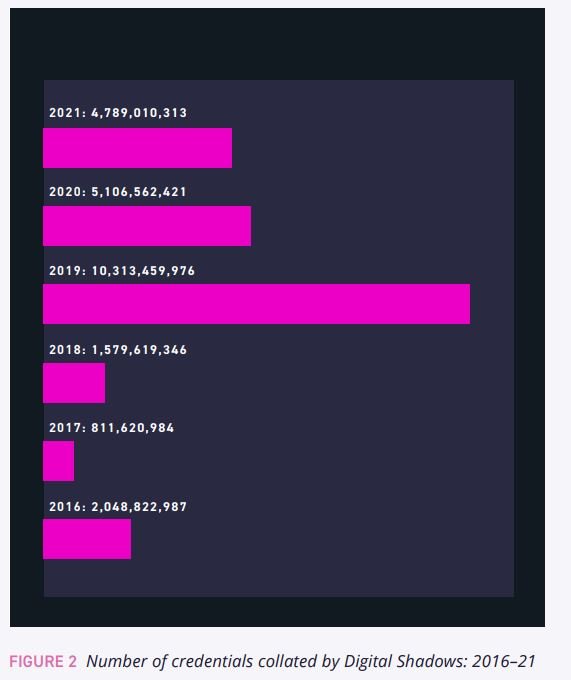
The Digital Shadow team collated more than 24 billion leaked credentials from the dark web. That’s a 65 percent increase from 2020, likely caused by an enhanced ability to steal credentials through new ransomwares, dedicated malware and social engineering sites, plus improved credential sharing. Within this leaked usernames and passwords, approximately 6.7 billion credentials had a unique username-and-password pairing, indicating that the credential combination was not duplicated across other databases. This number was 1.7 billion more than found in 2020, highlighting the rate of data breach across completely new credential combinations.
The most common password, 123456, represented 0.46 percent of the total of the 6.7 billion unique passwords. The top 100 most common passwords represented 2.77 percent of this number. Information-stealing malware and ransomware persists as an important threat to your privacy. Some of these malwares can be bought for as little as $50, and some go for thousands, depending on features.
Cybercriminal marketplaces and dark web forums are the best places to buy and sell stolen credentials. Companies whose data has been leaked have been informed but not much can be done at this stage. Several subscription services on the dark web have also been launched, offering cybercriminals a premium service to purchase stolen credentials. The price of credentials depends on the account’s age, the seller and buyer reputation, and the size of the data file on offer. Some also offer sample data sets to collaborate its uniqueness. Certain account types, like cryptocurrency-related accounts can be more costly.
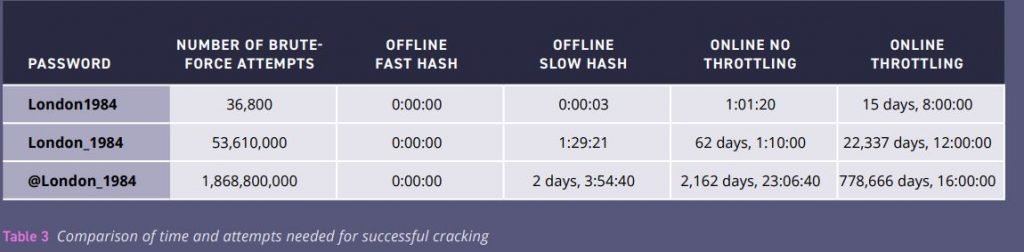
Once credentials have been obtained, free, open-source credential stuffing and password cracking tools can allow cyber criminals all the functionality required for a sophisticated attack to unlock passwords. Offline tools usually give the best results for cracking passwords. As per the cyber security awareness training experts 49 of the top 50 most commonly used passwords could be cracked in less than a second. Addition of a special character to a basic ten-character password adds about 90 minutes to that time. In addition, two special characters boost the offline cracking time to around 2 days and 4 hours, according to cyber security awareness training experts.
Most of these cyber criminals are Financially motivated, state-sponsored, and ideologically motivated actors (hacktivists like anonymous). All of them have used have all used ATO as a conduit for their activity in 2022. This includes several attacks by the data extortionists known as Lapsus$ Group. According to cyber security awareness training experts, until passwordless authentication becomes mainstream, the best ways to minimize the likelihood and impact of account takeover are simple controls and user education like multi-factor authentication, password managers, and complex, unique passwords.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











