DNSMap: Dnsmap is a tool used to gather subdomains & information of subdomains for a target host, as per ethical hacking courses. It was developed in 2006 and last updated in 2010. This package consists of 2 scripts – dnsmap, and dnsmap-bulk.sh. Dnsmap is used in scanning single domain and dnsmap-bulk.sh in bulk domains. According to ethical hacking expert from International Institute of Cyber Security, you can use dnsmap in footprinting activities also when you are doing black box penetration testing.
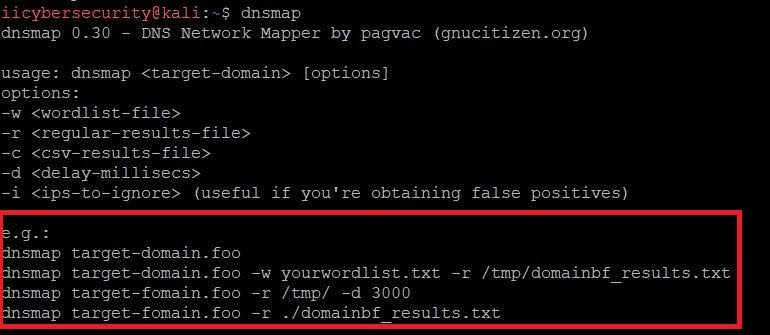
- For launching dnsmap simply go to linux terminal and type dnsmap.
- After typing dnsmap you will get below output.
- Dnsmap will give you help, which shows available options.
DNS USE:-
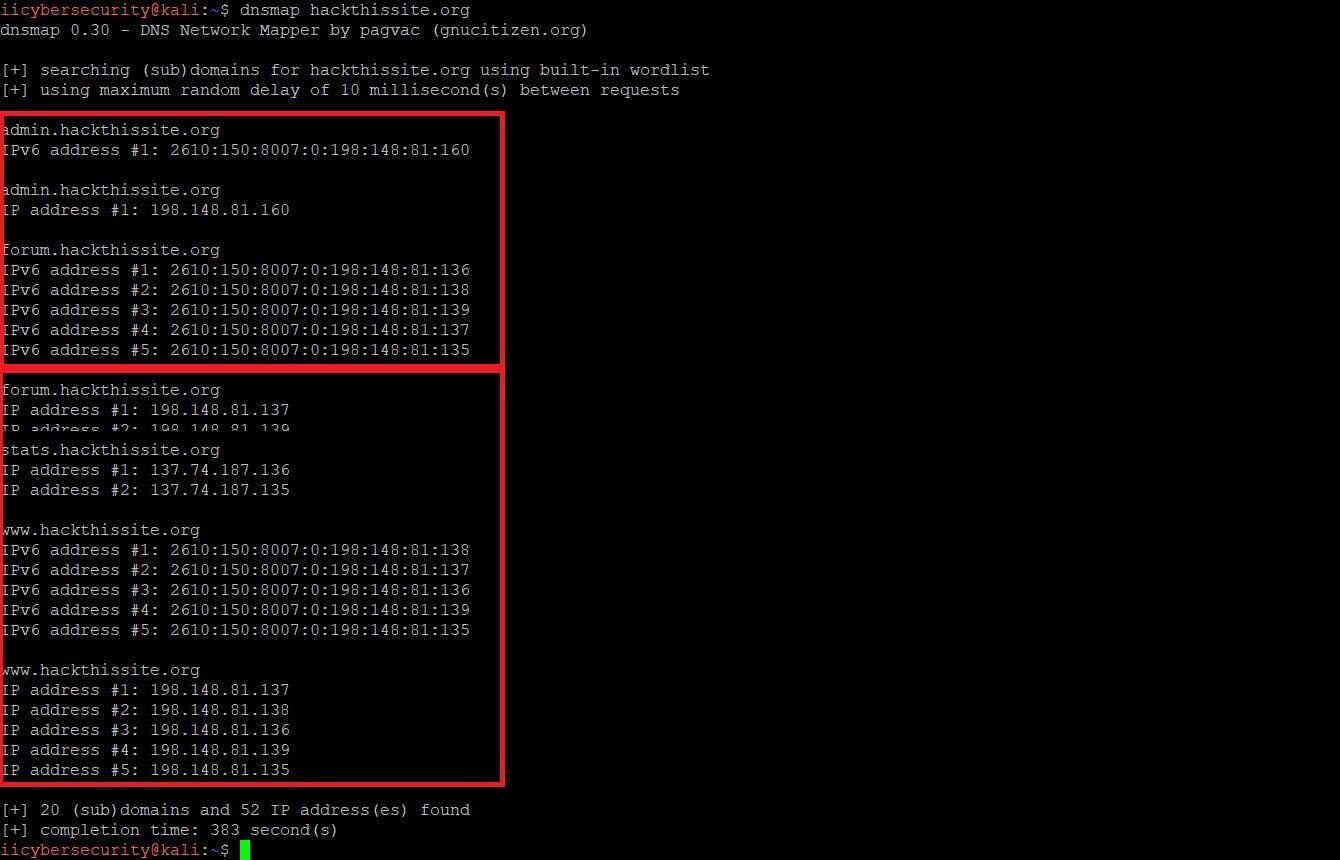
- Type dnsmap hackthissite.org
- If you run dnsmap without any options using only target address, it will use default list to brute forced target’s subdomains. As you see additional information in above screenshot could be used for testing.
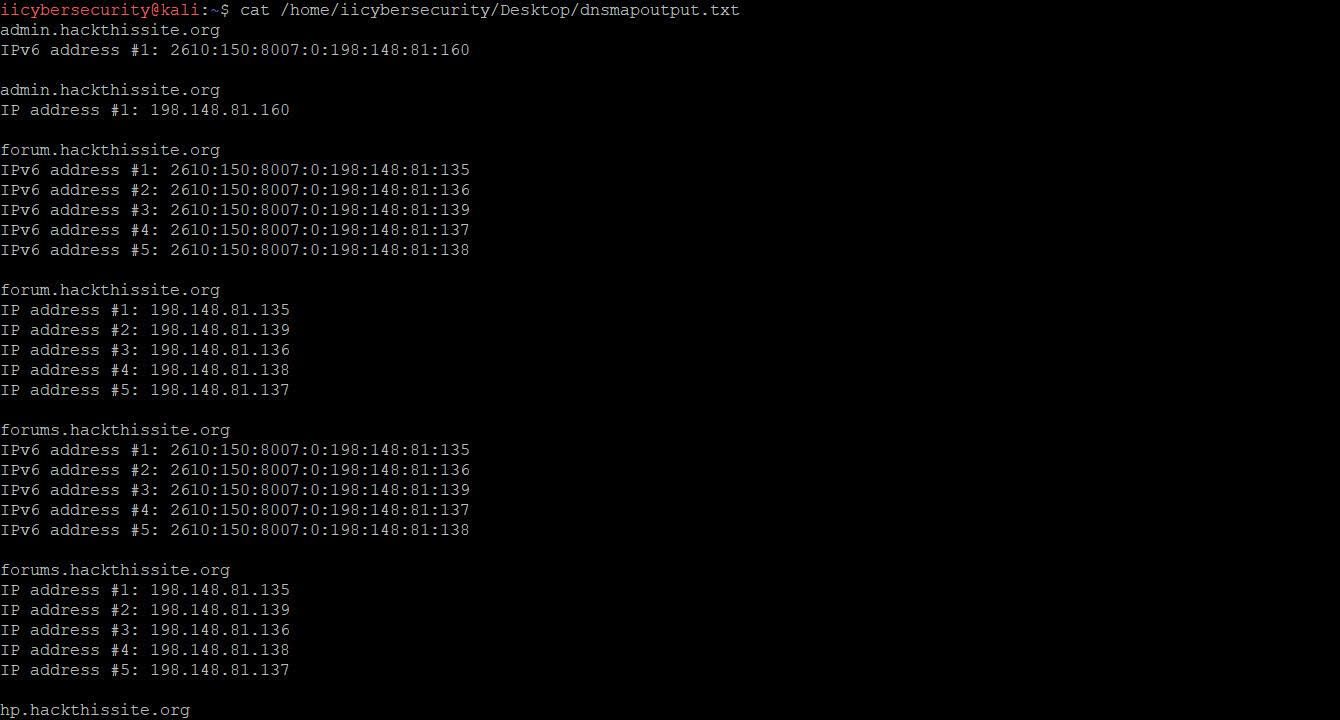
- For saving the output for later use in pentesting, rather than just viewing the results on the linux console. For saving the output in .txt file, type
dnsmap hackthissite.org -r /home/iicybersecurity/Desktop/dnsmapoutput.txt
- Once the scan finished open the text file, dnsmapoutput.txt in /home/iicybersecurity/Desktop/ path and you can see the same results as shown below:
- As you know dnsmap used default list, but you can use your own or another wordlist.
- Downloads wordlist from the given link and use it with -w option, as mentioned below:
https://www.md5this.com/tools/wordlists.html
- Dnsmap command with wordlist:
dnsmap target-domain.foo -w yourwordlist.txt -r /tmp/domainbf_results.txt
- As per the ethical hacking researcher from International Institute of Cyber Security, this tools is commonly used with the word list of different languages to scan the hidden websites belonging to the respective country.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.