EVADE USING PROXYCHAINS:- Whenever attacker attacks in any network, all traffic of the attacker can be logged which can reveal the identity of the attacker in destination network. All of these events increase the possibility of getting caught, explain ethical hacking professionals.
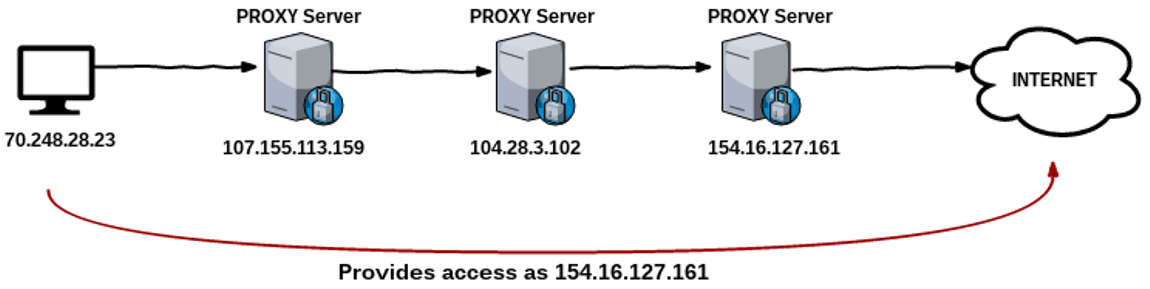
If you want to be undetectable on internet, you will have to work anonymously. This is where proxychain come. You can use proxy chain to hack anonymously. As shown below 70.248.28.23 is using proxychain (that is chain of proxies) to connect to internet.
On internet 70.248.28.23 is be masked with 154.16.127.161 IP address.
Proxychains is designed to accept attacker’s traffic and forward to target. If you are thinking someone can catch you? , then the answer is yes as well as no. Traffic from all intermediate proxies is normally logged depending on the proxy provider. For catching an attacker, forensic investigator need an search warrant to obtain logs, which can be sometime be difficult between proxies lying in different countries.
If attacker uses multiple proxies in a chain, proxychains make it harder to detect original IP address. As there can be any number of proxies between the attacker and the target, so sometimes it is hard for target to detect attacker’s IP address.
NOW HOW TO USE PROXYCHAIN?
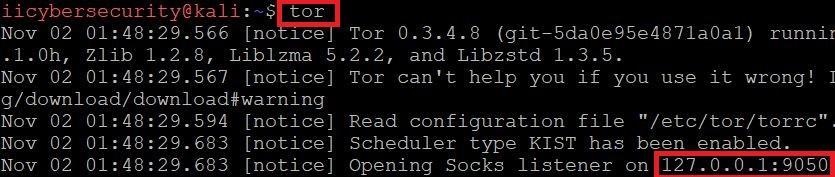
- Firstly check if the tor is running in your linux.
- If tor is not running start tor in linux terminal.
- Secondly start tor in linux. Type tor in linux terminal as shown below:
- By default tor runs on 127.0.0.1 using port 9050.
- If the tor is not installed then type apt-get install tor in linux terminal to install tor. If tor is installed move to next step.
- After configuring tor. Go to next step.
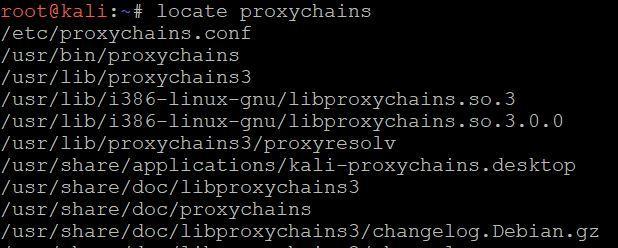
- Type locate proxychains to find proxychains.conf file in linux terminal.
- After locating proxychains.conf file we will start with scanning of any website anonymously.
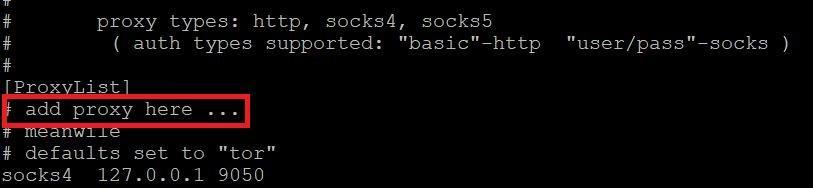
- By default proxychains.conf is configured to use tor proxy.
Note: There are two way of scanning target either tor proxies or open proxies. It depends on the attacker what proxy he/she want to use.
FOR SCANNING BY USING TOR PROXIES:
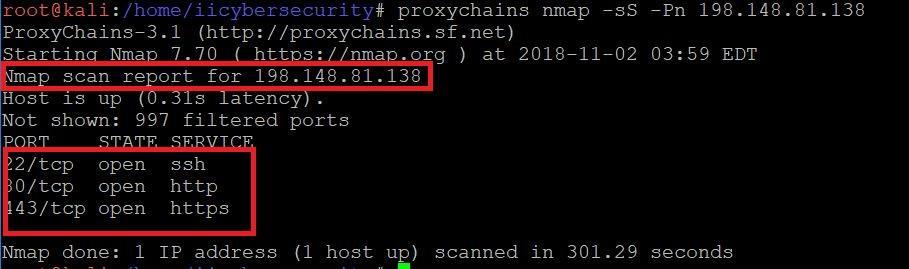
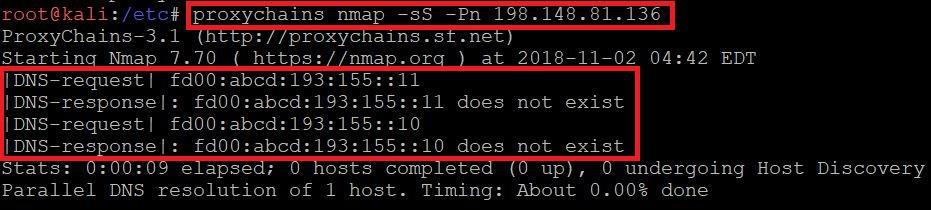
- Type proxychains nmap -sS -Pn 198.148.81.138
- By default tor uses its own set of anonymous proxies. If you want to add desired tor proxies you can add by configuring the proxychains.confg
- Type cat proxychains.confg. By default proxychains.conf is configured to use tor proxy running on 127.0.0.1:9050
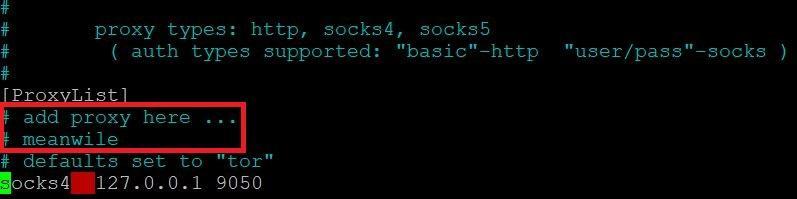
- For adding proxies type nano proxychains.confg in linux terminal.
- For adding proxies type nano proxychains.confg in linux terminal.
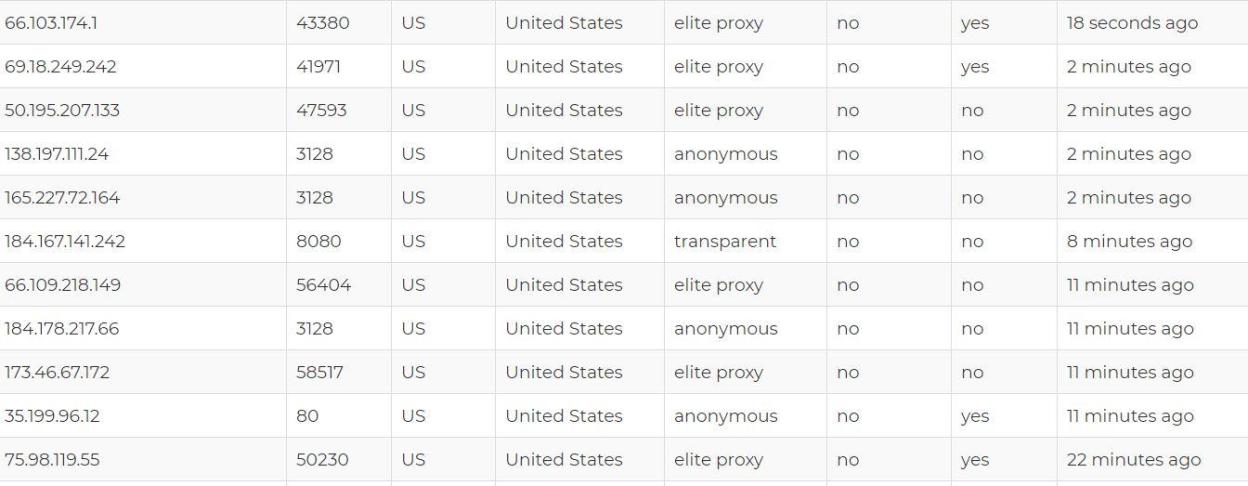
You can get large number of proxies by simply searching on google open proxies. You can also following links for getting proxies as shown below:-
EXECUTING USING OPEN PROXY:-
- In the above screenshot, query to DNS 198.148.81.136 failed, so try the above steps with other free proxies available on internet.
As per past researches done by ethical hacking experts in International Institute of Cyber Security, do not use open proxies in banking as they monitor your traffic.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.