DNSENUM. Dnsenum which is used to gather information about the target. Quite similar to (DIG) Domain information groper. Each of the DNS records can give bit of information about the target. The more information attacker get from the upfront, the better attacker is prepared for the attack. DNS security should not be left unattended and the security of DNS server is very important & sometimes ignored by many network administrators as seen in past research done by ethical hacking team of International Institute of Cyber Security.
Using DNSenum:
- For launching the tool go to linux and type dnsenum.
- If dnsenum shows error or warning while executing in any query that means you need update the some perl packages required for dnsenum as shown below:
- For installing missing per packages type: cpan String::cpan
- For example:
After launching dnsenum.
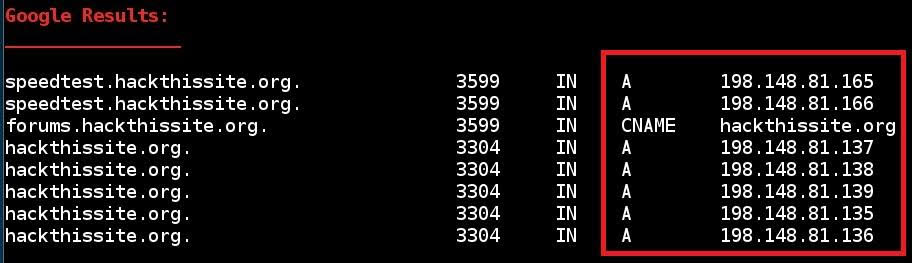
- Using DNS server for A, NS and MX queries- By default if you type dnsenum hackthissite.org. The query will use default DNS to gather information about the domain.
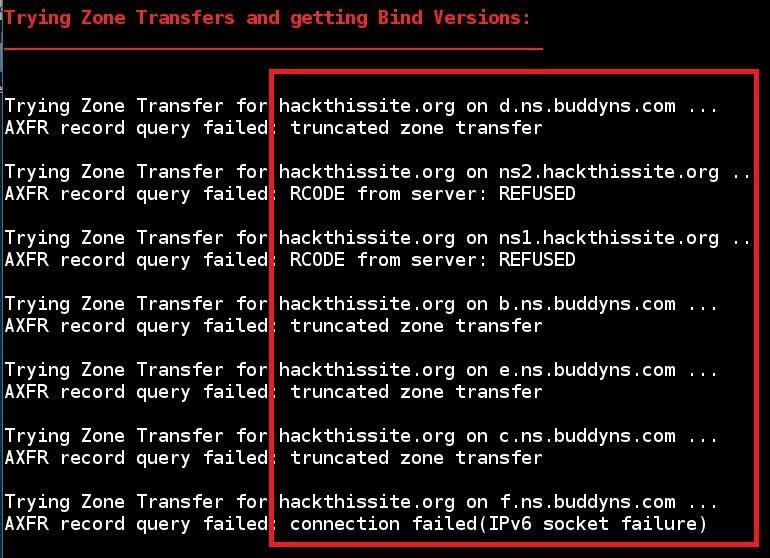
- As you can see in above screenshot: host address, name server, mail exchange and zone transfers. Zone transfers got failed because of reverse lookup operation failed.
2. For running the tool with specific DNS server:
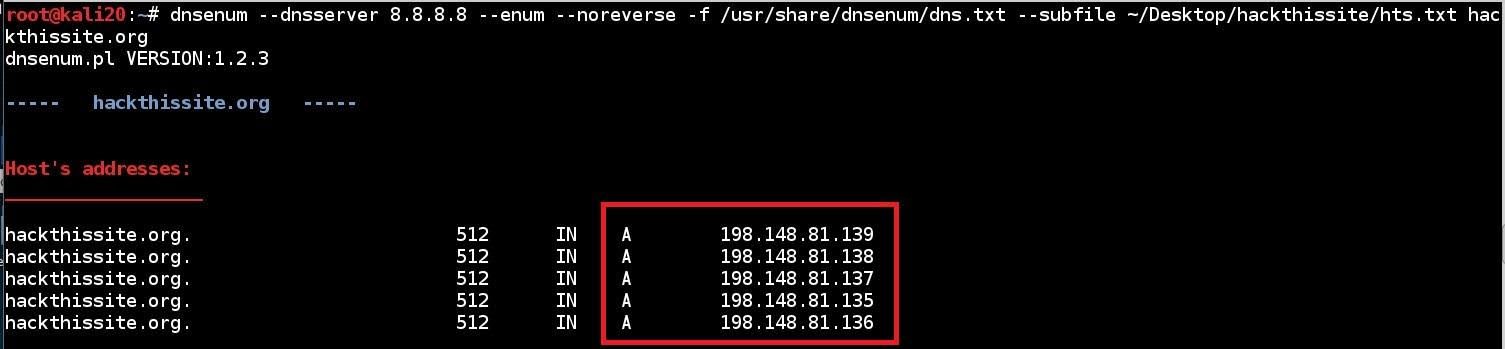
- Type dnsenum -dnsserver 8.8.8.8 -enum -noreverse -f /usr/share/dnsenum/dns.txt –subfile ~/Desktop/hackthissite/hts.txt
Host Address:
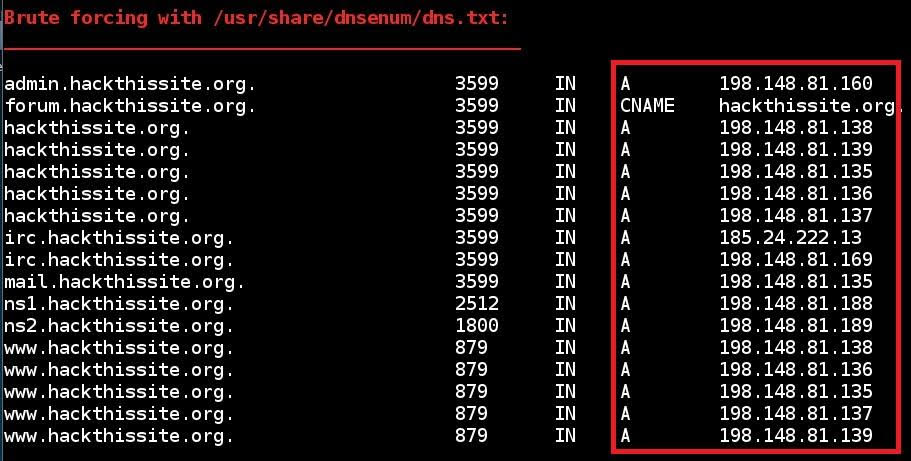
- Brute forcing subdomains of hackthissite.org using dns.txt :
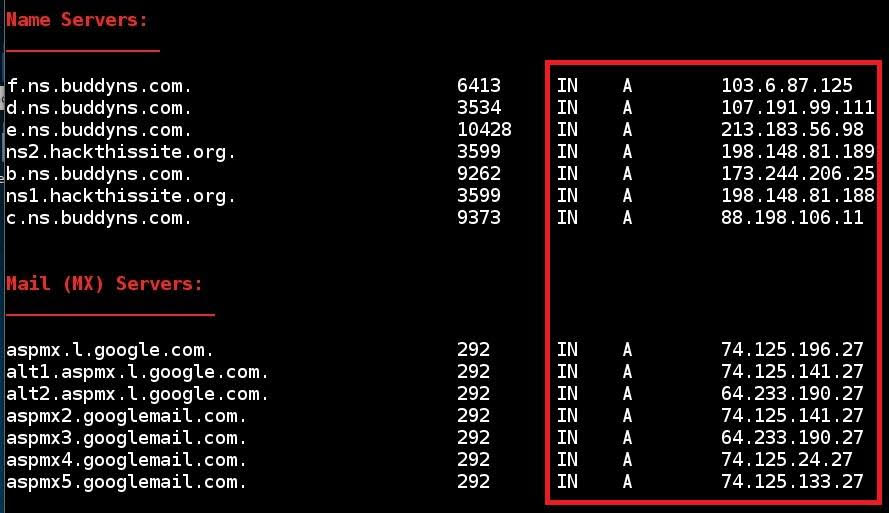
Mail Servers/Name Servers:
Google Results:
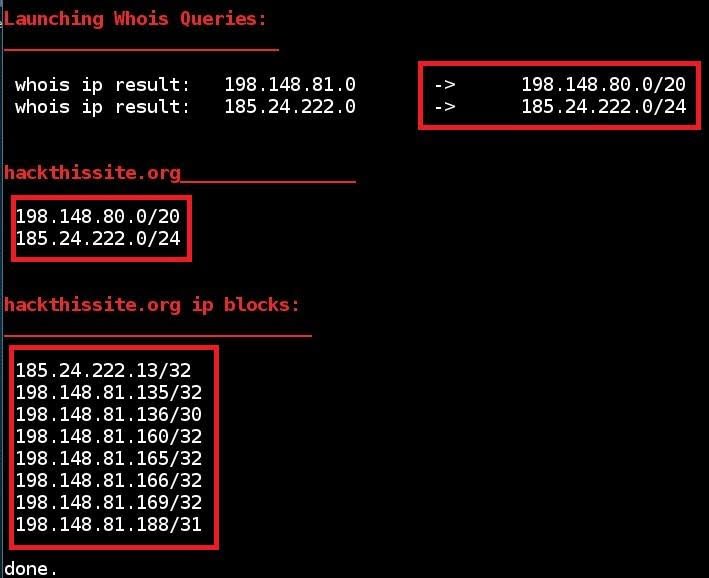
WHOIS:
Zone Transfer Failed example:
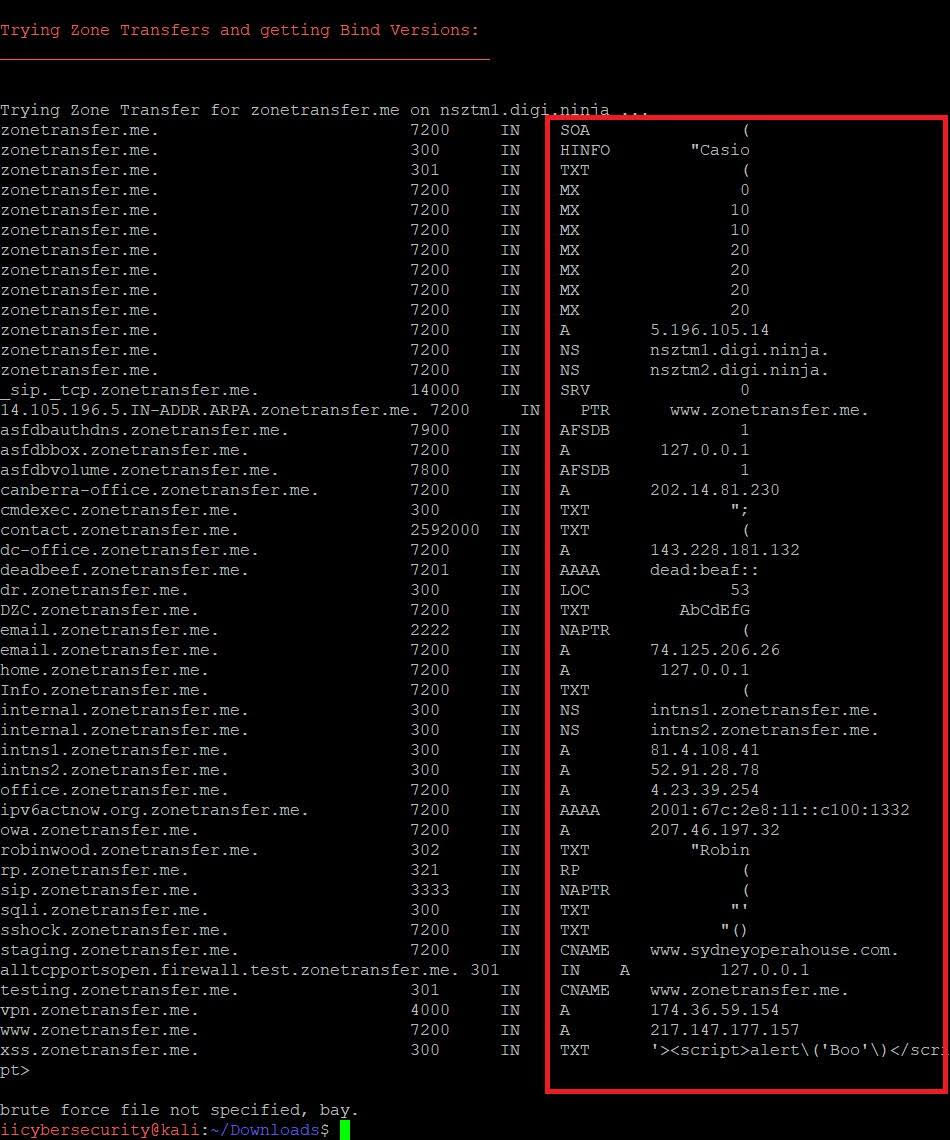
Zone Transfer Passed example:
Ethical hacking researcher of International Institute of Cyber Security have seen many customer with high end firewall and Intrusion Detection Systems but with least DNS security having zone transfer issues.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.