Wristband and armband devices such as smartwatches and fitness trackers could be used by attackers to spy on you!
We have discussed several times about the possibility to exploit IoT devices to spy on individuals. Lack of security by design and poor security settings could open the door to hackers. A Smartwatch or afitness tracker can reveal a hacker what a user you type into your computer keyboard.
In September, a group of students lead by Romit Roy Choudhury, Associate Professor at ECE Illinoisdeveloped a mobile app that is able to analyze the movements of a smartwatch to detect the keys pressed by the user. The researchers plan to present it this week at the MobiCon 2015 conference in Paris.
The project called Motion Leaks (MoLe) is funded by the National Science Foundation, the researchers have installed the homegrown app on a Samsung Gear Live smartwatch.
Using the watch’s built-in motion sensors, more specific data from the accelerometer and gyroscope, researchers were able to create a 3D map of the user’s hand movements while typing on a keyboard.
Now Tony Beltramelli, a masters student at the IT University of Copenhagen, is proposing another project dubbed “deep-spying” that exploit data gathered by gyroscope and accelerometers built-in the wearable device.
Users movement could be analyzed to guess what users wrote, for example while victims is inserting his PIN when accessing an ATM.
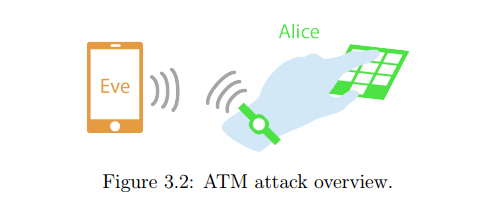
“A smartwatch is indeed potentially worn for an extended period such as the whole day, offering a pervasive attack surface to cyber-criminals,” wrote Beltramelli. “The implications are therefore significant: exploiting motion sensors for keystrokes inference can happen continuously.”
The software developed by Beltramelli collects motion data from a Sony SmartWatch 3 and elaborates it to guess everything typed by the user. The following video PoC shows the system guessing the numbers typed on a keypad.
“Dramatically, these observations imply that a cyber-criminal would be able, in theory, to eavesdropped on any device operated by the user while wearing a [wearable],” he wrote.
The goal of the researcher is to raise awareness about the risks related to motion sensors built-in IoT devices, demonstrating how it is possible to abuse them to spy on users.
“The LSTM-based implementation presented in this research can perform touchlogging and keylogging on 12-keys keypads with above-average accuracy even when confronted with raw unprocessed data. Thus demonstrating that deep neural networks are capable of making keystroke inference attacks based on motion sensors easier to achieve by removing the need for non-trivial preprocessing pipelines and carefully engineered feature extraction strategies.” states the paper.
Smartwatches and other wearable devices are enlarging our surface of attack and this study demonstrates it.
Source:https://securityaffairs.co/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











