CSV Excel Macro Injection also known as Formula Injection or CSV Injection is an attack technique used in the day today penetration testing of the application.
CSV injection is a vulnerability which affects those applications which has the functionality to export spreadsheets that are dynamically generated from invalidated or unfiltered user inputs
Modern web applications offer spreadsheet export function these days,which allows the user to download data in a .csv file format or .xls file format which is suitable for handling spreadsheet applications like MS-Excel and OpenOffice Calc which results in cells in the spreadsheets containing inputs from untrusted source.This can result into affecting the end user who is accessing the exported spreadsheet.
This vulnerability can be used by an attacker in order to execute attacks such as client-side command injection or code injection.
The attack scenario for this is purely targeting the user(s) who download the Excel file, naturally, this attack is usually disregarded as a non-issue, however, websites should still be aware of information that they are exporting can potentially affect the users.
Demonstration of CSV excel macro injection:
CSV excel macro injection can be exploited when the application supports export to excel functionality.
This happens on spreadsheet files which are dynamically generated from invalidated input data
Payloads used to test and exploit:
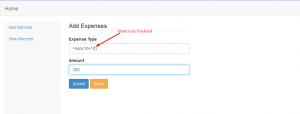
Formulae which are used in excel for carrying out operations can be used to test for formula injection on websites.
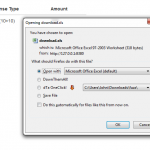
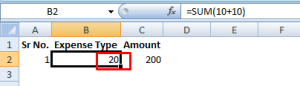
Eg: =sum(10+10)
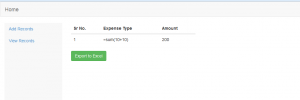
As you can see once we click on the export excel option the records are automatically exported to an excel file with the .xls format and it allows us to download the .xls file
Technical Analysis of the Vulnerability:
This vulnerability occurs due to the concept of dynamic Data exchange(DDE).DDE is a protocol for interprocess communication under windows supported by MS-Excel,LibraOffice and Apache OpenOffice.
The DDE function is in the following format:
=DDE(server; file; item; mode)
So by using some malicious arguments,it is possible to remotely execute apllications or commands on the victim’s computer of whoever opens the document.
The most common payload used is:
=cmd|’ /C calc’!A0
Technical Details of the above payload:
cmd is the name the server can respond to whenever a client is trying to access the server
/C calc is the file name which in our case is the calc(i.e the calc.exe)
!A0 is the item name that specifies unit of data that a server can respond when the client is requesting the data
So our final DDE call becomes:
DDE (“cmd”;”/C calc”;”!A0″)
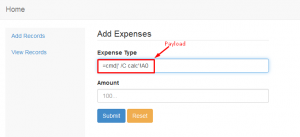
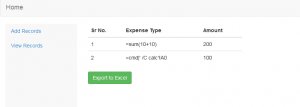
As you can see in the above screenshots our payload has been added to the input fields.Now once we export this record to an excel file our payload informs the program to run an application called cmd.exe with the following command /C calc which will execute calc.exe from the command line.
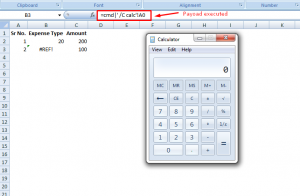
Once the excel file is open calc.exe will be executed as shown in the screenshot below.
These payloads are all fine and well however, sometimes the = character is being filtered out. However we can use some different combinations such as @, + or – . Current payload of choice for exploiting this as a proof of concept is.
@SUM(1+1)*cmd|' /C calc'!A0
We can use any formula starting with:
- =
- +
- –
- @
Recommendations
Updated on Sunday, 6:30 AM
It is always good practice not to trust user inputs and always encode the output. For the successful execution of the formula attacker will have to use the ‘-‘ , ‘=’ , and the pipe (|) is used to execute the binary in the excel software. It is strongly recommended to filter the ‘- ‘, ‘|’ , ‘+’ and ‘=’ to mitigate this vulnerabilty.
Source:https://blog.securelayer7.net/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.