It is a good day when a ransomware programmer channels their noobness and releases an insecure ransomware. This is the case with a new variant of the NoobCrypt Ransomware that was discovered by security researcher Jakub Kroustek. Living up to its name, the developer of NoobCrypt uses the same encryption key for every victim. This allowed Jakub to easily retrieve the password and post it on Twitter for victims to use.
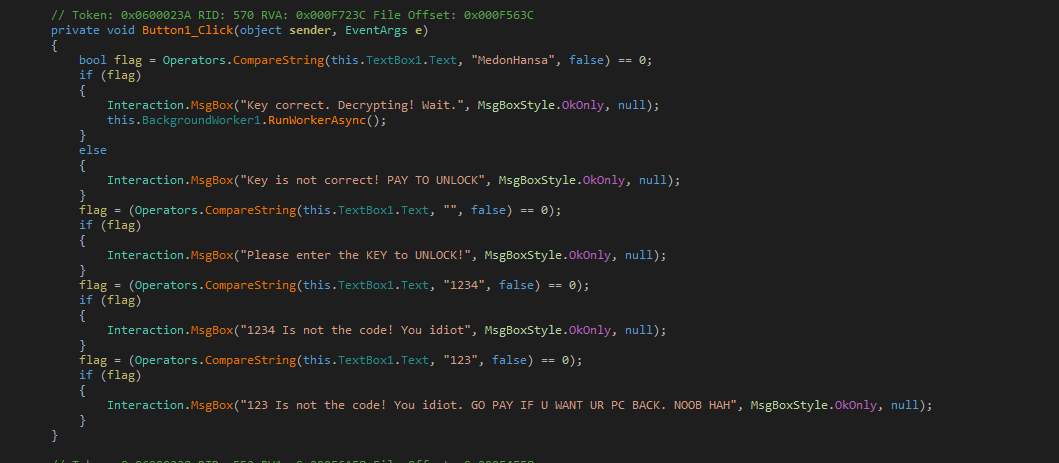
NoobCrypt gets its name from taunts found in the executable’s source code. These taunts would be displayed when victim’s enter various passwords in the key field to try and decrypt their files. For example, as seen by the source code below, when a victim enters 123, the ransomware would display an alert that taunts them with the message “123 is not the code! You idiot. GO PAY IF U WANT UR PC BACK. NOOB HAH”.
Looks like the joke is on the ransomware dev, as thanks to Jakub we have a list of known decryption keys that a victim can use to decrypt files affected by NoobCrypt.
Decrypting NoobCrypt
When a user is infected with NoobCrypt they will be shown a ransom lock screen like the one below. This lock screen will state “Your personal files are encrypted”, that it was “Made in R0MANIA”, the bitcoin address a payment must be paid to, and the amount of the ransom.
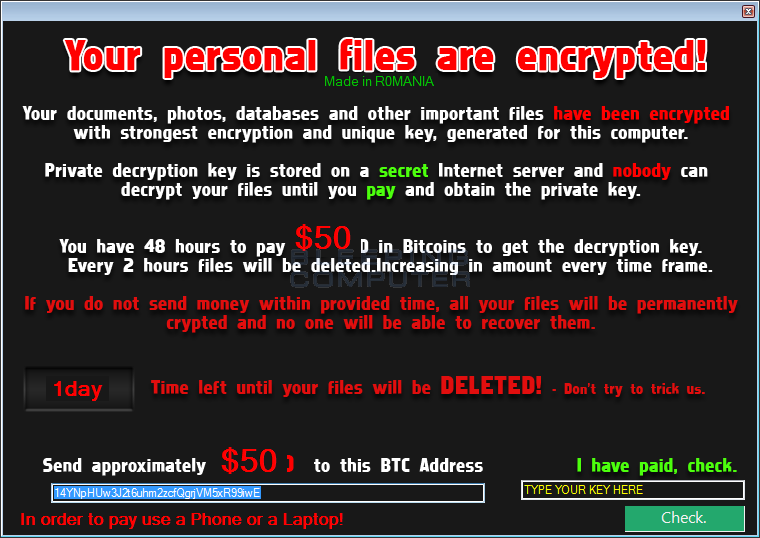
As each release of NoobCrypt has a specific bitcoin address and ransom amount that associated with that release, we can use this information and the table below to determine the decryption key. With the help of Jakub, the known list of passwords and how to identify what version you are infected with is below.
| Version | Ransom Amount | Bitcoin Address | Decryption Key |
|---|---|---|---|
| 1 | $299 | 1JrYNuMaE4VXKrod2gA9keBo6nzPvtaoZ6 | ZdZ8EcvP95ki6NWR2j |
| 2 | $100 | 1MCLTT5qAqpabSSuKnYecRt1ZQyF6aaQFe | ZdZ8EcvP95ki6NWR2j |
| 3 | $50 | 14YNpHUw3J2t6uhm2zcfQgrjVM5xR99iwE | lsakhBVLIKAHg |
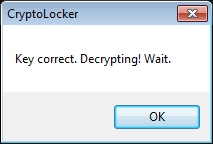
Once the associated decryption key is identified, a vicitm needs to enter it into the Key field of the ransom screen and then click the Check button. If the key is accepted, it will display a message and decrypt the victim’s files.
If the key is not accepted, simply send us a sample of the executable and we will retrieve the key for you.
Extensions encrypted by NoobCrypt:
txt,doc,dot,docx,docm,dotx,dotm,docb,rtf,wpd,pdf,xls,xlt,xlm,xlsx,xlsm,xltx,xltm,xlsb,cdx,xla,xlam,xll,xlw,ppt,pot,pps,pptx,pptm,potx,potm,ppam,ppsx,ppsm,sldx,sldm,accdb,db,dbf,mdb,pdb,sql,jpg,jpeg,raw,tif,gif,png,bmp,wav,mp3,aif,iff,m3u,m4u,mid,mpa,wma,ra,avi,mov,mp4,3gp,3g2,asf,asx,flv,wmv,vob,m3u8,ico
IOCs:
SHA256: 974d2a36971b0f05c8a2d5b0daaee93732b78f0edeb4555aadbc1b7736ce995f
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











