The author of the Petya-Mischa ransomware combo has returned with a new version that uses the name GoldenEye Ransomware, continuing the malware’s James Bond theme.
Brought to our attention today by a Bleeping Computer user named gizmo21, this new “GoldenEye” ransomware is almost identical to past Petya and Mischa variants.
GoldenEye Petya variant spreading via spam emails
The ransomware is currently distributed via spam campaigns that at the moment seem to be targeting German-speaking users.
The spam emails use the classic resume theme and come with two files attachments. The first is a fake PDF resume and the second is an Excel spreadsheet.
The Excel file comes with a macro script, which if allowed to execute would install the ransomware.
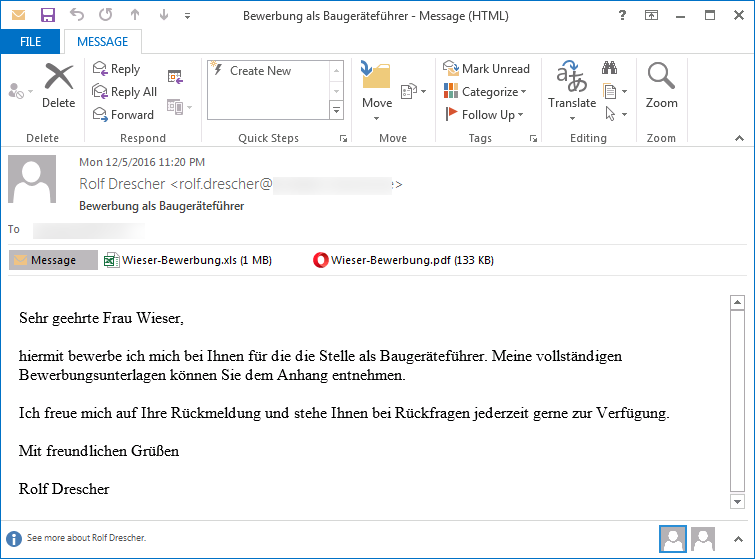

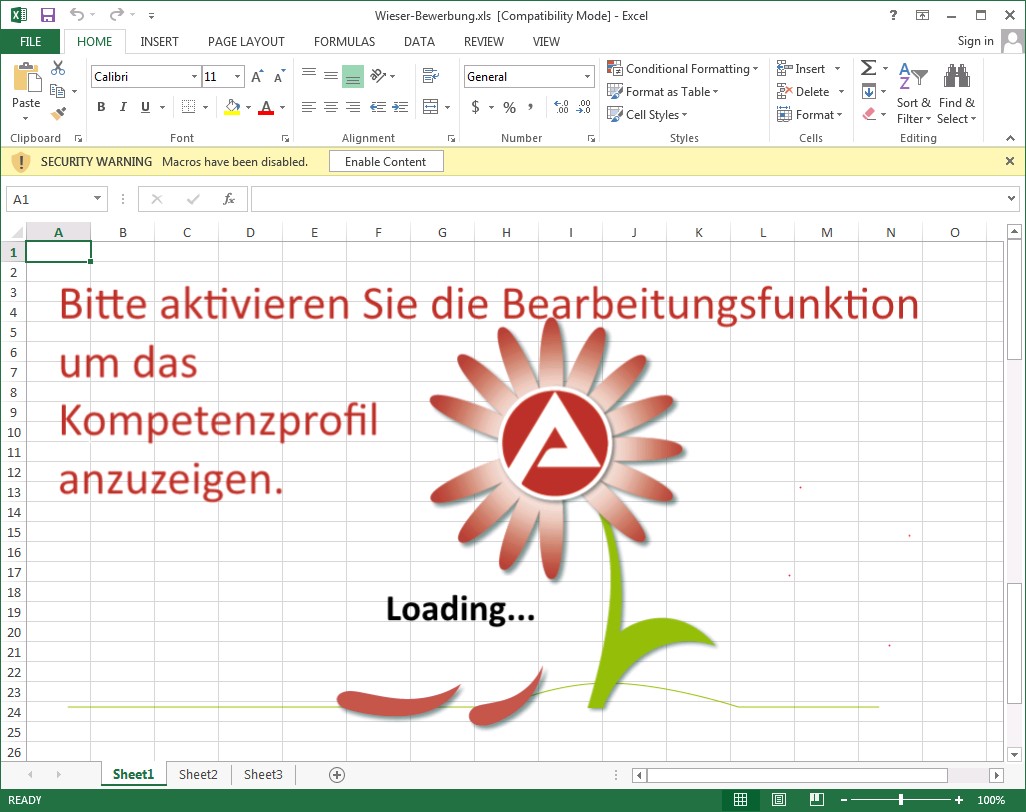
In the spam campaign observed in the past days, the Excel files have the following names:
Meinel-Bewerbung.xls
Seidel-Bewerbung.xls
Wüst-Bewerbung.xls
Born-Bewerbung.xls
Schlosser-Bewerbung.xls
Once the ransomware takes root, its modus operandi is the same as observed in past Petya and Mischa infections.
The GoldenEye variant starts by encrypting the user’s files, just like regular ransomware. For each file it encrypts, GoldenEye appends a random 8-character extension at the end.
The ransomware then also modifies the user’s hard drive MBR (Master Boot Record), with a custom boot loader.
Once this operation ends, the ransomware shows the following ransom note, for a short amount of time. The file’s name is YOUR_FILES_ARE_ENCRYPTED.TXT.
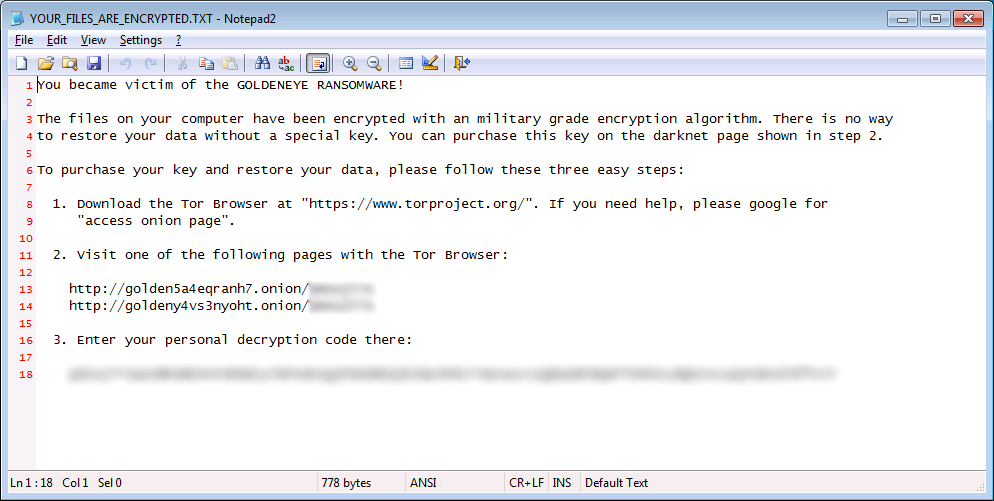
This is the “Mischa” part of the Petya-Mischa combo. Mischa acts as a regular file encryptor, while Petya is the hard drive locker.
Shortly after displaying the ransom note, GoldenEye enters in the Petya part of the file encryption process.
This occurs when the ransomware forcibly reboots the user’s computer and enters a stage where it starts encrypting the user’s hard drive MFT (Master File Table), making it impossible to access any files on the hard disk.
The MFT encryption process is masked by a fake chkdsk screen, just like in past Petya variants.
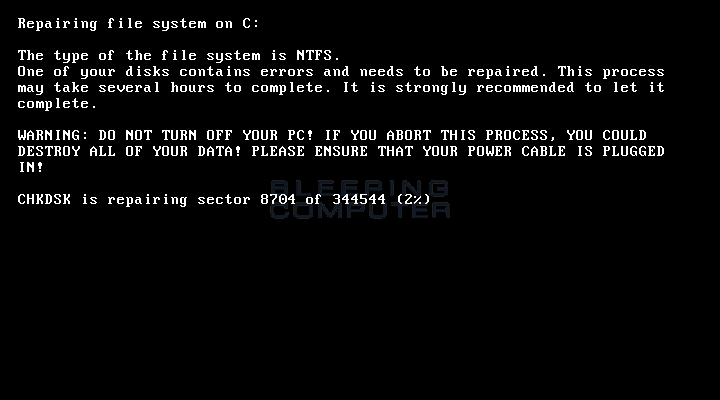
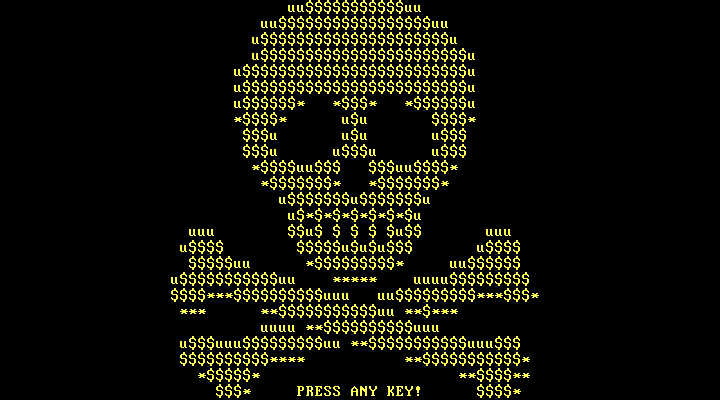
After this process ends it’s when we see the first visible changes from previous Petya-Mischa infections, with a new ransom screen.
Technically, this boot level ransom note is the same as previous Petya screens, but it’s now displayed using yellow-colored text. Initially, Petya used red text, and then switched to green when the Mischa component was added.
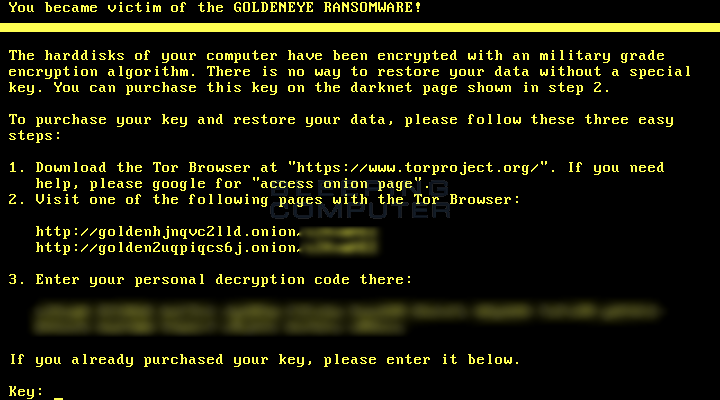
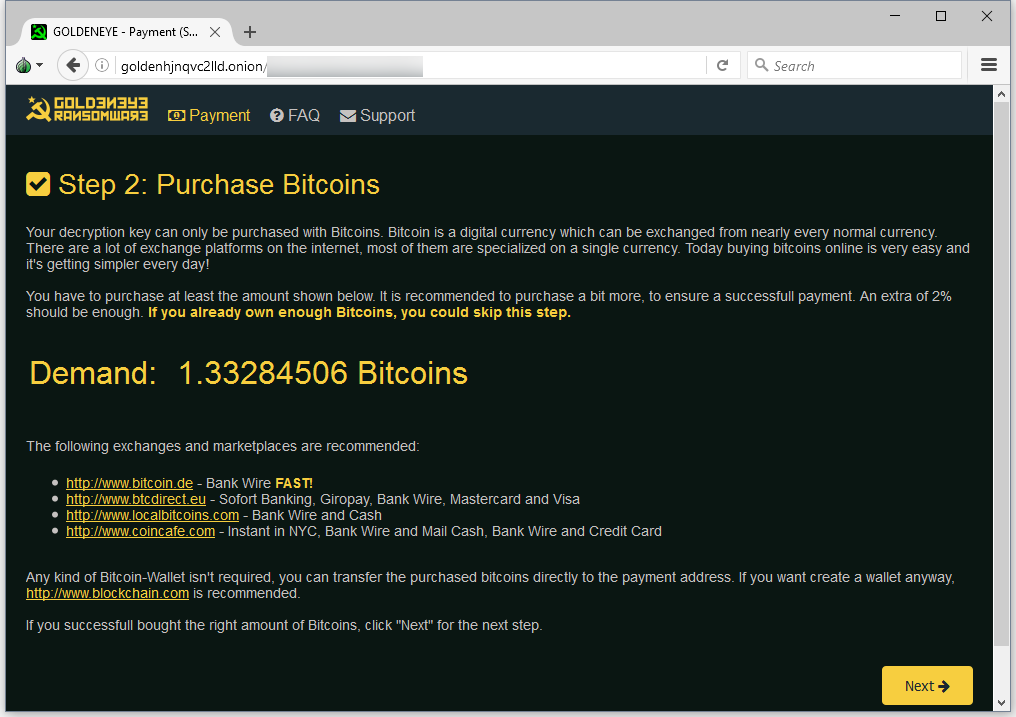
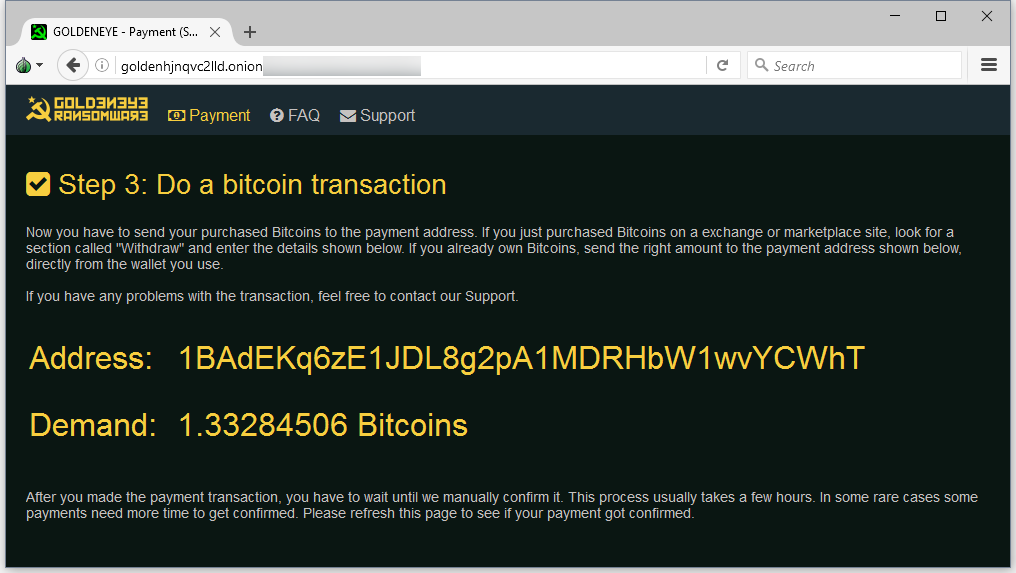
Users that want to recover files must take the “personal decryption code” from the ransom note and enter it on a Dark Web portal. The GoldenEye Petya version asks for 1.33284506 Bitcoin (roughly $1,000).
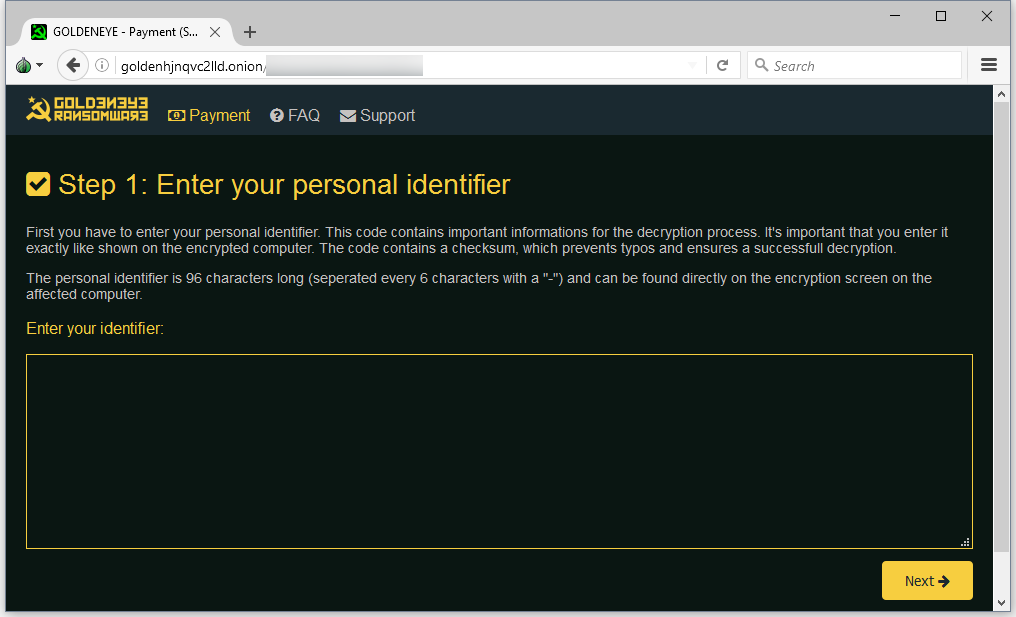
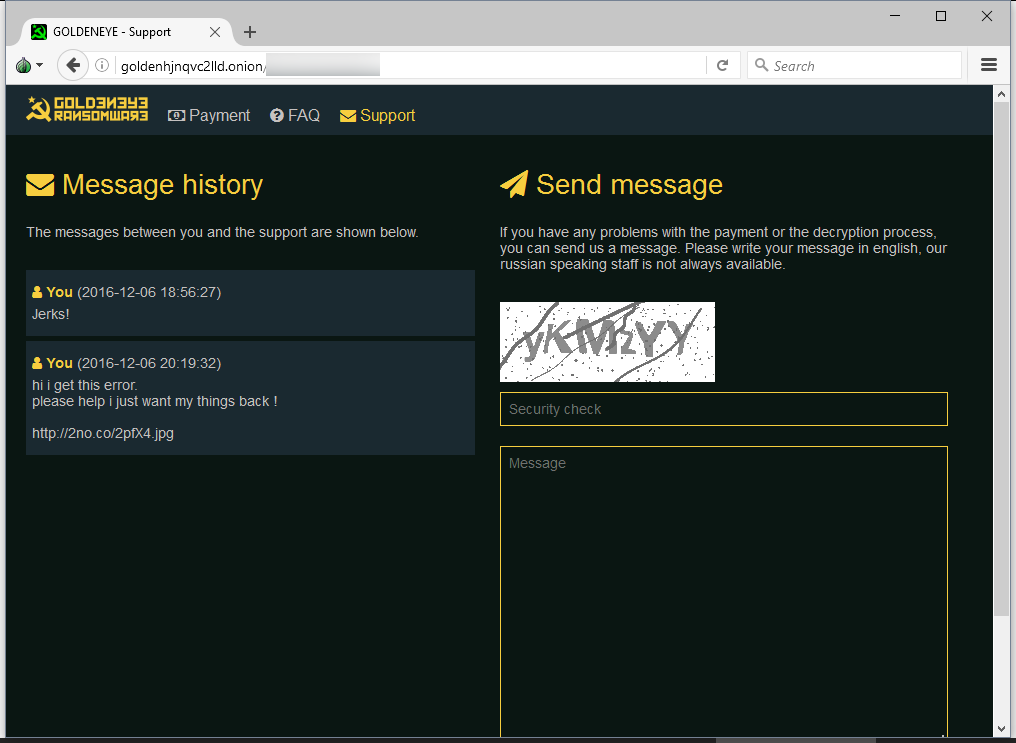
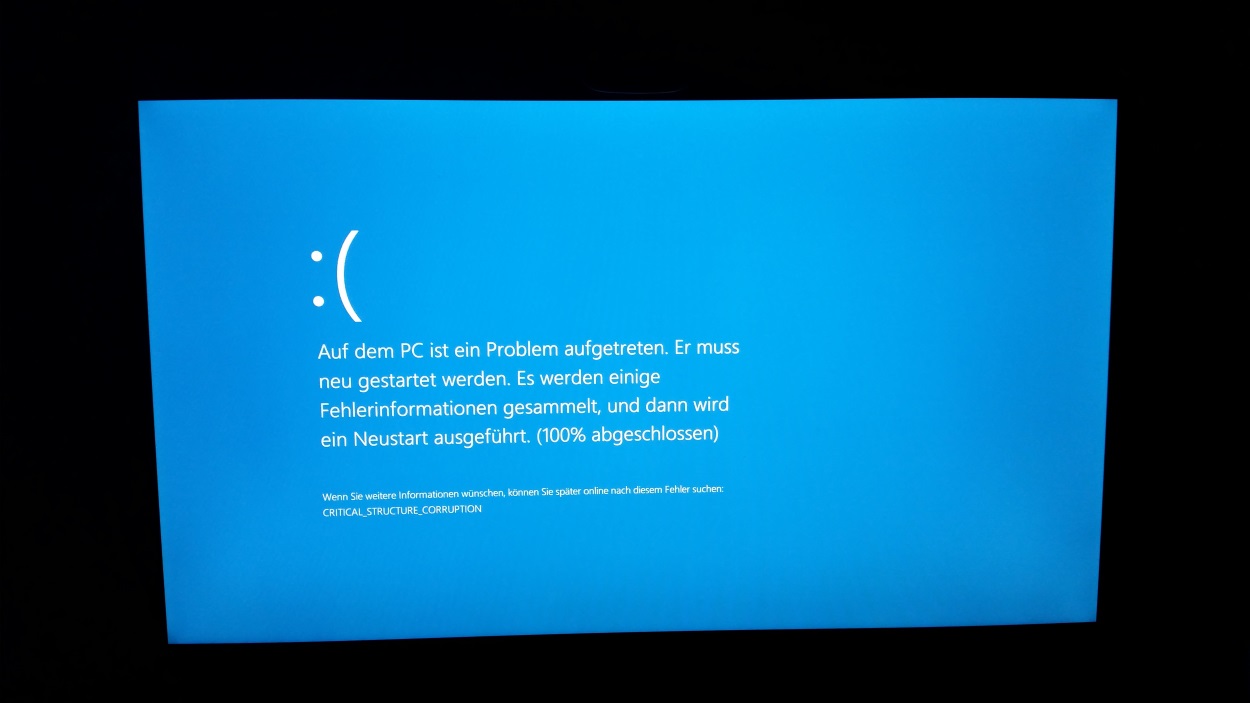
The Dark Web portal also includes a support area, where one user has already reported that GoldenEye has caused his computer to crash.
While GoldenEye tries to pass as a brand new ransomware, its modus operandi, ransom note texts, and about anything else give it away as a rebranded Petya-Mischa combo.
The Petya ransomware first appeared in March 2016, and in its first version only encrypted the MBR and MFT. Because this process caused multiple errors that stopped the encryption process and needed admin privileges to run correctly, in May, its creator added the Mischa file encryptor component to Petya, so to encrypt files to “classic” way, in case the HDD encryptor fails.
The man responsible for Petya and Mischa is a cyber-criminal that goes by the name of Janus, who up until October 2016 ran the Janus Cybercrime website, where he offered the Petya & Mischa ransomware combo as a RaaS (Ransomware as a Service).
In July, Janus also sabotaged one of his competitors by releasing the decryption keys for the Chimera ransomware.
Janus Syndicate is also the name of the cybercrime syndicate that was featured in the 1995 James Bond film GoldenEye.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











