In what has become a welcome trend, today another ransomware master decryption key was released on BleepingComputer.com. This time the key that was released is for the XData Ransomware that was targeting the Ukraine around May 19th 2017.
At 12:31PM EST, a new member named guest0987654321 posted a RSA private decryption key in our XData support topic and implied that this was the master decryption key for the ransomware.
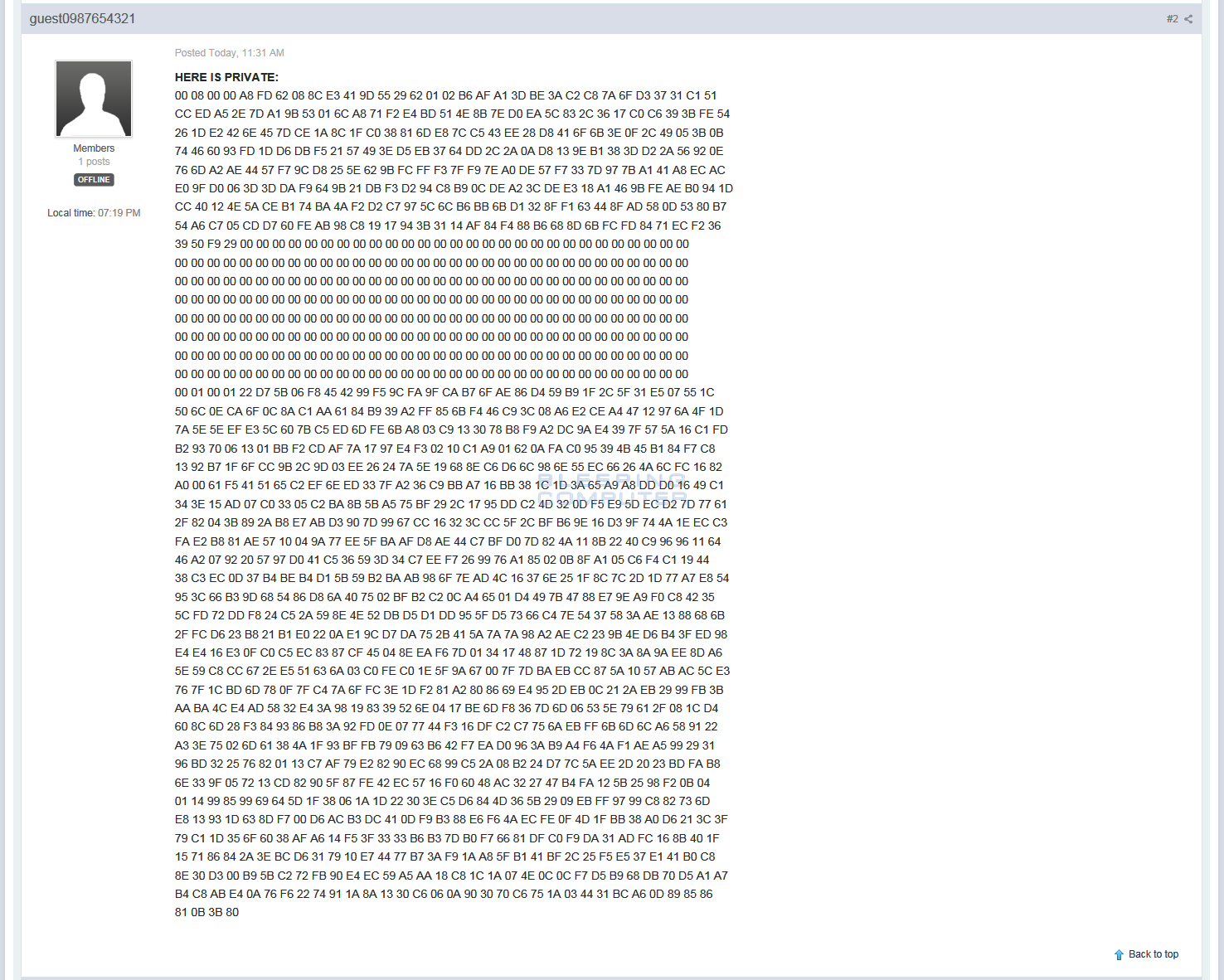
After seeing this post, BleepingComputer notified Kaspersky who quickly confirmed that this was indeed a valid key and updated their RakhniDecryptor to support the decryption of XData encrypted files.
XData Heavily Targeted Ukraine on May 19th
What made XData stand out was that instead of avoiding Russia or CIS countries like many other ransomware infections, XData specifically targeted them. This was especially the case with Ukraine, which was the victim of a targeted campaign on May 19th.
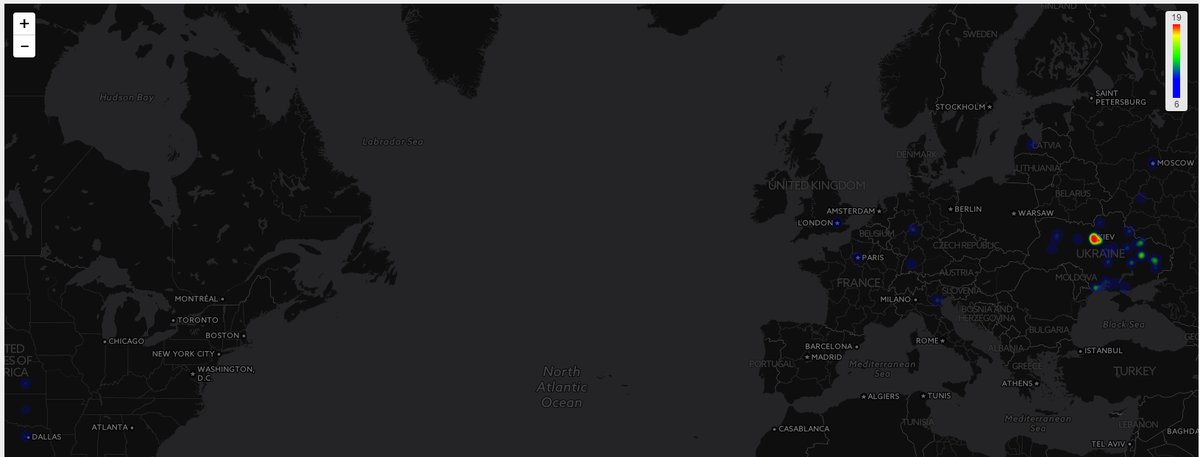
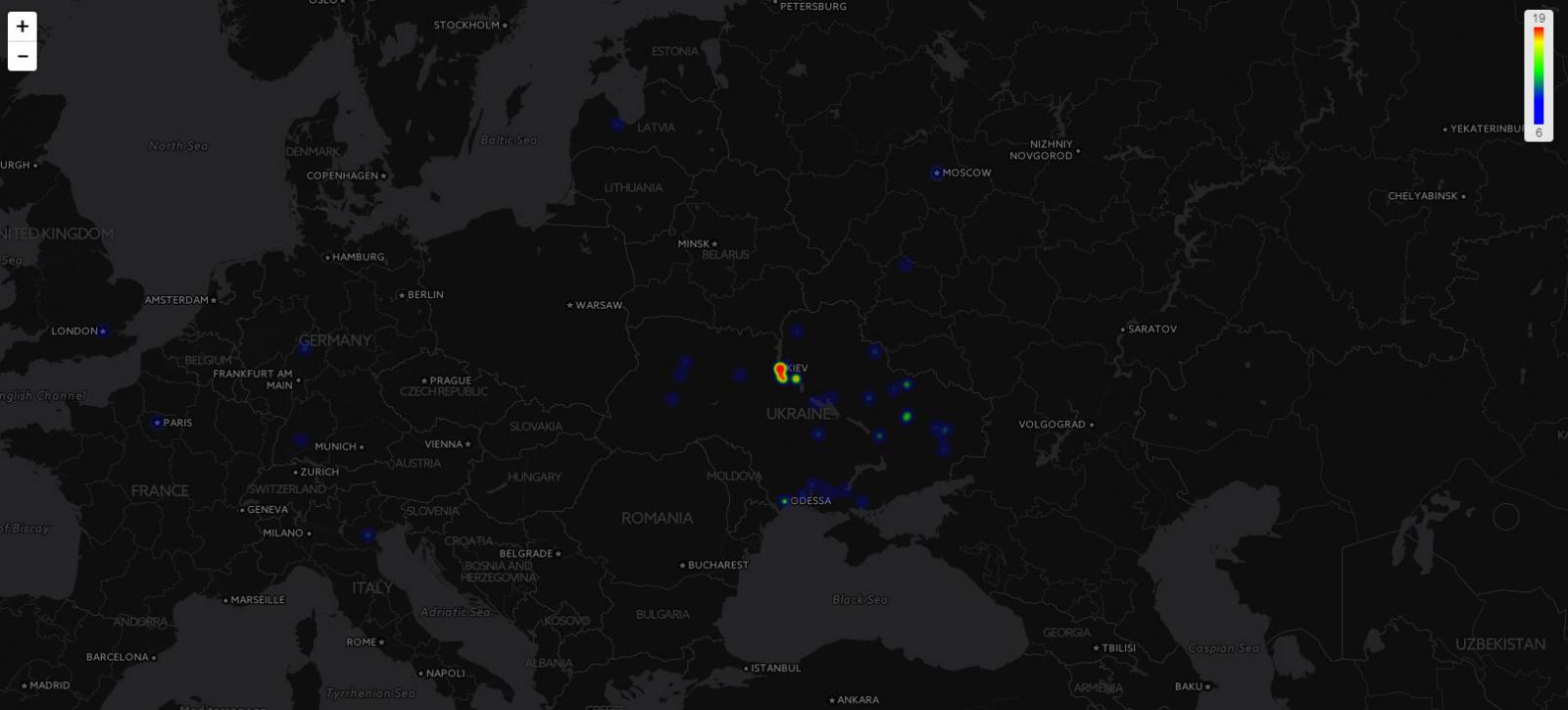
You can see a heat map of submissions to ID-Ransomware on May 19th and can see that the majority of cases were from Kiev and its outlying regions.
How to Decrypt XData Encrypted Files Using RakhniDecryptor
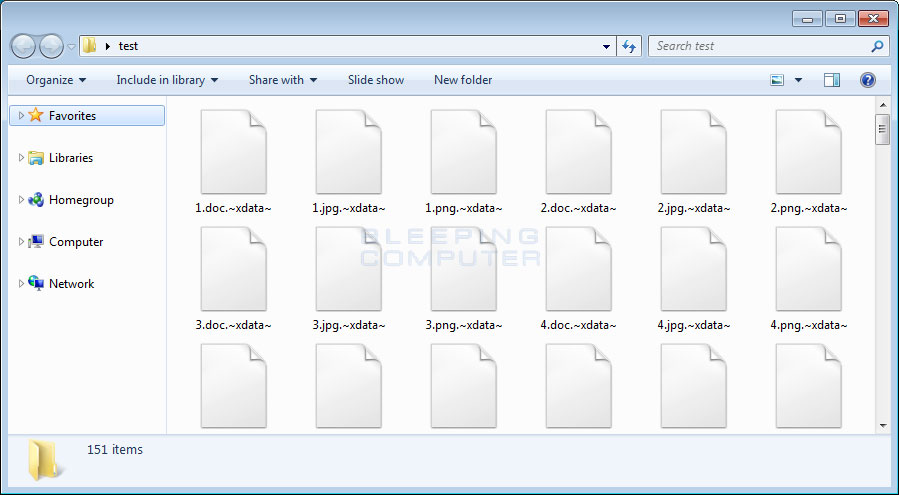
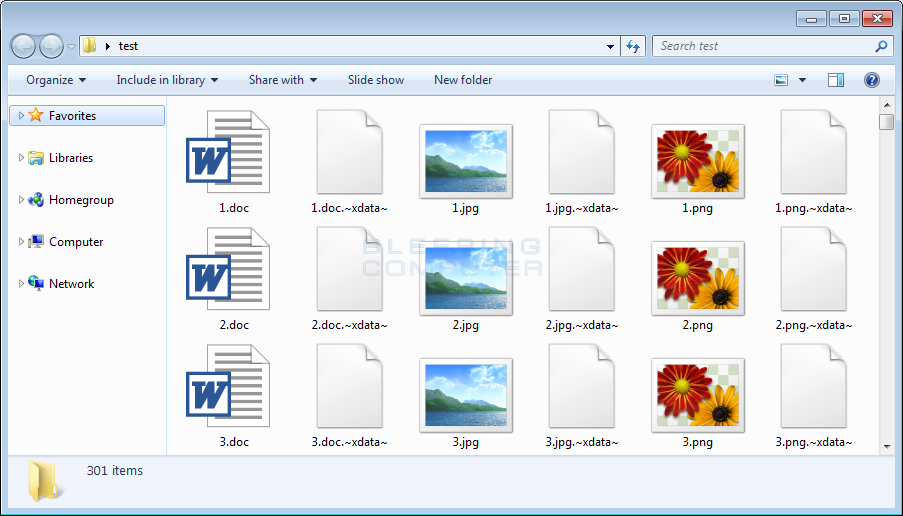
Victims of the XData ransomware can be identified by their files being encrypted and renamed to the format of [filename].~xdata~ or [filename].-xdata-. For example, a recent variant would have a file named test.jpg renamed and encrypted as test.jpg.~xdata~. An example of a folder of encrypted files is seen below:
Before we can begin decrypting XData encrypted files, we first need to terminate the ransomware. To do this, open the Windows Task Manager by pressing the Ctrl+Alt+Delete keyboard combination on your keyboard to open the Windows security screen. Then select Task Manager.
Once Task Manager is open, look for a process named msdns.exe, mssql.exe, or mscom.exe and terminate it by clicking on the End Process button while the process is highlighted. Please note, that there may be other legitimate processes with similar names, so only terminate processes that we specifically listed.
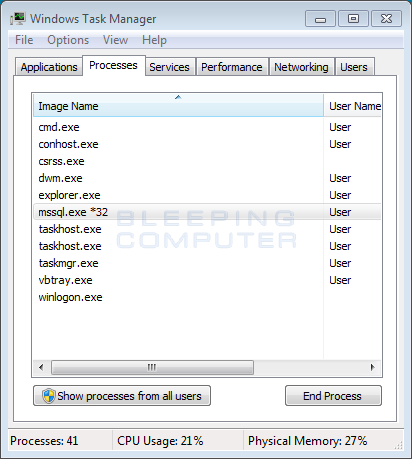
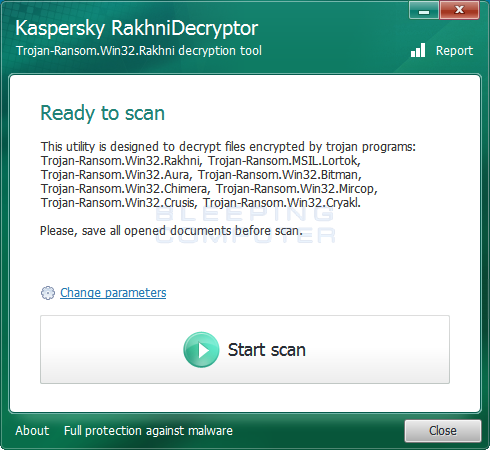
Now that XData is no longer running on the computer, we can begin to decrypt the encrypted files. First you need to download the RakhniDecryptor, extract the program, and then run it. Once running it will display the main screen as shown below.
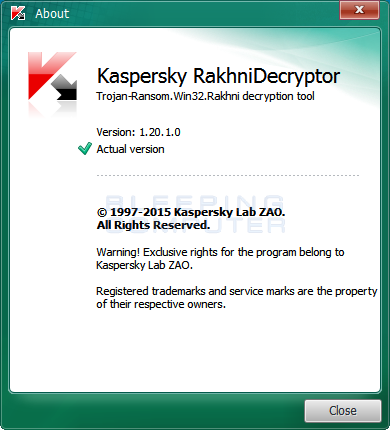
Before starting, you need to make sure that you are using version 1.20.1.0, which supports the XData ransomware. To check the version of the RakhniDecryptor you can click on the About link at the bottom left of the above screen. This will display a small window that shows the version of RakhniDecryptor.
If you are using version 1.20.1.0 or greater, then you should click on the Start scan button and RakhniDecryptor will prompt you to select an encrypted file. Browse to a folder that contains XData encrypted files and select a .Word, Excel, PDF, music, or image file. Do not select a text file as it cannot be used to decrypt the rest of your files.
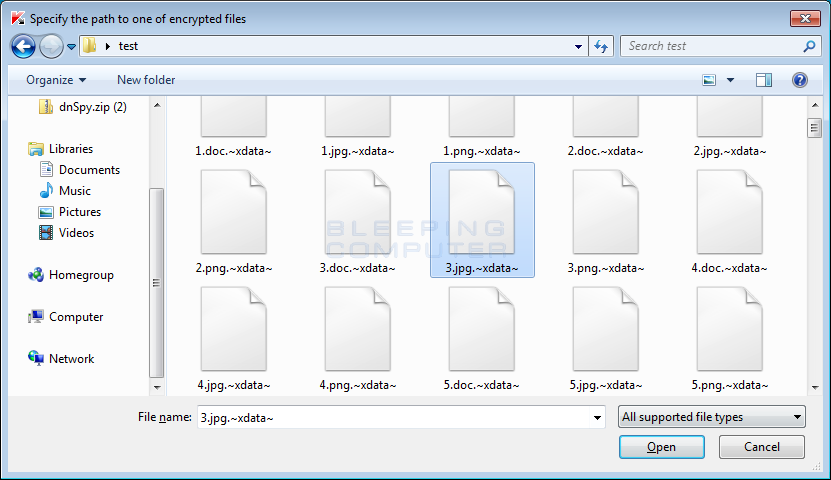
Once you have selected a file, click on the Open button. RakhniDecryptor will now scan the entire computer for encrypted files and decrypt them.
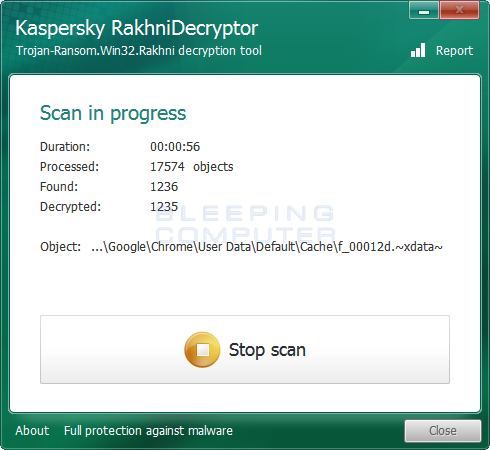
This process can take quite a long time, so please be patient while it scans your computer and decrypts the files.
When it has finished, you will be at a completed screen as shown below.
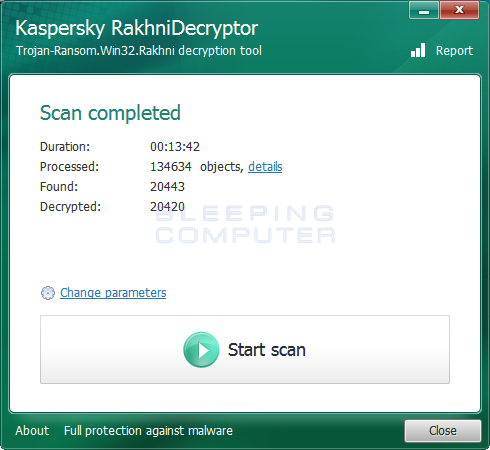
You can then click on the details link to see a full list of XData files decrypted by the decryptor.
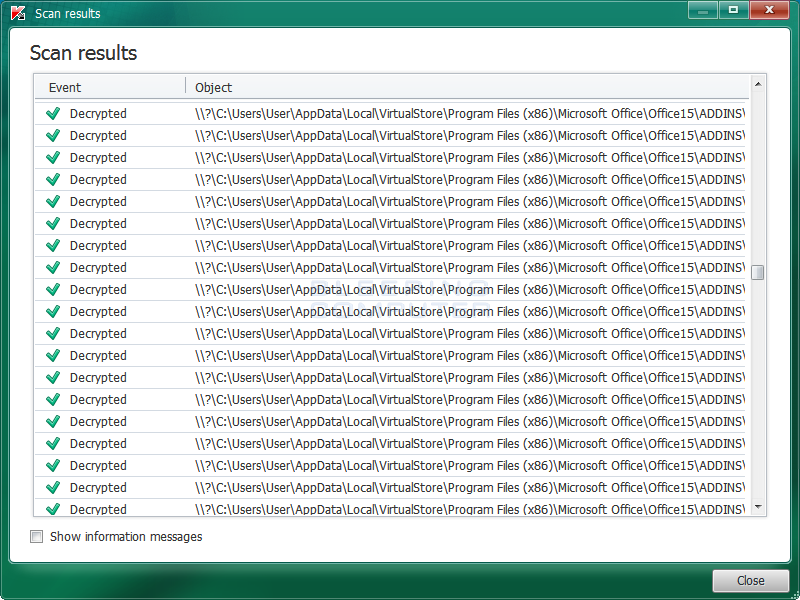
It should be noted that even though your files are now decrypted, the original encrypted files will be left behind.
Though your files are now decrypted, the original encrypted files will still be on your computer. Once you confirm that your files have been properly decrypted, you can use CryptoSearch to move all the encrypted files into one folder so you can delete or archive them.
Now that the files have been decrypted, you can close the RahkniDecryptor program.
Source:https://www.bleepingcomputer.com/news/security/xdata-ransomware-master-decryption-keys-released-kaspersky-releases-decryptor-/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











