How to hijack hundreds of HTTP connections for the modest price of $60 (VPS included)
Because not everyone has QUANTUM capabilities, a poor man’s gotta think about ways of getting inside a target network on the cheap, right?
Typosquatting has been known and abused since the 90’s, mostly for phishing, but is it still profitable for water-hole kind of attacks? Let’s find out!
How often did you type google.co instead of google.com? I hate it when this happens to me, but it’s fairly regular. And it happens everyday to thousands of people out there. So my main idea was to lookup for popular .com websites that has available .co domains and see how bad it can get : testing the scenario of a malicious typosquatted domain hosting an exploit kit. A poor man’s QUANTUM.
For example, the simple omission of a character could be abused with these country top-level domains:
.com -> .cm (TLD of Cameroon)
.com -> .co (TLD of Colombia)
.com -> .om (TLD of Oman)
.net -> .ne (TLD of Niger)
.net -> .et (TLD of Ethipia)
…
You got the idea, there are plenty of domains we could use! For this experiment I’ll use the TLD of Colombia (.co).
Step one: finding popular domains
Let’s grab the top Alexa websites and look for available domains.
Getting the most popular websites is quite easy, here is how to get the top 2000 .com domains:
$ wget https://s3.amazonaws.com/alexa-static/top-1m.csv.zip
$ unzip top-1m.csv.zip
$ cut -d”,” -f 2 top-1m.csv | grep “com$” | rev | cut -d”.” -f 1,2 | uniq | rev | head -n 2000 > top-2000.com.txt
I developed a small Python script to check for domain availability in bulk : 320 .co domains were available out of the top 2000 .com domains (16%). I picked 8 of them for my test, they looked like good candidates (most of the top were ad trackers that people don’t manually type in the address bar, so I removed them out). They all are within the 500th and 1000th most visited website of the world — which should gives us enough room to work with.
Step two: setting up the “watering hole” server
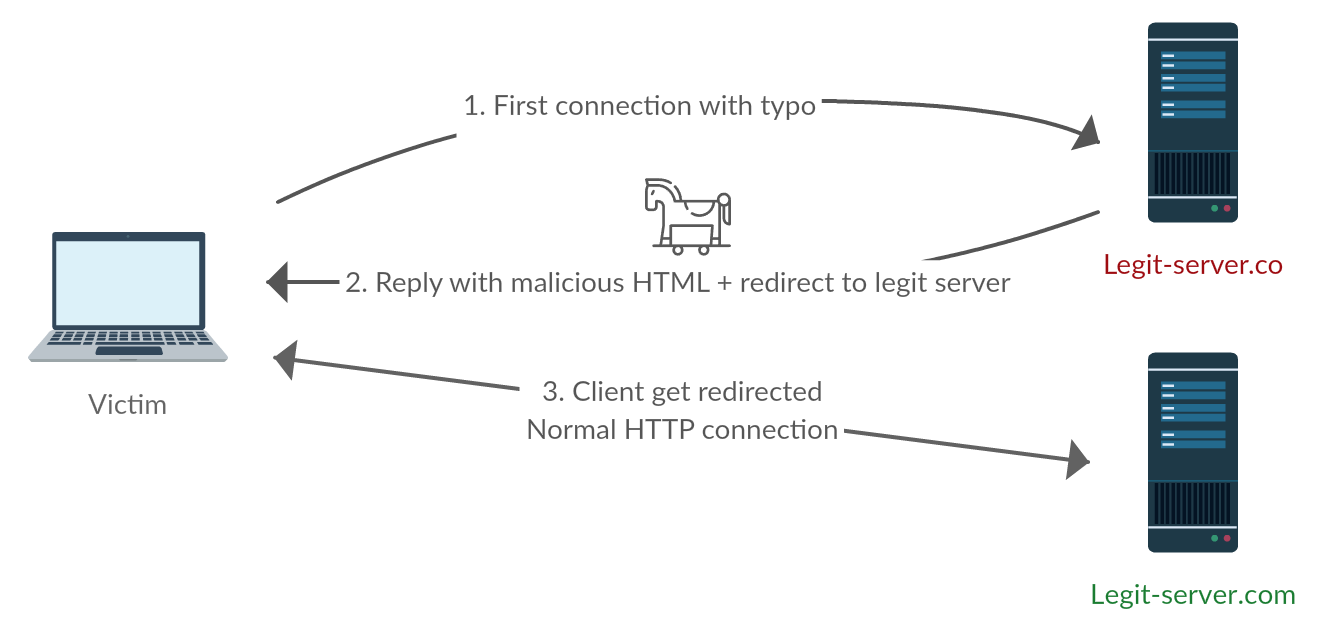
I bought myself a cheap VPS on CockBox for this test (got this sweet IP address geolocated in the Seychelles which is both cool and shady as fuck ?). Setting up a webserver to host the page that will redirect victims is fairly easy (I just installed PHP/MySQL to run a Piwik analytics platform).
The idea is to make incoming visitors load an innocuous JavaScript code and redirect them gently to the intended .com website. Something like this works fine:
Step tree: profit! ?
So now we have all our domain names set up and a server waiting for new victims to come by, sweet!
Pros: it’s rather stealthy, not e-mail based and victims are most likely not going to see what’s happening.
Cons: random results + wait time.
Results and statistics
This experiment lasted 40 days and I got 5430 entries on my log file. Most were crawlers and bots, filtering that out I got 1765 page requests counting 916 unique IP addresses (approximately 23/day) landing on the watering hole server. Looking at the User-Agents, those were actual browsers — people manually typing the URL on the address bar and got the domain wrong, it works!
Sadly, only 392 unique visitors loaded my Piwik JavaScript code. I suspect I got this low result because most people have ad blockers/privacy plugins enabled. Which is kind of a good news, though had I used an actual exploit kit that would have been yet another story…
Interestingly, some “hijacked” domains are producing very local results. A typosquatted Iranian news website is giving a lot of connections coming from Iran, as expected (on the right we can see more than 50% of the traffic was coming from Iran).
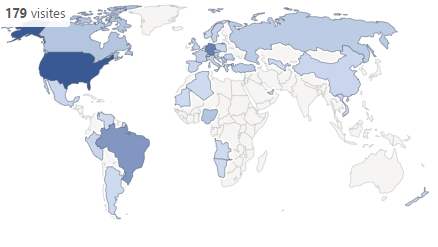
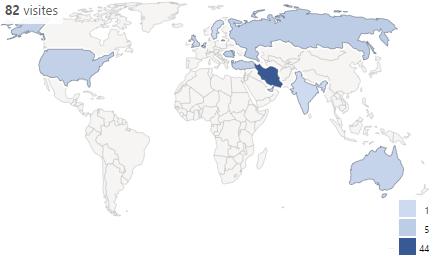
The actual cost of this attack is around $0.05 per click (unique IP), which is cheaper than average advertising PPC (Pay-per-click) for an e-commerce website. As the typosquatted domains I picked are quite popular you could expect different results on other less known domains, but still, very profitable!
WhatsApp leak
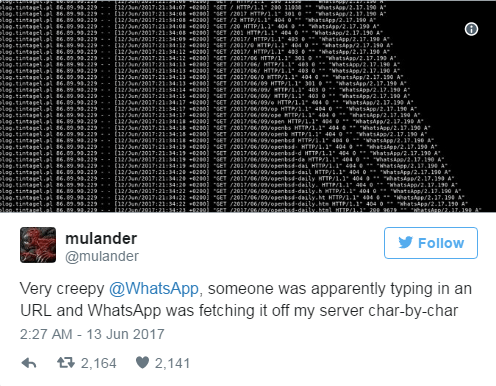
Worth noting, more than 800 connections were made from WhatsApp clients (simple GET / on my watering hole server). Side effect of this research, I suspect this happens when somebody type a complete URL. WhatsApp is known to fetch the website for each keystroke, char-by-char (1 request per keystroke).
Through this data leak, I’m able to see all the IP addresses of people typing one of the 8 real domains I typosqatted on WhatsApp (IP + timestamp), reaching my .co before writing the final M. That’s a terrible privacy issue… *insert facepalm.gif here*
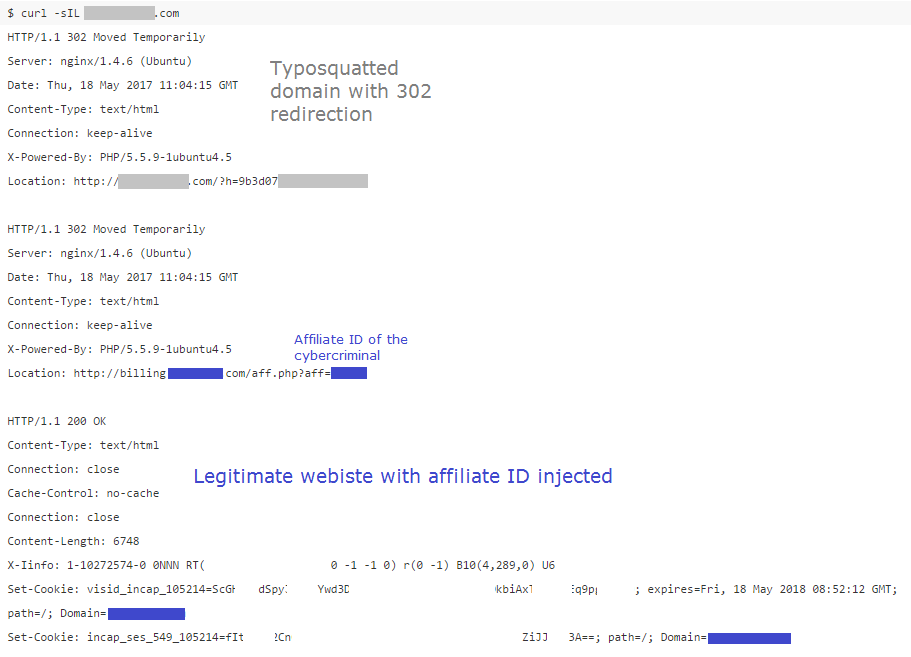
Typosquatting in the wild for affiliate program fraud
We have seen active DNS typosquatting campaigns, notably in Russia, targeting various VPN and hosting providers (credits to dustyfresh for the discovery ?).
The scheme is very smart, they register large amount of typosquatted domains that will be injecting their affiliate ID into a 302 redirect to the legitimate website. Almost invisible to the victim, the attacker will share a part of the profit when the user buys anything from the visited website.
It was confirmed that one group has made $400 this way for one abused company (among many others).
Conclusion
From the statistics we can tell it’s rather unlikely that someone will abuse this to massively spread ransomware, although we have demonstrated it can be used for targeted or opportunistic attacks, whether for fraud or corporate espionage.
For instance, a threat actor might want to use this to infect a computer inside a corporate LAN. Let’s say you’re targeting Random Big Corp and they have a few internal and external domain names, I bet you could buy yourself a few dozens typosquatted domains and get inside in less than a month. Just have to wait a few days/weeks until someone will make a mistake and boom infected[1]: you’re now inside. That’s a very likely scenario.
Source:https://blog.0day.rocks/practical-waterholing-through-dns-typosquatting-e252e6a2f99e

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











