You can get the sample from theZoo
SHA-256: 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7
We can use behavior analysis from hybrid-analysis.
 Seems like there is no known protection mechanism.
Seems like there is no known protection mechanism.
In the strings, there is nothing important other than this base64 encoded string: 
…and imports is not eloquent but there is our friend GetProcAddress: 
Let’s open in IDA:
sub_403760 is used to get necessary Win API functions: 
Inside sub_403760, malware decrytes strings and uses GetProcAddress to get addresses of functions: 
To decrypt strings before call GetProcAddress, Upatre uses following decryption routine: 
Inside sub_402F30 malware uses this teqnique to get addresses for following Win API functions:
NtAllocateVirtualMemory, NtUnmapViewOfSection, CreateThread, WaitForSingleObject, LoadLibraryA, HeapAlloc, RtlAllocateHeap, RtlDecompressBuffer, FlushInstructionCache, NtGetContextThread.
The decryption routine is used heavily by malware in different places to get plain text. 
At 00403572, Upatre decodes base64 encoded string and saves at 004051B0(I renamed variable as decrypted_bin): 
At 0040386D it creates a new thread: 
Main work starts inside the thread at 00403900, Where it decryptes and gets addresses for several Win API functions: CreateProcessW, ExitProcess, NtWriteVirtualMemory, NtSetContextThread, etc. 
Creates itself as a new process in suspended mode and saves Context: 
Decompresses decoded base64 string using RtlDecompressBuffer(format COMPRESSION_FORMAT_LZNT1):  …and writes into suspened process:
…and writes into suspened process: 
Note:
There is one interesting anti-debug trick, at the start it saves PEB and adds BeingDebug value [PEB+2] at different places, outside of a debugger this value is 0 and adding 0don’t causes any error, but if we try to add 1 (which is the value of [PEB+2] if the executable is inside a debugger) it may cause error. In this case RtlDecompressBuffer returns 0xC0000242(STATUS_BAD_COMPRESSION_BUFFER) error.
[eax+2] is the value of BeingDebug: 

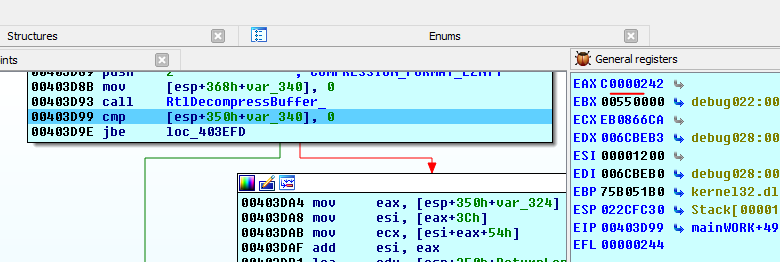 We can use
We can use ScyllaHide plugin for IDA to defeat this anti-debug method.
Back to our analysis, after decompress it calls NtSetContextThread, value of EIP is 401265:  Resumes thread and exits:
Resumes thread and exits: 
Before NtResumeProcess call attach x32dbg to child process and set EIP to 401265: 
Close IDA and start analyzing of the child process.
Tries to read uttE047.tmp file from %TEMP% directory without success: 
Creates one and writes location of the executable: 
Inside of uttE047.tmp file:
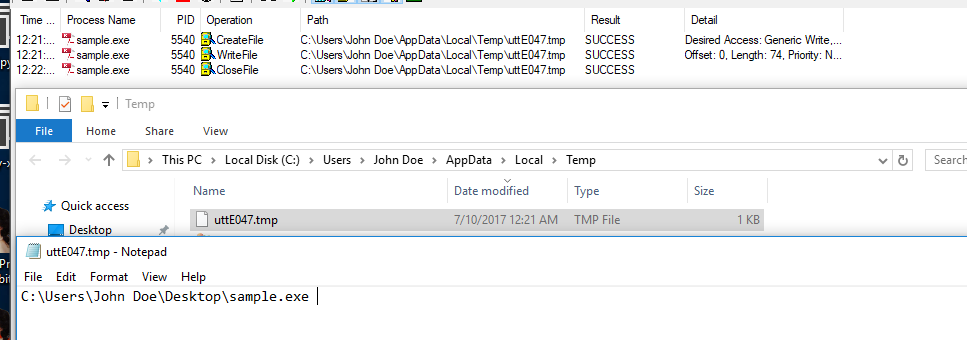
Copies executale to %TEMP% directory as utilview.exe: 
…and creates as new process: 
This process is exactly same as the first process, creates a new process and injects decoded and decompressed code.
Let’s reverse last part (injected code) a little bit higher level.
Now we are here: sample.exe -> sample.exe -> utilview.exe -> utilview.exe
The injected code is also same as before it checks uttE047.tmpfile, but this time there is uttE047.tmp in %TEMP% directory and malware goes a different direction, reads the content of uttE047.tmp, which is the location of the executable and removes that executable: 
After this it gets IP of the victim using checkip.dyndns.com: 
Also, there is a typo in user-agent string: 
and parses IP from returned file: 
It tries to download questd.pdf from https://penangstreetfood.net/wp-content/uploads/questd.pdf and https://yumproject.com/wp-content/uploads/2014/11/questd.pdf without success. 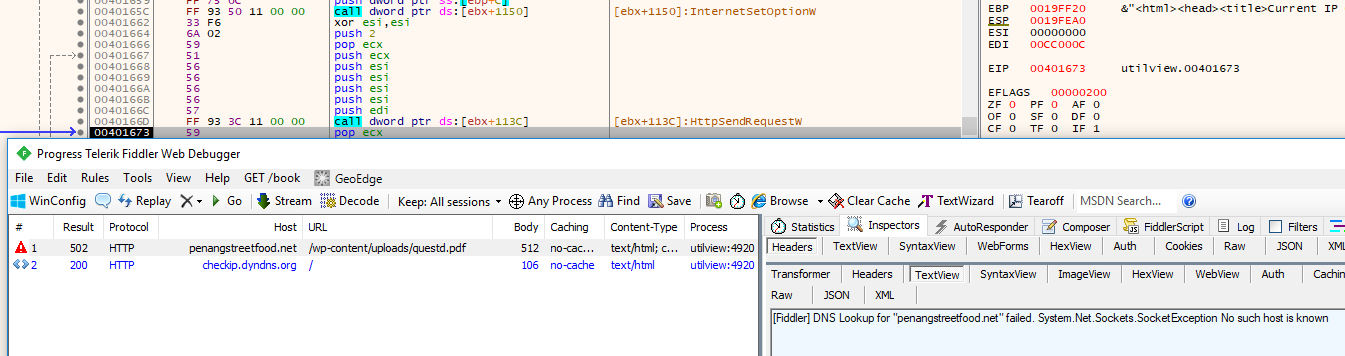
Sends GET requests to 95.181.46.38 with client related information, last string derives from victim’s IP address, Bis instead of . 
That’s all… Upatre’s main function is to download malicious files.
I know, I overlook many things related to Upatre, due to my limited knowledge, if you find something interesting please contact me.
Source:https://secrary.com/ReversingMalware/Upatre/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











