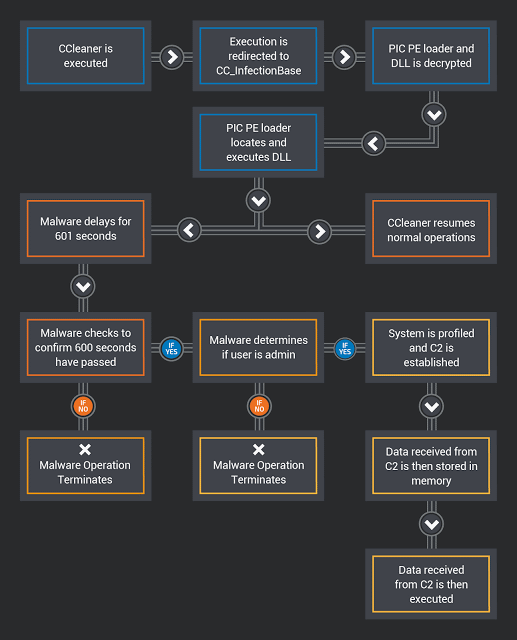
Version 5.33 of the CCleaner app offered for download between August 15 and September 12 was modified to include the Floxif malware, according to a report published by Cisco Talos a few minutes ago.
Floxif is a malware downloader that gathers information about infected systems and sends it back to its C&C server. The malware also had the ability to download and run other binaries, but at the time of writing, there is no evidence that Floxif downloaded additional second-stage payloads on infected hosts.
The malware collected information such as computer name, a list of installed software, a list of running processes, MAC addresses for the first three network interfaces, and unique IDs to identify each computer in part. Researchers noted that the malware only ran on 32-bit systems. The malware also quit execution if the user was not using an administrator account.
Threat actor compromised CCleaner infrastructure
Cisco Talos security researchers detected the tainted CCleaner app last week while performing beta testing of a new exploit detection technology.
Researchers identified a version of CCleaner 5.33 making calls to suspicious domains. While initially, this looked like another case where a user downloaded a fake, malicious CCleaner app, they later discovered that the CCleaner installer was downloaded from the official website and was signed using a valid digital certificate.
Cisco Talos believes that a threat actor might have compromised Avast’s supply chain and used its digital certificate to replace the legitimate CCleaner v5.33 app on its website with one that also contained the Floxif trojan.
It is unclear if this threat actor breached Avast’s systems without the company’s knowledge, or the malicious code was added by “an insider with access to either the development or build environments within the organization.”
Clean CCleaner versions released
Avast bought Piriform — CCleaner’s original developer — in July this year, a month before CCleaner 5.33 was released.
Piriform acknowledged the incident in a blog post today. The company said they found the malware in CCleaner version 5.33.6162 and CCleaner Cloud version 1.07.3191.
On September 13, Piriform released CCleaner 5.34 and pushed an update (v1.07.3214) to CCleaner Cloud users that do not contain the malicious code.
Updating to recent versions removes malware
In an email to Bleeping Computer, Avast CTO Ondrej Vlcek said that updating CCleaner to the most recent recent versions fixes any issues, as “the only malware to remove is the one embedded in the CCleaner binary itself.”
“The affected software (CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191) has been installed on 2.27M machines from its inception up until now,” Vlcek also added. “We believe that these users are safe now as our investigation indicates we were able to disarm the threat before it was able to do any harm.”
“There is no indication or evidence that any additional “malware” has been delivered through the backdoor,” Vlcek added.
Security researchers are now investigating other malware campaigns that appear to have been carried out from Avast’s infrastructre, including a Locky ransomware distribution campaign.
Technical details about the Floxif malware’s mode of operation, infection process, and indicators of compromise are available in a Cisco Talos report here.
Source:https://www.bleepingcomputer.com/news/security/ccleaner-compromised-to-distribute-malware-for-almost-a-month/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











