As has been happening, the problems with the mitigations for the Meltdown fault continue. Recently, information security professional has shown that the Meltdown patch in Windows 10 can be circumvented.
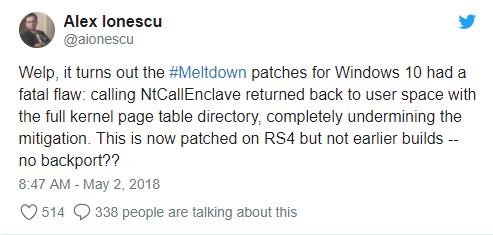
Alex Ionescu, a Windows Internals researcher, found that the Meltdown patch issued for Windows 10 is affected by a serious vulnerability that could be exploited to bypass it.

“Calling NtCallEnclave returned to the user space with the full directory of the kernel page table, completely undermining the mitigation,” he said via Twitter.
Ionescu also commented that Microsoft addressed the flaw with the release of the version of Windows 10 1803, which is the update of April 2018.
Microsoft recognized the problem reported by the information security expert and is currently working on a solution to include in the 1790 version of Windows 10, autumn update, which is the only version, affected.
Attackers could take advantage of Meltdown and Specter attacks to bypass memory isolation mechanisms and access sensitive data.
The CVE-2017-5754 vulnerability, Meltdown, could allow attackers to read the full physical memory of target machines by stealing credentials, personal information and more.
Meltdown exploits the speculative execution to break the isolation between the user’s applications and the operating system, in this way any application can access the system’s memory.
In the good news, we can know that, Meltdown attacks are not easy to perform and the risk of exploitation is considered low.
On the other hand less pleasant, we know that, the timeline for the Meltdown patch is full of problems. Researchers commented on previous occasions that the first release was promptly suspended by Microsoft in January due to instability problems observed in AMD processors.
In previous weeks, information security expert Ulf Frisk reported that part of the security of Meltdown and Specter that Windows updated has serious flaws.
The expert could notice that the security updates of Meltdown and Spectre released by Microsoft in January and February for Windows 7 and Windows Server 2008 R2 Meltdown patch are affected by a vulnerability that attackers could take advantage of to read and write easily in memory. It is believed that an attacker can deploy gigabytes of data per second by exploiting the vulnerability.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











