According to information security experts, GyoiThon identifies the software installed on the web server as OS, Middleware, Framework, CMS, etc. Then, run valid exploits for the software identified using Metasploit. Finally, it generates reports of scan results. GyoiThon executes the previous processing automatically.
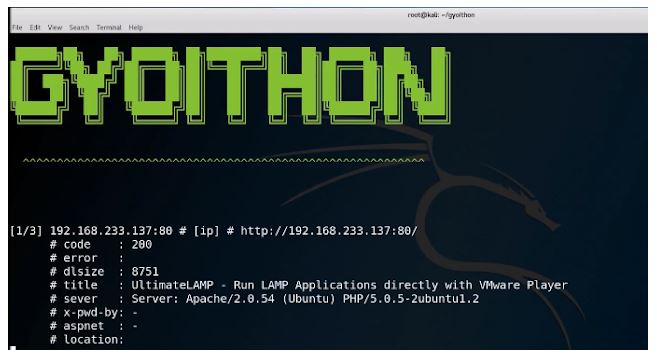
GyoiThon executes steps 1 and 4 automatically. The only operation of the user is to enter the top URL of the target web server in GyoiThon. You can identify vulnerabilities in web servers without so much time and effort.

Step 1. Collect HTTP responses. GyoiThon gathers several HTTP responses from the target website while reviewing the site.
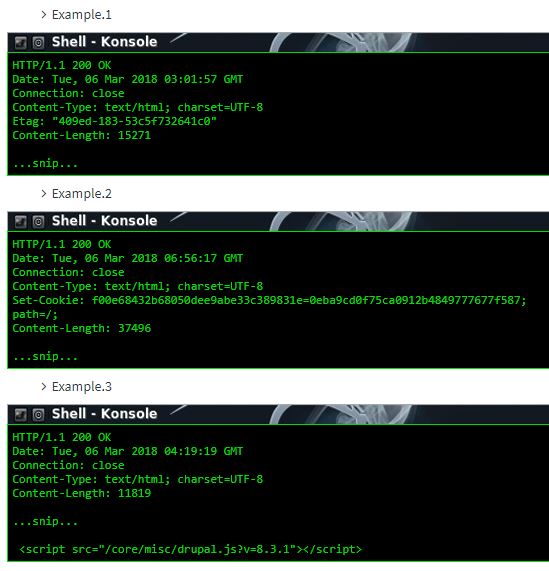
Step 2. Identify the name of the product. The expert comments that GyoiThon identifies the name of the product installed on the web server using the following two methods.
- Based on Machine Learning: when using (Naive Bayes) Machine Learning, GyoiThon identifies the software based on a combination of different characteristics; Etag value, Cookie value, specific HTML tag and others. Unlike the signature database, Naive Bayes is identified stochastically based on several features included in the HTTP response when the software can not be identified in a feature.
Ejemplo: Etag: “409ed-183-53c5f732641c0”
GyoiThon can identify the Apache web server software. This is because GyoiThon learns Apache features, such as “Etag header value (409ed-183-53c5f732641c0).” Apache uses a combination of lowercase letters and numbers as the Etag value and the Etag value is separated by 4-5. 5 digits and 3-4 digits and 12 digits, the final digit is 0 in many cases.
Example 2: Set-Cookie: f00e68432b68050dee9abe33c389831e=0eba9cd0f75ca0912b4849777677f587;
GyoiThon can identify the CMS Joomla !. This is because GyoiThon learns the features of Joomla! as “Cookie name (f00e6 … 9831e)” and “Cookie value (0eba9 … 7f587).
- Based on string matching: GyoiThon can identify the software by matching strings also used in traditional penetration testing tools.
Example: /core/misc/drupal.js?v=8.3.1
Step 3. Exploit using Metasploit. According to the information security expert, in this step, GyoiThon runs the exploit corresponding to the software identified using Metasploit and checks if the software is affected by the vulnerability.

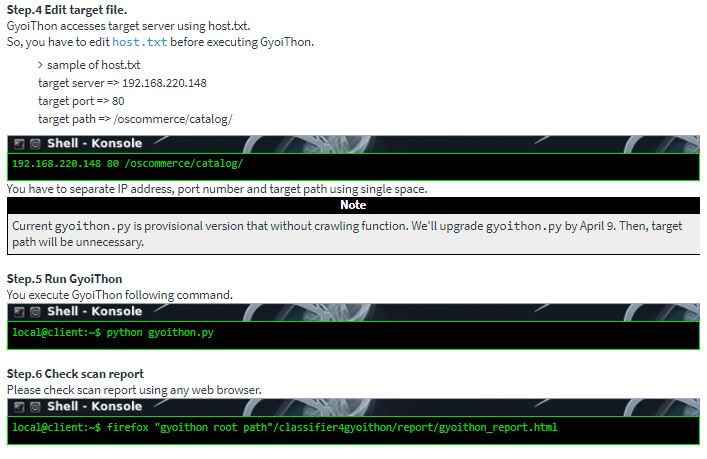
Step 4. Generate scan report. GyoiThon generates a report that summarizes the vulnerabilities. The style of the report is html.


Operation check environment:
- Kali Linux 2017.3 (for Metasploit)
- Memory: 8.0GB
- Metasploit Framework 4.16.15-dev
- ubuntu 16.04 LTS (Host OS)
- CPU: Intel(R) Core(TM) i5-5200U 2.20GHz
- Memory: 8.0GB
- Python 3.6.1(Anaconda3)
- docopt 0.6.2
- jinja2 2.10
- msgpack-python 0.4.8
- pandas 0.20.3

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











