The Android.Trojan.MKero.A malware is making a comeback in Androidland, and this time around, hackers found a method to bundle it with legitimate apps, capable of bypassing Google’s Bouncer app scanning system.
While the malware was first detected in 2014 and was mainly distributed to users installing Android apps from unverified sources, Bitdefender is now reporting on several instances of the trojan being found distributed via the official Google Play Store.
This time around, the malware is packed inside various Android games, and after infecting users it secretly subscribes them to premium SMS services, all without the user having to take any actions.
Using humans to bypass to CAPTCHA filters
According to Bitdefender’s researchers, the malware uses a clever and complex set of procedures that allows it to bypass various security mechanisms put in place by the premium SMS services to prevent fraud.
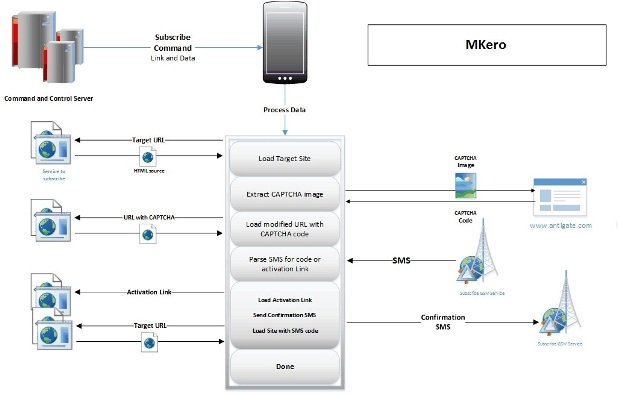
First, once on the infected device, the malware starts communicating with a C&C server, from where the URL of a target premium subscription website is loaded.
Android.Trojan.MKero.A then moves on to extract the CAPTCHA image from the subscription form, image which it sends to antigate.com, a Web service that relies on humans to solve image-to-text CAPTCHAs. (How ironic!)
After receiving the CAPTCHA’s solution from antigate.com, the malware subscribes the user to the service, and after receiving, parsing and extracting the confirmation code from an SMS message, it enters the code on the target website, effectively subscribing the user to the premium service.
Attackers are probably members of various affiliate programs
The purpose of infecting users with Android.Trojan.MKero.A and then subscribing them to these kinds of services is simple. The attacker is probably participating in various affiliates programs in relation to those services, and has monetary gains from each user it brings in.
“Considering the malware has been built with convert capabilities to operate completely silent on the victim’s Android device, user detection and removal is extremely difficult,” says Bitdefender’s Liviu Arsene, who recommends using a mobile antivirus client to perform regular scans of your devices.
Checking your mobile and data bill on regular intervals should also be a good idea, since increased costs that come out of nowhere can be a sign of a malware infection.
Bitdefender’s staff has identified 7 infected gaming apps on Google’s Play Store, all of which have been removed in the meantime.

Source:https://news.softpedia.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.