More than a dozen routers in four countries infected with fully featured implants.
Researchers have uncovered active and highly clandestine attacks that have infected more than a dozen Cisco routers with a backdoor that can be used to gain a permanent foothold inside a targeted network.
The SYNful knock malware has been found on 14 routers in four countries, including Ukraine, the Philippines, Mexico, and India and is likely being used to infect other parts of the targeted networks, researchers from security firm FireEye wrote in a report published Tuesday morning. The malicious router implants are loaded each time the device is powered on and support up to 100 modules, which can be tailored to individual targets. Cisco Systems officials have confirmed the findings and published intrusion detection signatures that customers can use to block attacks in progress.
“The impact of finding this implant on your network is severe and most likely indicates the presence of other footholds or compromised systems,” FireEye researchers wrote in Tuesday’s post. “This backdoor provides ample capability for the attacker to propagate and compromise other hosts and critical data using this as a very stealthy beachhead.”
The initial infection doesn’t appear to exploit any vulnerabilities in Cisco devices. Rather, attackers seem to be taking advantage of routers that use passwords that are factory default or are somehow otherwise known. The detailed FireEye report comes five weeks after Cisco warned customers of a series of attacks that completely hijacked critical networking devices. The attacks, Cisco said, worked by replacing valid “ROM monitor or “ROMMON” firmware images used to boot Cisco devices.
The FireEye report gave no details about the organizations that the 14 infected routers belonged to and whether the people behind the attacks are working for a state-sponsored spy agency or a criminal organization motivated by financial gain. In an interview with Reuters, FireEye CEO Dave DeWalt said, “That feat is only able to be obtained by a handful of nation-state actors.” In any event, there’s no doubt that the devices were infected by a professionally developed and fully featured backdoor. The researchers wrote:
Implant summary
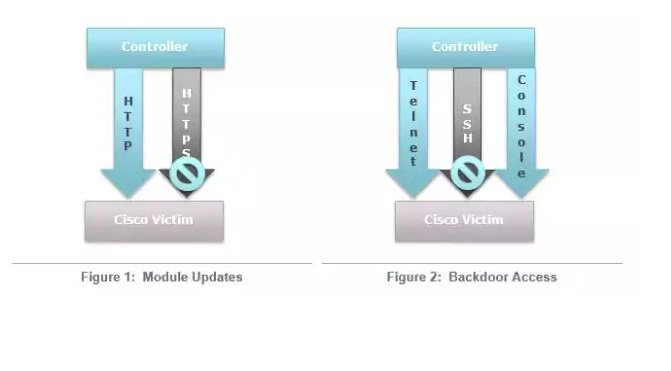
The implant consists of a modified Cisco IOS image that allows the attacker to load different functional modules from the anonymity of the internet. The implant also provides unrestricted access using a secret backdoor password. Each of the modules are enabled via the HTTP protocol (not HTTPS), using a specifically crafted TCP packets sent to the routers interface. The packets have a nonstandard sequence and corresponding acknowledgment numbers. The modules can manifest themselves as independent executable code or hooks within the routers IOS that provide functionality similar to the backdoor password. The backdoor password provides access to the router through the console and Telnet.
Known affected hardware
- Cisco 1841 router
- Cisco 2811 router
- Cisco 3825 router
Note: Our initial identification revealed that other models are likely affected based on the similarity in core functionality and IOS code base.
Persistence
The implant resides within a modified Cisco IOS image and, when loaded, maintains its persistence in the environment, even after a system reboot. However, any further modules loaded by the attacker will only exist in the router’s volatile memory and will not be available for use after reboot. From a forensic standpoint, if the modules are loaded in volatile memory, one can analyze them by obtaining a core dump of the router image.
Details
Modifications to the IOS binary can be broken down into the following four functions:
- Modify the translation lookaside buffer (TLB) Read/Write attributes
- Modify a legitimate IOS function to call and initialize the malware
- Overwrite legitimate protocol handling functions with malicious code
- Overwrite strings referenced by legitimate functions with strings used by the malware
Given that routers typically operate outside the perimeter of firewalls and many other security devices, router-based backdoors make the ideal hacking tool. Not only can they be used to monitor communications coming into and going out of the targeted organization, they can also be used to infect other sensitive hardware inside the same network. Such attacks have been theorized for years, but this is one of the first times researchers have found concrete evidence that such compromises are occurring in the wild. It wouldn’t be surprising for similarly advanced backdoors to exist for routers made by Cisco competitors as well.
The post goes on to offer several commands that administrators can use to tell if equipment they maintain has been infected. While the attacks at the moment appear to affect only a small number of poorly secured routers, it’s not a bad idea for people to inspect their gear, since so little is currently known about this string of compromises. In the early stages of many investigations, it’s not unusual for researchers to miss important clues or see only a small part of a much larger pattern. Administrators who want help diagnosing their gear can e-mail researchers at synfulknock-at-fireeye.com.
Source:https://arstechnica.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.