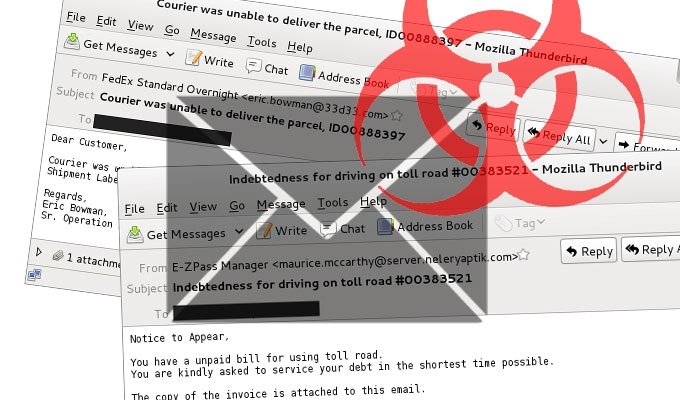
A malicious spam campaign that’s been doling out zipped Javascript (.js) files remains an issue, the SANS Internet Storm Center warns.
The campaign was spotted earlier this year, but Brad Duncan, a handler for the site and researcher with Rackspace’s information security operations center, claims he’s received a handful of notifications from other users who have seen the same emails, which prompted him to look into it again.
Once victims receive the spam emails, open the attachments, and run the .js files, they open themselves up to a slew of different types of malware, including Corebot, Kovter, and Miuref, according to a report Duncan published on SANS’ InfoSec Handlers Diary Blog.
Duncan first published something on the spam in July and despite there not being a huge shift in the campaign since, he decided to post an update Wednesday to stress how often the ISC has come across it.
“We’re still seeing it on a daily basis,” Duncan said of the emails when reached by Threatpost, “That means it’s a useful endeavor for the criminals behind this campaign. The same goes for any of the phishing campaigns we find from our spam filters on a near daily basis.”
Duncan claims the spam, which comes disguised as plaintext emails from American Airlines, FedEx, the IRS, and other phony sources, is being propagated via a botnet.
According to the writeup, Duncan said the attachment is a JavaScript downloader that grabs three malicious executables from the Web. Like it did in July, post-infection traffic also triggered alerts from the clickfraud Trojan Kovter.B and the Trojan Miuref. A newer strain of malware, the credential-stealer-turned banking-Trojan Corebot, was also detected in the traffic, Duncan claims.
Duncan writes that the emails wouldn’t make it past most users’ spam filters but notes that hasn’t seemed to stop attackers from carrying out the campaign.
“Either a significant percentage of people will infect themselves given the chance, or enough vulnerable hosts exist that establishing or renting this type of botnet is dirt-cheap. Or both,” Duncan said.
Paul Burbage, a researcher with Phish.Me, took a deeper look at a botnet purportedly behind some of the malicious spam late last week. Burbage, who was able to retrieve the PHP server-side code from a script associated with one of the spam emails, believes the attackers behind the campaign are using an affiliate model to distribute malware via botnet, or exploit kit operators.
Source:https://threatpost.com

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.