New Android malware was discovered, able to steal money from online banking accounts, and hide SMS notifications coming to confirm financial transactions.
This new malware detected by Dr.Web as the Android.SmsBot.459.origin trojan infects users via SMS spam, which, to be more convincing, in some cases even uses the phone owner’s name. The spam SMS message contains a link, which, if opened, will forcibly download the trojan’s APK file on the user’s device.
The only way to actually get infected is to tap and open the APK file, so if a Web page just downloads an Android app on your phone without asking you anything, don’t even think of opening it. Ever!
The trojan masquerades as a legitimate app
For users who are so “unlucky” to tap and open the APK, the trojan will mask itself as an app coming from a well-known source, in this case, as a client application for an advertising website in Russia.
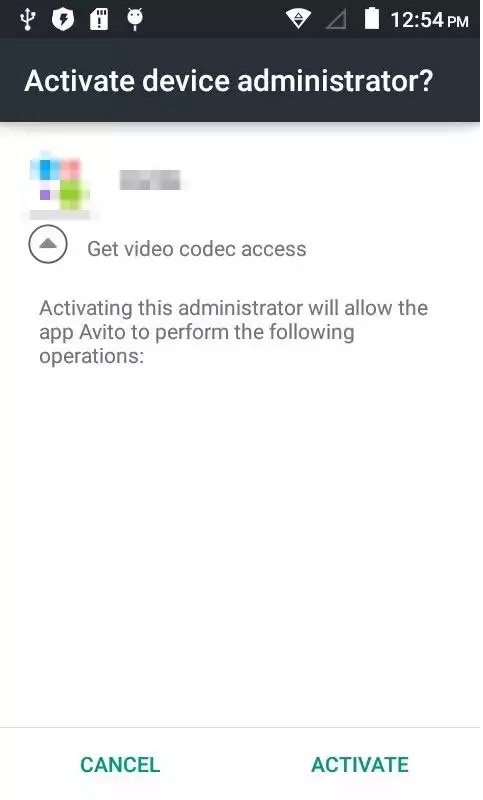
If the user agrees to install it, the app will immediately ask for admin privileges with the purpose of “getting video codec access.” This message is quite pushy and won’t go away until the user clicks “Activate.” As a side note to the article, popups that cannot be closed should be another sign that an app contains malware.
Once successfully installed and with admin privileges, the trojan now starts operating with its C&C server. The first thing it will do is to send all kinds of details about the user’s phone, beginning with its IMEI, model name, system language, mobile phone number, OS version, and so on.
The malware currently targets Russian users
Once this data is on the C&C server, the Android.SmsBot.459.origin trojan is then instructed to scan the device for a list of banking applications. For now, this trojan only scans for applications catering to Russian banks.
If banking applications are found, using pre-configured operations, the trojan will get the user’s account balance, trying to discover if they have any available funds.
Using special commands and SMS messages, the trojan then moves on to initiating financial transactions, stealing the victim’s money and moving it to another account, controlled by the attackers.
To keep all its actions hidden, the Android.SmsBot.459.origin trojan will hide any incoming SMS alerts the banking portal may be sending the user as a confirmation for their transactions.
The trojan uses a clever trick to hide SMS messages from phone owners
Even if Google engineers have made it impossible for SMS messages to be hidden on Android devices, the creators of the trojan found a clever way around this measure by disabling sound alerts, uploading SMS messages to the C&C server after they’re received, and immediately deleting them before the user ever notices anything.
By operating with a high degree of stealth, if the user does not have a mobile antivirus installed, Android.SmsBot.459.origin is very hard to identify until it’s just too late.
This Android malware can pose a multitude of problems if ever extended to cater to Western countries, or if its attackers find a more covert way of installing it with administrative permissions on infected devices, without needing any kind of user interaction. A way to achieve this would be by chaining together multiple Android vulnerabilities, just as Brain Test did, recent Android malware we reported on.
Source:https://news.softpedia.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











