A recent spam campaign is leading users to a fake PayPal app which steals their real credentials, but also comes hard-coded to target other mobile banking applications.
With more and more smartphones being produced and sold around the world, users are changing their daily habits, and instead of checking bank accounts from their desktops, laptops, an ATM or by going to the bank, they are now relying more on their smartphones for this trivial task.
This exact behavior is what cyber-criminals are now leveraging, creating malware that infects smartphones and steals data from legitimate banking applications.
The most recent example of such malware is the one discovered by Trend Micro, detected in their virus database as AndroidOS_Marchcaban.HBT.
The banking trojan is spread with the help of a spam campaign
This malware is spread via a classic spam campaign, which right now only targets German-speaking users. The campaign seems to be run from hijacked servers or from behind VPNs,Trend Micro reporting that the IP addresses used to send out the emails are located all across the globe, with most of them being in Vietnam (41%), while the rest are in the Ukraine, Russia, Brazil, and India. The company says it detected more than 14,000 instances of these spam messages.
If users are so foolish to click on the links, they are then redirected to a website where they are offered to download a (fake) PayPal app, bundled with the malware.
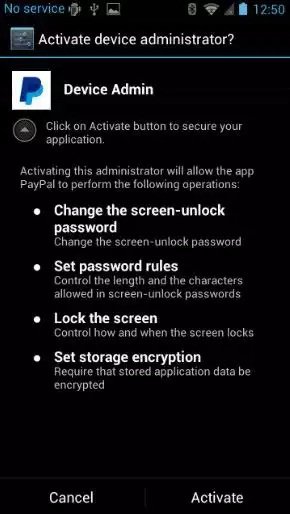
While it is not recommended to install Android apps from outside the Google Play Store, not all users know this, and some will do it. The users who install this particular app will get the AndroidOS_Marchcaban.HBT malware which, as soon as it finds itself on the user’s device, will request “Device Administrator” rights.
In case the user grants them, as with other malicious software, this one too will hide itself and run in the background, only coming to life when banking applications are started, extracting details and sending them to a C&C server.
The malware uses a fake UI to steal PayPal credentials
A particularity for this malware is the fact that “once the malware detects the real PayPal app running, it will put up a fake UI on top of the real one, effectively hijacking the session and stealing the user’s PayPal credentials.”
Additionally, to avoid being detected, the malware also intercepts transaction confirmation SMS messages, which it hides from the device’s user. In case a phone call is needed to an automated number, the malware can perform this operation without any difficulty.
Besides PayPal, AndroidOS_Marchcaban.HBT also targets users of the Commerzbank online banking app, one of Germany’s biggest banks.
The easiest way to avoid contamination with these kind of apps is to download them only from the official Play Store, and also run a mobile antivirus app on your phone.
Source:https://news.softpedia.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.