Group used Angler Exploit kit to push ransomware on unsuspecting Internet users.
Security researchers have disrupted an online criminal operation they estimated drew $30 million per year pushing ransomware on unsuspecting people browsing the Internet.
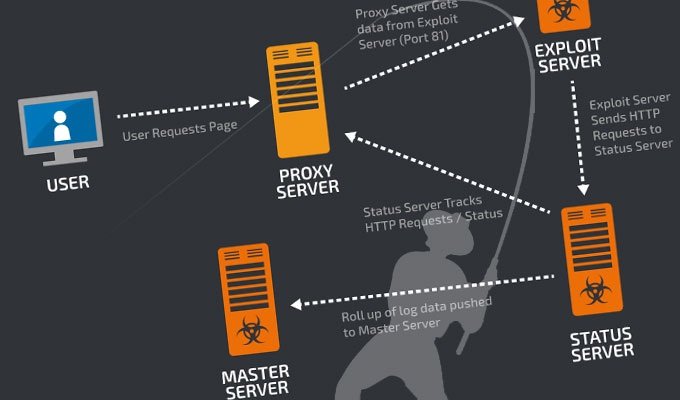
The takedown was performed by investigators from Cisco Systems’ Talos security unit, which was researching the Angler Exploit kit. The hack-by-numbers tool is sold in underground crime forums to people who don’t want to go through the hassle of developing and testing exploits themselves. Angler is one of the most potent of the exploit kits available, with the ability to successfully infect an estimated 40 percent of the end users it targets using attack code that surreptitiously exploits vulnerabilities in browsers and browser plugins. In most cases, the security flaws have already been patched, but, in some cases, the kits exploit zero-day vulnerabilities for which there is no currently available fix.
The Talos researchers quickly noticed that a large percentage of infected end users were connecting to servers operated by service provider Limestone Networks. After getting the cooperation of Limestone and examining some of the servers responsible for carrying out the operation, the researchers found that the single operation was targeting as many as 90,000 end users per day. They estimated that if just three percent of targets paid the average ransom demand of $300, the operation would generate more than $30 million in 12 months. The estimate is consistent with log files retrieved from just one of the servers accessed by Talos researchers. It showed the operation generating more than $3 million.
“This is a significant blow to the emerging hacker economy where ransomware and the black market sale of stolen IP, credit card info and personally identifiable information (PII) are generating hundreds of millions of dollars annually,” Talos researchers wrote in a report published Tuesday about the takedown.
Ransomware came into vogue in 2013 with the rise of a malicious title known as CryptoLocker. It got installed either by posing as a benign piece of software or through an exploit kit such as Angler. Once installed, CryptoLocker silently encrypted all files stored on hard drives or network devices and then demanded $300 in semi-anonymous bitcoins to provide the decryption key. After the past two years, huge numbers of people—including some inside police departments, government agencies, and small- and medium-sized businesses—have fallen victim to scores of copycat campaigns.
Talos estimates that the now-shuttered operation was responsible for about half of the Angler activity its researchers have observed. The researchers observed Angler being used to distribute non-ransomware payloads as well, including what’s known as the Bedep downloader, which is malware that delivers additional payloads. Talos also saw malware used in click fraud scams and several instances of keyloggers.
“It’s one of the most innovative exploit kits available today, but it doesn’t have a large footprint from an infrastructure perspective,” they wrote referring to the Angler. “Despite not having a large footprint, Angler is able to compromise a significant amount of users, for a presumably small amount of customers.”
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.