HE CONVICTION OF former Reuters employee Matthew Keys on hacking charges this week has renewed focus on a controversial federal law that many say prosecutors are using incorrectly and too broadly to inflate cases and trump up charges.
The Computer Fraud and Abuse Act, or CFAA, is a federal law that was designed to target malicious hackers who obtain unauthorized access to protected computers. But judges have used it in a number of controversial cases to, for example, prosecute and convict a woman for violating MySpace’s user agreement, and to convict a former Korn/Ferry International employee for violating his employer’s computer use policy. It was also used to indict internet activist Aaron Swartz for downloading scholarly articlesthat he was authorized to access.
The CFAA is back in the news this week after a judge used it to convict former Reuters social media editor Matthew Keys for conspiring with members of Anonymous in a hack against the Tribune Company, one of his previous employers. Keys faces a possible maximum prison sentence of 25 years for his involvement in the hack, although he’s likely to get much less—between six months and three years—given his lack of a past criminal record and the various other elements that judges use to calculate sentences.
Regardless of this, his conviction is complicated by what his lawyers say was the government’s wrongful and deceptive use of irrelevant losses to assess damage to the victim. They say Keys was charged under one provision of the CFAA—causing unauthorized damage to a protected computer—but prosecutors then calculated losses for activity that were unrelated to this charge and that caused no damage to a computer.
They say the government did this in order to inflate the losses and elevate Keys’ computer crime from a mere misdemeanor to a felony. The CFAA requires a minimum of $5,000 in losses to qualify as a felony.
The Tribune Company and prosecutors have alleged losses of more than $900,000, which they arrived at by calculating man-hours it took for its workers to respond not only to the breach, but also to taunting emails that Keys sent to his former Tribune Company colleagues. But Tor Ekeland, lead defense attorney for Keys, says the email activity has been wrongly lumped with the breach of a Tribune server. Sending a handful of harassing emails to someone doesn’t qualify as a hack, nor did it damage or impair Tribune computers.
“Typically people think damages has to do with loss of money, but damages have nothing to do with money under the CFAA,” Ekeland told WIRED. “Damage under the CFAA is [supposed to be about] simple impairment of the computer system. But there was no impairment [in this regard]—it was just a bunch of emails.”
The amount of losses isn’t just important for determining whether Keys should have been charged with a misdemeanor or a felony, however. It can also have a profound effect on his sentencing.
“The higher your loss numbers are, is a big factor in sentencing,” Ekeland said.
Defense attorneys raised this issue at trial, but Ekeland says the jury was likely confused by the complicated issues around the losses and didn’t know what to make of them. He thinks they have a strong case for appeal, however—one that could set a precedent for how losses are calculated under the CFAA going forward.
“Fundamentally, this case is about the definition of loss under the CFAA and that definition’s relationship to the definition of damage under the CFAA,” Ekeland told WIRED. “And I think it’s potentially a big case about the CFAA in terms of the government conflating the unauthorized access and the unauthorized damage provisions.”
The US Attorney’s office in Sacramento, which tried the case, declined to address the details of Ekeland’s assertions.
“Those issues were brought up in trial,” spokeswoman Lauren Horwood told WIRED. “The jury heard the evidence, and they brought back a verdict of guilty. And the matter of the loss is something that will be brought up at sentencing.”
The Case Against Keys
Keys was a deputy social media editor for the Reuters news agency when he was charged with providing the log-in credentials for a server owned by the Tribune Company. Prior to working for Reuters, Keys had been a web producer for the television station KTXL FOX 40 in Sacramento, which is owned by the Tribune Company. After a disagreement with his superiors in October 2010, he lost his job—though there are conflicting opinions about whether he was fired or quit before he could be fired.
Two months later he was in an online chat forum frequented by people affiliated with Anonymous when, using the online nickname “AESCracked,” he identified himself as a former Tribune Company employee and disclosed the username and password for a Tribune server. He encouraged members of Anonymous to use the credentials to “go fuck some shit up.”
A hacker going by the name “Sharpie” subsequently used the credentials to access a Tribune server and make a minor alteration to the headline of a Los Angeles Times news story—the equivalent of digital graffiti. The Los Angeles Times is owned by the Tribune Company, and both the Times and Fox 40 shared the same network and login credentials at the time.
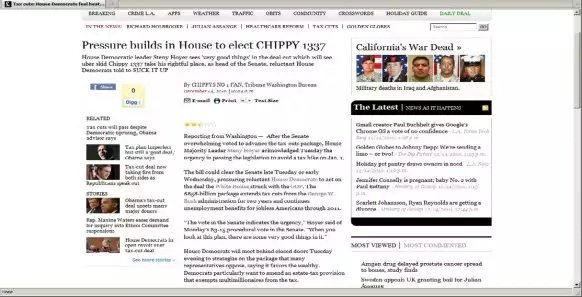
When Sharpie told Keys what he’d done, Keys replied “nice,” according to the indictment and a transcript of the chat. Within an hour, however, the Tribune’s system administrators had discovered the defaced article, fixed the headline, and disabled the credentials Sharpie had used. When he told Keys he’d lost access to the server, Keys tried to regain access for him but could not.
“I’m locked out for good,” he wrote, adding a sad-face emoticon.
Keys was charged in the Eastern District of California with three counts—conspiracy to cause unauthorized damage to a protected computer, transmission of computer code that resulted in unauthorized damage of a protected computer, and attempting to transmit malicious code to cause unauthorized damage.
But rather than restrict the charges to the actual breach and defacement of the headline, prosecutors also factored in actions they attribute to Keys between October and January, which they claim caused “aggregate” loss. For example, after Keys’s job with the television station ended, the station had to expend some effort to regain control of its Twitter and Facebook accounts, which Keys had previously managed for the station.
During the month when Anonymous defaced the LA Times article, a Tribune worker was also repeatedly locked out of her server account. Prosecutors say that Keys used his old credentials to gain entry to the Tribune server and repeatedly deactivate his former colleague’s login credentials. This forced her and the IT department to spend time resetting them, sometimes leaving the woman unable to work for hours while she waited for the problem to be resolved—hours that prosecutors then calculated as part of the losses related to the hack. Prosecutors could never definitely tie these incidents to Keys, however.
Station employees also began receiving a series of anonymous emails sent from someone they began calling “Cancerman” from various addresses, including cancerman4099@yahoo.co.uk, walterskinner5099@yahoo.co.uk, and foxmulder4099@yahoo.co.uk. The emails accused the station of being unethical and of violating the privacy of viewers through certain actions. Employees say they cited things that only Keys could have known about. Although Keys later acknowledged to law enforcement in a written statement that he had sent some emails to former colleagues, emails that he characterized as “more or less hooliganism” meant to antagonize his former colleagues, it’s never been proven that the “Cancerman” emails specifically were from him.
“Cancerman” said in email that he had obtained a list of emails of about 20,000 viewers who had signed up for the television station’s affinity program and that he planned to spam them with emails denouncing the station’s misconduct, according to Motherboard, which covered the trial.
Even though the criminal charge against Keys were about the LA Times breach and alteration of the news story, the Tribune calculated as part of its losses all of the employee hours spent responding to Cancerman’s email taunts and responding to viewers who complained about receiving the spam.
Brandon Mercer and Jerry Del Core, employees of the station, said they spent “scores of hours” trying to identify the source, prosecutors wrote a court document (.pdf). “They did this in meetings among management, counsel, and law enforcement. Mercer even had consensually recorded meetings with Keys in order to help the FBI figure out if Keys was the one behind the theft and misuse of Fox 40’s contact list.”
The Tribune Company also calculated “scores of hours” that employees spent responding to the breach of the Tribune server after the news story was altered. Although the defacement of the headline was fixed in a matter of minutes, there was time spent determining how the breach occurred and what else the intruders might have accessed and touched.
The government used the hourly rate of salaried Tribune employees to estimate the losses and justified this by saying that “costs associated with investigating intrusions into a computer network and taking subsequent remedial measures are losses within the meaning of the statute.”
Keys’ Best Defense
Keys’ attorneys argue that the government’s assessment of losses was based on “irrelevant, misleading, and inadmissible” evidence.
Simply stating that employees spent a certain number of hours responding and remediating a breach is not sufficient, they argued in a motion to the court. Without testimony from an expert verifying that the nature of the response and the amount of time spent was reasonable, “the government or a third party witness could greatly inflate CFAA loss,” they wrote in a court document. In fact, there are suggestions that Tribune staff might indeed have inflated the numbers to achieve the threshold for a felony case.
Source:https://www.wired.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











