The number of countries deploying it grows to 32.FinFisher, a piece of spyware sold to governments by a German security vendor, has been linked by recent research to at least 32 governments around the world, more than ever before.
Citizen Lab, a research department at the University of Toronto, has been studying the usage of FinFisher among government agencies for the past years.
The spyware, developed by FinFisher GmbH, a German security company in the same realm as Italy’s Hacking Team, has been selectively sold to government agencies to help with law enforcement investigations.
FinFisher used in the past for illegal government surveillance
This doesn’t mean that governments used it for true and valid reasons alone, and many states, like Ethiopia and Bahrain, were previously caught utilizing it to deter and keep dissidents in check.
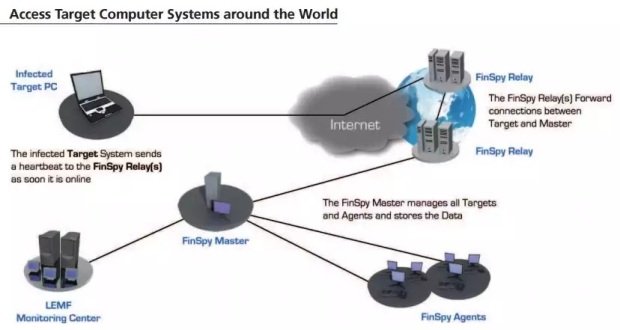
The way the spyware works is by relaying information from infected computers to a C&C server using intermediary proxies, known as relays, similar to the Tor network but without the complex encryption system.
While in the past Citizen Lab researchers could not differentiate between FinFisher relays and C&C servers, recent breakthroughs allowed the research team to detect subtle differences between the two, allowing them to map various FinFisher networks around the globe.
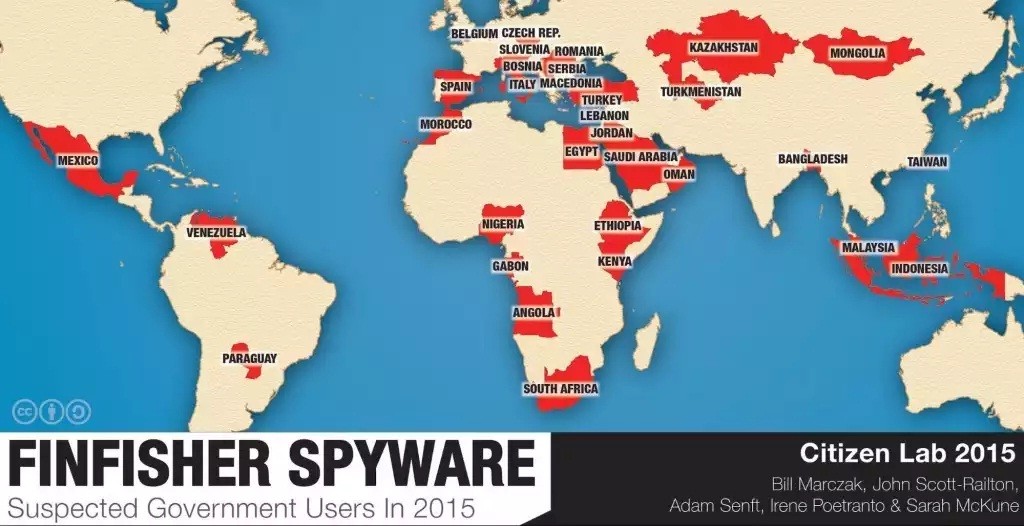
According to their research, there are currently 32 countries that deploy FinFisher spyware, more than ever before. In total, Citizen Lab observed 135 FinFisher instances, a mix of both relays and master servers.
The 32 countries that deploy FinFisher spyware are: Angola, Bangladesh, Belgium, Bosnia and Herzegovina, the Czech Republic, Egypt, Ethiopia, Gabon, Indonesia, Italy, Jordan,Kazakhstan, Kenya, Lebanon, Macedonia, Malaysia, Mexico, Morocco, Nigeria, Oman,Paraguay, Romania, Saudi Arabia, Serbia, Slovenia, Spain, Taiwan, Turkey, Turkmenistan,Venezuela, and South Africa.
The names in bold are countries that hadn’t been observed deploying FinFisher spyware prior to this research.
Additionally, the Citizen Lab research also managed to identify and pinpoint the IP address of FinFisher C&C servers to official IPs belonging to 10 government agencies from various countries.
Worse is the fact that some relay servers from various countries were located in other countries, opening the door for inter-state snooping.
The FinFisher GmbH data breach helped the company gain more visibility for its product
While FinFisher GmbH suffered a data breach in 2014, just like the Hacking Team suffered in June 2015, the 40GB of data spilled in that incident did not reveal a widespread usage of FinFisher spyware. What’s surprising is that the numbers spiked after the incident, showing that the data breach helped the company gain more publicity for its hacking tools, which seem to have spread to more countries compared to similar data disclosed via WikiLeaks documents.
“The market for intrusion software like FinFisher is challenging to track because the key players, from government customers to software developers, have a strong interest in keeping transactions private,” say the Citizen Lab researchers.
“As customer lists grow, so should concern over the documented abuse potential of intrusion software. Some governments clearly believe that it can be used, with proper oversight, in the service of legitimate criminal investigations and intelligence gathering. However, there are also well documented cases in which government customers have abused intrusion software to compromise political opponents within their borders, and overseas,” they add.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.