THE CHIP-ENABLED CREDIT card system long used in Europe, a watered down version of which is rolling out for the first time in America, is meant to create a double check against fraud. In a so-called “chip-and-PIN” system, a would-be thief has to both steal a victim’s chip-enabled card and be able to enter the victim’s PIN. But French forensics researchers have dissected a real-world case in which criminals outsmarted that system with a seamless chip-switching trick—and pulled off the feat with a slip of plastic that’s almost indistinguishable from a normal credit card.
French computer security researchers at the École Normale Supérieure university and the science and technology institute CEA late last week published a paperdetailing a unique case of credit card fraud they analyzed as investigators in a criminal case. Five French citizens (whom the researchers didn’t name in either their paper or an interview with WIRED) were arrested in 2011 and 2012 for using a clever workaround to spend nearly 600,000 euros (about $680,000) from stolen credit cards in spite of the cards’ chip-and-PIN protections. Through an investigation that included microscopic analysis and even X-ray scans, the researchers discovered that the now-convicted fraudsters actually altered stolen credit cards to implant a second chip inside of them, capable of spoofing the PIN verification required by point-of-sale terminals.
The French fraudsters took advantage of a long-known but theoretical vulnerability in chip-and-PIN systems to execute what the researchers describe as a “man-in-the-middle” attack that takes advantage of how cards and card readers communicate. When a buyer inserts his or her card and enters a PIN, the card reader queries the card’s chip as to whether the PIN is correct. A fraudulent chip can listen for that query and pre-empt the real chip with its own answer: a “yes” signal regardless of whatever random PIN the fraudster has entered. “The attacker intercepts the PIN query and replies that it’s correct, whatever the code is,” says ENS researcher Rémi Géraud. “That’s the core of the attack.”
The ENS and CEA forensic researchers note that the vulnerabilities used by the French fraud they analyzed have since been fixed—at least in Europe—though they declined to fully detail the new security measures. EMVCo, the consortium responsible for the chip-and-PIN standard, didn’t respond to WIRED’s request for comment. Nonetheless, cases like the French PIN-spoofing attack show that motivated criminals were able to defeat what EMVCo long considered an unassailable system.
A Long Time Coming
The PIN-spoofing trick the French forensics team detected was first demonstrated in 2010 by a group of Cambridge University security researchers. But their proof-of-concept attack relied on an FPGA—a kind of highly customizable chip—mounted on a board that fit into a box the size of a large bible and connected to laptop running their attack software. The Cambridge team showed the BBC how the FPGA kit could be connected to a credit card and hidden inside of a backpack to successfully bypass chip-and-PIN security and allow a thief to use a stolen card for purchases.
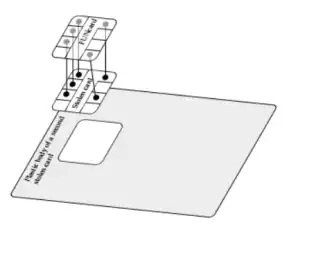
The French criminals, by contrast, miniaturized that backpack setup into a tiny FUNcard chip, a cheap, programmable device used by DIY hobbyists. That FUNcard chip, unlike the Cambridge researchers’ FPGA kit, was no bigger than the normal security chip used in credit cards; the fraudsters could remove the chip from a stolen card, solder it to the FUNcard chip, and glue both chips back-to-back onto the plastic body of another stolen card. The result was a stealthy device capable of performing the Cambridge researchers’ PIN-bypass technique while appearing to be little more than a slightly bulging credit card. “It was small enough they could fit the whole attack inside the card and use it to buy things in stores…It would be a bit harder to put it into the reader, but not so hard that you’d suspect anything,” says Géraud. “It was quite clever, quite hard to detect, and for some time they managed to evade detection.”
The fraudsters eventually created 40 of the PIN-spoofing forgeries from credit cards stolen in France, and used them to buy large quantities of lottery tickets and cigarettes from Belgian stores. After more than 7,000 fraudulent transactions, a French banking body known as the Economic Interest Group noticed the pattern of stolen cards being used repeatedly at a few locations. “They’d always buy at the same places, and that’s how they got caught,” says Géraud. In May 2011 police arrested a 25-year-old woman who had been making the in-person purchases. They followed up with arrests of four more members of the fraud ring—including the engineer who built the group’s ingenious card forgeries—across three French cities.
X-Ray Investigation
Even after seizing the card forgeries, the French forensic researchers say they weren’t allowed to fully disassemble the fraudulent cards to analyze them—they were still being preserved as evidence in the five fraud suspects’ trial. So instead, they examined one of the devices with non-invasive X-ray scans that revealed a hidden FUNcard logo on a chip inside. Then they reverse engineered the forged card’s computational activity by analyzing its use of electricity when inserted into a card-reader; the timing of the card’s power use revealed the same man-in-the-middle attack they recognized from the Cambridge demonstration from 2010, which the researchers say convinced a judge to allow them to fully disassemble the device and confirm its PIN-spoofing mechanism.
For the Cambridge researchers, the French attack is an “I-told-you-so” moment. Five years ago, EMVCo and the UK Cards Association both dismissed their attack as improbable or impossible. “Optimistic would be a polite way to describe the response we got,” says Steven Murdoch, one of the researchers who’s now a fellow at the University College of London. “I’m not surprised that criminals pulled this off, though I’m impressed that they did it in a way that’s significantly more sophisticated than our proof-of-concept.”
The French researchers write in their paper that EMVCo has since created new countermeasures to the vulnerabilities the fraudsters exploited and implemented them both in card readers and in banking networks. According to their paper, at least some chip-and-PIN card readers now send a command to verify a PIN before the user even enters it to check if the card responds with a spoofed “verified” signal. They also note that other protections have been added to the system at the network level, which they decline to detail for fear of tipping off criminals.
Even so, Géraud hesitates to claim that new security measures couldn’t also be circumvented—the attack he and his colleagues analyzed shows just how far criminals will go to outthink a security system. “Can it be done now? Maybe,” he says. “Awareness has been raised, the system has been equipped with countermeasures. But it’s impossible to say that no attacker would try.”
Source:https://www.wired.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.