Exploits can be used to snoop on encrypted traffic and cause debilitating outages.

Serious weaknesses in the Internet’s time-synchronization mechanism can be exploited to cause debilitating outages, snoop on encrypted communications, or tamper with Bitcoin transactions, computer scientists warned Wednesday.
The vulnerabilities reside in the Network Time Protocol, the widely used specification computers use to ensure their internal clocks are accurate. Surprisingly, connections between computers and NTP servers are rarely encrypted, making it possible for hackers to perform man-in-the-middle attacks that reset clocks to times that are months or even years in the past. In a paper published Wednesday titled Attacking the Network Time Protocol, the researchers described several techniques to bypass measures designed to prevent such drastic time shifts. The paper also described ways to prevent large numbers of computers from successfully connecting to synchronization servers.
The attacks could be used by malicious actors to wreak havoc on the Internet. An attack that prevented sensitive computers and servers from receiving regular time-synchronization updates could cause malfunctions on a mass scale. In many cases, such denial-of-service hacks can be carried out even when attackers are “off-path,” meaning the hacker need not have the ability to monitor traffic passing between a computer and NTP server.
Going back in time
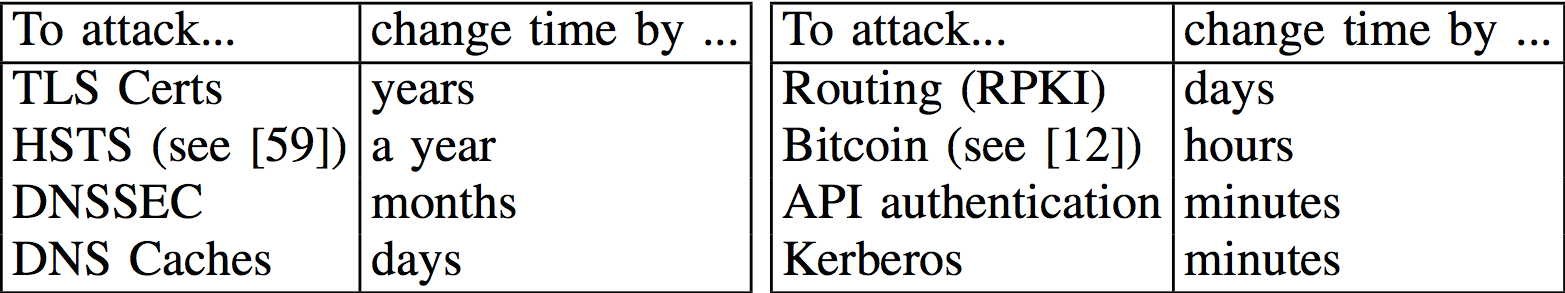
Even worse, the attacks can be used to snoop on encrypted traffic or to bypass important security measures such as DNSSEC specification preventing the tampering of domain name system records. The most troubling scenario involves bypassing HTTPS encryption by forcing a computer to accept an expired transport layer security certificate.
The researchers wrote:
An NTP attacker that sends a client back in time could cause the host to accept certificates that the attacker fraudulently issued (that allow the attacker to decrypt the connection), and have since been revoked. (For example, the client can be rolled back to mid-2014, when > 100K certificates were revoked due to heartbleed.) Alternatively, an attacker can send the client back to a time when a certificate for a cryptographically-weak key was still valid. (For example, to 2008, when a bug in Debian OpenSSL caused thousands of certificates to be issued for keys with only 15-17 bits of entropy.) Moreover, most browsers today accept (non-root) certificates for 1024- bit RSA keys, even though sources speculate that they can be cracked by well-funded adversaries; thus, even a domain that revokes its old 1024-bit RSA certificates (or lets them expire) is vulnerable to cryptanalytic attacks when its clients are rolled back to a time when these certificates were valid.
Besides HTTPS and DNSSEC, other security measures that could be defeated include HTTP strict transport security. The researchers also said NTP attacks could be used to trick Bitcoin users into rejecting legitimate entries in the official blockchain for the digital currency, or to tamper with user authentication systems used by websites.
It’s not clear how practical some of the attacks would be in real-world settings. A desktop computer with a clock that was set to a date months or years in the past would almost certainly be easy to detect. And it wouldn’t be surprising if the incorrect time would trigger errors from the operating system or other applications. Still, it’s likely the attacks could be used in limited settings, or in combination with other hacks. It also might be possible to briefly reset the clock to an earlier date to observe an encrypted Web session, and then change it back right afterward.
Another limiting factor to such attacks is a measure built into the NTP specification that’s designed to prevent time changes of more than about 16 minutes. Once the time change exceeds the “panic threshold,” the client computer is supposed to reject the instruction and record an error. But the researchers said this measure can be defeated in at least two ways. One is to employ a technique known as a “small-step-big-step” attack that makes the change gradually. Another bypass method involves using NTP to reset the time immediately after a targeted computer has rebooted. The reboot time reset function is turned on by default in some operating systems.
Wednesday’s paper comes 21 months after miscreants exploited separate NTP weaknesses to visit crippling denial-of-service attacks on game sites. The previously unseen amplification technique allowed a small number of attackers with limited bandwidth to bombard the targets with more than 100 gigabytes per second of junk traffic. Last December, attack code was published that exploited what was then newly discovered vulnerabilities in NTP implementation and in the process put countless servers at risk of remote hijacks.
Got crypto?
One of the key weaknesses making the attacks possible is the difficulty of ensuring computers communicate only with legitimate NTP servers. While it’s possible to use symmetric encryption to cryptographically authenticate an NTP service, keys are difficult to acquire. The National Institute for Standards and Technology, for instance, distributes keys only to users who register using US mail or facsimile, and they’re required to resend the application each year. The US Naval Office has a similar procedure. There’s separate measure known as Autokey that’s also designed to cryptographically verify that a client is connected to a valid NTP server, but many servers don’t support it.
Boston University researchers have published an information page that helps people diagnose and remedy NTP weakness both on client computers and servers that provide the time-synchronization service. At a minimum, clients and servers alike should run NTP version 4.2.8p4 available here. There are a variety of other configuration settings that can be applied to better lock down the service as well.
Source: arstechnica.com

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











