Researchers have found out that hackers took over around 900 CCTV cameras with weak login credentials and used them as a DDosS botnet that runs all around the world.
According to the researchers from Incapsula, it was really easy for hackers to hack into these CCTV cameras by conducting a simple brute force attack.
Researchers further believed the team responsible for configuring the devices was one to blame because either they didn’t change the default password or left it opened for outside connections.
While researching on the compromised devices, they found the hacked CCTV cams were running BusyBox (a stripped-down version of the Linux operating system) which is built for loT devices having limited resources and memory.
Once the systems were compromised, .btce malware was left behind by the hackers. The malware is specifically designed for BusyBox setups that run on HRM architectures.
When the hackers got complete hold of the devices they use them to launch DDoS using HTTP GET request floods.
Here is a geo location map of the hacked CCTV cams involved in DDoS attacks:
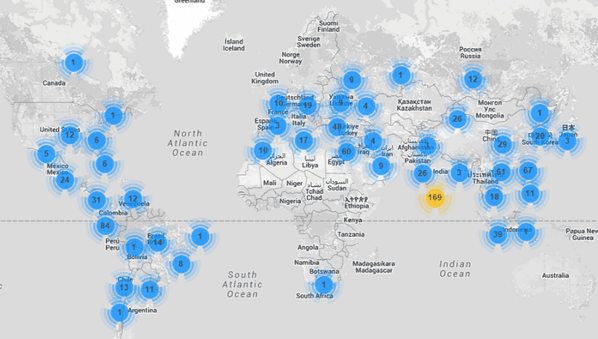
While studying one of the devices, researchers found it sending 20,000 HTTP request each second. Another device had multiple brute force attacks shown in the logs which quite clearly illustrated the device was hacked more than once.
There are over 245 million surveillance cameras installed around the world and most of them not configured properly which makes them vulnerable to hackers. Researchers believe increasing awareness on how to properly configure these devices might not provide an easy route for the hacker to take down these devices.
If you are using security cameras just change the login credentials to use strong username and passwords to avoid getting your camera being hacked and used by cyber criminals.
Source: hackread.com

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











