TalkTalk, a British phone and broadband provider with more than four million customers, disclosed Friday that intruders had hacked its Web site and may have stolen personal and financial data. Sources close to the investigation say the company has received a ransom demand of approximately £80,000 (~USD $122,000), with the attackers threatening to publish the TalkTalk’s customer data unless they are paid the amount in Bitcoin.
In a statement on its Web site, TalkTalk said a criminal investigation was launched by the Metropolitan Police Cyber Crime Unit following “a significant and sustained cyberattack on our website.”
“That investigation is ongoing, but unfortunately there is a chance that some of the following data has been compromised: names, addresses, date of birth, phone numbers, email addresses, TalkTalk account information, credit card details and/or bank details,” the statement continues. “We are continuing to work with leading cyber crime specialists and the Metropolitan Police to establish exactly what happened and the extent of any information accessed.”
A source close to the investigation who spoke on condition of anonymity told KrebsOnSecurity that the hacker group who demanded the £80,000 ransom provided TalkTalk with copies of the tables from its user database as evidence of the breach. The database in question, the source said, appears related to at least 400,000 people who have recently undergone credit checks for new service with the company. However, TalkTalk’s statement says it’s too early to say exactly how many customers were impacted. “Identifying the extent of information accessed is part of the investigation that’s underway,” the company said.
It appears that multiple hacker collectives have since claimed responsibility for the hack, including one that the BBC described as a “Russian Islamist group” — although sources say there is absolutely no evidence to support that claim at this time.
Separately, promises to post the stolen data have appeared on AlphaBay, a Deep Web black market that specialized in selling stolen goods and illicit drugs. The posting was made by someone using the nickname “Courvoisier.” This member, whose signature describes him as “Level 6 Fraud and Drugs seller,” appears to be an active participant in the AlphaBay market with many vouches from happy customers who’ve turned to him for illegal drugs and stolen credit cards, among other goods and services.
It seems likely that Courvoisier is not bluffing, at least about posting some subset of TalkTalk customer data. According to a discussion thread on Reddit.com dedicated to explaining AlphaBay’s new Levels system, an AlphaBay seller who has reached the status of Level 6 has successfully consummated at least 500 sales worth a total of at least $75,000, and achieved a 90% positive feedback rating or better from previous customers.
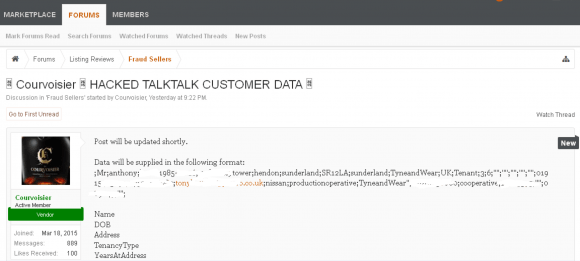
“Post will be updated shortly,” Courvoisier promised in an AlphaBay message thread Friday. “Data will be supplied in the following format:
Name
DOB
Address
TenancyType
YearsAtAddress
MonthsAtAddress
HomeTelephone
MobileTelephone
Email
Employer
EmploymentTitle
EmploymentLocation
EmployersPhone
Bank
AccountNumber
SortCode”
This roughly tracks the details that TalkTalk has said might have been accessed on customers:
Name
DOB
Address
Email Address
Telephone Number
TalkTalk Account Information
Credit Card and Bank Details
According to my source, the intrusion started with an attack technique known as SQL injection (SQLi), a method which abuses a misconfiguration in a database that causes the database to cough up or dump information. The source said the SQLi attack was punctuated by a denial-of-service attack that sought to prevent legitimate users from visiting the targeted site, and that the debilitating assault may have been launched to distract from the database hack.
Several individuals on Twitter also have been posting information suggesting they may know how the breach occurred, and that there were only a few thousand customer records exposed in the breach.
On October 18, 2015, a person using the screen name “Fearful” and alias “Glubz” reported a vulnerability in the videos section of TalkTalk’s Web site (videos.talktalk.co.uk). The flaw was reported via xssposed.org, a site that operates as a sort of public clearinghouse for information about unpatched Web site vulnerabilities. Xssposed.org said it verified the flaw indeed existed in the TalkTalk videos page, but that no technical details were being disclosed to the public in order to give website owner time to patch the vulnerability without putting its users at risk.
Interestingly, a Twitter user with the Twitter handle @Fearful has been posting about expecting a raid from the U.K. authorities at any minute. The Twitter profile links to the (possibly compromised) Web site elliottg[dot]net, which currently redirects to a page with scrolling images of a blond-haired young man, the TalkTalk logo, and a U.K. policeman.
A Google-cached version of the site indicates that Glubz has “continuously found website exploits ranging from non critical and critical exploits/bugs. I’ve always wanted to work for a company that specialises in stuff like this and that time has finally come. Being paid for something you enjoy is probably the best job ever. You may also find me on XSSPOSED under the username ‘Glubz‘.” Indeed, a listing at xssed.org ranks Glubz among its Top 50 Security Researchers, and says Glubz’ Twitter handle is “@Fearful”.
TalkTalk apologized for the breach and said that since discovering the breach on Wednesday it has undertaken a full security review of its Web site and had taken “all necessary measures” to secure the site. The company also is offering customers 12 months of free credit monitoring through Noddle, a credit reporting service offered by the credit reference agency CallCredit.
Extortion attacks put victim companies in a bit of bind, because even if they do pay the ransom demand, there is no guarantee the data was not already shared with or stolen by other attackers — or that the extortionists won’t simply go ahead and publish the data even if they are paid.
As I noted in a Reddit Ask Me Anything interview Friday, there is, unfortunately, a great deal of room for growth in cyber attacks that leverage some type of ransom or extortion.
“It seems like the crooks are getting better situational awareness when they break in somewhere, which of course increases the potential for an opportunistic attack (drive-by download, database hack, malware-laden spam blast) to mushroom into something much bigger and more costly for the victim or organization,” I wrote.
Update, 11:17 a.m. ET: Added information about vulnerabilities reported in the video portion of TalkTalk’s Web site.
Source: krebsonsecurity.com

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











