HACKERS WHO BROKE into the personal email account of CIA Director John Brennan have struck again.
This time the group, which goes by the name Crackas With Attitude, says it gained access to an even more important target—a portal for law enforcement that grants access to arrest records and other sensitive data, including what appears to be a tool for sharing information about active shooters and terrorist events, and a system for real-time chats between law enforcement agents.
The CWA hackers said they found a vulnerability that allowed them to gain access to the private portal, which is supposed to be available only to the FBI and other law enforcement agencies around the country. That portal in turn, they say, gave them access to more than a dozen law enforcement tools that are used for information sharing.
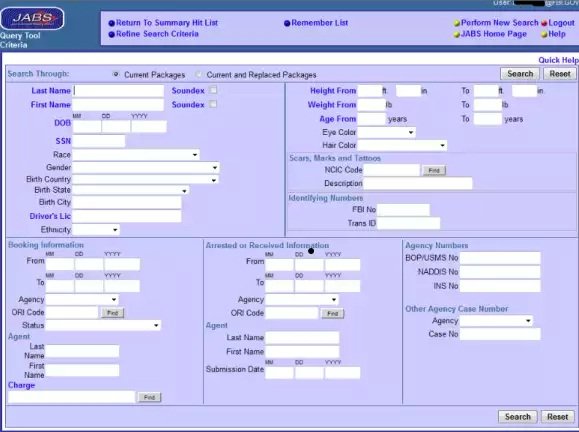
The hackers wouldn’t identify the vulnerability that gave them access, but one of the hackers, who calls himself Cracka, provided WIRED with a screenshot of one of the systems they accessed called JABS. JABS stands for Joint Automated Booking System, and is a database of arrest records for the US.
Cracka is the same handle of a hacker who spoke with WIRED last month to describe how the same group hacked into the private email account of the CIA director.
This latest breach, if legitimate, is significant because it gives the hackers access to arrest records directly after they have been entered into the system. This would be valuable information for gossip sites and other media outlets interested in breaking stories about the arrest of celebrities and politicians.
More importantly, the system can also include information about arrests that are under court seal and may not be made public for months or years—such as the arrest of suspected terrorists, gang members and drug suspects. Knowledge about these arrests can tip off other members of a terrorist cell or gang to help them avoid capture.
“Just to clear this up,” Cracka tweeted on Thursday about the breach of the JABS database. “CWA did, indeed, have access to everybody in USA’s private information, now imagine if we was Russia or China.”
Sealed arrest records are also quite common in hacker investigations when law enforcement officials quietly arrest an individual, then flip him to work as a confidential informant with agents to capture others.
A former FBI agent confirmed to WIRED that JABS shows “all arrests and bookings no matter the sealing.” But he noted that arrest records in which suspects are charged under seal “will only have limited data,” and sensitive records are sometimes removed from the system to prevent news of an arrest from leaking.
“The records go in but after processing they can be removed if they are sensitive matters,” he said, “or more likely there will be [a] flag when you run a name to contact a specific agency. Hackers might be removed if they are potentially cooperating witnesses or sources.”
He noted, however, that “[i]t takes some serious work or threats to get the records removed.”
The investigation into Silk Road, for example, involved a number of initial arrests that were kept quiet to avoid tipping off other suspects.
Cracka told WIRED that he and his fellow hackers were able to view the JABS arrest record of Jeremy Hammond. Hammond was a hacktivist with Anonymous who is currently serving a 10-year sentence for hacking into Strategic Forecasting in 2011 and stealing 5 million private email messages and 60,000 customer credit card numbers. He told WIRED, however, that they did not access other criminal records.
“[W]e wasn’t there to hurt innocent people, just the government,” he said.
Cracka wouldn’t identify the vulnerability used to access the portal, because he said the hackers are still trying to obtain more information from the system. But, notably, an announcement from Box earlier this year indicated that law enforcement has recently begun using its file-sharing system for transmitting records. It’s not clear if this partnership has some significance to the breach, and Cracka did not not respond when WIRED inquired about Box specifically.
It was through the vulnerable law enforcement portal that the hackers say they also obtained a list of about 3,000 names, titles, email addresses and phone numbers for government employees that they posted to Pastebin on Thursday. The posting, which they indicated was just “Part 1” of a presumably multi-part leak, consisted of a snippet of an alphabetical list of government employees working for the FBI and other federal agencies as well as various local police and sheriff departments around the country. It included job titles, email addresses and phone numbers.
The hackers leaked these contact details yesterday, November 5, which is also known as Guy Fawkes Day, a popular symbolic figure and date that has previously been appropriated by the hacking collective Anonymous.
In addition to the names and contact details of law enforcement agents and the JABS database, the CWA hackers say they had access to law enforcement’s Enterprise File Transfer Service, which the government describes as a web interface for securely sharing and transmitting files. Cracka provided WIRED with a long menu of sensitive tools that appeared on the portal’s main page and to which they presumably had access. The menu includes:
Enterprise File Transfer Service—a web interface to securely share and transmit files.
Cyber Shield Alliance—an FBI Cybersecurity partnership initiative “developed by Law Enforcement for Law Enforcement to proactively defend and counter cyber threats against LE networks and critical technologies,” the portal reads. “The FBI stewards an array of cybersecurity resources and intelligence, much of which is now accessible to LEA’s through the Cyber Shield Alliance.”
DFS Test and eGuardian Training—there was no description for either of these.
IC3—“a vehicle to receive, develop, and refer criminal complaints regarding the rapidly expanding arena of cyber crime.”
IDEAFX—a “web-based, file/folder sharing capabilities for cross-organizational teams”
Intelink—a “secure portal for integrated intelligence dissemination and collaboration efforts”
Intelink IM—provides real-time chat between users logged into the law enforcement system.
Justice Enterprise File Sharing—“This application has been created using https://box.com as the base technology and provides cloud hosted capabilities for greater stability and growth for file/folder sharing. It has the ability to transfer files up to 15 GB,” reads the description.
In addition to these, the portal also includes access to:
Special Interest Group—described as a “controlled/structured-access area for specialized organizations or disciplines to share and store information as a means to enhance collaboration with law enforcement, intelligence and emergency management communities.”
Virtual Command Center—a real-time, collaborative tool is used for operations and events that include active shooter incidents, warrants, natural disasters, child abductions, terrorist attacks and threats, as well as something described only as special events. The latter likely includes visits by dignitaries, such as the president or visiting foreign leaders, that require special coordination with local law enforcement agencies.
National Data Exchange, also known as N-DEx—“provides local, state, tribal, and federal criminal justice agencies with a mechanism to nationally share, search, link, and analyze information across jurisdictional boundaries.
National Gang Intelligence Center—a “multi-agency effort that integrates gang information from local, state, and federal law enforcement entities to serve as a centralized intelligence resource for gang information and analytical support.”
Repository for Individuals of Special Concern, also known as RISC—“allows officers on the street to use a
mobile identification (ID) device to perform a ‘lightsout’ rapid search of a limited repository of fingerprint records.”
RISSNET—which provides “timely access to a variety of law enforcement sensitive, officer safety, and public safety resources”
ViCAP Web National Crime Database—“a repository for behavioral and investigative information related to criteria Homicides, Sexual Assaults, Missing Persons, and Unidentified Human Remains cases. Authorized users can click on the ViCAP logo to access the database. All other users can go to the ViCAP SIG to obtain information about gaining access and view various ViCAP documents and resources.”
Active Shooter Resources Page—a clearinghouse for materials available for use by law enforcement agencies and other first responders around the country.
Malware Investigator—an automated tool that “analyzes suspected malware samples and quickly returns technical information about the samples to its users so they can understand the samples’ functionality.”
Homeland Security Information Network, or HSIN—which “provides users with a trusted network to share Sensitive But Unclassified information.”
eGuardian—a “system that allows Law Enforcement, Law Enforcement support and force protection personnel the ability to report, track and share threats, events and suspicious activities with a potential nexus to terrorism, cyber or other criminal activity.”
Cracka told WIRED that he didn’t conduct the hack for fame or laughs.
“[I] just want people to u8nderstnad im NOT and NEVER will be here for fame, im here for my message and thats it,” he wrote WIRED. “[I] just want people to know im doing this for palestine.”
On Thursday he posted several images to Twitter showing Palestinian victims of violence, and also posted a statement to Pastebin explaining his motives.
“I’m the bad guy in the news that’s targeting the US government for funding Israel,” he wrote in the Pastebin message. “Did you know there was over 26,000 civilian deaths due to war-related violence in the Afghanistan war? Did you know the US military bombed an Afghan hospital?…I am standing against the US government for a good reason and I don’t give a fuck what the consequences are, fuck the fame bullshit, I’m here to get my message across and that’s all I’m here for.”
Cracka told WIRED that they don’t currently have plans to leak more information, at least not any time soon.
Source:https://www.wired.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.