In the wake of the Paris attacks, the vigilante hacker group Anonymous has declared war on so-called Islamic State using the internet and claims to haveshut thousands of Twitter accounts used by IS operatives. But a much smaller online group has also emerged, with quite a different strategy – and they claim they’ve already thwarted at least one terror attack.
This group say they were fed up with what they saw as unsophisticated Anonymous tactics. Things came to a head after the Charlie Hebdo attack in January, and after that, the founding members of Ghost Security Group decided to make a clean break from Anonymous.
“They [Anonymous] don’t have any counterterrorism experience whatsoever,” said Ghost Security Group’s executive director, who spoke to BBC Trending via phone, asking for anonymity protect his safety. “We felt that not enough was being done and the Charlie Hebdo attack made it clear that ISIS was not confined to the Middle East.”
Security agencies such as the US FBI have refused to comment on the group – and it’s difficult to independently verify the claims they have made.
But the director of Ghost Security Group said volunteers live in the US, Europe, and the Middle East, and include linguists and “people familiar with intelligence gathering techniques.”
Instead of trying to shut down accounts and attack jihadi websites with distributed denial of service (DDoS) attacks – basically flooding a website with traffic to take it offline – Ghost Security Group members operate more like spies than hackers. They monitor suspected IS Twitter accounts and infiltrate militant message boards to find information, which they say they then pass along to law enforcement.
“We would much prefer to stop attacks than shut down websites,” the executive director said. “I don’t think DDoS attacks do a huge amount of damage to Islamic State. Anonymous are hitting some extremist forums that have intelligence value, but we would like forums to stay online so we can see what people are saying and gather intelligence from them.”
The group claims that it has already helped to thwart one attack in Tunisia by picking up on what they say was online jihadi chatter which indicated that militants would attack a specific location on the island of Djerba. The plot, Ghost Security says, was designed to be a follow up to the June beach massacre which killed 38 people, mostly British tourists. Reports indicate that Djerba did indeed appear on a list of IS targets in Tunisia in July. Like the other claims the groups have made, though, it’s difficult to verify that they thwarted an attack.
Michael Smith, chief operating officer of security consultancy Kronos Advisory, works with the group and says they spotted tweets that were being sent back and forth between IS accounts. Although the tweets would sometimes only exist for minutes before being deleted, Ghost Security Group operatives were watching. The group sent Trending screen grabs of examples of the types of messages it found on now-deleted Twitter accounts:
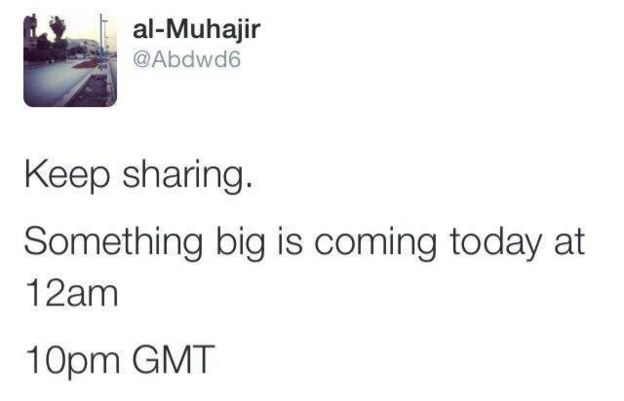
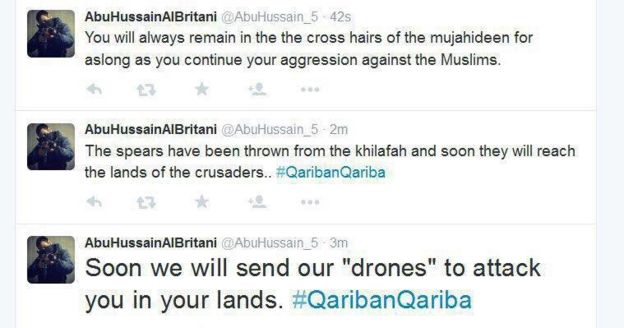
“They are not just identifying channels [of communication], they have put together a list of accounts which are utilised by people with influence,” Smith said. “These people have saved lives.”
Smith told Trending he works with the group to funnel the information they gather to security services, and said they came to him after realising they needed a conduit to pass along information, and to alert authorities to their operations so that they themselves wouldn’t be targeted for investigation, thus wasting time and resources.
By breaking away from Anonymous, the Ghost Security Group director said, the group says it has managed to sidestep the hackers’ often thorny relationship with the authorities. In the past, Anonymous has targeted various government agencies – for instance US police officers after the shooting of Michael Brown in Ferguson, Missouri.
The director told Trending that working with the American government is a trade-off worth making.
“We have data. We can’t do anything with that data unless we work with the US government. They have the guns and the boots on the ground, they can disrupt terrorist operations.”
The group has not been immune to the kind of criticism and infighting that has hit Anonymous, however. One member of Anonymous who contacted BBC Trending on Twitter accused the group of cosying up to governments and exaggerating its accomplishments. Anonymous operatives reject criticism of their mission and say they’re genuinely disrupting IS recruitment with their hacks.
“It stops them from talking. It stops them from recruiting young kids that have no place to go or people that are sick in the head,” an Anonymous operative told BBC Radio 4’s Profile. “A lot of people think that some of the stuff we do, we just blurt names out, but that’s not solely how we operate.”
At the beginning of November the group rebranded from “Ghost Security” to “Ghost Security Group”, abandoning an earlier version of its website. In a press release announcing the change, the group took a dig at Anonymous: “[Ghost Security Group’s] new trademarked look discards the hoodies and Guy Fawkes masks so often associated with publicity stunts and distributed denial-of-service attacks on government, religious, and corporate websites in favour of pristine, white graphics devoid of any reference to illegal activities.”
Smith said that although Ghost Security Group operatives do things that fall into “legal grey areas” in many countries, they eschew hacks which are clearly illegal in most parts of the world, and disagreements about the use of illegal hacks and the group’s relationship to governments led to the split and rebranding.
 Image copyrightGhost security group
Image copyrightGhost security groupRecently, Smith says, jihadis have moved from Twitter to more secure systems such as the messaging app Telegram – which has been closing Islamic State-affiliated channels since the Paris attacks – and that Ghost Security Group has made inroads into infiltrating difficult-to-penetrate networks.
The group’s director said he’s urging members of the public to report suspicious online activity via their website, but wouldn’t reveal details of the group’s current operations regarding the attacks in Paris, saying that to do so might put them in jeopardy.
“We’re trying to identify any social media accounts that may have been involved in communicating about those attacks,” he said, adding that when it comes to future plots “we definitely hope to uncover them before they happen.”
Source:https://www.bbc.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











