Root certificate debacle that hit Lenovo now visits the House of Dell.
In a move eerily similar to the Superfish debacle that visited Lenovo in February, Dell is shipping computers that come preinstalled with a digital certificate that makes it easy for attackers to cryptographically impersonate Google, Bank of America, and any other HTTPS-protected website.
The self-signed transport layer security credential, which was issued by an entity calling itself eDellRoot, was preinstalled as a root certificate on at least two Dell laptops, one an Inspiron 5000 series notebook and the other anXPS 15 model. Both are signed with the same private cryptographic key. That means anyone with moderate technical skills can extract the key and use it to sign fraudulent TLS certificates for any HTTPS-protected website on the Internet. Depending on the browser used, any Dell computer that ships with the root certificate described above will then accept the encrypted Web sessions with no warnings whatsoever. At least some Dell Inspiron desktops, and various Precision M4800 andLatitude models are also reported to be affected.
The crowdsourced discovery came over the weekend, as Dell customers shared technical details of the eDellRoot certificate installed on recently purchased computers. Joe Nord, a self-described programmer, showed the certificate as it appears in the Microsoft Management Console:
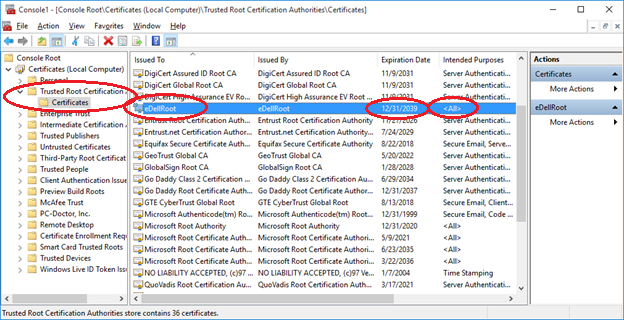
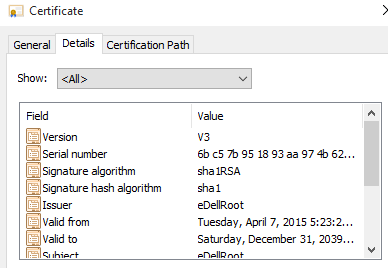
He also included the fingerprint of the private key that underpins it:
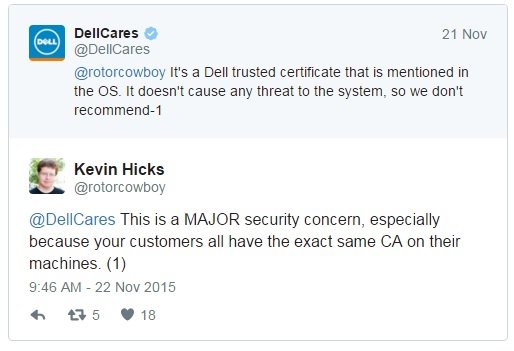
A separate Dell customer took to Twitter to say an eDellRoot root certificate with the same private key was installed on his laptop. The person went on to publicly warn Dell officials that its inclusion on Dell computers represented “a MAJOR security concern, especially because your customers all have the exact same CA on their machines.”
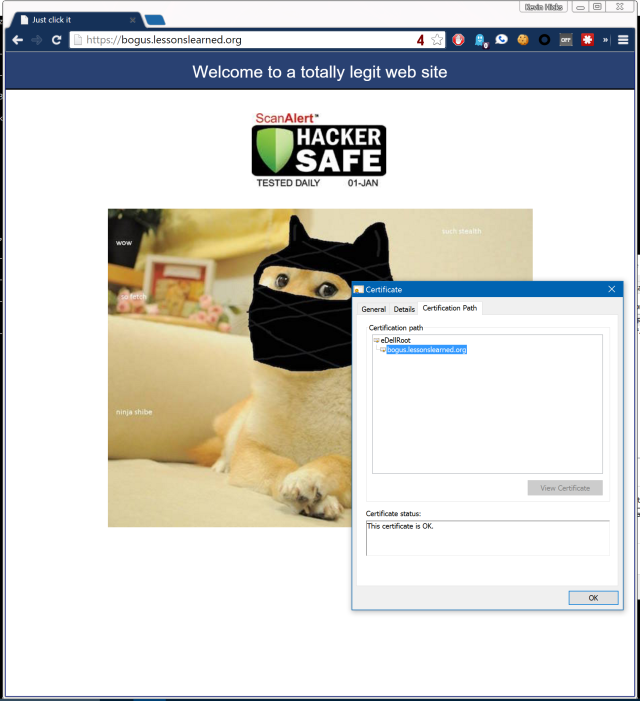
Seeing is believing
Nord told Ars that he visited this HTTPS test site, which was created by security expert Kenn White using the private key contained in the Dell certificates. Nord said the Google Chrome and Microsoft Edge and Internet Explorer browsers established an encrypted Web session with no warnings, even though the certificate was clearly fraudulent. Fortunately, Firefox generated an alert warning that the certificate was not trusted. Kevin Hicks, another Dell customer known to be affected, reported the same findings. He included the following screenshot of Chrome running on his enterprise-grade laptop being fooled by White’s test site:
Many of the most important questions around this troubling discovery remain unanswered. It’s still not clear, for instance, how widely Dell has distributed the eDellRoot credential or if Dell distributes similar root certificates that are also signed with identical private keys. It’s also not yet known if the certificate can be used to sign applications so that they bypasses Microsoft malware checks. Update:Researchers now say such code signing is possible, a finding that raises still more concerns. The purpose of the certificate isn’t clear either, although there’s some evidence the credential is linked to the Dell Foundation Service application. Rather than waiting hours or days for answers, Ars is publishing what is known now. To check if a particular computer is vulnerable, users can follow these instructions for using the Microsoft Management Console. The eDellRoot certificate will look similar to the one in the image above from Nord’s computer.
Dell issued a statement early Monday morning that said technicians are investigating the reports. Until they and other outside experts weigh in, it’s too early to say how widespread and severe this problem is. What is clear now is that the eDellRoot certificate was generated two months after the Superfish debacle came to light and that it poses a risk to at least some Dell customers. Ironically,Dell has publicly capitalized on the Superfish debacle even as it engaged in a blunder that poses the same threat to its own users. People who find this certificate installed on their computer should temporarily use only Firefox to browse to HTTPS-protected sites.

Affected people should also stay apprised of events and updates in the coming days. If the worst concerns about this root certificate are confirmed, Dell almost certainly will soon provide a tool to remove this credential. More on all of this will be coming in the hours or days to come.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











