On September 11, 2015 I visited Media Markt in Utrecht Hoog Catherijne, a well-known electronics shop in The Netherlands. Since summer 2014, the biggest independent Dutch phone retail company Phone House also operates (white labeled) from within Media Markt locations as a store in a store concept. I had a few questions about my phone subscription so I talked with a Phone House employee. We were discussing the new Samsung Galaxy S6 Edge phone and I was thinking about buying one.
Somewhere in the conversation the service & sales guy asked what I did for a living so I told him that I earned my money as a freelancer by hacking (with authorization) into computer systems of businesses and writing security reports about it. He thought that was cool so we talked a few minutes more about this subject. I even told him that I had noticed some months ago that one of his Media Markt colleagues had written a password on a post-it and attached it onto a computer monitor near a cash desk, in plain sight where any customer could see it :


As you can see, the password to unlock Media Markt computers was media321. A very strong one!
We both laughed about how irresponsible and naive that was.
The conversation continued about my desire for a new phone and about all associated kinds of subscriptions that I could choose of. After about ten minutes I made up my mind and ordered a new phone and a new subscription. I’m still in shock about what happened next!
Context
But first two things about the context:
- As Phone House is not a telecom operator itself, it functions as a dealer for telecom operators in The Netherlands such as Vodafone, KPN, Telfort, T-Mobile, Tele2, UPC and others. So, they basically can cover the complete Dutch telecom market.
- The telecom service & sales desk is located in the middle of the Media Markt store and designed in such a way, that customers can look at the computer monitors that employees use. No effort is made to block your view on the monitor and customers can look straight in on Media Markt’s service computers.
Opening up the password file
The sales guy starts renewing my Vodafone subscription and therefor needs to log in at a dealer portal from Vodafone. He doesn’t remember the login password, and, here it comes, on the screen he opens an Excel file which contains *all* their passwords.
Is this happening for real? I just told him minutes ago I’m an experienced professional hacker and we had just laughed together about the password-taped-on-monitor leak.
Curiously and intensively I looked on the screen to get a picture of the treasure trove that was in front of me. Passwords to view and modify customer data of KPN, Vodafone, Telfort, T-Mobile, UPC, Tele2 and other companies were right in front of me.
A curious detail was that the Excel password database was stored on Google Docs and the login details of their Google Account were also in front of me. Neat! Now I can lookup their passwords anytime I want from any computer in the world.
Passwords stored unencrypted on Google Docs
As Google is a company located in the United States, the Google Docs servers are probably also located there, or at least subject to the Patriot Act. I think it’s safe to say that the NSA probably (still) has direct access to documents stored in Google Docs. The password database is stored unencrypted in the cloud thus it can be assumed the NSA has access to it. So much for all the encryption effort made by Dutch telecom providers after the Edward Snowden leaks: Phone House is trusting their passwords to an American company.
Leaving the file open
The sales & service guy who is assisting me is frequently approached by his colleagues for help. Apparently he’s the senior of the telecom department.
He printed a renewal contract for me which I had to sign. I told him that I first wanted to read it. He said: “You’re the first person in years who wants to read the contract”. I often hear that. Apparently nobody takes time to read only one page of small text. Most people seem to blindly trust companies, but I’m not like that. The sales guy said: “Take your time”, and then moved away from his desk to organize products in his part of the shop. He left the password sheet open right in front of me. I couldn’t believe that he just did that. Was he testing me?
The battery of my old phone had died (hence I wanted a new phone) and I unfortunately couldn’t take a picture of what just happened. I silently cursed. Without any evidence, would a stranger believe me if I told him what just happened? I think it’s a small chance: seeing is believing.
Documenting the password gate
I left the shop and returned three weeks later on October 3rd (2015) curious to see if the same employee I spoke to was working there again. But he wasn’t! Well, let’s try with his colleague to see if I could social engineer him in such a way he would open up the password file again. I asked him something about my subscription. To answer that, he needed to login to the Vodafone portal, and yeah, there we meet again, my precious password file:
I also made a high resolution photo of the screen:

It was not just an incident in which one employee was careless with the company password database, apparently multiple employees were. Seems like a structural problem and a fundamental lack of security and privacy awareness within Phone House and Media Markt.
Password strength analysis
As a customer you would expect the company you trust your personal data to, to make the utmost effort in protecting those, right? Doesn’t seem to be the case. Your personal details were protected via passwords such as:
- m
- 12345678
- Utrecht
- beginnen01
- Utrecht12345
- upc12345
- Welkom03
- Mediautr03
For the non Dutch readers, I’ll translate the following Dutch words:
- ‘beginnen’ means ‘beginning’.
- ‘welkom’ means ‘welcome’.
- ‘utrecht’ is the city the shop is located in, sometimes abbreviated as ‘utr’.
As you can see, there is even an account that has an one character password and also the password 12345678 is used on multiple accounts. That last password is the fourth most used password in 2014. Phone House employees lack creativity or just done care. And apparently also: the dealer portals don’t enforce strong passwords.
Looking at the passwords Welkom03 and Mediautr03 it seems that a password change policy is active on some systems that forces users to regularly change their passwords. Looks like Phone House employees have found a system to circumvent that protection by incrementing the digit of their password each time. It seems that they already have done that two times. Giving user accounts the initial password Welcome01 is de facto standard in companies, as this one complies to most password policies: it consists of upper and lower case characters, and also contains multiple digits. And, you should welcome your new users, right?
User name analysis
All the user names in the password file are non personal. This means that telecom providers and Phone House can’t hold account of who exactly logged in with a given user account. Also, if a Phone House employee quites the company, all passwords of the shared non personal accounts should be changed. Given the circumstances I highly doubt this is the case.
Even if the passwords for some accounts are regularly changed, the most important password, that of the Google Account in which the password database is stored, seems to be static: Utrecht12345.
Opening up the dealer portals
The password sheet contained all kinds of portal names, but their internet addresses weren’t located in the file. In order to estimate the risk involved, I needed to find out if these portals were freely accessible over the internet, so I started googling them. Within a minute I found out that the employees of a Phone House store located in the city of Joure created a public link directory with all locations of the dealer portals they use:
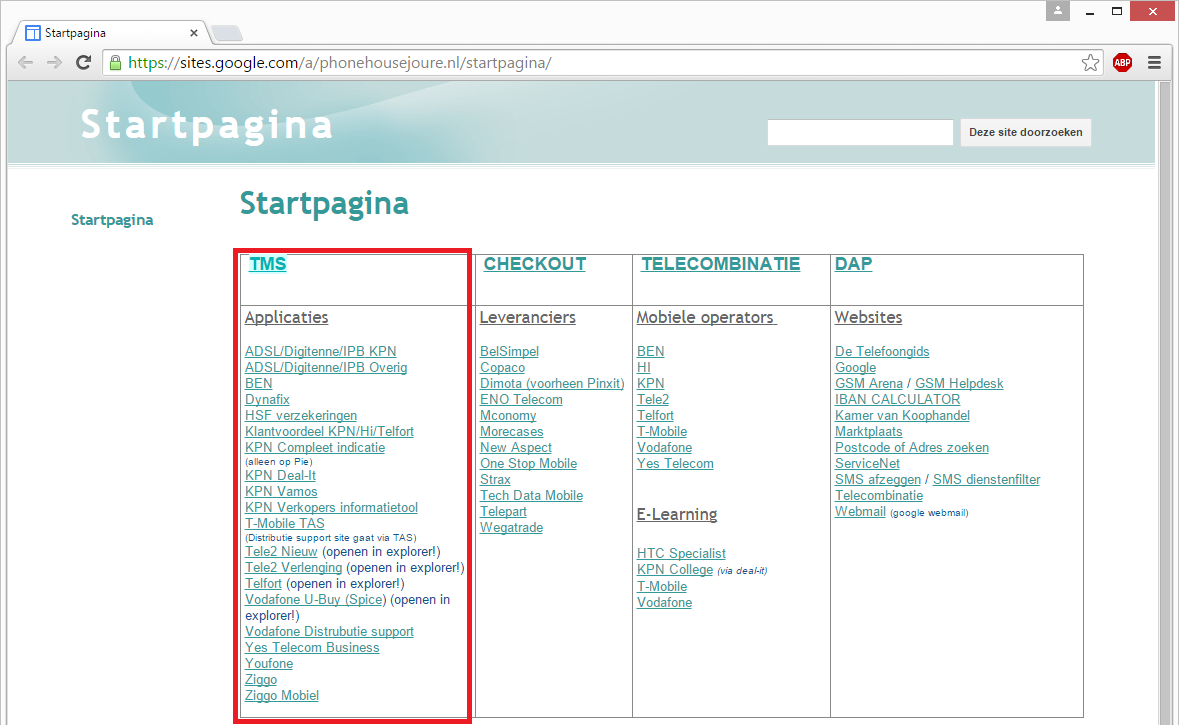
I clicked on all dealer portals to see if they were freely accessible via internet, and quite a lot of them actually were:
| ADSL/Digitenne/IPB KPN | : | Login screen visible |
| ADSL/Digitenne/IPB Overig | : | Login screen visible |
| BEN | : | Just links to the main Ben website |
| Dynafix | : | Login screen visible |
| HSF verzekeringen | : | Login screen visible |
| Klantvoordeel KPN/Hi/Telfort | : | Error message is shown |
| KPN Compleet indicatie | : | Error message is shown |
| KPN Deal-It | : | Login screen for business market visible. Login screen for customer markted protected via IP address whitelisting |
| KPN Vamos | : | Error message is shown |
| KPN Verkopers informatietool | : | Link redirects to main KPN website |
| T-Mobile TAS | : | Login screen visible |
| Tele2 Nieuw | : | Login screen visible |
| Tele2 Verlenging | : | Login screen visible |
| Telfort | : | Error message is shown |
| Vodafone U-Buy (Spice) | : | Error message is shown |
| Vodafone Distrubutie support | : | Login screen visible |
| Yes Telecom Business | : | Login screen visible |
| Youfone | : | Login screen visible |
| Ziggo | : | Login screen visible |
| Ziggo Mobiel | : | Link redirects to main Ziggo website |
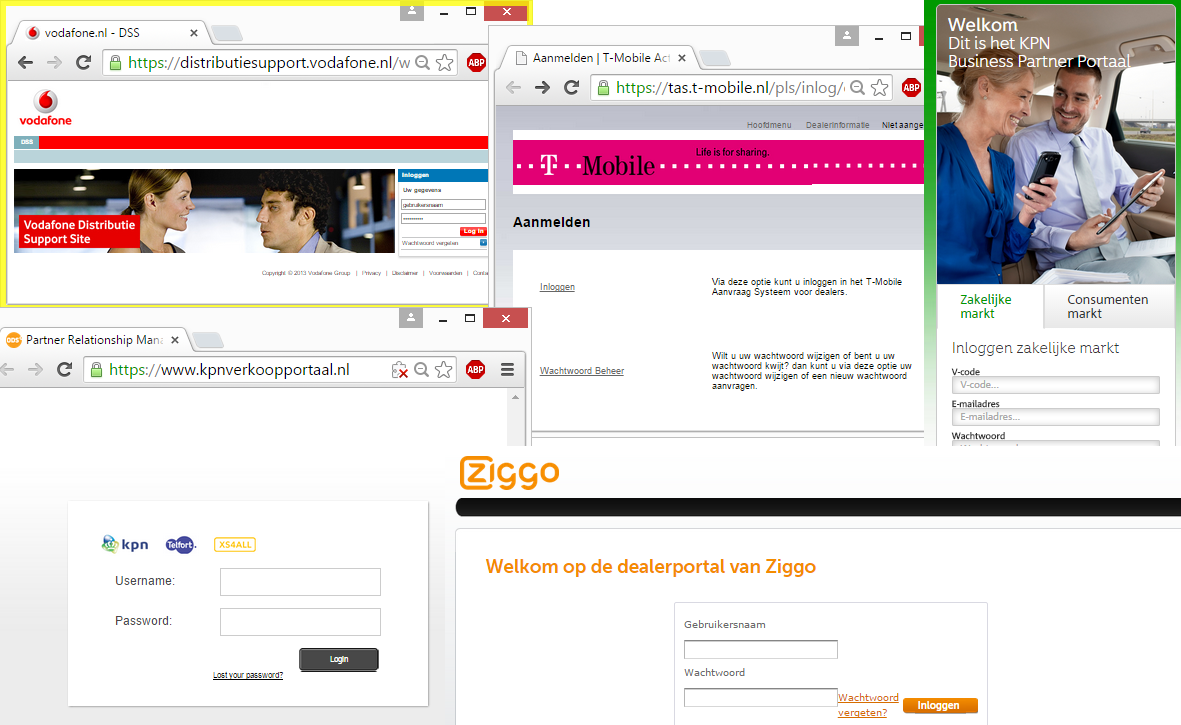
Six portals seemed to use mutual SSL/TLS authentication and/or IP address restriction, like it should be, but twelve portals were freely accessible. This means that I could log in as a Phone House employee on those dealer portals and manage the configuration of customers. I didn’t log in. If I had done so, I would have broken the law and I never do this.
I could use the easy to use Tor Browser Bundle in order to masquerade my IP address. That way I could perform the unauthorized access completely anonymous, leaving no traces. Talking about a hard to solve crime.
Circumventing IP address restriction
The portals that have IP address range restriction set-up, can easily be defeated by covertly installing a LAN Turtle or mobile broadband enabled WiFi Pineapple in one of the Media Markt shops, so remote access is gained to their internal network and thus the IP address restriction can be circumvented.
Finding a network cable or socket to attach the remote access device to is fairly simple, as Media Markt is a hardware store, customers have easy access to all kinds of occasional unmanned support desks which are located anywhere in the shop. I had found quite a few vulnerable spots already.
Impact of leak
My personal estimation is that Phone House, via dealerships, has access to personal data of basically all Dutch citizens who own a mobile phone. That would be between 10 and 14 million people. Only counting the people who are alive. But I guess these portals also contain data about deceased people. Black hat private detectives, stalkers and fraudsters would love to have direct internet access to such a trove of personal data.
I discovered that my findings had been applicable to all Media Markt and Phone House stores for over a very long period of time. More on that later.
Back to Phone House Joure
The Phone House store in Joure created a Google Sites website in order to host their links on. Wondering how recent the link directory was, I clicked on the ‘recent site activity’ link in the footer:
The complete history of all site modifications was shown. Including a change to a specific file that had nothing to do with the link directory:
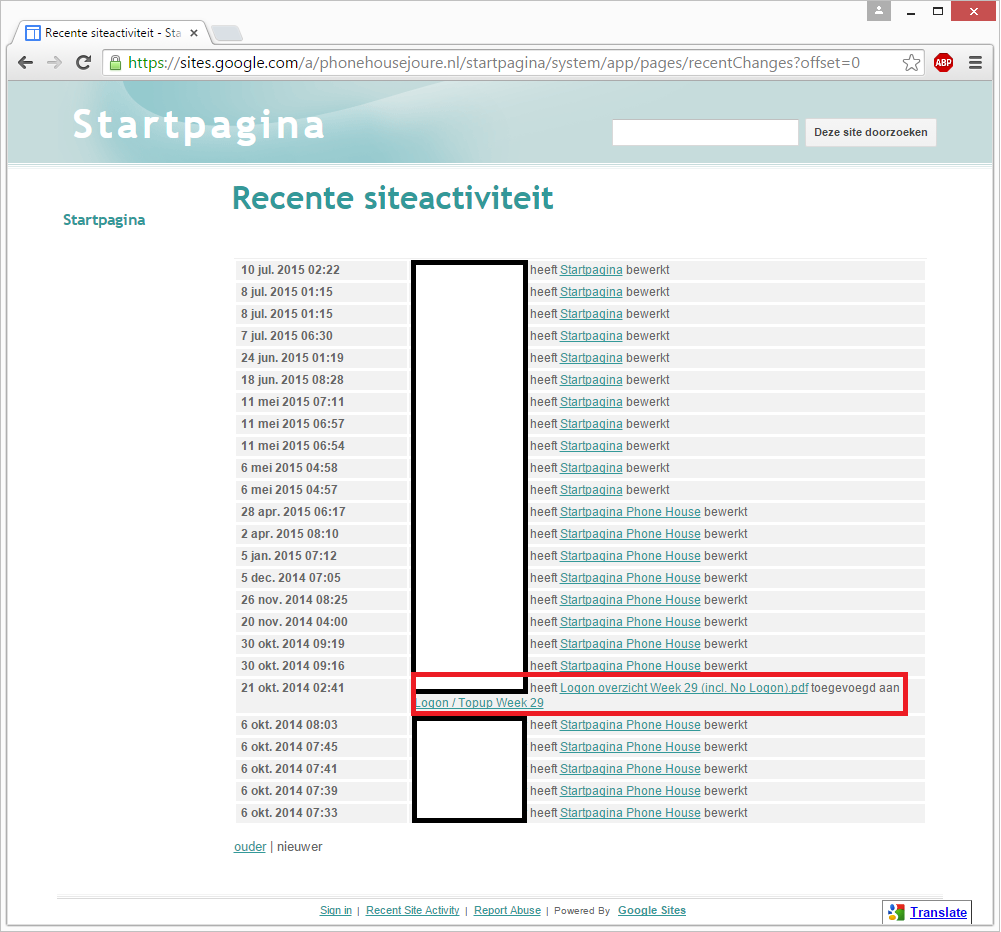
I clicked on that specific file to see what it would contain:
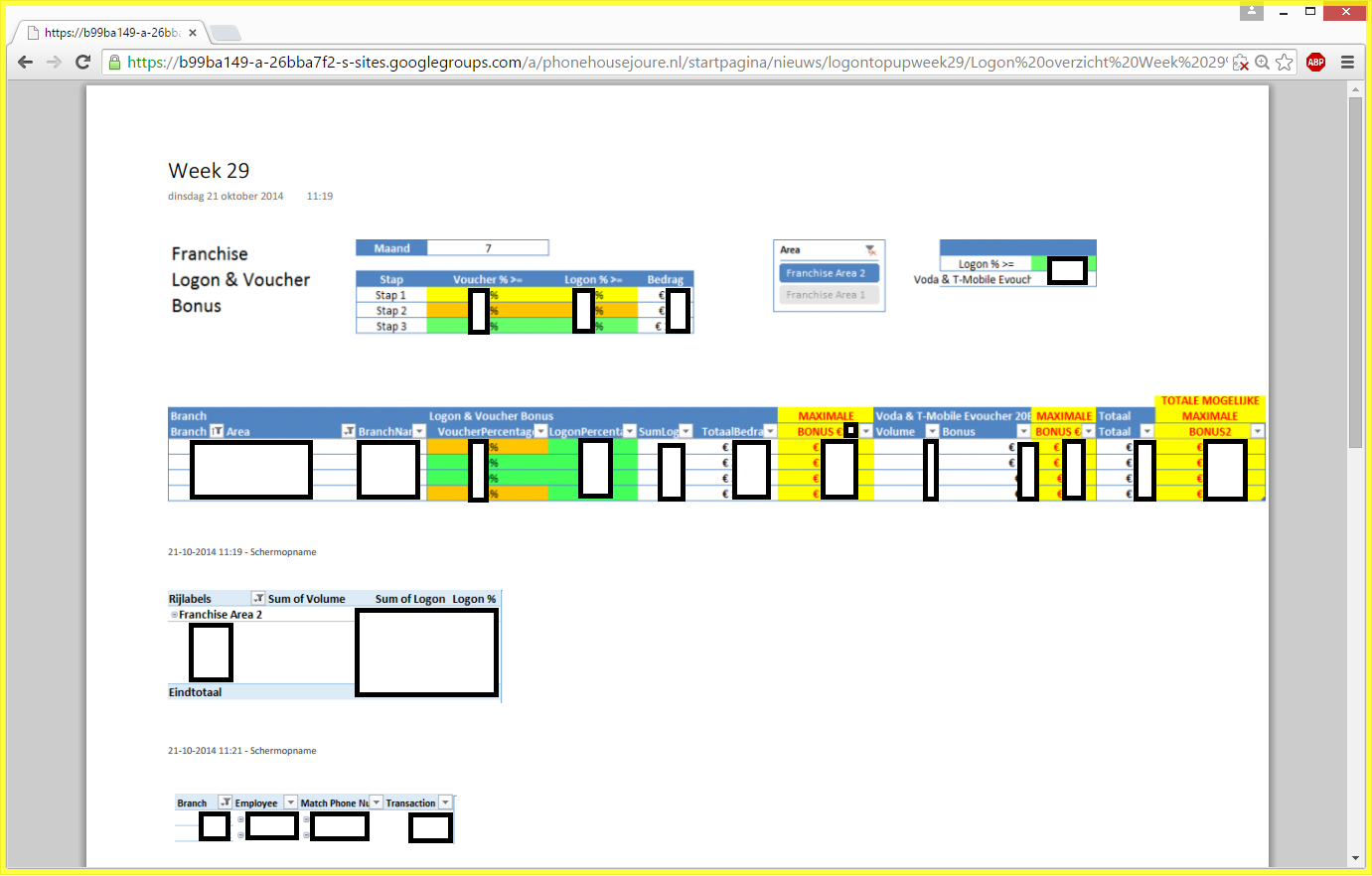
Things were getting weirder. What I saw seemed to be internal financial administration of Phone House Joure. Somehow I got the feeling this was private company data not meant to be seen by others. Or has Phone House got a really transparent policy towards their provision and sales data? Okay, I’m not to investigate this particular matter any further. I digress. Back to the password story.
Computers are never locked
What I also noticed, is that when service & sales employees leave their computers, they never ever lock it, and so people walking by have full and easy access to it. Further more on all occasions that I witnessed the password file, it had already been opened by the employee. They just had to ALT + TAB to it.
Leaving a computer unlocked when walking away makes it very easy for an attacker to obtain all passwords. Also, I noticed that this specific computer had easy to reach USB ports. I could perform a USB drive by attack with a prepared Rubber Ducky or Teensy, with which I could have gained remote access to the computer within 10 seconds.
Auto completion of passwords
Web browsers of Phone House computers are configured to save user names and passwords and prefill them (most of the times) whenever they’re navigating to a login screen. A computer user only has to press the ‘login’ button to enter the system. Permanently storing passwords in browsers is risky as they are by default stored non-encrypted on the computer. A master password could be configured to open the browser password store (and add encryption), but practice shows that most users never configure one.
Opening up a customer file
Another thing that I noticed, was that I only had to give my telephone number to the Phone House employee and subsequently my Vodafone file was opened. No other security questions were asked to validate my identity. However, a reverse validation question was asked: “Do you live at address [..]?”. I malicious person would of course reply: “Yeah I definitely live there”.
What should have been the case
If we sum up the story, how should it then have been done ideally?
Improvement points for Phone House and Media Markt:
- Don’t write passwords on post-its stuck onto monitors.
- Don’t let (potential) customers look at the screen that an employee operates on.
- Physically shield the viewing angle of the computer monitor.
- Apply a privacy screen on the monitor to further minimize the viewing angle.
- Create strong passwords.
- Change passwords frequently.
- Lock computer screens when leaving the computer.
- Never use a non personal account with multiple people. Create an individual user accounts for every employee.
- Change the passwords of non personal accounts when an employee who had access to those accounts quits the company.
- Use a safe password store, such as KeePass, that shields passwords and uses strong file encryption.
- Don’t store the password database in the cloud.
- If a cloud solution is nevertheless used (and still, keep your password database out of it), use a cloud provider with a data center in The Netherlands so that intelligence agencies such as NSA and GCHQ don’t have direct access to your files.
- Never store passwords on a computer without encrypting them.
- Always close the password database file after coping the password that was needed.
- Protect user accounts (such as the Google Account) with multi-factor authentication (such as Google Authenticator).
- Don’t publish links to dealer portals publicly on the internet and shield your financial administration.
- Perform decent checks to validate if a customer is really who he says he is:
- When working with personal data in a store, always check the customer’s identity card. It’s mandatory in The Netherlands to have one on you at all times.
- If a customer calls the service desk, call him back on the telephone number that is linked to the customer’s account.
- Disable USB ports on computers via a software or hardware solution.
- Train your employees in IT security and privacy practices.
- Create a corporate culture so that security and privacy is propagated by your employees.
Improvement points for telecom operators:
- Make sure dealers have the possibility to create individual user accounts for their employees.
- Apply IP address restriction on dealer web portals.
- Require a client HTTPS (X.509) certificate when setting up a connection to a dealer web portal.
- Enforce a strong password policy, such as:
- a minimum password strength of eight characters;
- a password that isn’t known in brute force password lists;
- add custom complexity rules: enforce the use of upper, lower case, numbers and special characters;
- passwords can not be the same as user names;
- enforce that passwords are regularly changed;
- enforce that changed passwords aren’t reused and are substantially different in comparison to previous configured passwords.
- Make sure that your web portal supports multi-factor authentication.
- Disable the HTML AutoComplete option in web forms that process authentication data such as passwords.
Summing it all up, you see it’s quite a list of things that went wrong (!).
It makes me very sad that all of the mentioned above still isn’t regular practice for businesses in 2015.
Media Markt threatens to sue me and denies everything
It’s time to contact Phone House and Media Markt and tell them my findings (October 4, 2015). As I had the direct e-mail address of the responsible Media Markt department in Utrecht (it was visible in the password file), I mailed them my findings. They didn’t respond.
A few days later I got an e-mail from the store manager of Media Markt Utrecht Hoog Catherijne and he threatened that he would sue me if I went public. There you stand as a good willing civilian just wanting to make the world a safer place. I think it’s childish and also a very hostile response towards someone who simply notifies you of a critical security vulnerability that your company is responsible for. It’s like shooting the messenger.
To go even further, Media Markt denied I could get access to web portals which are hooked up on the internet with the captured login details. This response demonstrates the fundamental lack of knowledge about how the internet works. I’m not crazy: if I have login details and if the login screen is accessible over the internet, then I can log in with those credentials. Simple as that. I didn’t do so, cause it’s illegal.
Media Markt dismisses all my findings as “appearance of insecurity”. Talking about ignorance … They end their e-mail demanding I destroy the pictures I took of their passwords within 24 hours.
I replied explaining how responsible disclosures work and that this attitude towards me is damaging his company. To eliminate any possible anxiety people have when in contact with a hacker, I clearly stated that my intentions were good. This luckily had a positive effect and the next day I was invited for a cup of coffee. More on that later.
Contacting the affected telecom providers
As I had anticipated that such a lame initial response from Media Markt and Phone House was possible, I had also taken time to inform telecom providers involved. These providers are very important stakeholders for Phone House and can apply the right pressure in order to fundamentally improve security and privacy practices. In comparison to Media Markt, all involved providers were very polite towards me.
I have to give special credits to the KPN computer emergency response (CERT) team. They contacted me frequently about their progress and also immediately set a minimum password strength policy on their dealer portal, so new one character passwords weren’t possible anymore. KPN has become very capable of handling responsible disclosures since they have been badly hacked in 2012. Kudos for them. They were also the only party involved that gave me a nice bounty:

The Vodafone security guy also was very kind towards me as well as Tele2, who took the time to learn about the whole story.
Status: two weeks after disclosure
Two weeks after I had contacted all parties involved, I went back to the Media Markt store, cause I was in need of a birthday present for a friend of mine. I also had a genuine question about my Vodafone subscription.
When entering the shop, I saw no more passwords written on post-its stuck onto monitors. Things were looking good! So I went to the telecom desk with my question. The employee logged in on Windows with a password that ended with 1234. I couldn’t see it clearly, but I think the first password part was media. Cool, they also changed their main Windows password and made it more secure by adding an additional character.media1234 is so much more secure compared to media321. Good job!
Then the employee logged in on another system. He hit character 1 and with one smooth and fluent movement stopped his finger at character 8. I’ve never seen anyone entering password 12345678 in one smooth swipe like this. It really looked cool!
Subsequently he opened up the notorious Excel password file in front of my eyes. Some passwords had been changed, many had not. Actually, nothing really had changed.
Media Markt, we need to talk.
Having coffee together
A few days later (October 22nd, 2015) I went to meet the store director face-to-face. Given the circumstances, the start of the conversation was slightly uncomfortable. I was told they initially misinterpreted my intentions and had seen me as a bad hacker.
Once the ice had been broken, I told him password gate had not yet been fixed and urged him to take action immediately. He said he was waiting for Phone House to act since it was their infrastructure and personnel. I told him I wanted the vulnerabilities to be fixed before I was going to publish this story. To add pressure, I added that I didn’t want to wait very long with this publication.
As a quick and dirty fix that would close the most important gate in five minutes, I suggested they should make the font color of the passwords in the Excel file black, as well as the background color of the cell. This would still enable the telecom employee to copy the password to the clipboard, but the password would not be visible anymore whenshoulder surfing. I told him to apply this patch himself and shouldn’t wait for Phone House.
A week later
Curious to see if progress had been made, I sat down together with the director a week later (October 28th, 2015). Our earlier conversation had had impact since directly afterwards various actions had been performed and internal company pressure had increased to set priorities right:
- All my recommendations (as mentioned above) had been sent to all fifty Media Markt stores in The Netherlands and also to Phone House as well.
- They had chosen a safe software product to store their passwords on. A lengthy manual had been written (they showed it to me) so their employees would know how to use it.
- Privacy screens had been installed and the secure password database was now implemented in the Media Markt store in Utrecht.
The director asked me to wait with publication for a few more weeks as Phone House had planned a road trip to install their new password store software in all their shops, of which there are quite a lot.
I told the director I had not heard anything from Phone House yet and that given the circumstances I felt as if I was being ignored by them. He relayed that feeling and the next day I got a friendly call from Phone House.
Having coffee together helps!
TalkTalk gets hacked
As I’m writing this story, the large British telecom provider TalkTalk was hacked. On October 30, 2015 they confirmed the following numbers:
- Total number of customers whose personal details were accessed is 156,959;
- Of these customers, 15,656 bank account numbers and sort codes were accessed;
- 28,000 obscured credit and debit card numbers were accessed.
According to them “these criminals were very smart” and the attacks were “sophisticated”.
A week later the BBC reported that four people have been arrested over the hack so far: a boy of 15 in Northern Ireland, a 16-year-old boy from west London, a 20-year-old Staffordshire man, and a 16-year-old boy in Norwich.
I wouldn’t call a cyber attack very smart and sophisticated when it can be performed by teenagers. But, perhaps calling it like that says more about the competence of the telecom company than about the perpetrators.
Salient detail is that it’s the third hack on the TalkTalk website since February this year.
Apparently TalkTalk is not the only telecom provider that has bad IT security.
Final words
The password database gate of Phone House could be exploited by anyone with basic computer skills. You only need a camera and know how to use a login form. I hope this story is a wake-up call for everyone who works with computers and handles personal data of others.
As an IT security consultant and professional ethical hacker, I work for many different kinds of businesses each week and analyse their security. I won’t name specific customers as I’m very loyal to them. But believe me in saying that Phone House and Media Markt aren’t the only big companies with terrible IT security. Nowadays it’s actually standard (really!). Only banks and the military have the budget to get the right IT security. Unfortunately even they get very vulnerable on occasion.
Should things be fundamentally changed in our society regarding IT security? Or do we accept the fact that we’re inherently insecure? How about in 10 years time when our houses, cars and human bodies are hooked up to the internet? And what about our critical water, food and energy infrastructures? Oh uh, those have already been connected to the internet.
Timeline
Overview of events:
| September 11, 2015 | First observation of the Phone House password gate. Couldn’t take photo of password file. |
| October 3, 2015 | Second observation of the Phone House password gate. Took a photo of it. |
| October 4, 2015 | Reporting the vulnerability to Media Markt and telecom operators. |
| October 6, 2015 | Media Markt sends threatening mail. |
| October 17, 2015 | Validated that password gate was not yet closed. |
| October 22, 2015 | Having coffee with Media Markt store director. |
| October 28, 2015 | Having coffee part two: “We patched one store, but we need weeks of more time because of big patch road trip”. |
| October 30, 2015 | Details about the hacked British telecom provider TalkTalk were published. |
| December 8, 2015 | This story is published. |
Source:https://sijmen.ruwhof.net/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











