Wave of attacks grows. Researchers advise sites to install just-released patch.
Attackers are actively exploiting a critical remote command-execution vulnerability that has plagued the Joomla content management system for almost eight years, security researchers said.
A patch for the vulnerability, which affects versions 1.5 through 3.4.5, was released Monday morning. It was too late: the bug was already being exploited in the wild, researchers from security firm Sucuri warned in a blog post. The attacks started on Saturday from a handful of IP addresses and by Sunday included hundreds of exploit attempts to sites monitored by Sucuri.
“Today (Dec 14th), the wave of attacks is even bigger, with basically every site and honeypot we have being attacked,” the blog post reported. “That means that probably every other Joomla site out there is being targeted as well.”
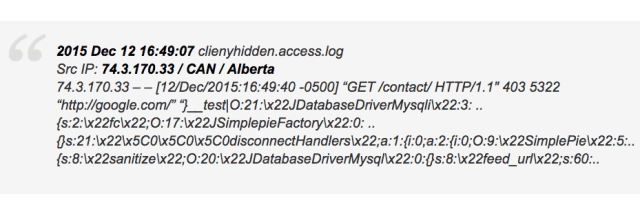
The researchers went on to advise people who administer Joomla sites to search logs for the IP addresses 146.0.72.83, 74.3.170.33, or 194.28.174.106, since those were the first ones observed carrying out the attacks. Sucuri also recommended admins search logs for events that use “JDatabaseDriverMysqli” and “O:” in the user agent. Systems that test positive for any of the strings should be presumed compromised and undergo a thorough scan and clean-up regimen.
Joomla 1.5 was released in January 2008, making the bug almost eight years old. Version 3.4 was released earlier this year. It’s not yet clear exactly what happens to vulnerable systems that are exploited. This post will be updated if those details become available later.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.