Fixed by Microsoft’s latest patches, bug could be “enterprise killer,” says researcher.
One of a heaping collection of critical bug fixes pushed out by Microsoft on December 8 as part of the company’s monthly “Patch Tuesday” was an update to the Microsoft Office suite designed to close a vulnerability that would allow an attacker to sneak past Outlook’s security features. While the patch addressed multiple vulnerabilities in the way Office manages objects in memory, the most severe of them allows for remote code execution through a “specially crafted Microsoft Office file,” Microsoft reported.
Now more details of just how bad that vulnerability is have been provided by security researcher Haifei Li in a paper entitled “BadWinmail: The ‘Enterprise Killer’ Attack Vector in Microsoft Outlook.” The vulnerability allows a crafted attachment to an e-mail to bypass Outlook’s layers of security by exploiting Office’s Object Linking and Embedding (OLE) capabilities and Outlook’s Transport Neutral Encapsulation Format (TNEF)—the e-mail attachment method associated with Outlook messages’ winmail.dat attachments.
The winmail.dat file includes instructions on how to handle attachments embedded within it. “When the value of the ‘PidTagAttachMethod’ [within winmail.dat] is set to ATTACH_OLE (6),” Haifei wrote, “the ‘attachment file’ (which is another file contained in the winmail.dat file) will be rendered as an OLE object.”
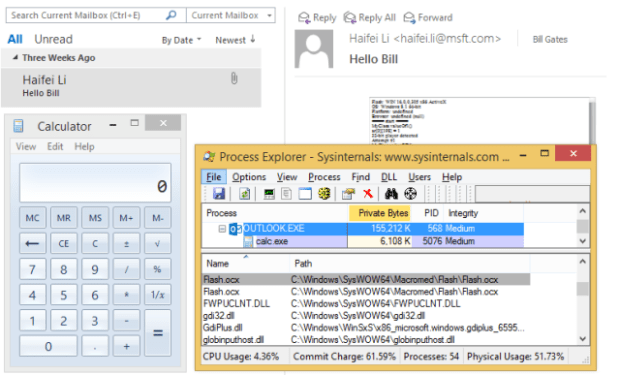
OLE objects are handled differently by Outlook without the new patch—they are rendered within the e-mail and call code from the application they’re based on—breaking out of the “sandbox” that Outlook usually contains documents within to prevent malicious scripts from launching. As a result, an attacker could “‘build’ a TNEF e-mail and send it to the user, when the user reads the e-mail, the embedded OLE object will be loaded automatically,” noted Haifei.
This sort of vulnerability makes for an extremely dangerous phishing attack—the victim doesn’t even have to click on anything within the e-mail for it to execute, as it opens automatically when the e-mail is viewed. And that automatically opened attachment can even be a Flash exploit, as Haifei confirmed in testing. “By packing a Flash exploit in an OLE enabled TNEF e-mail, an attacker can [achieve] full code execution as long as the victim reads the e-mail,” he reported. “We use Flash OLE object as an example since Flash (zero-day) exploits are easy to obtain by attackers, but please note that there are other OLE objects [that] may be abused by [an] attacker.”
The OLE method can even be used within the content of an e-mail message sent as an attachment. Outlook automatically sees .msg files as “safe” and opens them in an Outlook message view rather than sandboxing them—and as a result, any OLE content within them will also automatically be opened. This makes the vulnerability “wormable,” Haifei noted—an exploit could re-send itself as an attachment from the first victim to others in the victim’s address book, spreading the exploit quickly across whole organizations. In effect, a single e-mail simply read by a targeted individual could result in the compromise of a whole company, as a message forwarded by a colleague would be more likely to be opened.
The vulnerability, identified as CVE-2015-6172, affects Office 2010 and later, as well as Microsoft Word 2007 with Service Pack 3. If you haven’t been able to apply the patches from December 8 yet, Microsoft has recommended turning off the message preview pane for Outlook to prevent malicious messages from being automatically opened and changing settings to view all e-mails as plain text. Haifei also suggested making registry setting changes with an “Office kill-bit” to block Flash content from automatically opening via OLE, by blocking the CLSID D27CDB6E-AE6D-11cf-96B8-444553540000 with Windows Registry Editor:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\Common\COM Compatibility\{D27CDB6E-AE6D-11cf-96B8-444553540000}]”Compatibility Flags”=dword:00000400
Changing this setting will prevent OLE-embedded Flash exploits within other Office documents from being executed as well.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.