Facebook doesn’t appreciate the effort, threatens to sue. Wesley Wineberg, an independent security researcher, participating in Facebook’s bug bounty program, managed to crack his way through Instagram defenses and almost get complete control over the service. Soon after the researcher disclosed the vulnerability to Facebook, the company threatened to sue, instead of paying the reward he was due for his work.
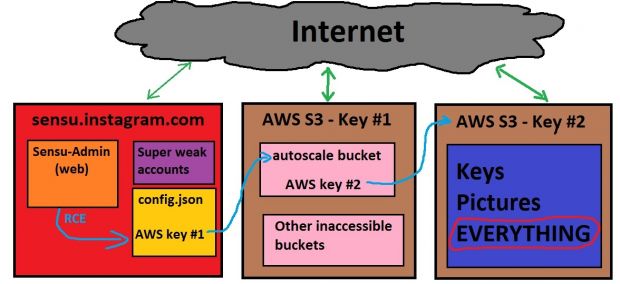
Mr. Wineberg, started his research into Instagram systems following the tip he received from a friend, that the sensu.instagram.com Web page, an administration panel for Instagram’s services, was publicly available via the Internet.
Researcher accessed Instagram’s backend administration panel
The researcher quickly tracked down the software used to run the administration panel, as the Sensu-Admin, and using older research that said the software may be vulnerable to RCE (remote code execution), he eventually managed to crack the service and access one of its configuration files containing credentials for the Sensu-associated PostgreSQL database.
In this database, Mr. Wineberg discovered over 60 accounts belonging to Instagram and Facebook employees. He followed his investigation by taking some of the password strings, encrypted via bcrypt, and proceeding to crack them.
Since some passwords were quite weak (e.g.: changeme, instagram, password), results popped up within minutes, and he was quickly able to follow through on his investigation, by logging in on the sensu.instagram.com interface.
Mr. Wineberg discovers Instagram heaven: all the selfies in the world
But Mr. Wineberg didn’t stop here, and he also had a look at other configuration files he found on the server. Here, in one of the files, he discovered an access key to an AWS (Amazon Web Services) account, which he then used to access the several S3 buckets (data storage units).
The researcher’s wild trip down the rabbit hole Instagram backend didn’t stop here, though, and he discovered yet another AWS key, which lead him to another 82 AWS S3 buckets, but these buckets were special.
Mr. Wineberg had inadvertently stumbled upon Instagram’s source, SSL certificates, other API keys used for interacting with other services, user pictures, static content from the instagram.com website, or as the researcher eloquently put it: “EVERYTHING” (selfies included).
But here is where his adventure ends, because considering himself to be a true white hat hacker, and also because of the limitations of the Facebook bug bounty program, he had to stop before doing any real damage to the service.
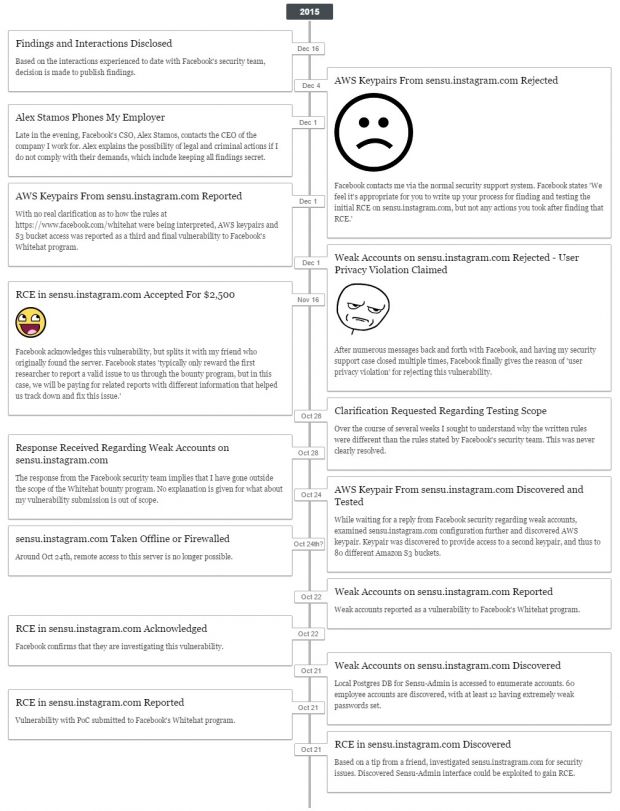
He disclosed his findings to Facebook’s security staff, but conversations did not go as expected, and instead of receiving a reward from Facebook for his hard work, Mr. Wineberg was ignored and admonished by the company’s employees.
Facebook threatens with lawsuit, tries to intimidate researcher’s employer
Communication from Facebook’s side became very scarce, and at one point, Facebook CSO (Chief Security Officer), even went as so far to secretly call Mr. Wineberg’s employer and threaten a lawsuit, unless the researcher keeps quiet about his findings and deletes any data he may have.
Following the mounting pressure, and the genuine mafia-like behavior showcased by Facebook, the researcher decided to go public with his findings, and penned a blog postwhere he provided both the technical details to reproduce the bug and the conversations he had with Facebook’s security department.
“In my opinion, the best course of action was to simply be transparent with all of my findings and interactions,” said Mr. Wineberg. “I am not looking to shame any individuals or companies, but I do believe that my treatment in this situation was completely inappropriate.”
In the meantime, Facebook has blocked access to the Sensu-Admin application. We reached out to Instagram’s PR for a statement, but previous emails for other stories always landed on deaf ears.
Earlier this year, Mr. Wineberg received a $24,000 reward for finding a security vulnerability in Microsoft’s Live.com service.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











