Despite calls to eliminate Adobe Flash Player, researchers inside and outside the vendor continue to invest in and build mitigations against modern attacks.
As recently as three weeks ago, Adobe announced it had rewritten its memory manager, laying the groundwork for widespread heap isolation, which is an important protection against use-after-free vulnerability exploits.
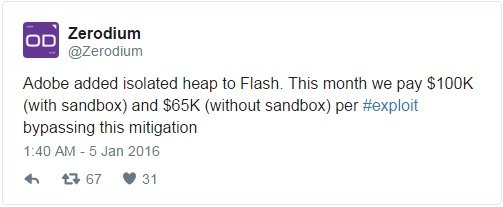
Today, however, exploit acquisition company Zerodium announced via its Twitter account that it would run a month long bounty program, paying as much as $100,000 for exploit code bypassing the heap isolation mitigation in Flash Player.
Zerodium, launched in July by VUPEN founder Chaouki Bekrar, buys high-risk zero-day vulnerabilities for all major platforms and third-party applications. Bekrar said that the attacks his company purchases would be available to customers via a feed of vulnerabilities, exploits and defensive capabilities; none of the attacks would be made public.
In September, the controversial Bekrar announced that Zerodium would host a million-dollar bounty for browser-based and untethered jailbreaks for Apple iOS 9, which had just been released. Zerodium announced at the end of the bounty that there was one winning team, but no details were released about the winners or the exploit. In November, the company published payouts for eligible zero-days.
Zerodium’s bounty is just the latest assault against Adobe Flash Player, which has been the focus of a number of high-profile targeted nation-state attacks, as well as a favorite target of exploit kits used to great profit by cybercrime outfits.
Many in the security community have pleaded with organizations to ban the use of Flash Player because of its history of vulnerabilities. Adobe, for its part, pushes out what has become almost a scheduled monthly security update for Flash; the December update alone was a massive release that addressed 79 vulnerabilities, most of those enabling memory-based attacks such as use-after-free.
Use-after-free attacks have been a favorite vector for attackers, who have steadily gravitated away from buffer over exploits and in this direction. Adobe has received help from its partners in addressing this problem, with Google’s Project Zero research team the highest-profile participant.
In July, Project Zero introduced heap partitioning, which was integrated into Flash Player; the technique isolates different types of objects on the heap, Google said, adding that Chrome and other browsers make extensive use of this technique.
Prior to using Heap isolation, Adobe used a single heap for ActionScript objects, giving an attacker the luxury of attacking a Vector object and dictating where objects are allocated. By corrupting memory in this way, attackers could read and write in virtual memory and bypass ASLR to execute code. Heap isolation prevents this by allocating Vector objects in a separate heap, eliminating the attacker’s ability to corrupt memory in this way. The technique isn’t foolproof, however, as Endgame Systems proved when in November it published a bypass for heap isolation in Flash.
Heap isolation isn’t the only new mitigation to find its way into Flash in the last 12 months. Adobe said in December that it worked with Microsoft as an early adopter of its Control Flow Guard to protect static and dynamic code in Flash Player.
Source:https://threatpost.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.